What is Search Baron?
Whereas cybercrime is a dynamically changing territory, there are constants ‘hard-coded’ into malefactors’ repertoire regardless of this evolution. Browser hijacking is one of these invariable attack vectors. It’s not a destructive technique at all, but it has a huge monetization potential that lures malicious actors. Here’s a classic formula of this exploitation: a rogue app plus dodgy browser extension causing a redistribution of the victim’s web traffic, multiplied by advertising networks smoke-screened via a legit search engine – equals fraudulent profit.
Search Baron is an element of a massive ongoing campaign sticking with the above logic. Although it is often referred to as a virus or adware, the name was coined by victims and researchers based on the URL that appears in one’s browser as part of the redirect compromise. Specifically, those infected keep visiting junk sites and search engines they never opted for, with SearchBaron.com being a domain in transit. It is only visible for less than a second but plays a crucial role in the shady traffic capture scheme.
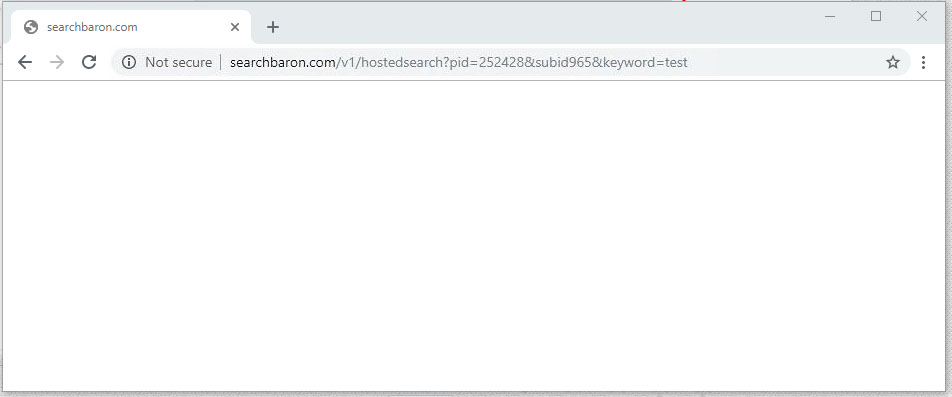
The main symptom of this hijack is that the prerogative of choosing a web search service is taken away from the victim. Every query entered in Google or in the browser’s location bar returns SearchBaron.com first and then the navigation is thrown to Bing.com through a series of in-between ad networks and cloud computing platforms such as Amazon AWS. It’s worth pointing out that the first-stage redirect URL will additionally have a number of IDs and sub-IDs, so the resulting address will assume a pattern similar to the following: SearchBaron.com/v1/hostedsearch?pid=[random digits]&subid[random digits]&keyword=[search term]. You may be curious why Bing, a legit and authoritative entity, could have possibly been added to this hoax. This is an attempt to veil the stratagem’s untoward effects and mitigate the awful impression from the whole rerouting madness going on. In the meanwhile, the crooks achieve their real goal by forcing momentary hits to traffic aggregator sources they are in cahoots with.What’s the function of SearchBaron.com in this conspiracy? It is a trigger used to intercept, dispatch, and allocate the unwitting victims’ Internet navigation activities in a peculiar way. This is done at the expense of regular users’ normal web experience, but the felons couldn’t care less if it affects a speedup of a MacBook user’s device and the overall experience.
How did Search Baron virus infect my Mac?
The ground zero of this infection’s distribution is an unethical co-promotion technique based on bundling. Packaged installation of several apps under one umbrella isn’t necessarily a malicious phenomenon. Ideally, it is a way for software devs to make profit while spreading their solutions free of charge. The gray side of this mechanism is that malware makers can embed their toxic programs into installers of popular freeware. The catch is that users may be unaware of the extra applications being pushed along the line, because the default setup option includes no indication of it.
An important thing to keep in mind is that the pest under consideration isn’t manifested as Search Baron in these dodgy installation wizards. Instead, the PUA (potentially unwanted application) is called Spaces. Also known as Spaces.app, this is a notorious Mac adware that maintains control of a user’s web browsing preferences and supervises the online search routine by staying tuned for queries the person enters. When such an event is identified, the sneaky program re-assigns the lookup process to SearchBaron.com. The latter then acts according to its predefined redirect algorithm, leading to Bing via a number of affiliated services.
Is Search Baron dangerous?
This hijacker is, for the most part, a nuisance rather than a serious threat. However, it is known to collect PII (personally identifiable information) as a byproduct of its operation inside a Mac computer. It logs details about the host system (macOS version, IP address, user geolocation) along with browsing-related data that speaks volumes about the victim’s lifestyle. The stealthily harvested info includes the visited sites, e-shopping preferences, and search terms. The individuals in charge of Search Baron campaign may be able to mishandle these statistics by displaying targeted malicious ads, carrying out phishing attacks, or selling the data to interested parties. All in all, the infection is definitely a threat to one’s privacy, although this aspect is obscured by the annoying and conspicuous symptoms in the web browser.
How do I remove Search Baron virus from Mac?

