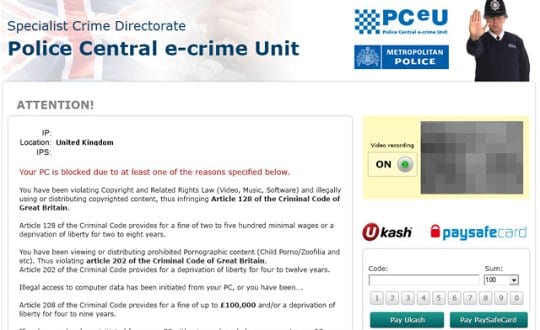
Following the influx of the FBI MoneyPak ransomware variants, yet another type of extortion technique came to be in June 2012, pretending to emanate from the Police Central e-Crime Unit, part of the British Metropolitan Police Service. Mainly targeting UK users through determining the victim’s IP location, the virus displays a fake Windows block screen on behalf of the above-mentioned law enforcement agency and lists possible cybercrime offenses that the user is allegedly guilty of. To settle down the ‘case’, the ransomware suggests that the victim pays a fine of 100 Euro for the completely hijacked computer to be unlocked. The extorted payment is to be submitted via Ukash or Paysafecard prepaid services by entering a corresponding code from a purchased card into the block page.
The prevalent known channel that the fraudsters have been utilizing for distributing the Police Central e-Crime Unit ransomware has to do with web exploit toolkits, such as BlackHole, as well as the infection known as Trend DNSChanger Bot, offspring of the infamous DNSChanger whose infrastructure was taken down by the FBI in 2011 and resulted in a number of arrests. The way victims get infected is typically through exploiting software vulnerabilities, mainly those in Java – yet another good reason for the average user to run regular Java updates.
PCeU Ukash virus: versions and screenshots
There are two known variants of the Police Central e-Crime Unit fraudware: one based on Win32/Weelsof infection, and the other making use of the notoriously ubiquitous Reveton Trojan. Whereas the former pretends to originate from Metropolitan Police proper as the generic institution, the latter tends to get somewhat more narrow and specific in terms of the purported law enforcement subdivision, stating that it’s being generated by the Specialist Crime Directorate. Other than the list of criminal charges indicated on the hijack screens, the exhibited routine is identical: the virus jacks up the targeted PC, displays false accusations, and demands a fine payment.
Here is what the block pages look like:
Symptoms of being infected with PCeU ransomware
Along with obvious inability to use the infected computer due to the fake police warning showing up right after system startup, the malware is known to also do the following:
- Webcam control:
The virus accesses the webcam on the infested PC and displays a streaming video of what’s around. This ‘feature’ is hard-coded into the ransomware apparently to add persuasiveness and intimidate the victim further. In case there is no webcam connected or built-in, the ‘Video Recording’ field on the hijack screen will be blank. - Disabling security software:
The malware prevents any system processes associated with legit antivirus, antispyware, Internet security software, etc. installed on the targeted machine from getting executed.
Police Central e-Crime Unit virus removal
Due to specificity of this infection, standard cleanup through the use of security software is barely applicable. Likewise, manual removal is considerably aggravated because of inability to access system directories where the virus embeds its components.
Thus, having thoroughly analyzed this malware, we came up with a number of removal methods that proved to be the most efficient for complete extermination of the PCeU Ukash virus.
PCeU virus removal using HitmanPro.Kickstart
For carrying out this removal procedure, you will need a USB drive to further launch the cleanup software from. Please note that all the data on this USB drive will be lost, so make sure you back it up before proceeding.
- Download HitmanPro software to a computer that is not affected by the virus and save it to your Desktop. Before performing the download, be sure to select the version according to the bit-type of your Windows operating system (32- or 64-bit).
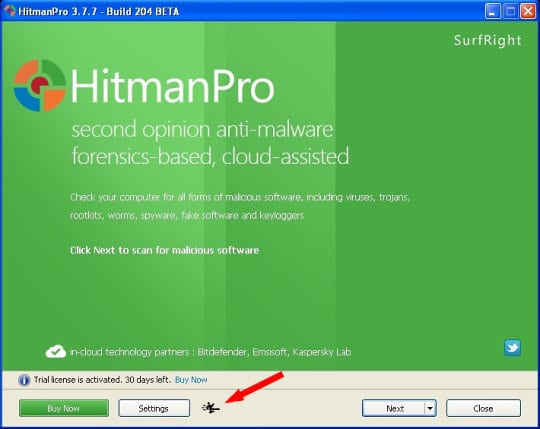
- Plug in the USB drive that you are going to use for installing HitmanPro.Kickstart. Having inserted the thumb drive, double-click on the HitmanPro icon on your Desktop. The program’s main Window will appear. Please click on the kicker button as indicated by the red arrow on the screenshot below.
