
The Federal Bureau of Investigation is warning the Internet users of a dangerous and immensely aggressive virus called Reveton which is known to block computers on behalf of the government organizations, attempting to extort money from confused users.
Based on the official report, Reveton is a typical representative of the Winlock Trojan family. Unlike many other viruses out there, this particular threat does not rely on the use of executable files or email attachments for spreading. It gets automatically and stealthily installed on the user’s machine when a compromised website is visited.
Based on the in-depth analysis conducted by well-known security researcher and blogger Brian Krebs, the distribution of Reveton is quite likely to be associated with another infection known as Citadel which, in its turn, is derivative of the notorious password-stealing ZeuS Trojan. Furthermore, the author of KrebsOnSecurity.com believes Reveton’s propagation might be assisted by a version of the BlackHole exploit kit which resides on hacked or malicious sites and checks visitors’ web browsers for vulnerabilities, e.g. ones emanating from outdated Java, Flash or Adobe Reader components. Such exploits being spotted, the malicious kit injects Reveton and the ‘bundled’ password-stealer into the system.
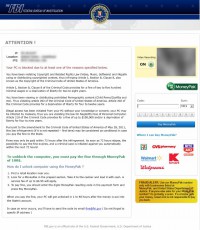
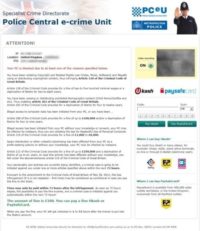
Once inside the targeted workstation, Reveton prevents the user from accessing Windows and displays an alert with accusations of committing serious crimes such as distribution of child pornography and Copyright Laws violation. Typically, this virus demands the user to pay the FBI or other government organization a fine amounting to around $200 in order to get the computer unlocked.
One of the victims described his experience with Reveton this way: “Reveton displays the emblem of the FBI in the pop-up window which cannot be closed, and next to it there is information about the alleged abuse of the following federal laws: illegal downloads of media content, viewing child pornography or negligence in computer use. Creators of the page offer transferring the fine via MoneyPak. It also states that in the event of failure to comply, the filing of the appropriate criminal charges would take place, and my computer would remain locked.”
Employees of the Internet Crime Complaint Centre (IC3) report to be currently dealing with an inundating stream of similar user complaints. The head of the Center Donna Gregory stated that a lot of people actually fell for the fake warning and paid the so-called ‘fine’.
Let’s get back to the virus proper to better understand its essence and how to treat it. Reveton was first discovered in May of this year; reports about the threat have been regularly coming in from all over the USA ever since. It’s interesting that an influx of similar attacks had been affecting European countries for quite some time before the United States got hit, so the cyber criminals apparently ventured to take a bold move and win another huge market for making illicit profit.
The French-based botnets.fr project’s representatives claim to have been monitoring the activities of the international gang behind Reveton virus for months. One of researchers states that the cyber criminals have been continuously refining their technical infrastructure and tactics in order to keep their illicit business going and prospering globally, ranging from establishing secure connection to the extortion pages – all the way to maintaining a complex server network in a number of countries.
Furthermore, as Brian Krebs points out, the criminals no longer depend on affiliate networks that can be shut down due to law enforcement actions or user complaints. MoneyPak, which is the payment processing system suggested for use by the FBI ransomware authors, enables submitting the payments without credit card involvement. This technique allows the gang to operate without having to bear the risk of getting the money flow cut off.
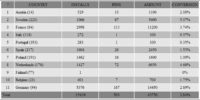
Botnets.fr team managed to get hold of sensational insider statistics of Reveton’s daily infestation rate and the financial output of this routine in Europe. According to the file, out of 15,419 total Europe-wide virus installs that went through in a single day (May 18, 2012), 503 victims ended up paying the ransom. The bad guys therefore made over €40,000 (about $54,000), and that’s in just one day. Although the conversion rate is not particularly high, the overall earnings are huge. No wonder the scammers decided to expand their activities over to the United States.
Specialists from the IC3 highly recommend victims to refrain from transferring the money as a ‘fine’, or providing additional personal information to the criminals. The most reasonable step in this situation is to immediately seek professional computer help. Be careful, even if you managed to unlock the computer on your own, malicious software could still be operating in the background without your awareness. Always send a formal complaint to IC3 and follow the updates dedicated to Reveton on IC3 website.






























This “FBI” virus has my desktop locked down. How can I get the malware off?
Ralph!
F-secure gives instructions here http://www.f-secure.com/v-descs/trojan_w32_reveton.shtml
Terry
I have been attacked several times by this @#$%^&^* and found onne way to eliminate iit is formatting the harddrive and reinstall the OS. In my case that is XP and I can get access via safe mode. In attempting to hunt compromising files I have yet to actually locate them and it has blown right through Security Essentials and Windows Defender. Could I still be doing something wrong?
David,
Formatting the hard drive is probably the last resort in this case. Before doing something as radical as that, try sticking to the recommendations provided in this article, it does help.
Thanks
What I did was on Windows 8 I clicked on my cc cleaner and it forced google to close cleared all my browsing data and ran my antivirus. All Good so far. if you can’t do that ctl+alt+n will clear your browser to get it off.