
Spanish computer security expert Chema Alonso gives a great talk at Defcon 20 about the ways to expose online scammers through the use of JavaScript botnets.
 The title of this session is “Owning bad guys and mafia with JavaScript botnets”. I hope you will enjoy the topic.
The title of this session is “Owning bad guys and mafia with JavaScript botnets”. I hope you will enjoy the topic.
But before I start, I would like to introduce myself and my country. I am Chema Alonso, (@chemaalonso) I work in a small company called I64 (Informatica 64) in Spain, I’m also a Microsoft MVP in Enterprise Security, and I live in Spain.
Do you know Spain? Have you ever been to Spain? If not, you have to go and visit our country. This is Madrid (see left-hand image below), the city in which I live. As you can see, this is a city that is never asleep, but it is smaller than New York. And there are a lot of big places in Spain that you have to visit. This is the Sacred Family in Barcelona (image in the middle), one of the most beautiful churches in the world, as you can see.



Of course, there are other places that you might like to visit. This is Ibiza (right-hand image above), a small island to which I’m going tomorrow, so if you want to rest and discover a different Spain – it’s very close to you, it’s in Europe, just across the ocean.


And of course, if you’re a brave man you can visit all the cities with all the parties. This is Pamplona (see left-hand pic). How many of you have run from bulls any time of your life? There is only one rule: if you drink, don’t run. That’s the only rule. The rest is easy, you only need to run faster than the bull, it’s very easy to do.
And of course, if you’d like another party, we’ve got something special. This is the Tomatina (on right-hand image above); it’s a battlefield with tomatoes, one day long. I am not sure about the history of this party, but you only need to throw tomatoes – that’s all, it’s quite interesting. Well, we are Spaniards, you know.
Well, let’s start with today’s topic. Today’s topic is quite simple: let’s create a botnet – that’s all. But we’ve got a lot of problems with this from the start. I guess many of you have been thinking about creating a botnet any time in your life. How many of you have been thinking about creating a botnet? How many of you did it? I did it.

Well, the idea of creating a botnet is quite interesting, but of course, I assure you, I’m lazy. I’m from Spain, so it’s normal. So, we are lazy, and this is a nice picture (see image). I would like to show you this picture, because when Spanish people need power supplier, and they are using flip-flops to connect it through the swimming pool. It’s incredible! This is more or less like a thing we’re used to doing in Spain.
So, that’s the idea of creating a botnet. We wanted to create a botnet, but we were lazy; we have no money – you know it; we have no 0-days; we aren’t the FBI or the NSA, so we cannot intercept communication for free, and of course we are not Google, Apple or Microsoft that are running all their devices around the world. And, you know, we are Spaniards, so we need to do something different from the beginning.

The idea of creating a botnet was quite simple. We thought: okay, let them be infected; let’s do something that allows bots to be infected for themselves. So, the only thing that we wanted is so that they would want to be infected, quite simple.
In the end, if you think about this topic, it’s very useful and the malware industry had been using it for around the last 5 or 10 years; we’ve rolled antivirus and social engineering tricks. So, why not make our own botnet doing the same trick?
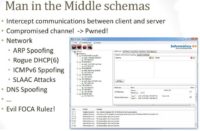
So, the idea of creating a botnet is just to create a man-in-the-middle attack. There are so many man-in-the-middle attacks that can be used in different scenarios. Of course, if we are in a network we can use something like ARP spoofing, or we can use rogue DHCP in IPv4 or IPv6 networks, man-in-the-middle attacks in IPv6 networks. We are going to publish a new tool, a new FOCA, which is the evil FOCA, to perform man-in-the-middle attacks in IPv6 networks: just point it and click, quite simple.
And of course, if you are able to manage the DNS, you can do the man-in-the-middle attack. But it is quite complicated in terms of the Internet because you have to deal with a lot of Internet service providers and networks, so it’s difficult to use on the Internet.

One of the most used practices on the Internet several years ago was the man-in-the-browser, in which things like Browser Helper Objects are installed in Internet Explorer, and lots of malware samples have been using this trick. We got a lot of malware this way, especially from Russians. You’ve seen this trick, this is very effective and it works so well that they need special files to configure the Trojan to attack different banks. This is how a banking Trojan uses an XML file to configure the man-in-the-browser to control all the different web pages from different banks. Quite simple, and yet it works very well.
But we needed to code something and deal with antivirus system, managing the detection program, so we decided that it was very complicated for us and we needed something easier.

