
The Metropolitan British Police virus is one of the series of sophisticated geographically localized ransomware threats (FBI MoneyPak, PCeU malware) affecting computers at a steadily increasing rate for months now. The large-scale campaign behind this infection involves a complex infrastructure of web exploit kits and intricate cashout services that allow the cybercriminals to stay afloat and prosper in their malicious underground endeavors. The prevailing method being leveraged for distributing this malware has to do with exploiting software vulnerabilities on the targeted PCs and dropping a malign object such as the Reveton/Citadel Trojan which was designed to aggressively lock user access to Windows. The infection routine is typically obfuscated so that the victim stays unaware of the menace until the machine is actually blocked.
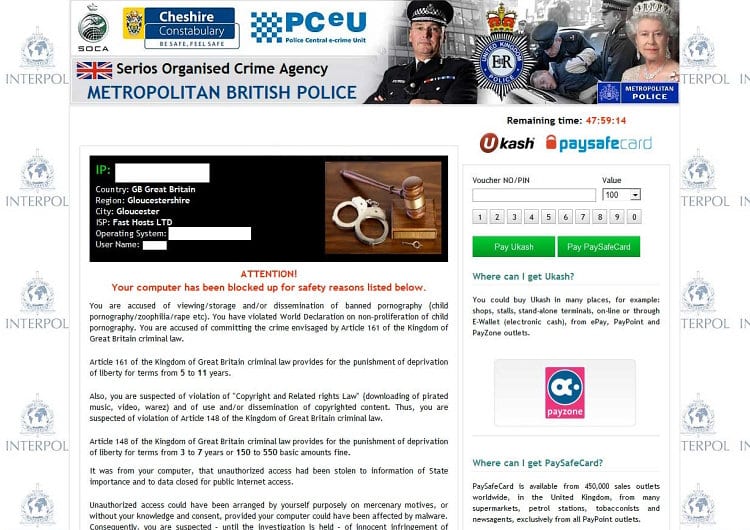
Also known as the Serios (misspelled ‘Serious’) Organised Crime Agency (SOCA) virus, this ransomware displays a fake lock screen whenever the victim starts the contaminated PC. The message on it reads: “Attention! Your computer has been blocked up for safety reasons,” being followed by a list of possible cyber offenses such as “viewing/storage and/or dissemination of banned pornography”, “violation of Copyright and Related Rights law”, etc. All of this misinformation is meant to convince the user to pay a fine of 100GBP, which is stated to be the sole possible condition for the system to be unlocked. Being driven by the intent to stay anonymous and avoid being busted, the fraudsters have integrated a ‘suitable’ payment method meeting the above purposes: Ukash or Paysafecard – these denote prepaid cards that can be bought at a variety of places (stores, standalone terminals, etc.) and contain a code which is to be entered into the field embedded in the right-hand part of the block page.
Perhaps the most judicious advice with regard to the Metropolitan British Police virus is to refrain from paying the demanded fine. The message generated by this ransomware is in no way related to any genuine British law enforcement agency, nor should the information therein be trusted.
Metropolitan British Police virus: the key symptoms
Unlike some other types of malicious software such as rootkits, password-stealing Trojans or keyloggers, the Metropolitan British Police virus is impossible to miss on a PC it infected: it gets to completely control access to Windows by displaying a bogus warning once the machine boots. This version also differs from the Police Central e-Crime Unit and the FBI Moneypak malware in that it was not found to gain webcam access on the targeted system. However, what this ransomware does in the background might be more than what the victim sees:
- Preventing security software from executing:
Whichever antivirus or Internet security software you are using, it will not keep the virus from doing its job once it’s already inside, because the corresponding processes get blocked. Containment of this malware is therefore beyond the regular AV activity after the infiltration actually happened. - Unauthorized computer access:
With this ransom virus on board, your system is an easy-to-hit target for cybercriminals who might harvest your private data for unethical purposes, including financial compromise. This fact makes it yet more important to eliminate the malware completely and as soon as possible.
Metropolitan British Police malware removal
Since the PC is literally locked, extermination of this threat is unfortunately not a matter of using conventional security software in the regular way, not to mention manual deletion of the files and system registry information added by the ransomware.
Therefore, having conducted an in-depth analysis of this malware, we came up with the removal tactics that proved to be effective for getting rid of the Metropolitan British Police bug.
For carrying out this removal procedure, you will need a USB drive to further launch the cleanup software from. Please note that all the data on this USB drive will be lost, so make sure you back it up before proceeding.
Metropolitan British Police virus removal using HitmanPro.Kickstart
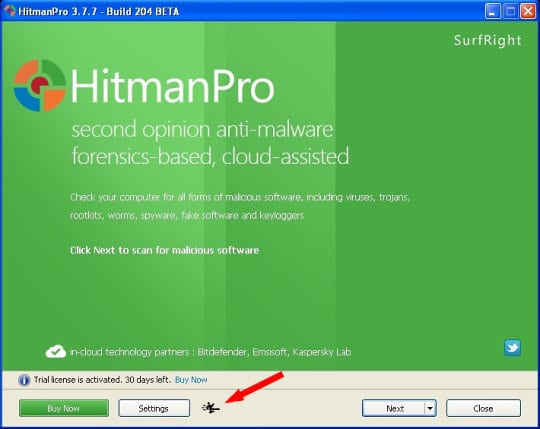
- Download HitmanPro software to a computer that is not affected by the virus and save it to your Desktop. Before performing the download, be sure to select the version according to the bit-type of your Windows operating system (32- or 64-bit).