Although this threat manifests itself in the web browser only, it actually leaves a footprint across the system to maintain persistence. The subsection below will help you find and remove all the components of Search Baron virus manually. Keep in mind that some of its files are a no-brainer to spot, while a few may be hidden so that the cleanup is harder to complete than in a typical software uninstall situation.
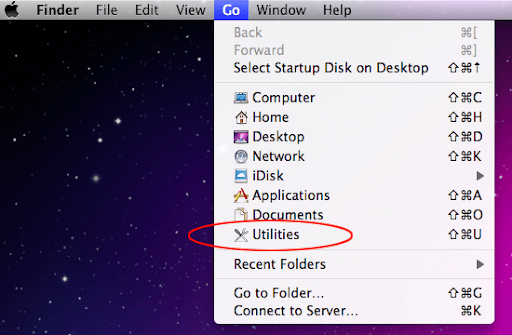
- Expand the Go menu in your Mac’s Finder and click the Utilities entry.

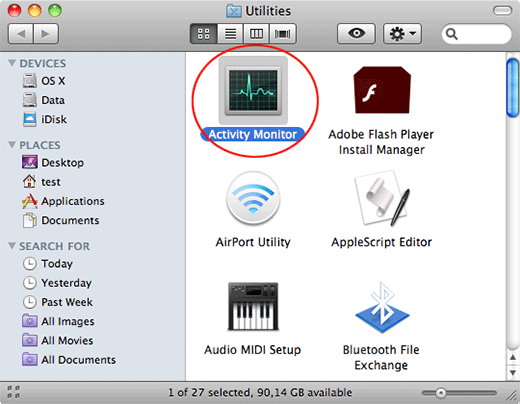
- Proceed to the Activity Monitor.

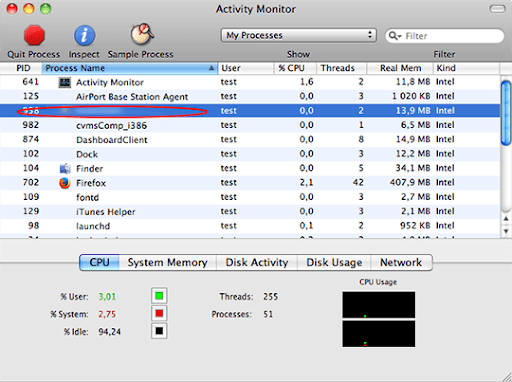
- Explore the Activity Monitor for processes that appear dubious and use up a good deal of the CPU. Be advised that the malicious executable isn’t necessarily named Search Baron or Spaces, so you’ll have to follow your intuition to an extent. If you find such a suspicious object, use the Quit Process option to terminate it. Confirm the action by clicking Force Quit on a follow-up prompt.
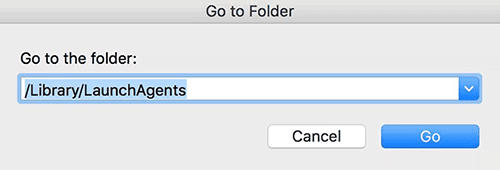
- In the Finder bar, click the Go icon and select Go to Folder in the list. Alternatively, you can press the Command+Shift+G key combo.
- Once the system search bar appears, type /Library/LaunchAgents in it and click Go.

- When the LaunchAgents folder is in front of you, look for suspicious files and drag them to the Trash. Note that the names of such malicious objects might appear to be unrelated to SearchBaron or Spaces adware. Here are a few examples of known-harmful files spawned by Mac viruses: com.mcp.agent.plist, com.pcv.herlperamc.plist, com.avickupd.plist, etc. Any items that don’t fit the mold of benign Mac files should be moved to the Trash immediately.
- Follow the same logic (Go to Folder feature) to open the directories called ~/Library/LaunchAgents, /Library/Application Support, and /Library/LaunchDaemons in turn. Look for suspicious files (see examples above) in each one of these folders and remove them.
- Now use the Go drop-down menu in the Finder again and choose Applications.