So, we thought about man-in-the-“tab”, or JavaScript-in-the-middle. The idea is quite simple: if you are able to run JavaScript in one tab; you can do a lot of things. You can access the code, you can modify the HTML, you can access the form fields, you can manage even the cookies that are not supposed to be managed, like HttpOnly cookies, using different tricks, and so on (see image).
In fact, there is a very well known project, which is BeEF – the Browser Exploitation Framework project that allows you to do a lot of things by just installing a small piece of JavaScript code in a browser.
Another idea that we thought might work in our case is just to do cache poisoning. The problem is that we needed to configure this on the Internet, and it’s quite complicated as you want to infect a lot of bots on the network. So, we were thinking about how to make it easy, and we came up with the following: the idea is how to create a JavaScript botnet from scratch, and it’s quite simple.
First of all, we thought about the TOR nodes. The idea with TOR nodes is quite simple: if you are the last one on the line, you will be able to access all the content, you will be able to intercept all the communication. The problem when we tried to create the rogue TOR node was that they are using some security test to discover who is modifying the DNS response, or who is having some special files, and so on. And we got detected (see image to the left). So we thought: “Well, it’s too complicated, we need to detect when they are sending their test and create interception for the test – too difficult, we are Spaniards.”

The next thing that we did was just create a proxy. Creating a proxy is quite simple, because a proxy is not a big infrastructure like the TOR network, in which everyone is connected. A proxy server is a standalone server that people decide to connect to.
So, the idea is that if you read all the manuals online about how to be anonymous, the first thing is: “Connect to any proxy server on the Internet.” We thought: “Hey, it’s very interesting, because it’s a man-in-the-middle scheme.” So, if we are a proxy server on the Internet and people decide to connect to the Internet through our proxy server, we will be able to collect all data and infect all browsers. So, we did it.

The first thing we needed to do was just rent a server on the Internet; of course you have to take care about what kind of server you are going to use. Don’t use any Pirate Bay server, not one in Amazon – remember what happened to WikiLeaks, and not in Megaupload. It’s better to select any country in which there are no laws. So, we were renting servers in Iraq, Afghanistan, Kazakhstan, Spain.
Then, once you rent your server, you only need to configure something that is very simple – Apache web server and SQUID proxy. And the idea is that with this server we were going to infect all JavaScript files with one small piece of code – two lines only.
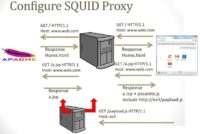
So, when the user connects to our proxy server we go to the website, we go to the response page, and the response page has a JavaScript file (see scheme). Then we retrieve the original JavaScript. Then we add only two lines to load the new payload. We didn’t want to use a payload that is very well known on the Internet, like BeEF, so we just coded two lines and installed those two lines in all JavaScript files that were across our proxy server.
So, in the end all you need to do is this: first of all, we created a rewrite program to add those lines of code, we need to configure this option in SQUID proxy; and then we added the ‘no expiration’ policy in Apache, because once we infected a JavaScript file in a web browser, we wanted to be there forever.

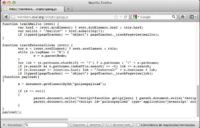
Then, the code that we needed to create is just this (see image): it’s PerlScript, as you can see, and the only thing that we are doing is retrieve the file using Wget; we copied it to our file system, and then we added the pasarela.js file to the JavaScript. And then, of course, we sent the new JavaScript to a client using Print. It’s a very small piece of code, it’s full of common injection vulnerabilities, but it works.

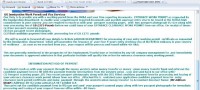
The JavaScript is just this: it’s a small piece of code, and we’re just connecting to the control panel, and the only check that we do is just whether we are running only one instance of the payload in every tab – so simple. And of course, we didn’t want to do anything bad to the good people, so we created a special advice advert on the webpage of our server saying the following: “This proxy server is being used for a security research. All JavaScript files will be infected and all your data will be collected. If you want to be safe, don’t use this proxy server. If you do that, don’t send sensitive information. If after all you continue, do it at your own risk.” So, if you don’t want to lose your passwords, if you don’t want to be infected – don’t use our proxy. That’s quite simple; it’s a good security policy. Actually, in the army you get the same security policy: “Warning! The following unsecured FTP site is for temporary uploading and downloading of files for official government use only. Any other use is unauthorized. Use of this unsecured FTP site is at your own risk.” This is a web page from Army.mil; it’s basically the same security policy, so it’s legal.
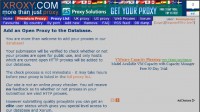
So, the next thing we needed to do is just make our proxy server public, so we copied our IP address and published the IP address on a proxy server list – as you can see, XPROXY – and then just let the Internet do its magic, and in a few days we had 1110 different results about our IP address, because all proxy server lists copy themselves. So, if you publish your IP address in one proxy server list, they are copying the same IP address to all proxy server lists, which is funny, because in one day you can have a lot of bots.

