
While participating in HITBSecConf Malaysia, security analysts The Grugq and Fyodor Yarochkin present their study of the ins and outs of the Russian hacking community, hacking forums and culture.

The Grugq: Hi everyone. This is Fyodor, I’m Grugq by the way. What this talk is on is it’s basically on the Russian underground hacking forums, and the Russian underground hacking culture. We’ve spent the last year…
Yarochkin: …Two
The Grugq: … It used to be 6 months, and then 6 months turned into 12 months and extended to more than a year, so we have spent quite a long time sort of monitoring these forums.
Yarochkin: Intelligence gathering project.

The Grugq: Yeah, open source intelligence gathering. It is still not open, but we are apparently making it into a service where you can purchase access to information about the trends within the underground community, but then we’ve had a lot of snags with the automated analysis that we need to do, we’ll get into that. So, roughly, this is a snapshot of what we have got so far (see right-hand image), so we are going to go over, basically, how both of us are experts at using our tongues. If there are any women that don’t believe us they can ask for a private demo.

Yarochkin: So, what we set out to do is we wanted to create a framework for doing open source intelligence gathering, automated monitoring of hacking forums both in the Chinese web-sphere, and also within the Russian web-sphere, so it is like a multilingual thing.
The Grugq: The beauty of this idea is that Fyodor speaks Russian, Mandarin and English – mostly English. And I speak Thai, which has a huge hacking community, as everyone knows. And we work with Fyodor to help him with basically figuring out what’s the stuff that we should be paying attention to and work on that. And we also had to build something like a back-end technology for doing this really massive web-scraping that we had to do. Everything fell apart when we had to deal with that fucking rubbish that Russian hackers speak – it’s not pure Russian, it’s not like a subset of Russian; it’s just a bizarre lingo. Basically, we figured out that we had to automate this. We started out by making Fyodor read everything every day.
Yarochkin: … And click.
The Grugq: This worked fine for me, but Fyodor started complaining, so we decided to automate the intelligence gathering part and then try and sift through a lot of the noise and extract the signal. So we had a fluctuating number of domains; we were dealing with ten top of the domains, each of these will have multiple sub web forums that we monitor, so there’re basically buyers, sellers, wipers, rippers, etc.
Yarochkin: And general hacking discussions which are usually quite crappy.
The Grugq: Yeah, it’s something like: “I need to get into my girlfriend’s Yahoo! webmail account, can you guys help me?” And then those guys go: “No, no, you’re so lame, if you have to ask you don’t know;” and some other dudes go: “Shut up man, you don’t know how to do it,” so it’s all pretty rubbish.
Yarochkin: I think the most interesting forums are actually these offerings of sales and buys – that’s basically where you can actually see what people are up to.

The Grugq: So, actually, from this we’ve detected several trends which are now starting to actually show up like we saw them initially; they’re now showing up as issues that you guys have to deal with on the Internet, like all the fake antivirus stuff. The reason why we had to do most of the shit manually – and by “manually” I mean that Fyodor had to read it off – is because we’re dealing with natural language. Natural language is notoriously difficult to parse into something useful. It’s incredibly complicated and you are dealing with these kids that do not know how to spell.
Yarochkin: They don’t want to know how to spell. It’s basically one of the criteria of being cool.
The Grugq: Yeah, they use the Russian form of leetspeak as well, where they misspell things deliberately to be cool. Some of the words that they use have been taken from English; they convert them from English into Cyrillic, so they have multiple misspellings of the same word. We’ve got an awesome example of this, of why automated stuff doesn’t work.
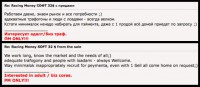
Yarochkin: How do you read foreign language forums normally? Any ideas on how to try to understand if you don’t know the language? You could use Google Translate. We’ve got a message here (see right-hand image).
The Grugq: Yeah, you take this, which is basically a very standard posting for an offering of a service. Some guys are selling something for 32 bucks. And what the fuck does that actually say? That’s the question. Let’s ask Google. Alright, so what does it say? It says: “We work long, know the market and needs of all. Adequate trafogony and people with loadami – always Wellcome. Way minimalok inappropriately recruit for peymenta, even with 1 Sell all come home on request. Interested in adult / biz cores.” So, yeah, good luck with that! Google is pretty fucking useless. The problem is manifold. So, Fyodor, could you quickly explain what this guy actually says?
Yarochkin: Basically, he is selling a traffic generating service.
The Grugq: Selling traffic to sites.
Yarochkin: He is also saying that people with big loads – big traffic generating capability – are always welcome.
The Grugq: Yeah, so this is basically mostly manual process.
Yarochkin: And the signature says: “I’m interested in adult / business traffic”.

