Reveton – the universal extortion instrument
The Reveton Trojan which has become a buzzword in the IT security circles over the course of the past year or so is being actively exploited in different profit-driven cybercrime campaigns. A few weeks ago we posted a thorough analysis of the version generating a fake FBI alert on victims’ machines, but there appears to be much more to Reveton’s activities than that. This entry is intended to provide a deeper up-to-date insight into what’s behind the scenes of Reveton virus distribution.
Most security analysts are inclined to believe that the malicious payload is being delivered to computers with the aid of the infamous BlackHole exploit kit which is known to be one of the prevalent web threats globally, according to AVG and Sophos statistics. Users typically get infected with this malady via compromised web pages or by navigating to a malign link embedded in a spam email. This way the potential victim gets sent to BlackHole server’s landing page which leverages obfuscated JavaScript in order to determine all possible exploits on the targeted computer. If delivering the payload turns out successful, the BlackHole exploit kit server receives data on the specific exploit that was used for contamination. Some of the more recent research testifies to the fact that the semi-legit Styx exploit pack is involved in Reveton propagation as well.
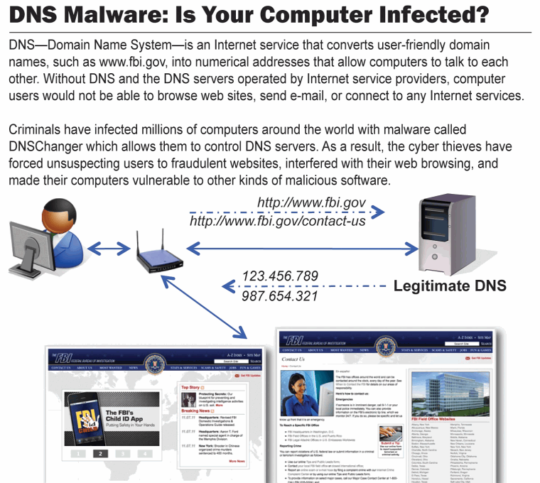
The previous distribution background of this infection was eventful and marked by a number of noteworthy facts. Its predecessor, known as DNSChanger, was active since 2007 and would covertly modify an affected machine’s DNS settings in order to redirect the victim’s web traffic to certain ad pages, which was an activity intended to generate advertising revenue to its creators.
Since the DNSChanger campaign gradually reached an enormous worldwide scope, the international law enforcement made a move to cease it and dismantle the gang spreading the virus. Resulting from a two-year investigation by the FBI dubbed the ‘Operation Ghost Click’, the criminals were identified and arrested in 2011. As it turned out, the DNSChanger botnet was maintained by a number of Estonian individuals led by Vladimir Tsastsin, formerly the owner of EstDomains Inc. which was known to cooperate with the Russian cyber mafia in terms of registering domains that were used for spreading rogue antiviruses and other malware.
The sensational arrest of DNSChanger botnet creators did not bring this whole underground business to a halt. In July 2013, security analysts discovered a new version of this infection, currently known as Trend DNSChanger Bot. In contrast to its infamous forerunner which indulged in click fraud and illicit advertising schemes, the new threat can be used for money extortion purposes due to the fact that it can lock the host computer. Furthermore, Trend DNSChanger exhibits refined rootkit features, which makes its code hard for security software to detect and exterminate. Therefore the obvious shift that took place here is in monetizing tactics. As long as this version’s creators are still at large, the bot is being used as part of the diversified scheme for ransomware campaigns implementation.
Insider statistics
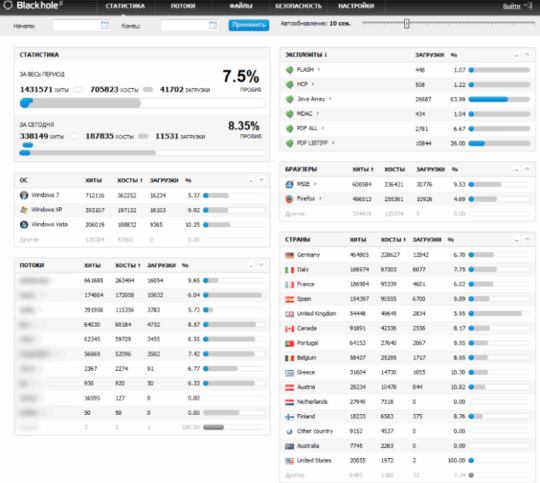
A French security expert and blogger known by the handle Kafeine and his colleagues from the botnets.fr project have managed to access BlackHole exploit panel associated with Reveton distribution. The screenshot below illustrates the actual breakdown of statistical data on exploits that were used to plant this infection during one single day, as well as the daily amount of traffic by operating system, browser, and country.
There are quite a few things one could take away from this screenshot alone. First off, the panel’s interface is in Russian, which hints at the origins of this entire campaign. The number of hits and downloads per day is enormous. Furthermore, the exploit that’s being most intensively used for executing Reveton appears to be Java-related, most likely due to outdated installations of this software. Also, the most vulnerable web browser in the context of this campaign is Internet Explorer. The countries being most targeted are European ones, which in fact brings us to the next point of this article reflecting schemes for monetization of the malicious traffic.