The next thing we do is just create a small piece of payload. The first one is cookie stealing – we were running our JavaScript inside, we didn’t want to deal with HTTPS connection, we didn’t want to deal with secure cookies, we didn’t want to deal with HttpOnly cookies, so we just copied the normal cookies, the unsecured cookies, and sent the cookies to our control panel just using a GET.

Then we created a small payload to grab all form fields (see image). The idea is that we hook the Submit function and copy all information in the fields, and send the fields’ value to our control panel – and that’s all, just enjoy. Doing this in just one single day, we were able to get 5000 bots, which is not bad – no pay-per-install, not creating any special polymorphic malware – just publishing one IP address on the Internet. We are from Spain, you know.

So, the question is: who the hell uses proxy services on the Internet? How many of you are using this kind of services on the Internet? If you read related manuals, they all say: “If you want to be anonymous, use anonymous proxy server. If you want to be more anonymous, use more than one anonymous proxy server,” which is cool, because you can be infected by more than one proxy server.
And the idea is that the kind of people who are using these services are, of course, bad people. All we were able to collect was bad people doing bad things. Of course, the first thing we discovered was the Nigerian scammers. We collected all information, and of course we collected all usernames and passwords. But we had warned them, so it’s all legal.
So, once we got the passwords, we could get into the mailboxes of those people. There were lots of people doing this, but this is one of my favorites (see image to the left). As you can see, the email alias is royalhotelengland@hotmail.co.uk. That guy was creating a spam campaign trying to scam people with visa scheme. He was offering the victims a special visa to get a job in the UK.
This is the mail (see right-hand image), of course he was asking for money, 275 Pounds. And a lot of people were suspicious, saying things like: “I appreciate the information, but show me the job first. Show me the job and then I’ll send the money.” Of course, if the guy was suspicious, the scammer wasn’t continuing the scam. But others weren’t so suspicious, so in the end they were sending all the information needed to create a visa – passports, application forms, resumes, high-quality pictures for the UK passport, even fingerprints, and so on. This is the easiest way of identity theft that I’ve seen in my life, for sure. If you got all this information, then you probably can create your own mule to use in banking malware.
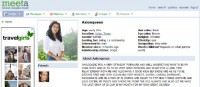
Here is another one (see image to the right), which is one of my favorites too. This is a profile on a social network for having a fling, that kind of thing. How many of you really think that this girl needs to search for a guy on the Internet? Well, it was very suspicious to us from the beginning. So, we decided to collect the username and password of this profile and analyze what she was doing.
And in the end, as you can see, this Axionqueen here is searching for relationship and dating, she is from Texas, and she is about 30. But she has another profile on another network (see image to the left). And in this case she is from New Zealand, she’s 31, she’s Aries, and so on. And in another profile, she lives in Virginia. Anyone from Virginia who has seen this girl? And of course, the most wonderful thing is that in all the profiles she looks completely ‘different’.
In the end, we decided to get into this guy’s email box, and we read the information he was storing there. Well, this person, of course, is not a girl, it’s a boy, it’s a he, and he was collecting conversations with people who were in contact with this profile. Those profiles are for phishing the victims.

That is one of my favorite chats (see image), in which kkbill is supposedly the girl, and fiat176punto is the victim:
– Hello, sweetie.
– Hello, my sweet Mous. (I think we need an “e” here.)
The second one is:
– How are you doinf?
– Doinf?
In the chat they are discussing the details of their love, and one of the details implies 700 Euros that need to be sent in exchange for the ‘nicked’ pics. I don’t know what kind if pictures those are. And the point is that this guy, this predator, is a multitasking scammer, so he is chatting with different people at the same time, and that’s probably why he fails here, because in the middle of the chat he started to chat in German, I think so: “Ich frage Sie, dass, wenn Sie…”
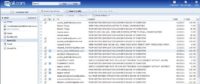
So, we went inside the email box and it’s quite nice, because he has all the victims very well classified in his email box (see image). And there is a folder with all the chats, in which he is working right now, and we were searching for mails asking for money through Western Union, and, as you can see, there were 158 messages asking for money from Western Union.