The Grugq: “Traf” (“Траф” in Cyrillic) – that’s not cores, that’s short for “traffic”, which is English. So, what you find is that the Russian hackers’ slang (see left-hand image) is made up of a combination of “Fenya”, which is Russian prison slang; anglonyms, which is basically loan words direct from English; the Rhyming slang, where they basically take words that sound like the English words but are Russian…
Yarochkin: Who can tell us what “mylo” (“мыло” in Cyrillic) stands for? It means “soap” if you literally translate it.
The Grugq: So, what could “soap” be? Email, obviously, because the Russian word for “soap” sounds very similar to the English word for “email”.
Yarochkin: And also, there’re lots of cases where they just take an English word, they use a direct dictionary translation into Russian, and then they’ll be using it all over. If you go back to the image with the Russian posting, you’ll see “всегда велком” – the latter is basically just a Russian-spelled English word “welcome”.
The Grugq: Alright, so the automated translation – if we could get that right, we’d probably make more money than we ever would on just being able to sell the intelligence from this. So, that’s a bit of a snapshot of some of the issues that we’re dealing with. The things that we found are significantly more interesting: there’s a large number of different scams and schemes that are being played out on these boards. What we mostly pay attention to are the buyer and seller boards, where there’re people who are trying to sell services or products, and other guys who want to buy specific services or products. There are guys that get out there and say: “I need a load of traffic to these websites so I can do installations.” What will happen is someone will have websites that will basically run Trojans that will install onto boxes. And they want other guys to send traffic to those websites so that they can install their stuff onto those boxes. And they are willing to pay you money for every install that they run.

Yarochkin: Yeah, and you might be getting up to about $32 per single installation.
The Grugq: That can add up quickly, you can make $32 at home with your mother’s PC.
Yarochkin: So, a little bit of classification on the types of activities that we’ve seen so far (see right-hand image).
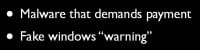
The Grugq: How do people actually make money? We’ve picked four arbitrary categories; you could go a lot finer, you could go a lot larger. There’s the Extortion thing (see left-hand image) which uses spyware that charges you to install it.

Yarochkin: We can show you the screen (see right-hand image). Have you seen this before? It’s in Russian, but there’re also international versions.
The Grugq: It says you are running a fake version of Windows. You have to send an SMS to this number and then you will get a special code to unlock your computer. It basically shuts down your box until you send the SMS which is premium-rate.
Yarochkin: So far we’ve seen two options. One is you need to send an SMS to the number, and they charge your phone. And another one is you just need to pay online with your credit card, and it’s a really bad idea to hand over your credit card details.

The Grugq: More interesting schemes are the “Partnerka” ones; the word comes from “partnership program” in Russian.
Yarochkin: If you look at this ad (see left-hand image), this is a real advertisement from one of the forums, it says “Installation Partnership Program”.
The Grugq: Sounds pretty legitimate, doesn’t it?
Yarochkin: And what kind of installations are those? They pay you for displaying their web content, which would be like an exploit loaded with malware. You may have heard about the case where people were opening The New York Times and got infected with stuff, because some of these guys bought advertising service and they used Flash with an exploit in it. So chances are you go to The New York Times – and you get the stuff installed on your box.