- Plug in the USB drive that you are going to use for installing HitmanPro.Kickstart. Having inserted the thumb drive, double-click on the HitmanPro icon on your Desktop. The program’s main Window will appear. Please click on the kicker button as indicated by the red arrow on the screenshot below.
-
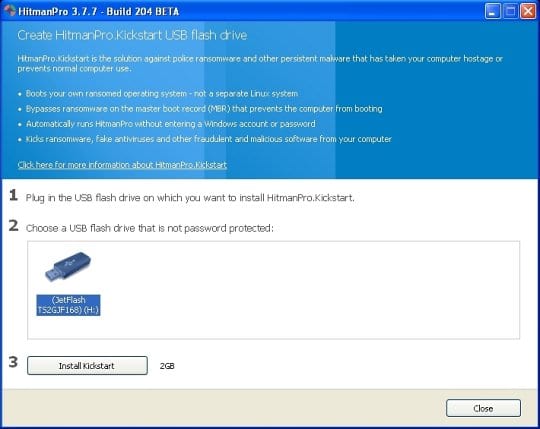
You will now see a window that will guide you all the way through creating the HitmanPro.Kickstart USB flash drive. Select the right USB drive by clicking on it in the corresponding field, and click the Install Kickstart button.
The software will ask you whether the USB drive contains any important files (all of them will be erased). If there are none, click Yes on the alert. This will automatically initiate the install process. When it completes, click Close button. - Remove the USB drive and insert it into the computer infected with the the Metropolitan British Police virus.
-
When it is inserted, turn off the infested PC and switch it back on. As the computer is beginning launch, take a good look at the boot screen to find the key that should be pressed for accessing the Boot Menu or BIOS Setup. Please note that these keys may be different on different computer models. For entering the Boot Menu, those are mainly F10, F11, F12 or Esc buttons. The ones for BIOS Setup are usually Del or F2.
Having determined the appropriate key for Boot Menu access, reboot and start hitting that key repeatedly as the PC is beginning to load. When in the Boot Menu, use its prompts to select the drive you want to boot your computer from, i.e. USB drive. -
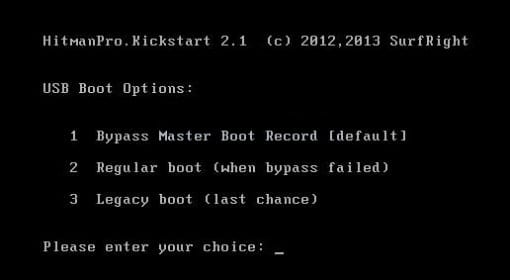
Now your PC will boot from the USB drive and load the HitmanPro.Kickstart saved to the memory stick. You will see a screen requesting you to choose USB Boot Options.
You should press 1 as your choice. Doing so will be followed by Windows starting to load. -
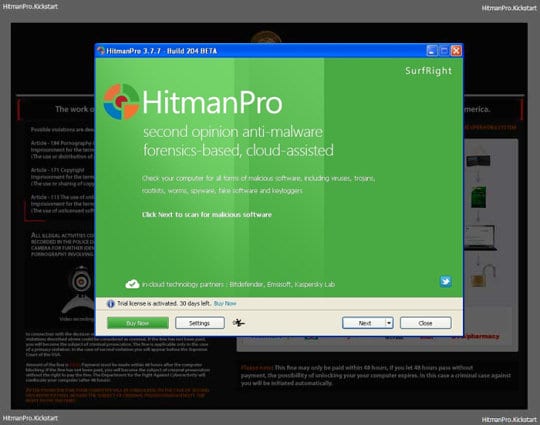
Right after Windows launches, the fake Royal Canadian Mounted Police block screen will appear as it did before, however in 15-20 seconds the HitmanPro main console will pop up on top of that.
Please click Next on the program’s GUI. -
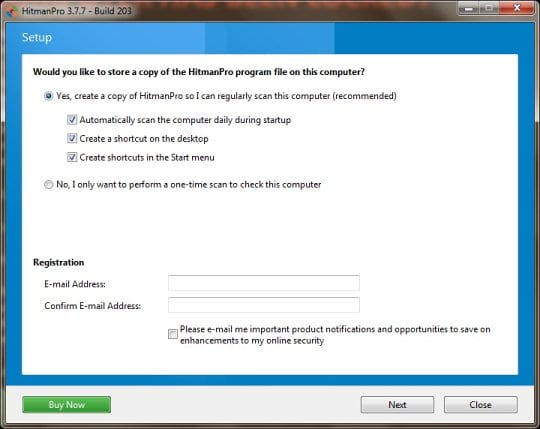
On HitmanPro’s setup screen that appears, we recommend leaving the default installation settings as shown on the following screenshot:
Please click Next.

