What is Sodinokibi?
The ostensible chilling of the global ransomware climate is illusory, and the overall anticipation of the epidemic’s end turned out to be premature. Whereas mainstream crypto viruses actually saw a dramatic decline over the past two years or so, a more serious adversary emerged that is spreading mayhem in a somewhat different way. Instead of firing shots in the dark in an attempt to cover maximum victim audiences, well-motivated and sophisticated groups of cyber extortionists started zeroing in on big prey via targeted raids. Large businesses, healthcare institutions, and local governments are at risk now in 2019 more than ever before. The ransomware dubbed Sodinokibi, also known as Sodin or REvil, exemplifies this evolutionary transition in the nasty e-crime model.
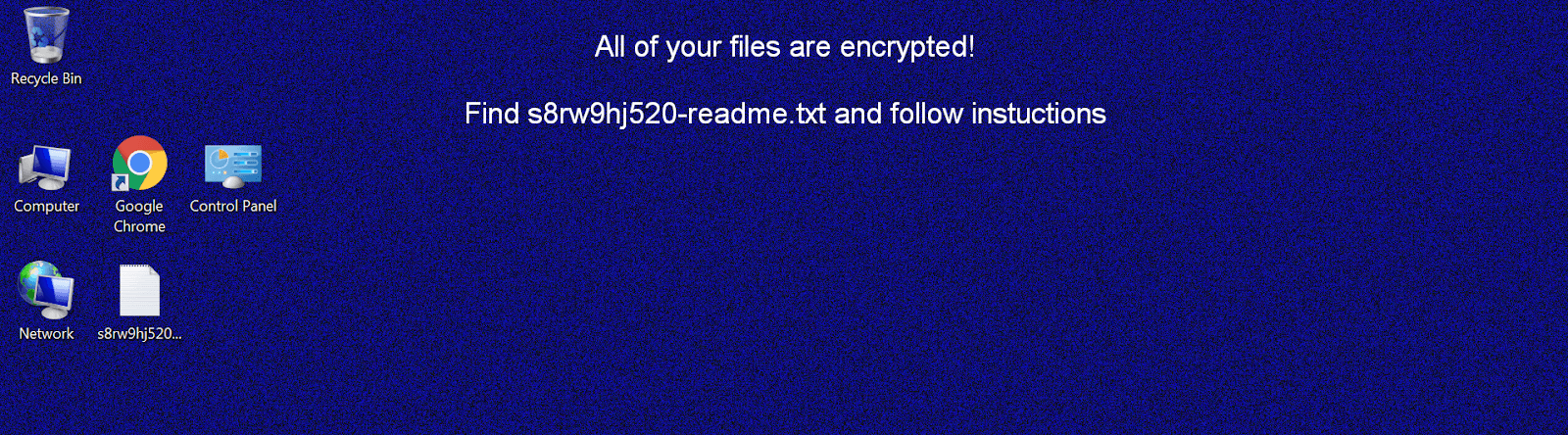