The Grugq: The way these guys operate (see right-hand image) is they actually set up legitimate credit card payment gateways; they set up their own credit card processing systems, these are Visa / Mastercard regulation compliant and also PCI compliant, so other people can’t hack them. And then what they do is they look for partnerships, web funds.
Yarochkin: If they charge people on their credit card and someone complains that it’s an illegitimate charge and the gateway doesn’t return the money back, then Visa basically cuts it off. So they have to stay connected to the Visa payment gateways, and they actually have a policy where if you for example buy this software, or if you unlock Windows and then you realize it was all fucked up – then they’ll actually give your money back. But the people who actually realize this stuff and ask for the moneyback – there’s much fewer of those than the people who don’t.
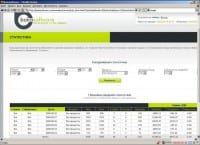
The Grugq: These guys make significant money, and they partner with webmasters and other scum. We’ve got a screenshot here (see left-hand image). These are partners who are making 30% of every payment. Here’s the top ten of the moneymakers (see image below). If you look at the numbers – around 150K, 100K, 90K, etc. – these guys are making real money: on a monthly basis, that’s not too bad, particularly in Russia. You can live quite well there if you earn that much.
Yarochkin: Unless you live in Moscow, then that’s a pretty sufficient amount.
The Grugq: The “Partnerka’s” are now starting to drive a lot of the online activity. All the hacking stuff is now moving to these partnerships. What we saw earlier is sort of loose collections of people that offered this and that, like “I’m selling access to Skype” or whatever. Nowadays we’re seeing that it’s more organized, with these dudes going like “We are a firm offering this service. We will pay you at this rate”.
Yarochkin: And they actually also do hires. Have you seen advertisements about an established company hiring, for instance, a Financial Manager, and you get, like, 30% from every transaction? Have you seen that kind of ads? The way it works, basically, is it’s like a money mule. How do people get traced? Usually through a banking transaction. The people who organize the whole thing don’t want to leave the record of banking transactions. So, what they do instead is they hire people – it’s like an illegal job – and once you get hired you get money (like WebMoney) on your account, and you are supposed to transfer it somewhere else. For every transaction you complete, you get 30%. And in certain occurrences, they also require that you give up your username and password so you get “better” trust relationship with your company. So they get pretty scrupulous with the whole identity control.
The Grugq: There’s some really cool identity stuff that they do as well. A lot of the money that gets moved around in these illegal economies is basically done by virtual currencies (see right-hand image). The main one right now is called WebMoney. The Russian FSB are supposedly now taking over WebMoney. It used to be run mostly by the Russian mafia.
Yarochkin: In Moscow it’s getting kind of tough. I was in Moscow about a month ago, and they’re starting to change regulations. So, when you go to the WebMoney office, if you cash money – you’re supposed to show your identity card, if you sell money – you can stay absolutely anonymous. But Russia cannot control the whole world, so if you look at the WebMoney offices (see left-hand image), there’s one in Czech Republic, in Prague; but the funny one is in Thailand. Why do you think a WebMoney office would be in Thailand?
The Grugq: Because all the Russian mafia are based in Pattaya. I was once purchasing services from some of these Russian forums…
Yarochkin: You were purchasing services for illegal transactions?
The Grugq: I was not doing anything dodgy, I just needed a lot of proxies – really a lot of proxies. And so, basically, I needed to get WebMoney because that’s the only way that you can do transactions with any of these Russian guys. And what was happening is I went to the website, I clicked through all the stuff until I get to something like “Now send me money”, and there was this guy named Stanislav who gave me the bank account, and I could go to any Kasikorn Bank, which his bank account was, pay cash, it got directly deposited into his thing, send an SMS to his number – and then he transfers 90% of whatever you gave him to WebMoney account. He also used to offer a cash out service, where for 6% he would take any money out of what you transferred as WebMoney to him, convert it into cash and then send on a courier to wherever you were.