Mimicking Local Police Forces
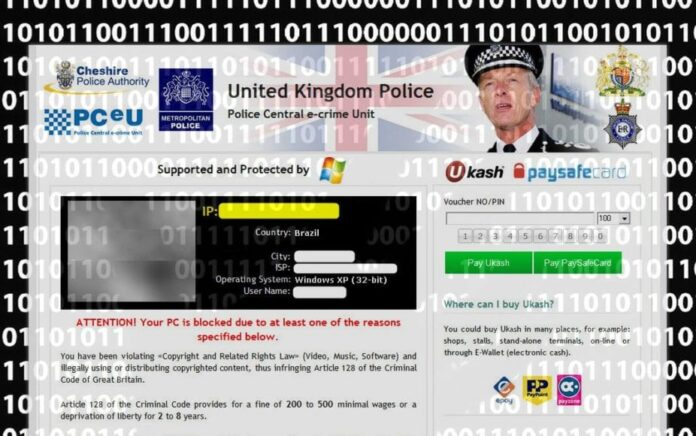
The somewhat unexpected geographic orientation of Reveton spreading is inalienably associated with new manifestations of the virus. While victims in the United States are mainly affected with the FBI MoneyPak variant, users from other countries are encountering ransomware that displays phony block screens allegedly from the local law enforcement services, e.g. Metropolitan British Police, PCeU – Police Central e-Crime Unit, Royal Canadian Mounted Police, CIBS POL. Bundesamt fur Polizei, Australian Federal Police, Office Central De Lutte Contre La Criminalite Liee Aux Technologies De Information Et De La Comunication, and many others. The fake alerts are written in the corresponding languages, accusing victims of certain criminal offenses, including violation of copyright and related rights laws, distribution of prohibited pornographic content, illegal access to personal data originating from one’s PC, etc. It’s obvious that all of these claims are framed up and should not be taken as ones originating from the actual law enforcement divisions in one’s country. The fine of around €100 for unlocking a jacked up PC is to be paid via PaySafeCard or Ukash, which guarantees the fraudsters a significant degree of anonymity due to the fact that those are prepaid services.
Below is a set of screenshots for most widespread localized versions of the virus:







The infrastructure behind Reveton
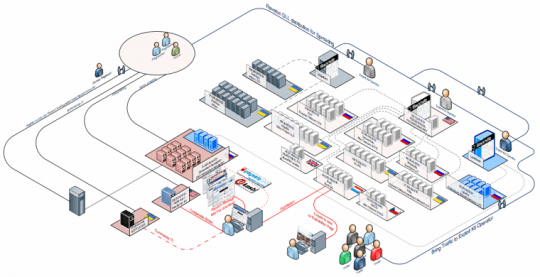
Judging from in-depth investigations conducted by cybersecurity specialists, delivering the Police ransomware to potential victims’ machines and further gaining profit is a complex process involving multiple intermediary components: BlackHole exploit kit operators, data centers scattered throughout a number of European countries, diversified payment processing units, etc. Based on long-term analysis of this criminal gang’s operations, Kafeine from botnets.fr has outlined the entire infrastructure of Reveton distribution and monetizing details in the following graphic:
By its essence and the underlying malicious payload, the “Police of … virus” is nearly identical to its FBI counterpart, the only significant differences being the block page design and ransom payment channels. As can be seen from the scheme above, part of what this cyber threat can do in any of its manifestations is credentials theft therefore attack prevention should be prioritized as a key objective.
The criminals’ earnings
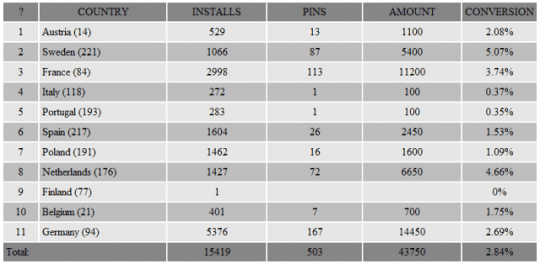
Now, what’s the financial output of this ongoing massive campaign? According to the actual stats obtained by the above-mentioned French researchers, the amount of earnings gained by Reveton distributors appears to be pretty astonishing. The extortion revenue from European countries alone may exceed 40,000 Euros daily (see image).
Monetization
As has been mentioned, ransomware victims are urged to pay a fine through prepaid cards such as Ukash, PaySafeCard or MoneyPak by entering a 14-digit code into the form on the fake block page and submitting it to the scammers. Now, the specificity of cashing these funds implies that the codes can be used at a pre-defined list of stores for buying goods or should be tied to a United States bank account. Apparently, the above options are unlikely to suit the bad guys who are most likely to live outside of the U.S, so the fraudsters had to come up with some other ways to launder their illegal earnings.
As per extensive research by the well-known cybercrime analyst and blogger Brian Krebs, one such scheme presupposes the use of the so-called cashout service. It involves gambling services in the United States, where one can bet on dog and horse races; individuals who link the voucher codes to prepaid debit cards, withdraw money through ATMs, get their commission and wire the rest of the funds to the cashout service (e.g. via Western Union). Then the ransomware distributors get their share credited to their account.
It’s difficult to estimate the total amount of money that has already been laundered this way, but given the approximate stats known with regard to 300-dollar MoneyPak voucher codes – about 24,000 of those have been processed through the cashout service – simple math testifies to the following: it’s over $7 million. Again, these are not accurate numbers; moreover, scammers have got a presumably large quantity of Ukash and PaySafeCard codes as well at their disposal, so it’s a very serious business.
Takeaways
It’s obvious that the Reveton Trojan is an inalienable component of a whole underground economy, so it’s not likely that scammers are going to abandon this immensely profitable business anytime soon. To significantly reduce the odds of being infected with different variants of this virus, one should make sure potentially exploitable software is regularly updated – this particularly applies to Java. Running an effective antivirus with up-to-date definitions database is equally critical.






























Your computer has been locked virus is another bogus police message which is from the same ransomware family that tricks novice PC users into believing they have done something wrong and instructs user to pay fine through moneypak.
Its Fake and never pay anything to remove but contact professional
when ever this rogue virus pops up and blocks your browser simply note what site you visited then click the task bar goto task manager and end task on whatever internet browser is running such as chrome just close it…