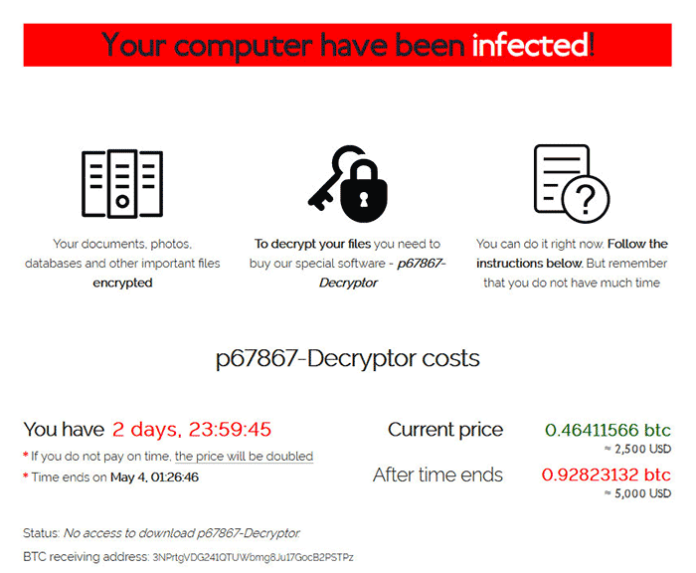
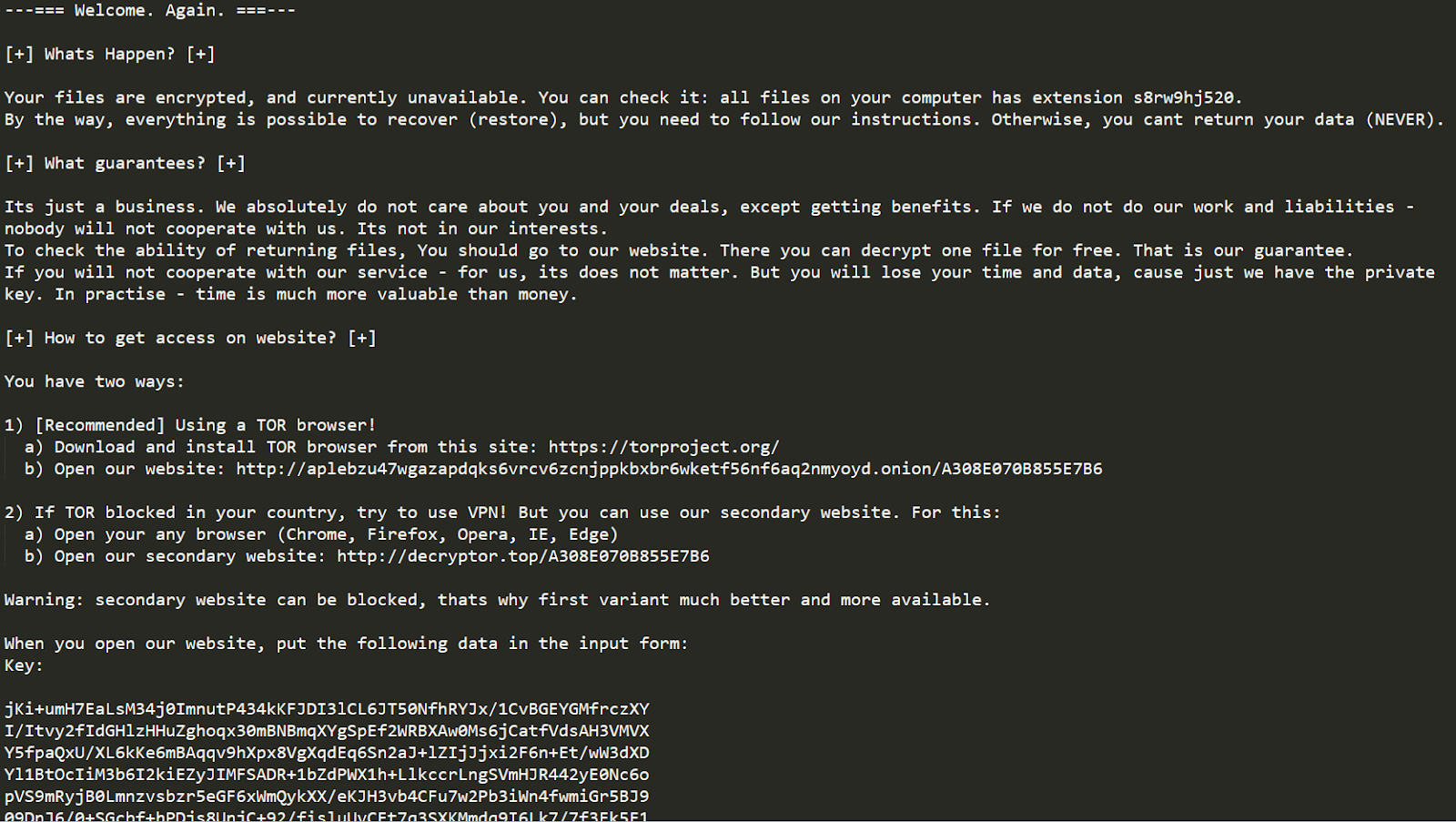
For a start, here is a quick summary on this threat. Its distributors focus on hitting Windows based computer networks, with individual users being occasional victims as well. When inside an enterprise environment, Sodinokibi easily evades detection while obtaining privileges high enough to spread laterally within it. Having encrypted the most valuable data, the ransomware appends a unique alphanumeric extension to every file. It also replaces the desktop wallpaper with an alert saying that all the information has been encrypted and providing a reference to a ransom note named according to the following pattern: [random]-readme.txt or [random]-HOW-TO-DECRYPT.txt, where the prefix matches the extension assigned to the hostage files.