Yarochkin: Yeah, so there’s this guy on a motorbike with a bag of cash delivered to your house.
The Grugq: Now we’re moving on to online goods. Another problem with a lot of these guys is, once you get a credit card, it’s very hard to convert a credit card into actual money.
Yarochkin: You cannot just withdraw money from the credit card directly.
The Grugq: Yeah, you need to convert a credit card into cash, because you can’t pay rent, buy food or alcohol with just the credit card numbers – that’s not good enough. So the typical way to do this is by selling goods online. One of them is Skype, so you can buy Skype accounts (see right-hand image).
Yarochkin: Just some orientation rate: 1 WebMoney corresponds to 1 American dollar.
The Grugq: Yeah, 1WMZ means 1USD.
Yarochkin: In one of the advertisements, they say: “10-dollar Skype accounts are going for $4”. The other one says: “For Skype OUT you get 1 to 2.5 exchange rate”, so if you want to buy a 250-dollar Skype account – you pay $100.
The Grugq: The Cyrillic “ВМЗ” stands for “WMZ”.
Yarochkin: And then, you get unlimited Skype access to call all around the world for $25.
The Grugq: This guy is quite legitimate. One of the things to realize about this is these ads are on Russian hacking forums, so what they’re trying to do is they’re trying to sell Skype accounts registered by hackers to other hackers. This is not a good market. These are not the ideal people to try and sell these things to.
Yarochkin: And yet, they’re offering moneyback guarantee, so if you buy a Skype account and it doesn’t work, they can give you another Skype account or return your money back.
The Grugq: So, yeah, you can’t lose, except for the fact that none of the people that they are selling to would actually buy this. These guys are not the brightest bulbs on the tree; they can steal credit cards but they can’t actually sell things to each other. They’re not very good. This (see left-hand image) is a Chinese version actually.
Yarochkin: They basically sell iTunes gift cards, and the exchange rate goes 100 US dollars –12 Chinese Yuan. So, for a 100-dollar gift card you pay 12 RMB (renminbi). Considering the official exchange rate, you pay a little over a buck for a hundred.
The Grugq: The amazing thing is, when this first started about six months ago, you were paying 80 USD for a 100-dollar gift card. The first guy to figure this out was making bank, and then everyone else who saw it was like: “He’s charging 80, I’ll do 50”. And even two months ago it was about 20 to 1, and now it’s something like 100 to 1. We took this screenshot a couple of hours ago.
Yarochkin: So, if you’re still interested, you can go and buy.
The Grugq: The thing is, this is basically a Chinese version of eBay; it’s not even an underground forum. Like, if you go on eBay and you look for iTunes gift cards – it’s similar to what these dudes have got, selling iTunes cards that they get with stolen cards. Next step – we are going to look at some real examples. Oh, this one is going to be hard to read.
Yarochkin: And yet, I’m going to read it. It says: “I’m selling proxies for brute-force. The price is 20 proxies for $4, 50 proxies for $6, 100 proxies for $9, and 200 proxies for $15. If you want more, we can agree on special price”. Then we got the follow-ups…
The Grugq: Yeah, some dude goes: “How fast are they?” And the next dude is like: “Are you fucking kidding me? Are these made of gold?!” So, the follow-up after that is: “Obviously, you’ve made a mistake – you forgot a zero, so it should be 200 proxies for $4”. It’s really pretty amateur on these boards. And then the last one is pretty good; this guy goes: “What are you fucking talking about? For $4 you can buy 400 proxies, not 20!” So, these dudes are really not making money.
Yarochkin: If you look at the forum posts, you can see how many offers they got there. There’s a whole bunch of selling offers. There are lots and lots of pages with these.
The Grugq: There’s a lot of traffic on these things. Daily, it updates with dozens of posts, no problem.

