Peruse the article to learn the profile of Bit Cryptor ransomware, get fresh updates on the issue and learn how to prevent the adverse effects of this attack.
Bit Cryptor is an uncompromising computer infection that follows a well-trodden path of the notorious ransomware hoaxes. This sample was first reported in early May 2015, so it’s new in terms of the timing but fairly conservative as far as features and tactics are concerned. In fact, it was found to represent the same family as the once newsmaking CoinVault virus. Similarly to its ill-famed prototype, Bit Cryptor encrypts its victims’ files with AES-256 standard, consequently success of the decryption relies on the private key and the initializing vector (IV) data. Because these parameters are generated for each computer individually and stored on a remote server that’s run by the criminals, the user ends up being trapped between the horns of a dilemma: to pay the ransom or try restoring the stolen information using alternative workarounds, which isn’t an efficient endeavor, to be frank.
Speaking of the latter option, it is significantly tangled by the fact that the ransomware wipes out the files’ Shadow Copies, a native Windows feature that makes and stores snapshots of data at certain intervals. Bit Cryptor also goes more advanced than its forerunner in the context of the attack surface. Not only does it encrypt data on the single machine that got infected in the first place, but it also hits all connected nodes on the network. Another novelty is about the types of files being targeted: the virus won’t meddle with the objects in operating system directories, such as Program Data, Program Files, Appdata, Recycle Bin, Temp, etc. Instead, the focus is strictly on the user’s personal files that meet the criterion of the around 90 different extensions being sought. Bit Cryptor leverages advanced AV evasion techniques by blocking the executables that tend to be associated with security software. Furthermore, to prevent manual troubleshooting on the victim’s end, the ransomware terminates such Windows processes as ‘cmd’, ‘msconfig’, ‘rstrui’, and ‘regedit’ once they are launched.
” Bit Cryptor leverages advanced AV evasion techniques. “
There is no single vector for contamination used by Bit Cryptor. The malicious code injection might take place due to a social engineering attack or the activity of an exploit kit. Some reports say that users of crytpocurrency exchanges where targeted by this malware. To be on the safe side, it is recommended to visit sites like cryptohead.io and read useful tips on how to buy and sell crypto safely. Whereas security awareness and plain caution might prevent the former workflow and keep the user from opening some contagious email attachment, the latter scenario makes the machine a low-hanging fruit.
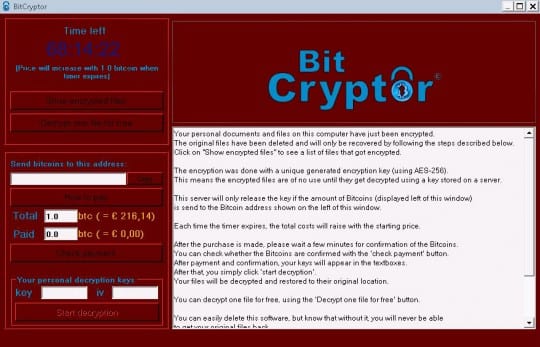
On the initial stage of the compromise, the virus adds its process bclock.exe to the startup list, scans the HDD for files of interest, deletes their previous versions if any, and encrypts them. It then changes the desktop wallpaper to a spooky dark image reading “Your files have been encrypted”. The main console of the malign program provides essential details of the attack and contains a number of clickable options, including the “Show encrypted files” and “Decrypt one file for free” buttons. The GUI also displays a unique Bitcoin address to which the ransom of 1 Bitcoin must be paid for file recovery. The clock ticking at the top left counts down 72 hours (3 days) before the ransom increases by 1 Bitcoin.
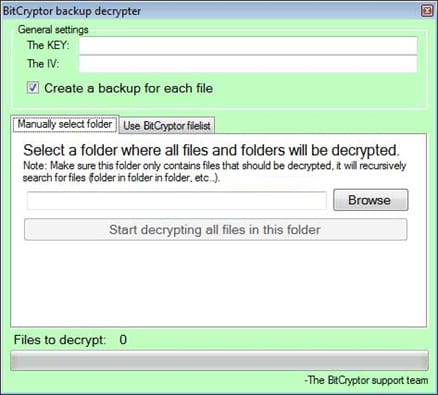
Essentially, what happens if the victim does submit the payment is they are provided with two files: one with the personal decryption key along with the IV, and the other being a ZIP archive with a tool called “BitCryptor backup decrypter”. Reportedly, file recovery actually works if the ransom is sent to the criminals, and yet that’s not a very pleasing thing to know after you got ripped off.
It’s hard to give any actionable advice in this situation. BitCryptor, regretfully, is good at what it was designed for. It infiltrates computers surreptitiously and leverages a crypto standard that’s nearly impossible to crack. The decryption key, therefore, can only be made available if you give in to the bad guys – period. To top it all off, Shadow Copies of the files get automatically deleted, so one of the widely recommended workarounds will be to no avail. Although this does sound like doom and gloom for the most part, some preemptive action can save you the trouble of facing the hard choice – to pay or not to pay. Keeping data backups in the cloud, making sure potentially vulnerable software is up to date, and running reliable antimalware are the measures that will make the average user’s day.