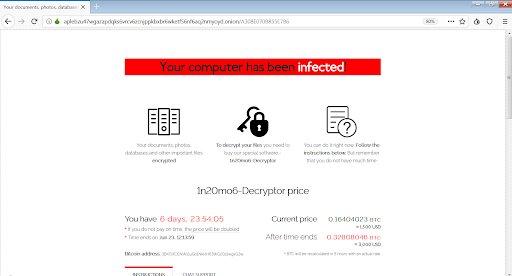
The attackers’ recovery manual instructs the user to visit a personal Tor page or, if it’s inaccessible in their country, to go to a “secondary website” using a regular web browser. The payment page instructs the victim to send $1,500-$2,500 worth of Bitcoin cryptocurrency to the criminals’ BTC wallet. After a deadline of up to seven days expires, the amount doubles. It’s worth emphasizing that the size of the ransom per large organization can be several times higher than that.
Judging by the basic symptoms and tactics alone, it may appear that Sodinokibi is a run-of-the-mill ransomware with nothing special under the hood. This is a misconception. In fact, the strain features a number of characteristics that make it really stand out. One of these offbeat traits manifests itself in the contamination chain. In April 2019, when this infection was discovered, the only spreading mechanism boiled down to exploiting a security loophole in Oracle WebLogic Server software. Although it was an effective and sneaky method of trespass, the range of potential victims was limited. As time went by, the crooks in charge of Sodinokibi have enhanced their propagation logic with more techniques, including exploit kits, RDP compromise, phishing, and malspam (malicious spam).
The more “exotic” tricks involve breaches of well-known MSPs (managed service providers), as was the case with an attack against Kaseya RMM last June. Yet another vector, referred to as SWC (strategic web compromise), relies on hacking popular software vendors’ websites and replacing the original app installers with booby-trapped copies that end up dropping the ransomware payload onto users’ computers. As if this multitude of entry points weren’t enough, the malefactors have been also duping people to download the harmful code by redirecting them to malicious sites from compromised Internet forums.
Sodinokibi ransomware is being distributed by numerous different groups of perpetrators. This approach is known as RaaS, which stands for Ransomware-as-a-Service. Its bears a close resemblance to a legit affiliate network, except that the underlying activities are shady to the bone. The authors of the deleterious program get a 30-40% share of all ransoms paid by victims, and the remaining amount is earned by the threat actors who deposited the infection onto machines. As per analysts’ reports, many of the affiliates spreading Sodinokibi used to be part of the RaaS network propping the advances of GandCrab, a now-extinct ransomware family that had dominated the ecosystem before the lineage under scrutiny surfaced. Moreover, there are evident similarities in the code of these two infections, which means they may have been crafted by the same developers.
At the time of writing, Sodinokibi is one of the world’s top ransomware threats in terms of technical complexity, AV evasion efficiency, victims made, and the total amount of ransoms collected from them. Here’s just one episode of this rampant campaign: in mid-August 2019, the black hats plagued 22 local governments in Texas by means of compromising a managed service provider responsible for IT tech support in the affected towns. The attackers’ demands were as high as $2.5 million. Pair that with an ever-increasing number of Sodinokibi victims, and the big picture gets scary. In case this ransomware has impacted a computer or enterprise network, the predictions regarding successful free recovery of the data aren’t very optimistic. However, a few forensic techniques should definitely be applied to see what information, if any, can be reinstated without submitting a fortune to the attackers.
Sodinokibi ransomware removal
As counterintuitive as it is, removal of this particular threat is not too complicated unlike the cleanup scenarios for screen lockers, which represent another group of ransomware infections on the loose. The main challenge in regards to Sodinokibi/REvil ransomware is getting personal files back without having to do what the extortionists want. Basically, this means you can get rid of the malady using efficient security software without much of a hindrance, but options for recovering the encrypted data are a matter of a separate discussion, which we will touch upon in this guide as well.
Let’s now outline a rather easy and perfectly effective way of ransomware removal from a contaminated computer. Please follow the directions below step by step:
- Download and install HitmanPro.Alert
- Open the program, click on the Scan computer button and wait for the scan to be completed
- When HitmanPro.Alert comes up with the scan report, make sure the Delete option is selected next to the ransomware entry and other threats on the list, and get the infections eliminated by clicking on the Next button

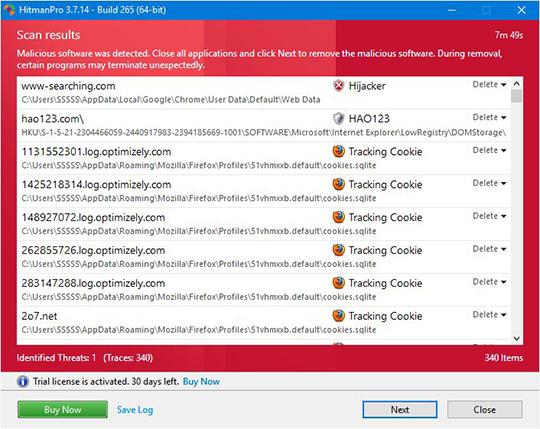
Now you’ve got both some good and bad news. On the one hand, Sodinokibi ransomware is gone from your computer and won’t do any further damage. On the other, your files are still encrypted, since elimination of the malware proper does not undo its previous misdemeanors. In the next section of this guide we will highlight methods that may help you restore your data.