Yarochkin: We picked some interesting ones. How many of you know how useful passport scans could be? It’s really “useful”. So, in one of the offers they are basically selling Russian passports. This guy sells a complete set (see left-hand image). He sells a bank account with ATM card of a European bank. The package includes the online account access, ATM card, passwords – per month you can withdraw up to $6000 – copy of the passport, and SIM card registered on the “right” name.

The Grugq: We got a picture of all these things (see right-hand image).
Yarochkin: And the last thing in the advertisement says: “I can prepare the identity for you on order, takes me one week”. I think what he does is he takes the passport scan…
The Grugq: …And then he starts registering. What he’s doing is he’s taking a passport scan, which will have a complete identity and enough to start setting up bank accounts. So, once he has bank account he starts setting up more of an identity.
Yarochkin: We’ve got another example. It’s an advertisement selling passport scans, very cheap, but it’s not limited to Russia. I can translate the list of countries; it says this thing is organized across continents, so you can buy from Austria, Australia, England, New Zealand, Belgium, Germany, Finland, Hungary, the Netherlands, Norway, Poland, Portugal, Estonia, Switzerland, and other countries, such as United States, Canada, Mexico, Bangladesh, Columbia. And then, they also sell credit cards. You can buy by name, or age, or country, or city of residence. One scan costs 3WMZ for international passport, and for Russian passport it’s 4WMZ. I don’t really know why the Russian passport scan is more expensive; probably, because it’s more “Russkiy” (transliterate for the word “Russian”).
The Grugq: So you can see just how valuable someone’s identity is.
Yarochkin: Yeah, and there’s another funny thing: he also offers the service of redrawing the passports.
The Grugq: So, basically, you can send him a passport scan and he will fix the name and stuff, in case they got it wrong for you. Regarding cash-out, that’s probably one of the hard problems that these guys have. So, if they steal access to a bunch of bank accounts, they still need to extract the content, they need to extract the money. I guess anyone who’s been on the Internet has seen all these articles about Russian criminals being organized into offering services and stuff. This is what it looks like; these are the guys offering services you read about in those articles. And it’s pretty amateur. These guys have got reputation systems based on handles on web forums. They have whitelists and blacklists, for instance some guys will say: “I only deal with people who have good reputation on this forum, or you have to pay upfront”.
Yarochkin: One of the most valuable commodities on these forums is actually ICQ numbers. Even now, as of today, ICQ is one of the primary communication means for this whole scene. What you need is a good ICQ number, sometimes obfuscated so that an automated grabber won’t pick it up.
The Grugq: Yes, one of the most valuable commodities they have to sell each other is nice-looking ICQ number, like if you’ve got lots of double digits, etc. You see ads where they say, like: “This is 4 years old”. And I’m like: “Yeah, this is a good finely aged ICQ number, none of this new trash, you know”… We’ve got another kind of funny one, this is on the forum that’s no longer up. So, everyone knows about Steam accounts, right? It’s where you sign up and you can play games. If you purchase these accounts you will be able to download and run these games as for the registered, not as hacked or cracked or anything like that. And these go for about $3.

Yarochkin: Here on one of the forums we see an ad saying: “Steam accounts – 5 accounts for Left 4 Dead” (see right-hand image). The price is in roubles. So, it’s 220 roubles, and the exchange rate is about 1 US dollar for 30 Roubles, so it’s 7 bucks or so.
The Grugq: Obviously, the price of Steam accounts has gone up. So, there’re really a lot of different things that get sold, and some of those aren’t the things that you really think about as having any value, like ICQ numbers, or access to gaming accounts.
Yarochkin: There’s also a service for sending SMS from a spoofed number.
The Grugq: There’s also these identity services, where you can purchase a completely new identity based on passport scans. Fyodor actually had a theory on how the passport scans were captured.
Yarochkin: It was in my home city, Moscow, in the airport (undisclosed name). But actually it’s possible to get access to the systems which are used for immigration control: whenever you go through the immigration control your passport gets scanned. So, I think that’s one of the primary sources for the passport scan data. And it’s not only Moscow. I think at the airport of Bangkok it’s similar. Basically, you walk through the airport and you see some Ethernet plugs there – has anyone tried to plug in a cable and see what’s on there? The password is “cisco”.

The Grugq: …That is all speculation, by the way. So, this is a guy offering a complete package (see left-hand image).
Yarochkin: The funny thing is, it literally says: “For funds of any degree of dirtiness”. You get the whole package which includes bank account, online access, ATM card; you can withdraw $1000 per day; you can also increase the limit, this will cost you $30; you get the code map for online access; you get copy of the passport, and you get the SIM card. You can also order custom-made accounts: if you have a passport scan, this guy can do the rest of the stuff for you. He didn’t list the price there – you’re supposed to contact him.
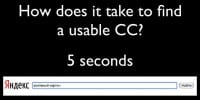
The Grugq: One of the other things is – how long do you think it will take to find usable credit cards using these Russian forums? A wild guess? Starts from close to nothing.
Yarochkin: Slightly longer, because it takes a few seconds to type.
The Grugq: So, this is the number one Russian search engine.
Yarochkin: Yandex is like Google of Russia. The first link, if you put in something like “dump of credit cards” using the Russian forum slang, gives you names, addresses. If you are looking for more, you can actually buy it.
The Grugq: In terms of the question regarding whether there are people who buy this stuff or not, many people buy proxy services; I’ve bought proxy services. I know that there are people who complain about prices, like: “When I used to buy CCVs they never cost that much”. It’s hard to tell. And a lot of the stuff looks like they’re hitting the wrong markets, like they know that they want to make money, and they have figured out a way to make money – they just haven’t figured out that they can’t make money from each other. These dudes are really not very bright in terms of generating revenue from the resources that they have available. Like with the Skype credit – Skype credit is something that many people would be interested in buying at a discount rate. I guess that there are several people in this room who would purchase discount Skype credit. iTunes gift cards – 1 dollar per a 100-dollar card. I would pay money for that; that is a good value. The thing is – I don’t read Chinese very well, at all actually. So, posting on a Chinese forum is not a good way to find me as a consumer. Similarly, having posts for Skype credit on a Russian hacking forum is a great way to tell other Russian hackers that they can use their stolen credit cards, buy Skype credit, and try and sell it. It’s not a good way to convert stolen credit cards into actual cash money. This is a great opportunity for someone who wants to enter in a certain level of the Russian criminal market and really take over. You could access these Russian web forums and make them available to international market.