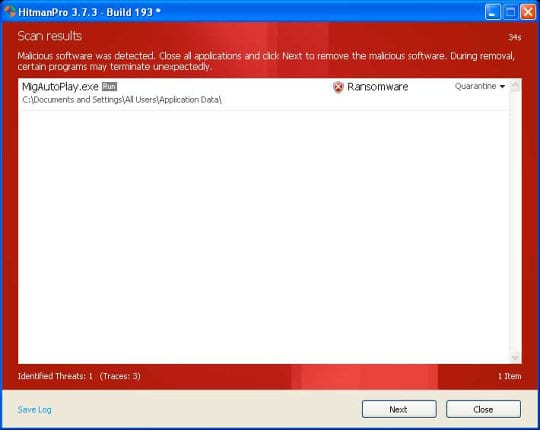
- SurfRight HitmanPro will now start a virus scan. Having completed the scan, the utility will come up with a report listing the detected threats.
- To get the spotted infections eliminated from your system, click Next. After the removal routine is complete, choose the Reboot option on the subsequent screen. Your computer will restart as usual. The Metropolitan British Police virus is no longer affecting your system. If you are not certain your current antivirus can prevent such infections from getting through in the future, you might want to consider upgrading to HitmanPro licensed version.
Metropolitan British Police virus removal using System Restore
This cleanup method allows restoring your operating system to the time period when it was not contaminated with the Metropolitan British Police ransomware. This procedure will not lead to loss of any files. To perform system restore, please stick to the following steps:
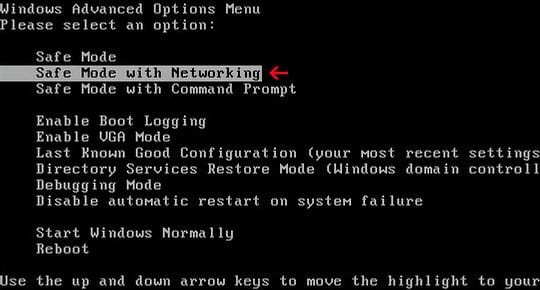
- When the infected computer is starting to load, tap F8 on your keyboard repeatedly to open up Windows Advanced Options Menu. When on this screen, use the arrow keys to highlight Safe Mode with Command Prompt, and hit Enter.
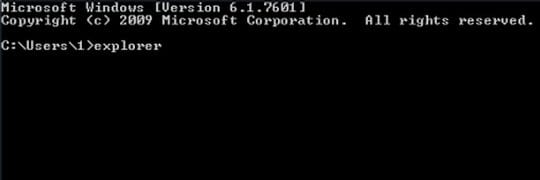
- Once the Command Prompt screen opens, type explorer and press Enter. Be advised this needs to be done quickly (within 2-3 seconds) or else the malware will not allow you to type anymore and you will have to start the process over.
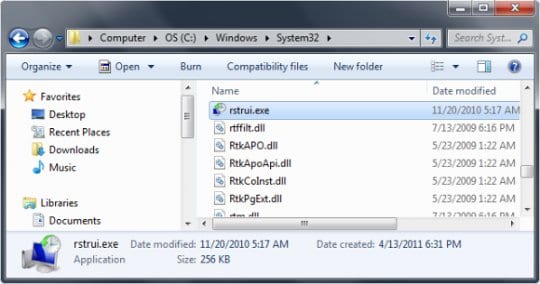
- In Windows Explorer, browse to the following path:
On Windows XP: C:\windows\system32\restore\rstrui.exe and hit Enter
On Windows Vista / 7: C:\windows\system32\rstrui.exe and hit Enter
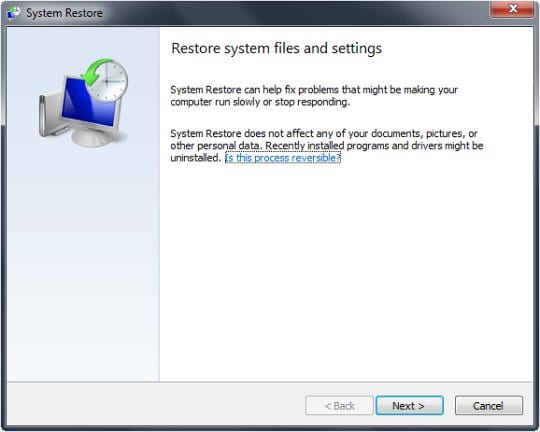
- Using the System Restore prompts, get your system restored to the date when it was unaffected by the ransomware virus.
Download, install and run reliable security software to get effective protection from cyber threats further on.

At the end of the day, it’s absolutely critical to realize that keeping your software up-to-date can prevent such infections from getting in, and this does not only apply to antivirus software. As the recent research shows, the greater amount of contaminations take place due to exploiting the vulnerabilities in outdated Java and PDF software. So, this is an aspect definitely worth taking into account.




