- Inspect the list of your applications for a potentially unwanted entity whose installation time co-occurred with the Search Baron issue. It’s most likely the Spaces.app or some random-named piece of software you don’t recollect installing recently. Once you find the unwelcome app, drag it to the Trash. Empty the Trash folder when done.

- Use the Finder to navigate to your System Preferences

- Proceed to Accounts and select Login Items. The system will display all user profiles created on your Mac as well as the programs executed automatically whenever your turn on your computer. Use the “minus” pictogram to delete the rogue account along with the sketchy item (e.g. Spaces) triggered at boot time.

- Uninstalling the harmful application is half the battle. It is a way to make sure that the symptoms won’t reappear after you implement the browser-level part of the repair. In the meanwhile, the SearchBaron.com redirect nasty continues to affect your preferred web browser and therefore you need to revert to the correct Internet surfing settings. Read the subsection below to find out how.
How do I stop SearchBaron.com redirects in the web browser?
Thankfully, you needn’t reinvent the wheel in terms of invalidating the adverse tweaks caused by the Search Baron virus in your browser. A tried-and-true technique is to reset the affected browser to its original defaults. On a side note, Apple has removed the “Reset Safari” button since the release of the Mac native browser’s version 9 back in 2015, so the procedure is now a bit more complex than a one-click experience (see below). Anyway, here’s a simple way to purge the most popular web browsers of the malicious influence:
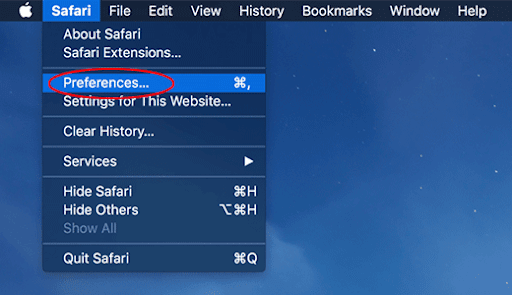
- Tidy up your Safari browser
- Select Preferences in the Safari menu and as illustrated below.

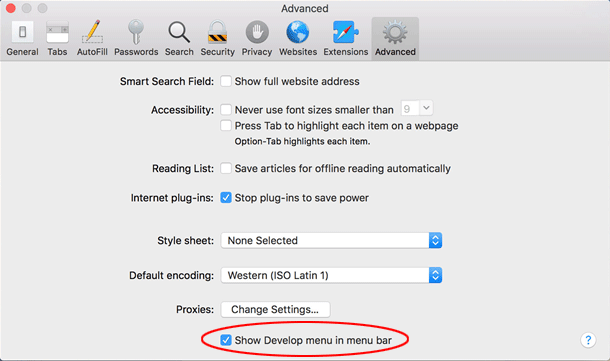
- Click the Advanced tab and put a checkmark next to the Show Develop menu in menu bar option.

- Click the Advanced tab and put a checkmark next to the Show Develop menu in menu bar option.

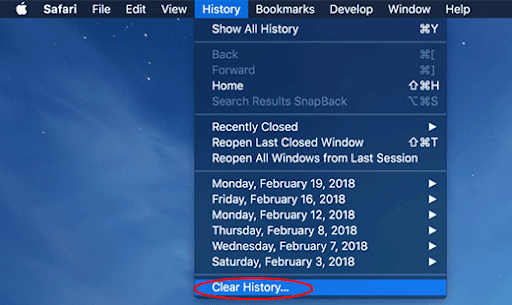
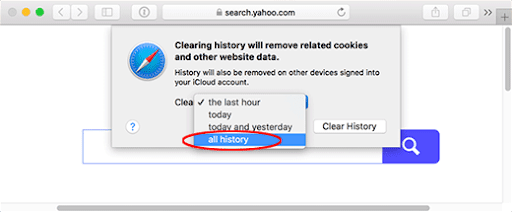
- Check if the browser is still being forwarded to SearchBaron.com. If it is, go back to the Safari menu bar, expand the History menu, and select the Clear History option as shown in the screenshot below.

- Customize the process using a follow-up dialog that allows you to define the period of time for which you want to remove cookies and other website data. It’s recommended that you select all history. Then, go ahead and click Clear History.