And the mails were like this (see left-hand image) : “Hello sweetie, why haven’t you sent me the nicked pictures you promised me?” And the guy said: “Hello baby, I don’t know but my bank manager told me that the address city and country are not possible, now what can we do?” Of course, she is asking for money that needs to be transferred to a different country in which she’s supposed to be living, that fake profile, and she gets angry: “Stop playing games on me, I gave you the right address!”
Another scammer in that test that we did was someone very weird, because he was doing something strange with dogs. We weren’t sure what he was doing with dogs and why he needed to use a proxy server on the Internet, an anonymous proxy server on the Internet. So, we decided to use the username and password to get into the email box, and we discovered something very hardcore. We discovered a picture – I’m warning: please, if you love animals, don’t look at this picture, because this is the picture (see image). He was selling this fake Yorkshire, and in the end he was selling the same Yorkshire around the world. So, it’s the most profitable Yorkshire in the world. He was placing the same picture in a lot of places selling dogs and making money out of it.

Of course, we discovered psychotics. This is what the control panel looks like (see image), and as you can see, this guy was searching xnxx.com for “Mother”, “Rape sister”, “Violent rape”, “Violence”. We were about to send this IP address to the police, because this guy is not normal.
Also, a lot of people are trying to be anonymous, and the first thing they were doing was just test if they were anonymous. The problem is that if you are using a proxy server, you are anonymous to the end page, but not to the proxy server, so the proxy server can track you anytime, it’s quite simple. So, okay, you are ‘anonymous’: we know what country you are from, and we know your real IP address – so, it’s quite simple. There are lots of cases when people are doing the same, trying to be anonymous.
This is the worst case we discovered (see image). It’s a guy trying to make money by reading blog posts. It’s supposed to be a business: you read a blog post of anyone around the world and you will be paid for it. And after one month he was able to earn 24 bucks, so I’m not sure it’s such a good business right now.
Of course, we discovered a lot of people hacking, doing defacing, and so on. And this is one of our favorites: in the control panel we could see the local files and the website that had been hacked. We connected to the website that had been defaced, and we could now see the email address of the hacker, so it was anonymous, but we got the email address. But the problem is that this hacker was using our web cell, and the web cell was hacked with JavaScript. You probably know there are lots of web cells on the Internet with small pieces of JavaScript that are copying your web cell, and you are Trojanized by this web cell. This web cell was Trojanized by a JavaScript file, so when the JavaScript file went through our proxy server, we infected that JavaScript and then we owned the web cell of the hacker. In the end, the hacker who was hacking was hacked.
Also, one of our favorite things is that once you are using a proxy server, if you disconnect from the proxy server but you don’t erase your cache, you will be infected for the rest of the time, because the JavaScript is in your cache. So, the idea is that we discovered that some intranet applications were using JavaScript from the intranet, so we were able to infect that JavaScript, and then we infected the intranet application (see image).
In this case, this is a guy from Mexico, he wanted to browse for some porn on the Internet, and then he disconnected from the proxy server, but he was infected. And, as you can see, this is an internal server; we weren’t able to connect to it, but there is an ARP application with data and, of course, a lot of information on the user, such as the password and so on. But we couldn’t connect to that intranet because it’s not published on the Internet.

And, of course, porn, a lot of porn; people searching for porn. Porn is the business, believe me. Not hacking – porn, porn, porn. We discovered this (see left-hand image), this is a very nice story, where in a Catholic church they discovered this painting from monks, about 7 centuries old – they were painting penises. It’s true.
So, we were collecting URLs and we discovered a lot of URLs of porn. Also, a lot of usernames and passwords (see image below); we’ve been selling them on the Internet, of course…
In the end, once we got the bots infected with JavaScript, we can create a special payload. And, of course, if you are connecting through a proxy server, probably you won’t connect to your banking system, or you are not going to connect to your social profile, or you are not going to connect to your intranet or your personal website, or whatever. But if you don’t clean your cache, you are infected. If someone forced you to load a JavaScript file which is on the web page you are going to visit after you’ve been using a proxy server, then you will be hacked.
As part of the study, we analyzed LinkedIn and saw there were some scripts loaded in LinkedIn website. So, if you are using our proxy server, then we can create a special payload forcing you to download these JavaScript files. Then this JavaScript file will be infected. Once you disconnect and connect to LinkedIn, our payload will be executed – it’s so simple. So, we can create special targeted attacks to several websites, collecting passwords of people who were using our proxy server before on the Internet, it’s quite simple.
So, you only need to select the target – whatever: a bank, a social network, intranet – analyze the files that are going to be loaded by this website, and force this file to load when the guy, the victim, is connected to the proxy server. It’s pretty simple.