-
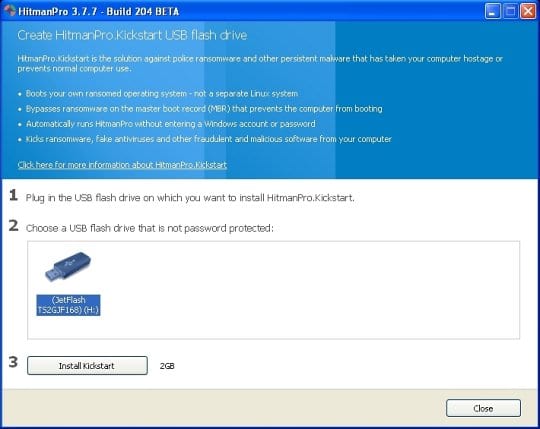
You will now see a window that will guide you all the way through creating the HitmanPro.Kickstart USB flash drive. Select the right USB drive by clicking on it in the corresponding field, and click the Install Kickstart button.
The software will ask you whether the USB drive contains any important files (all of them will be erased). If there are none, click Yes on the alert. This will automatically initiate the install process. When it completes, click Close button. - Remove the USB drive and insert it into the computer infected with the PCeU virus.
-
When it is inserted, turn off the infested PC and switch it back on. As the computer is beginning launch, take a good look at the boot screen to find the key that should be pressed for accessing the Boot Menu or BIOS Setup. Please note that these keys may be different on different computer models. For entering the Boot Menu, those are mainly F10, F11, F12 or Esc buttons. The ones for BIOS Setup are usually Del or F2.
Having determined the appropriate key for Boot Menu access, reboot and start hitting that key repeatedly as the PC is beginning to load. When in the Boot Menu, use its prompts to select the drive you want to boot your computer from, i.e. USB drive. -
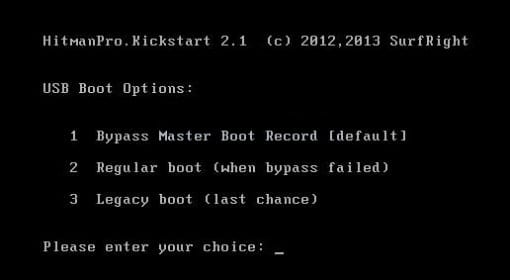
Now your PC will boot from the USB drive and load the HitmanPro.Kickstart saved to the memory stick. You will see a screen requesting you to choose USB Boot Options.
You should press 1 as your choice. Doing so will be followed by Windows starting to load. -
Right after Windows launches, the fake Royal Canadian Mounted Police block screen will appear as it did before, however in 15-20 seconds the HitmanPro main console will pop up on top of that.
Please click Next on the program’s GUI. -
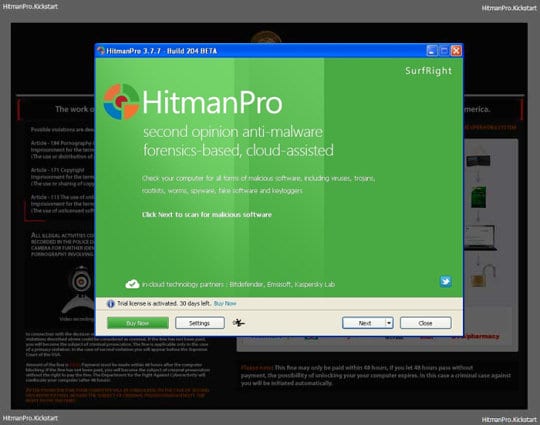
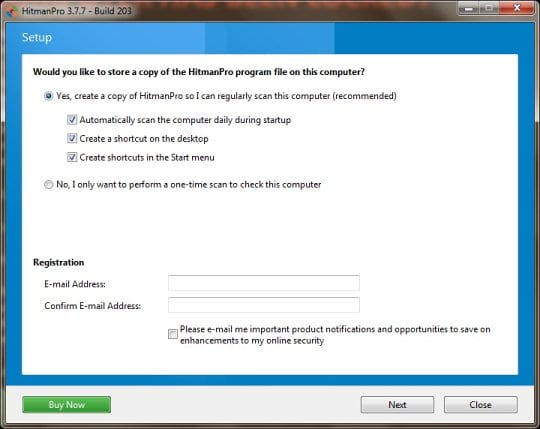
On HitmanPro’s setup screen that appears, we recommend leaving the default installation settings as shown on the following screenshot:
Please click Next.

