Alexey Sintsov graduated from Saint Petersburg State Polytechnical University. Since 2001 Alex has been working on practical questions in the field of security analysis and vulnerability detection, as well as exploit development. He works for Nokia as a Senior Security Engineer. Alexey also writes for xakep.ru magazine. He has spoken at a number of infosec conferences like BlackHat, CONFidence, and HITB Security. Alexey is the co-founder of the first DEFCON community group in Russia – DCG 7812 and is also the co-organizer of ZeroNights conference.
Alexey Sintsov graduated from Saint Petersburg State Polytechnical University. Since 2001 Alex has been working on practical questions in the field of security analysis and vulnerability detection, as well as exploit development. He works for Nokia as a Senior Security Engineer. Alexey also writes for xakep.ru magazine. He has spoken at a number of infosec conferences like BlackHat, CONFidence, and HITB Security. Alexey is the co-founder of the first DEFCON community group in Russia – DCG 7812 and is also the co-organizer of ZeroNights conference.
Alexey has recently participated in Black Hat Europe conference and delivered a talk about honeypots. Privacy PC asked Alexey several questions about his talk and the honeypot concept.
Wikipedia definition: a honeypot is a trap set to detect, deflect, or in some manner counteract attempts at unauthorized use of information systems. Generally it consists of a computer, data, or a network site that appears to be part of a network, but is actually isolated and monitored, and which seems to contain information or a resource of value to attackers.
In brief: “Honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource.” (Spitzner, 2002)
– How old are honeypot techniques and how widely are they used now?
– The idea of honeypots is pretty old. The techniques are also old. But there are no limits on them. So actually you can use any IT techniques for honeypot. New, old – does not matter. It is good to improve the honeypot system by implementing new things. Main idea – an attacker thinks that he is attacking a real system. You can use anything you like as honeypot – VMware, web script, real hardware servers and/or honeyd.
– To what extent do laws restrict it and what are the general practices?
– Speaking of classic honeypot, I do not know any law against it. But if we are talking about “aggressive” honeypot, then it is a difficult question. Hacking systems is an illigal action, so in this case yes – “hacking back” is a bad thing to do, but if an attacker is hacking you, and then downloads something (backdoor) from your private system and runs it – why is it illigal? You do not PUSH anyone to download and run it. Nobody knows about this “something”, and any good Internet user never finds it, because this is in a protected zone where no one has access. So in this case there is no “corpus delicti”. Of course I am not a lawyer, and it’s just some of my thoughts that do not have any power.
– Whenever various factors are restricting us from really hacking back, annoying the attackers to death can be the way out (as in PaulDotCom guys example of recursive directories). Why not just annoy attackers – make them do more moves and waste more time? Moreover, it is completely legal. How prevalent are “annoying” methods in honeypots?
– Yeah, it is good and fun. And, you know, it works. Most attackers are script kiddies and they’re trying to have fun from their activity, and if it is not possible – they might stop. Another way is to make an attack more difficult, without any dirty things. For example, it is very easy to exploit a dump SQLi, but if it is a double-blind SQLi against non-typical RDBMS with many tricks and hacks for success, in this case most script kiddies just give up and leave us alone. Also we can use it for understanding motivation of an attacker. If they do not want to give up and continue their research – it is mean and we then have to deal with a real threat. So it can be a good feedback for us.

– Different honeypots have different purposes. Some of them are used for getting fresh versions of malicious code, exploits, etc. Some – for monitoring malicious activity. In my experiment I was trying to get real attackers, and I got a few – so it works. Of course it depends on the attacker type, skills, and luck. At least, honeypot can tell you what skills and motivation the attacker has. It is already more than just IDS alert.
– DDoS attacks are popular these days; how can honeypots help prevent or mitigate them?
– Interesting question. Actually, maybe it will work. For example, we can try to make a honeypot against DDoS on “application level”. We can try to cheat: for example, let’s make a balancer (L7) that forwards the “first” request (that emulates the activity of “processing” of something), but in a real-world scenario it will be just a fake, and all “first” requests will be going to black-hole with traffic analyzer. All real functionality starts from next steps, but if an attacker thinks that this first request is the most important, they can try to DDoS our service by using this “first request”. It is just an idea, and of course there are many “if’s”. But I think there is some field for research.
– Can one have no honeypot at all but still convince outsiders of it presence? Does knowing that the honeypot is there keep the bad guys out?
– I think it is “security through obscurity”, but against some types of attackers it can work, just like the alert: “Prohibited territory. Evil dog! Please get out!”
– Nowadays companies can be attacked by bad guys of different skill set – how do I choose which type of honeypot to employ?
– First of all, you need to understand what type of risks you have, what the attack surface for your system is. Is it web risks, or you have some services exposed to the Internet? When you have the answers, you can start to deploy honepot that looks like part of your system. And in my talk at BH2013 EU I described how we can detect different types of attackers by skills and motivation. It is all possible! So if we are talking about web risks, then custom-honeypots are the best solution, because there are no signatures for them.
– What is the typical honeypot now? What does it consist of and do?
– It can be deployed honeyd. It is used as IDS with less “false positives”.
– What about client-side honeypots that are not server based and detect client-side attacks? Are they rare? What are their advantages and disadvantages?
– Actually these types of honeypots are very popular in AntiVirus/Malware-hunting companies. It can be “bots” with client-side software which is surfing the Internet and looking for some new exploits, malware samples and malicious/compromised www pages.
– Do you advise creating your own honeypot or using already available solutions?
– Custom things are always better than the ‘default’ one. Anyway, you can customize known software for better results.
– Can you suggest any free or paid readymade honeypot?
– I am trying to use my own things, but I know that honeyd is a pretty useful thing in some cases.
– Should IDS include honeypots? Do we have combined solutions on the market now?
– It is possible. Actually there are different paradigms on how they work, so if they are working together it can help – a honeypot detects the fact of a succesfull attack on the honeypot, and IDS can help to understand which resource in our network is under attack.
– How widely are honeypots used with mobile environment and devices?
– I have no information about real usage, but there are some projects in this regard.
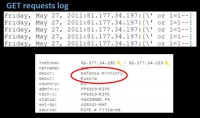
– How vulnerable are the attackers now? How often can I successfully hit them back with the same exploit?
– Depends on the attacker. If it is an operation against your company, then you do not have a big chance to exploit back; but if you use social engineering, you chances go up, because attackers are not expecting a ”hack back” thing these days. Against White-Hats/Script-Kiddies – you have a pretty good chance to hack them back. A bit less than in the case of “casual Internet user”, but it works. My experiment shows that my pretty simple PoC has 17% success on hacking back.
– Honeypots are becoming more and more popular, they have some similar patterns. How often do honeypots become targets themselves?
– I do not think that it makes sense. What is the point in hacking a honeypot? In most cases they are deployed in an isolated environment, so it is useless to spend time, money on hacking honepots. Only for fun.
– Can you suggest any anti-honeypot techniques?
– Fingerprints. The one and only thing – detect honeypot before you start wasting time hacking it.
– During you research you were able to catch some big fish like the Ministry of Defense of Russia. Could you please talk about it? How deep were they trying to dig? Did this case have any consequences?