A Russian computer security company detected a new spyware program called Flame. Julia Smirnova from Die Welt, a German national daily newspaper, talks to Kaspersky Lab’s Senior Virus Analyst Alexander Gostev about this new cyber virus.

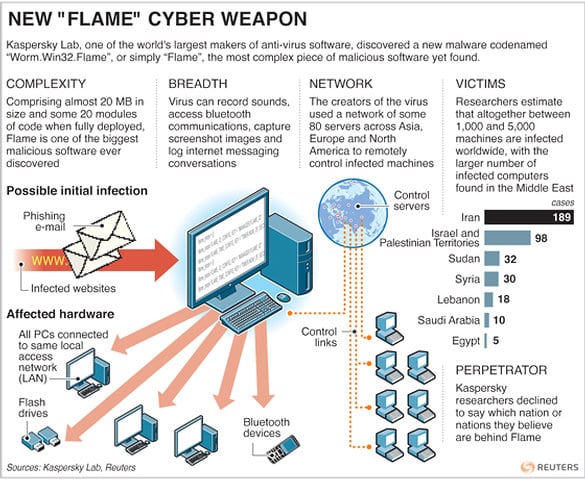
Alexander Gostev: In April of this year, several computers of the National Iranian Oil Company, as well as several Iranian ministries, have been infected by an unknown virus. This case was just a single link in a chain of cyber attacks during which viruses like Stuxnet1 and Duqu2 were used. The International Telecommunication Union (ITU) has asked us to analyze the situation. We have been searching for a virus called Wiper, but found something more terrible instead – the Flame.
– What exactly does the Flame virus do?
– Like Duqu, Flame is designed to steal different databases. A completely new thing that Flame can be used for is audio spying. Flame detects and recognizes a microphone on the infected computer, turns the microphone on and then records every conversation taking place in this room. Recorded data is immediately transferred to the server from which the virus began to spread.
– Did Flame attack the same objects in Iran that Stuxnet attacked?
– Unlike the Stuxnet case, the number and character of attacked computers was broader. In addition to individuals, universities were among the victims, as well as various businesses.
– Do you think surveillance was carried out over nuclear scientists?
– We have no information about who owned the infected computers at this point.
– Does it look like the same people are behind Flame and Stuxnet?
– In our opinion, this was clearly not the same group of developers: a different programming language, as well as different software architecture was used in Flame. But there is still much in common between Flame and Stuxnet. For example, the way both viruses spread on the internal network of the enterprise and USB-sticks. Moreover, the virus authors used the same security vulnerabilities, those hacking techniques are not used anywhere else.
– How do you explain this?
– Most likely, there were two parallel projects which ran simultaneously. Both Flame developers and Stuxnet developers had access to the same database of security holes and vulnerabilities. It is also possible that Flame was created later, and its creators have made use of published and publically available information about the Stuxnet virus.
– But who can be behind this program?
– Flame is much more complicated, and the volume of its code is 20 times greater than that of Stuxnet. Flame has been used since 2010. Its authors have been constantly developing new modules, managing servers and manually collecting information from hundreds of computers. This is not an easy task at all. I believe that approximately from 10 to 20 programmers were involved in the development of this virus, and this is not counting the server management staff. I do not think any of the known groups of cybercriminals is capable of that. We believe Flame, as well as Stuxnet and Duqu, represent a modern-day cyber weapon developed by nation states. But we have no definitive evidence that a particular country has been involved in its development.
– Where are the servers which collected the stolen data? Where are they located?
– We suspect that at least 80 servers were used by the Flame virus. They are located in different countries – Germany, Turkey, Italy and Vietnam. Until recently, 4 servers had been actively used, but after we informed the public about the new virus, those 4 servers were cleaned.
– Where is the main control center?
People who run the new virus do not necessarily have to be in the same country in which the servers are physically located. In the past several months, virus operators changed the location of the servers a number of times. When we discovered the virus, the most important servers were located in Turkey and a few days later they were already moved to Germany.
– Have you ever received orders from Iran?
No. Relations with Iran are very complex. While analyzing Stuxnet and Duqu, we needed to contact the victims of attacks in Iran. But Iran turned out to be quite a closed country. We have received no response for any of our inquiries. We could have detected more viruses if Iran cooperated with us.
1 – Stuxnet is a computer worm discovered in June 2010. Stuxnet initially spreads via Microsoft Windows, and targets Siemens industrial software and equipment. While it is not the first time that hackers have targeted industrial systems, it is the first discovered malware that spies on and subverts industrial systems, and the first to include a programmable logic controller (PLC) rootkit.
2 – Duqu is a computer worm discovered on 1 September 2011, thought to be related to the Stuxnet worm. The main component used in Duqu is designed to capture information such as keystrokes and system information. The exfiltrated data may be used to enable a future Stuxnet-like attack.