Yarochkin: I think you have to speak the language well, too, because, if you want to buy proxy servers, as soon as you don’t sound fluent enough, they’ll think you must be a cop. One more thing: aside from the credit card stuff, you can also buy money laundering service (see left-hand image).
The Grugq: This one is awesome! The direct translation of this – you’ll never get it. Basically, this is for money laundering – you can actually purchase money laundering services online.
Yarochkin: The title of the post is translated as “trash can for dirt”.
The Grugq: …Or, as we say in English – money laundering, obviously…The reason that it’s called “trash can” is…
Yarochkin: …Because the combination “trash can” in Russian sounds kind of similar to the word “washing”.
The Grugq: So, the word for “trash can” in Russian sounds similar to the word for “washing” – washing money, right?
Yarochkin: The code for Yandex Money is literally translated as “poison”, because the Russian word for “poison” coincides with the Russian abbreviation for Yandex Money – “ЯД”. So, another advertisement says: “I want to buy dirty grey poison, up to 120 thousand roubles; I take 40%, i.e. for 100% dirt you get 60% of clean money. I’m going to wire it via Alfa-Bank, Telebank, or clean Yandex Money account”.
The Grugq: So, you can “wash” your money. They can streamline the workflows and start going together – like complete packages – and then offering them in English. That way they would probably make more money.
Yarochkin: Another good business is selling traffic. What kind of traffic is that? It’s basically about clicks, real computer users’ clicks.
The Grugq: We saw an advertisement about this service on one of the forums. Basically, what it comes down to is they have the best infection ratio. So, for the amount of traffic that gets sent they guarantee the highest number of infected computers.
Yarochkin: Why would you need the infection ratio thing? If you build a botnet, what do you do? They have these “Partnerka’s” where they have some exploit-loaded malware; you get people clicking on it, and the ratio of the number of people who clicked on the link to the number of people who actually got infected and had feedback to the control center – that’s the infection ratio.
The Grugq: And these guys guarantee the highest level of infection ratio.
Yarochkin: You can actually buy the “guaranteed antivirus un-detection” service, where you get .exe binaries from them, and they give you something like a month guarantee. Aside from that, they typically have a website providing paid service, where, whenever the binary gets detected by an antivirus, they’ll just do another update. And it’s all really automated.
The Grugq: There’s a site that used to sell access to a botnet directly online – www.proxy.ru. They are apparently not up anymore. It was basically just a control panel for a botnet. It was awesome; they just rented direct access to a botnet.
Yarochkin: You could select it per country.
The Grugq: Yeah, you could filter it down the list, like, for example, I only want Netherlands IP addresses and I want only SOCKS proxies, and then – bang, done.