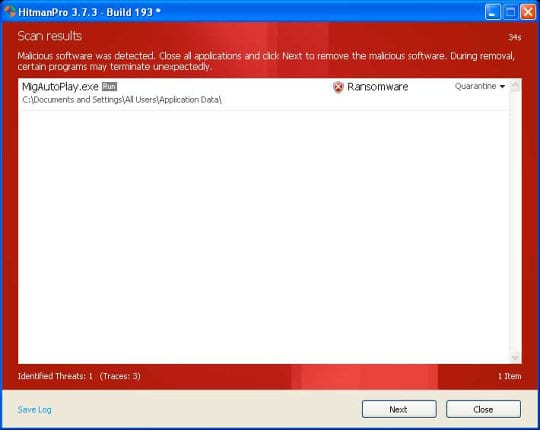
- SurfRight HitmanPro will now start a virus scan. Having completed the scan, the utility will come up with a report listing the detected threats.
- To get the spotted infections eliminated from your system, click Next. After the removal routine is complete, choose the Reboot option on the subsequent screen. Your computer will restart as usual. The PCeU Ukash virus is no longer affecting your system. If you are not certain your current antivirus can prevent such infections from getting through in the future, you might want to consider upgrading to HitmanPro licensed version.
PCeU virus removal using System Restore
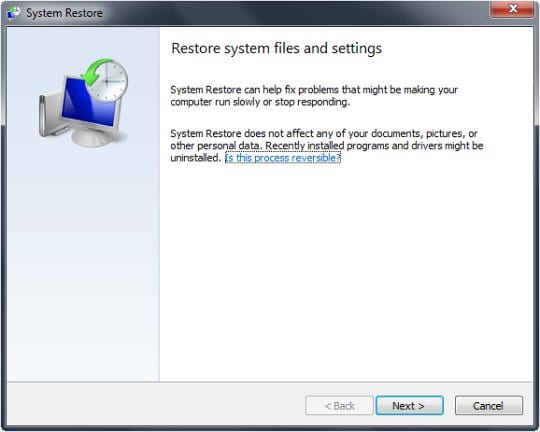
This cleanup method allows restoring your operating system to the time period when it was not contaminated with the Police Central e-Crime Unit ransomware. This procedure will not lead to loss of any files. To perform system restore, please stick to the following steps:
- When the infected computer is starting to load, tap F8 on your keyboard repeatedly to open up Windows Advanced Options Menu. When on this screen, use the arrow keys to highlight Safe Mode with Command Prompt, and hit Enter.
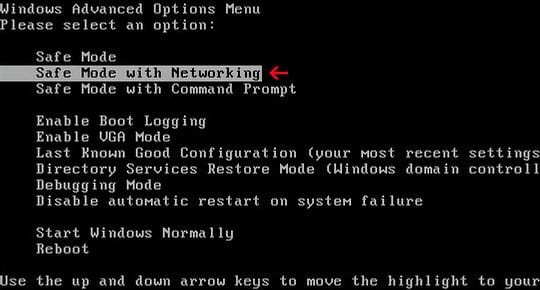
- Once the Command Prompt screen opens, type explorer and press Enter. Be advised this needs to be done quickly (within 2-3 seconds) or else the PCeU virus will not allow you to type anymore and you will have to start the process over.
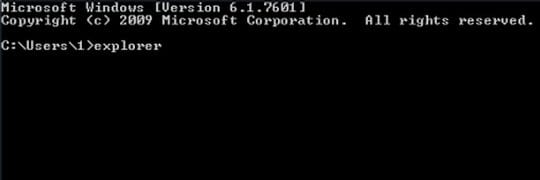
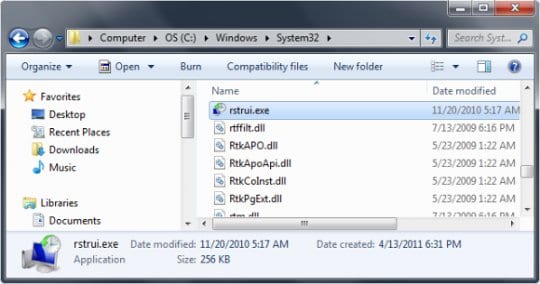
- In Windows Explorer, browse to the following path:
On Windows XP: C:\windows\system32\restore\rstrui.exe and hit Enter
On Windows Vista / 7: C:\windows\system32\rstrui.exe and hit Enter
- Using the System Restore prompts, get your system restored to the date when it was unaffected by the ransomware virus.
Download, install and run reliable security software to get effective protection from cyber threats further on.






























I believe I have been affected by the updated version on this malware, which blocks safe mode completely. Do yoy have any advice on how to tackle this problem? I tried system restore but can’t do it quick enough.
Dave,
If you have access to another computer that’s not infected with this virus, try the removal method with HitmanPro.Kickstart, which is highlighted as #1 method under PCeU cleanup section of this article. This should help.
Thanks for your question
Neden Ukash.. Good ukash paysafe ukash card