I wanted to do a real demo, but first I’d like to show you the control panel and what it looks like. Of course, we turned off the proxy server on the Internet, but for BlackHat and Defcon I created a new control panel (see image). I didn’t publish this proxy server on the Internet, but after delivering the talk at BlackHat – I don’t know why – someone published it online. So, we configured this proxy only for 10 parallel connections, and right now, this morning I’m going to show you the bots, the zombies; and as you can see, if we search for today’s date, we started to receive a lot of bots from different countries, a lot of them from the States, Brazil, elsewhere. And we got a lot of information collected from them. We didn’t want to do it, we didn’t publish the IP address, believe me.

The demo I would like to show you is more or less this. Let me show you the website, this is the California Credit Union League (see screenshot). As you can see, this website is perfect for a targeted attack, because it’s an HTTP website; there is a login form that is going to send the credentials to HTTPS web server, but we can inject a JavaScript file very easily in the HTTP website, hook the form, and collect the usernames and passwords from this website. So, the only thing we need to do in our control panel is analyze the target and select one file. In this example I selected members.ccul.org, scripts, gatag.js.

And then in our control panel we created some special payload. So, we go to the control panel, and you can see we got preset attacks in which you can configure what is of interest to you, and in case with the California Credit Union League the only thing that we needed to do is force to download this file (see image).
So, the guy who is using our proxy server, who is watching porn and is infected, will be downloading this file to the cache. He will be watching porn, hacking websites, whatever, but at the same time he will be downloading this JavaScript file for the targeted attacks. Then, when he will be disconnected, in this case by selecting not to be connected anymore, the JavaScript file which is in the cache will be infected with our payload, because we downloaded it before, and this file is not out of date, so their browser will be using it. In the end, after the guy connects to the website sending the information, that form will be hooked and we are going to be able to retrieve all this data in our control panel. It’s so simple, so easy to do, and very profitable.
Now, some thoughts about JavaScript botnets. In this example we didn’t worry at all about doing something special with the HTTPS connection; we didn’t worry about pre-cached objects using the E-tag or using special tricks to force the expiration of the objects that were previously in the cache; and we didn’t want to do anything with the HTTPS connection because we didn’t want to raise any alerts. And, of course, we didn’t have any Flame digital certificate, and Moxie was very busy tweeting, so we couldn’t contact him to create a special digital certificate.
And the whole point of it is that we did it only in one day. So, in one day we were able to configure the proxy server, configure the Apache, publish their IP address, create the JavaScript, and collect all this information.
We were able to do this in only one day; the problem is: how many of you think that government, intelligence services, the bad guys aren’t doing the same on the Internet? The question is how many of you think that only one of those proxy servers on the Internet is secure? No one? I mean the server that is not going to infect you or collect your data. It’s the one you run; it’s not an anonymous proxy server, it’s yours.
In the end, using a proxy server on the Internet is a very bad idea, but we got thousands and thousands of web pages on the Internet, same people: “If you want to be anonymous, use a proxy server on the Internet.” We are going to have this problem for a long time. So, don’t use it.
Some protection, of course. This is a man-in-the-middle schema, in which you decide to be hacked, because you configure your web browser to use that man-in-the-middle, that proxy server, so you have to think twice whether it’s worth it – to be using that proxy server.
And certainly, the problem is with TOR networks, but right now we’re getting more news about rogue TOR nodes on the Internet than about fake proxy servers on the Internet, and I don’t know why. And of course, after using this kind of services, if you have to do this for whatever reason you have, take care and clean all the information that you downloaded from the Internet. Take special care with that machine. If it’s possible, use a new virtual machine and burn it out after using, throw it to the trash, wherever you want. And, of course, VPNs are not a silver bullet, because in this case we were able to discover a lot of people connecting to our personal VPN to be outside of the network in which they were connecting, and then from the VPN connect to our proxy server, and in the end it’s possible to infect the client in any case. So, take care of it.
Thank you very much!




