The Grugq: So, everyone probably knows Twitter went down some time ago. How much do you think that cost per day, on average? It’s 80 bucks! Come on, 80 bucks to take down a web server!
Yarochkin: It’s a DDoS 911 service. If you translate literally, I think it’s quite funny: “Our service is the best way of getting rid of annoying competitors who don’t allow you to work. The best feature of our service is we work regardless of the thematic of the target site. Immediate assistance in solving your problems – 24-hour support. We have the most affordable prices on the market. The average price is $80 per day. The final price may vary slightly (increase or decrease). And we offer a wholesale discount”.
The Grugq: Alright, there are some other ads as well. We also found a different forum post where there’s a guy called Vlad. He is selling DDoS service for the same price, 80 bucks a day. And some other guy posted, saying: “How do I know you’re good?” And he’s trying to get endorsements from other people who are saying something like: “Vlad is the best man! If you want to take down the Pentagon – you go to Vlad”.
Yarochkin: That’s actually a typical way of selling the service. People are not going to buy stuff unless you get endorsement from a trusted partner on the forum. So whenever you post an advertisement on the forum, you would normally include links to endorsements, where other people on the forum say: “Yeah, I’ve bought this service, it really works”. Some will say: “I’ll give you 5 minutes of free testing service”.
The Grugq: Yeah, what a lot of these guys offer is they can give a free test where they can take down a site for a short period of time to show that they can do it. And then you can actually purchase the full day of DDoS.
Yarochkin: So, if your site gets DDoSed for about 5 minutes, get ready for some more serious stuff.
The Grugq: As long as it takes the WMZ to get transferred between accounts – that’s how long you have before you go down.
Yarochkin: Do you remember Twitter being down for a few days? Do you know what the reason was? Basically, a Georgian dissident who was tweeting and blogging on LiveJournal – and LiveJournal was actually DDoSed last year – and what they did is they blocked one of this guy’s accounts, but the other accounts were still accessible. Speaking about Twitter, they didn’t differentiate – so the whole Twitter went down for 2-3 days.
The Grugq: That’s 160 dollars’ worth of DDoS services to take Twitter down. And it’s all because this guy pissed off some people who have access to WebMoney accounts and can read Russian.
Yarochkin: Yeah, 80 bucks – well, I can afford it.
The Grugq: So, we’re going to do conclusions.
Yarochkin: And then we can maybe show you some other funny examples.