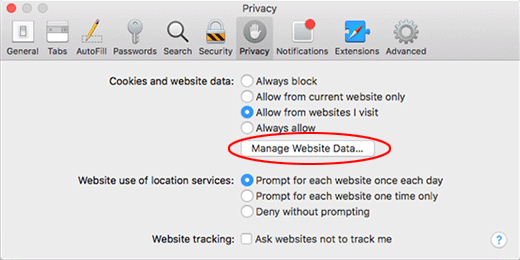
- If your Safari browser is being rerouted to the rogue URL regardless, go to the Preferences pane via the Safari menu bar again and hit the tab called Privacy. Find and click the Manage Website Data button.

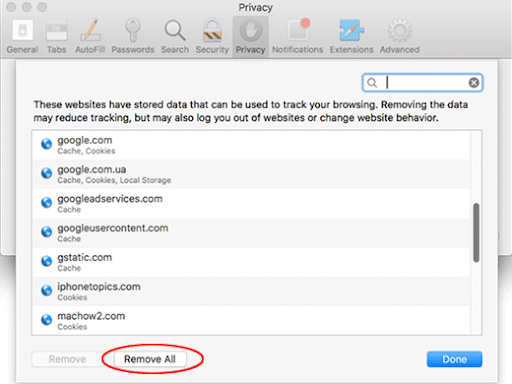
- Safari will display a list of all sites that have retained your online data. Click the Remove All button without a second thought. Once the information has been deleted, click Done at the bottom right.

- Select Preferences in the Safari menu and as illustrated below.
- Reset Google Chrome settings
- Open Chrome, click the Customize and control Google Chrome (⁝) icon in the upper right-hand part of the window, and select Settings in the drop-down list.
- Look for the button called Advanced and click it to access beyond the basic Chrome settings.
- In the Reset settings area, click the button that says Restore settings to their original defaults.

- All that’s left to do is click Reset settings on the respective dialog in case you are okay with the resulting changes listed there. Restart Chrome to make sure the benign tweaks take effect.
- Give Mozilla Firefox a tune up
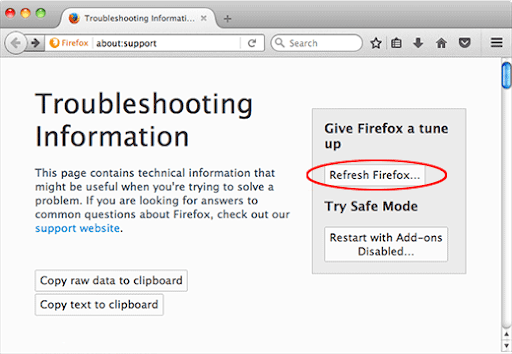
- Open Firefox, click Help, and select Troubleshooting Information in the list.
- Click the button called Refresh Firefox.

- The browser will trigger an extra popup dialog where you should confirm the reset action. When finished, restart Firefox and enjoy your web surfing without Search Baron virus messing around with it.
How do I make sure that Search Baron virus is gone?
Symptoms isolated to the browser are the tip of the iceberg. Search Baron and its associated malware can gain a foothold in the Mac beyond redirect activity alone. The drawback of manual removal is that there might be hidden leftovers of the threat that will reinstall it after what seems to be a successful cleanup. This isn’t necessarily the case, but you may want to double-check if you are in the clear.
Consider scanning your Mac with Combo Cleaner, an optimization and security app with a decent track record. It’s lightweight, and it can detect all prevalent forms of Mac malware in a snap. Here’s the how-to:
- Download and install Combo Cleaner
By downloading any software provided on this website you consent to the provisions listed in our Privacy Policy and Terms of Use. Be advised that Combo Cleaner scan is free, but you will have to buy its full (Premium) version to enable the virus removal feature.
- Open the Launchpad from your Mac’s Dock and click the Combo Cleaner icon to run the app. Wait for the tool to update its database of virus definitions and click the Start Combo Scan button.

- In addition to identifying malware and privacy issues, the app will inspect your Mac for junk files, duplicates, and large files you might no longer need. Deleting these redundant objects can release a good deal of disk space.

- Scrutinize the scan report. Hopefully, its results by the antivirus and privacy categories are blank and the verdict is “No Threats”, which means you are safe. If there are infections listed in the report, though, use the Remove Selected Items option to get rid of them.