
 The Chief Intelligence Strategist for ‘Treadstone 71’ Jeff Bardin presents his overview of cybercrime from several different angles. Mr. Bardin describes cyber fraud as viewed from within this industry, outlining such aspects as credit card fraud, botnet operations, spam distribution, phishing, money mule recruiting schemes and software vulnerabilities exploited by the criminals. Importantly, you will also get to learn how these activities relate to international terrorism.
The Chief Intelligence Strategist for ‘Treadstone 71’ Jeff Bardin presents his overview of cybercrime from several different angles. Mr. Bardin describes cyber fraud as viewed from within this industry, outlining such aspects as credit card fraud, botnet operations, spam distribution, phishing, money mule recruiting schemes and software vulnerabilities exploited by the criminals. Importantly, you will also get to learn how these activities relate to international terrorism.
My name is Jeff Bardin, and we will talk about malware. We are also going to speak on malware’s ties to terrorism, as well as card and ID markets, and these card and ID markets were pretty impressive. And we will talk a little bit about the FBI’s hands into these markets and what they did to take them down.
So let’s get into the malware right away here, we will talk to that. So, most people know about zero-day malware attacks. This is when there is a vulnerability that is undiscovered in software, usually on the Internet or even on your desktop. It’s undiscovered by the software company or the authorities, let’s put it that way. What it is discovered by is the cyber criminals because they will go out and continually reverse-engineer and search for vulnerabilities in software. They are constantly scanning, probing, searching for these vulnerabilities, and they find them before companies know they are there, and before they can actually create a fix for that software.
A zero-day attack or threat is a computer threat that tries to exploit computer application vulnerabilities that are unknown to others or the software developer. Zero-day exploits (actual software that uses a security hole to carry out an attack) are used or shared by attackers before the developer of the target software knows about the vulnerability.
Wikipedia
So zero-day is something that they exploit on a regular basis. We have seen it most recently with Stuxnet1. But it is a constant battle and their whole ‘modus operandi’ is to find these and then incorporate into their malware products.

So there are a lot of different botnet2classifications here. As you see on the image, there are proxy botnets that you can use to secure information and stop people from tracking you. There’s credential stealing, using trojans and other information; web hosting sites that actually look and smell just like banking sites, but in fact they’re not – they look exactly the same, but when you go to those sites you can be immediately affected with a zero-day malware attack. There’s spam out there as well, where people will click on links that take them to sites that actually will download software, and you won’t even know that you’re infected, it does it very quickly and effectively. There’s malware droppers, and the credential stealing we talked about in the spam botnets out there.
So, when you become infected with a botnet, something that will give you an indication that you’re infected is the constant flashing of the lights on your machine because it’s overworking and you are actually now a zombie in the botnet – you are part of it and you have been infected.

So let’s continue on here. This is a picture here of maybe a rack environment at a hosted data center. If you follow the words on the image, this is basically how they set up their infrastructure: spam content servers, pharmaceutical fraud sites where people will go and buy and sell Viagra and different information, so you may get the Viagra, sometimes you’ll get bogus drugs, but what they are really after is your credit card information.
Money mule3 sites that will go out there and offer jobs in the downmarket – these sites will offer lots of jobs out there, but when go into the jobs section of this website – it looks very legitimate – only one job will be open, and that’s the money mule job, where they’ll transfer money into your account so that you basically launder it, or they’ll send goods to your house that you’re supposed to store and forward, and eventually you’ll get caught because you are just a mule. That lasts usually from one month to three months before you get nailed unsuspectingly, but in the downmarket that’s done frequently.
Malware drop sites, the infection sites, rogue name servers out there, child pornography sites, phishing are there as well.
Rogue payment processing sites look exactly like payment processing sites for credit cards when in fact they are completely bogus and they are stealing your information as you enter it. Bank account intrusion sites, distributed denial-of-service sites are out there, and the carding forum sites where credit cards are bought and sold.
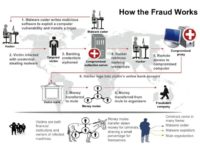
This is a part of the infrastructure out there, and I am going to talk a little bit too here on how the fraud actually works (see image). So, a malware coder goes out and writes the code for a zero-day attack along with bundling it up with multiple payloads, meaning – put a trojan in there, the trojan will install on your machine, and then it can send information out through a secure channel.
Once it exploits a vulnerability in the software on your machine, it drops the software onto your machine. Then, as you go into your bank site from your PC, it keystroke logs your user ID, password information, and then gets into the bank site and steals information there. It will save that information onto your machine, and then through that trojan and this secure HTTPS connection it’ll send that information back to a collector site, where it stores it and eventually moves it back through possibly the other site. And this jumps around the world until it eventually gets back to the cybercrime organization.
Now, that’s one model of this. Other models are such that you can actually buy the software, and they have become a software house where you can buy the Zeus software (most people know about it), set it up on your own servers, and you can become the purveyor of the cybercrime software. And the people that write this software then will send out updates to you. They will send out software updates and push it to you with the service-level agreement that you have paid for when you bought this software.
So it has become quite an industry out there. And this is one example here of the money mule activities, where once, say, they do get that information, they may create credit cards from it, give it to a mule who then will go out to a bank site or go shopping, buying high-end goods such as Gucci handbags or whatever. They take that material and will post it on the eBay site, sell it for less than the normal price out there to move it quickly, take that money and then pay off the mules, but with a small amount, and refund their whole process.
So this is just a couple of the models out there that are being used today, and they are very effective, efficient and they continue to evolve and avoid our defenses.