The Grugq: Yeah, we have lots of porn that we’ve downloaded on these sites as well. We’ll look at that. Okay, one of the main things that we didn’t mention at all but I’d really like you guys to take away from this is that the people on these forums are geeks, not gangsters. Everyone has this impression that the Russian hacking scene is dominated by the mafia. As far as we can tell, that’s not the case. A lot of these guys are high school students, college students, sysadmins that have too much free time and access to computers. They are not, like, hardcore mafia. They are guys who, when they get angry, will spend 80 bucks and have your website taken down. They are not the people with prison tattoos, they can’t do that anyway. They are basically young kids who are a bit dumb, and they are making pretty small amounts of money – 80 bucks to take down Twitter is not good money for a value. What we’ve seen is a lot of this is youth culture. Everyone remembers back in the late 90s, early 2000s, when they had the “hacker renaissance“, everyone was talking in leet and k-rad.
Yarochkin: There’s a market for beautiful ICQ numbers. Who knows what’s the difference between 8-digit ICQ number and 6-digit ICQ number? Expiration date. So, if you have a 6-digit ICQ number – you’ve been on the scene for a long time.
The Grugq: Yeah, it means you were back in the day, man…So, a lot of this is basically youth culture stuff, like these deliberate misspellings, this hard lingo. They use some Russian prison slang, but it’s not real “Fenya”, not the real Russian prison slang – it’s actually a dialect of Russian. So people who are long-term prison inmates learn real “Fenya” and they’ll speak in “Fenya”, not in Russian. And what these guys do is, to basically build a bit of cred, they use some “Fenya” themselves to show, like, “Hey man, I know a couple of words of “Fenya”, I’m pretty hardcore”. But the thing is, they have to use “Fenya” words that everyone else knows, otherwise no one knows what the fuck they’re talking about.
Yarochkin: For most of the goods they’re trading with, they’ve got a separate word to denote those. For example, dedicated server – they just call it “dedic”, which, when spelled out in Russian (“дедик”), means “old man”.
The Grugq: Yeah, as you’ve noticed, a lot of it is actually based on English stuff. Also, what we’ve seen is that these dudes are actually profit-driven, which is kind of cool – they are making some effort to make money, they are just not very good at it.
Yarochkin: Alright, do you have any questions?
Question: On your point about the ratios: so, this guy was offering the best ratio; do you know any figures?
The Grugq: That is an excellent question. One of the things that we planned to do, if we’d actually been accepted for this talk before yesterday, is we wanted to develop metrics to see how costs of services have changed and costs of goods have changed over time, and also the number of people offering things – you can see that partnerships start appearing at one point, and there’s one guy offering it, and suddenly there’s ten; and you could track all these trends. So we wanted to develop metrics and stuff like that. But we didn’t, because we didn’t have the time. What are the ratios for that? I have no idea. I know that the word for it is “otstuk” (“отстук” in Russian), which means something close to “feedback”.
Yarochkin: In one of the advertisements, they mention a 30% “otstuk”. So, if you get 1000 visitors – 300 get infected.
The Grugq: We came across a post about a botnet where they’re making fun of a guy for charging so little. These dudes are ragging each other a lot on the forums; it’s a really hostile environment. For example, some dude shows up and says: “I’m offering this thing for sale”, and all of a sudden he gets “You suck!” in response. It’s just guys like us. Another case: there was some guy trying to sell a botnet for $440 (440WMZ), and everyone’s like: “How come it’s so cheap?”
Yarochkin: The guy says: “I’m selling a botnet, complete set, for $440. All questions via ICQ”. And then the other guy goes: “Is it only 20 bots or what?” And the guy answers: “No”. The next question is: “Fewer?” And some other guy says: “It must be Zeus botnet”. You know, Zeus is like a builder for botnet binaries so you can build custom binaries with custom function, and they are not supposed to be detectable by signature-based antiviruses. And then the guy goes: “I’ve got over 5K bots in my botnet”. And the other guy asks: “5K bots – is that online ones, or total number?” And they answer is: “Of course it’s total. 5K online bots cost more”.
The Grugq: So, one of the things you see is that with botnets the actual membership fluctuates quite a lot, based on whether PCs are up and they’re able to connect. But you will have a large pool of infected machines and a subset of ones that will be available every time.
Yarochkin: Yeah. He’s giving some further details on the package: “Apart from the bot, I’m also selling 5 clean builds of the loader”, – a clean build means it won’t be detected by an antivirus, – “also hosting and domain pre-paid for a month”. That’s it.
The Grugq: So, these dudes are really funny online. We also saw on a forum someone selling a botnet for $2000, but he didn’t offer a lot of information, and it was obviously too rich for these guys. What other funny stuff have we got?
Yarochkin: There was an incident in Russia, where an online video player was requiring you to download a codec, and the codec would be a binary which, aside from being a codec, would manipulate your Hosts file and send your traffic somewhere else. There’s, like, a Russian version of Facebook called Vkontakte.
The Grugq: So, there was a phishing website set up for this Russian counterpart of Facebook. And the binary was weak, and their PHP skills were lame; and it ended up that the password was actually available on the Internet. Basically, it was posting everything directly to one address and you were able to download it.
Yarochkin: You could get the source code for the phishing Trojan.
The Grugq: So, that’s the fascinating world of the Russian hacking forums.
Yarochkin: Do you have any more questions? Anyone want a free beer?
Question: Aren’t most of these forums monitored by Kaspersky?
Yarochkin: I think the volume is too large. I don’t think Kaspersky actually follows up this stuff.
The Grugq: I think a lot of the stuff that they post on these forums is not binaries or something; it’s not like: “Here’s the latest virus that I’ve now written, please download it for free and add it to your antivirus signatures”. It’s more like this stuff: “Hey guys, I’m selling a botnet” or something. So, monitoring it is not going to generate revenue for Kaspersky unless they want to start doing open source intelligence gathering.
Question: These are not password-protected forums, right?
Yarochkin: Not really. You have to sign up if you want post stuff, but even if you don’t have a login and password, you can still see most of the stuff; you might not be able to see some links and attachments.
The Grugq: They don’t have very long time spans, so they won’t be monitored a lot.
Yarochkin: They’re coming up and going down all the time. The longest possible time span there is probably a year or so.
The Grugq: One of the problems is that I’m pretty sure a lot of these forums get registered with hacking, like with stolen credit cards. So, after 1-month payment cycle the web host goes away; and they move on.
Yarochkin: There are good websites to look for new forums. Those are like online bookmarking services in Runet, the Russian Internet, and you can search for the keywords – and this way you find new forums.
The Grugq: We really wanted to make a lot of this automated and then be able to pull out metrics and start being able to offer information, but… We’re looking for numbers; we’d like to be able to track what’s happening. As I said, part of our problem has been that Fyodor doesn’t scale.
Yarochkin: Maybe I will.
Question: Why don’t you just hire some of the guys on the forums?
The Grugq: Yeah, for 3 bucks a day. I think if they could speak any English at all, they would probably make a lot more money than they are doing now. You see that pretty much everything and anything gets for sale. These dudes can come up with the rudest ideas of what they can sell for money. Well, that roughly comes to the end of everything we were going to talk about. So, thank you guys very much! Who said they wanted free beer?






