Recover encrypted files using Shadow Copies
As previously mentioned, despite successful removal of the Sodinokibi virus, the compromised files remain encrypted. While it does not appear possible to obtain the key for decryption in this case even with brute-forcing, you can try to restore previous versions of these files either using the native Windows functionality or the application called Shadow Explorer. Please note that this method is only applicable in case you have System Restore enabled on your PC, and the versions of the files that you can recover this way may not be the most recent. It’s definitely worth a try, though.
Getting your files back using Previous Versions functionality
Windows provides a feature where you can right-click on an arbitrary file, select Properties and choose the tab called Previous Versions. Having done that for a particular file, you will view all versions of it that were previously backed up and stored by the so-called Volume Shadow Copy Service (VSS). The tab also provides the history of these backups by date.
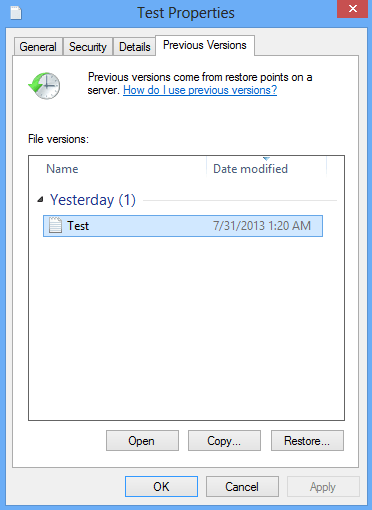
In order to restore the needed version of the file, click on the Copy button and then select the location to which this file is to be restored. In case you would like to replace the existing file with its restored version, click the Restore button instead. Conveniently enough, you can have whole folders restored the same way.
Restoring encrypted data with Shadow Explorer utility
Besides the built-in Windows functionality highlighted above, you can use an application that will restore previous version of entire folders for you. It’s called ShadowExplorer. Once you download and launch this program, it will display all of your drives as well as a list of dates when Shadow Copies were generated. Simply pick the desired drive and date for restoration, as shown on the following screenshot:
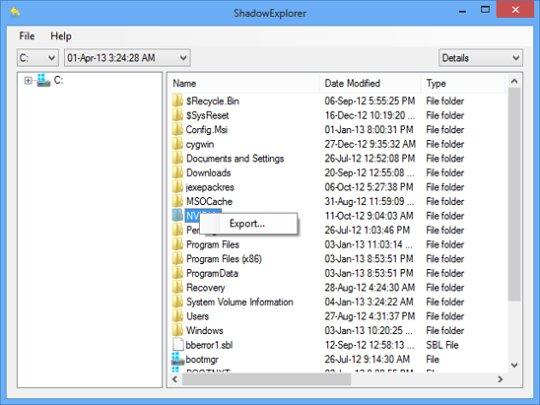
Right-click on the directory you wish to restore and choose Export in the context menu. This will be followed by a request to indicate where you would like to restore the information to.
Use automatic Recuva recovery software
It might sound surprising, but Sodinokibi ransomware does not encrypt one’s actual files. It deletes them. What does get encrypted is the copies. This brings us to the point where a specific type of software can be used for dragging the original data out of memory, where it ended up after the erasure. Efficient recovery tools can work wonders in these ransomware scenarios.
Download and install Recuva by Piriform to give this restoration vector a shot. By running a computer scan with Recuva, you will get a list of all recoverable files and be able to reinstate them to their original location or another place of choice.

Bottom line
The Sodinokibi crypto virus poses a critical risk to end users’ and organizations’ proprietary data, therefore the focus security-wise should be made on prevention. In this context, some basic precautions can do the trick: train your personnel to refrain from opening email attachments from unknown senders, apply OS and software patches as soon as they are released, and schedule regular antivirus software updates. Before deciding to collaborate with MSPs (managed service providers), businesses should ask for evidence of proper security practices to make sure the partnering entity doesn’t become a loophole into enterprise network. Most importantly, performing data backups is the most reliable way to avoid the adverse aftermath of this attack.




