So, what are some of the ties to terrorism here? How does terrorism fit into the cybercrime market? We’re gonna touch on that right now. Back in 2003, these three gentlemen here (left to right on the image): Tariq al-Daour, Younis Tsouli and Waseem Mughal – indulged in terrorist activities. Now, the one that’s most well-known is Younis Tsouli, or better known as Irhabi 007, or Terrorist 007. But he was not actually the brains behind it, it was actually Tariq, the gentleman on the far left.
So they used a lot of information out there that they would send back at the time to Iraq, and gentleman al-Zarqawi eventually was removed from the Earth by a couple of five-hundred-pound bombs. Anyway, they would use lot of their fundings here, their collection from illegal activities online to fund terrorist activities in Iraq, until they were caught.
Younis Tsouli came to London with his father from North Africa, attended Westminster College and started taking computer classes to learn a lot about computers. He was basically the computer mind behind this where he would set up a lot of different sites, take videos, compress them, distribute them.
So how did these folks actually fund their operations, where did they come into play with us?
Well, before we get to that, some of the things that Younis Tsouli did here is he would go out and preach Jihad4 on the Internet – communication mechanism, recruiting effort to get other Muslims to come to the aid of the folks in Iraq, funding them: “We want you to develop hacking skills. We want you to be able to steal credit cards out there. We want you to learn how to do this online”.
So, going through these classes himself, he was actually offering courses online on how to do this stuff: how to make bombs, how to learn how to hack. These were all documents, sometimes even videos on how to do this. And he was pushing that across on his cyber Jihadist sites.
And also, trying to get them to do the same, he was saying: “This is Halal5, it’s not Haraam6, it’s good to do this because it’s against the infidel, it’s not forbidden, or Haraam. Because it is in fact against the infidel, so it is okay to do this. And it’s a means to an end. And if you do this you’ll make a lot more money. Of course we want you to contribute that money back to us so we can help fund the cause”. So trying to talk people into this wasn’t very hard, there was a lot of affinity to this with the U.S. Forces being in Iraq.

Quickly back here to Madrid in 2004, this was during the train bombing where nearly 200 people were killed, where simultaneous bombs went off across different train stations, killing 200 different people. This was covered extensively by CBS News (see image). They used Mitsubishi Trium Mobile phones to actually trigger the bombs, they had them in backpacks. But to get these phones, they had to have funding for it.
They traded hashish to a former miner to actually get the explosives. And then, once they got the explosives, they learned how to construct the bombs. And they did that by going to sites, a lot of them propped up by Younis Tsouli and company that had already put them there before. That was starting to get flooded from people connecting out of Iraq, saying: “This how you create an IED7, this is how you create the best bomb, this is how you create the triggers with these particular phones” – video, how-to, specifically showing how you manipulate these and the triggers.
In addition, they found all kinds of drugs on site and they had again to have funding to get these drugs.
And then 2 million dollars in cash and drugs out there were found when these folks were eventually arrested, but it was too late, they had already perpetrated their crime, and 200 people paid for it with their lives.
Then they moved to England in 2007, this was July 2007 when the bombs went off in the subway systems and on the double-decker buses in London. When these folks were actually caught, they found all kinds of credit cards on them as well. They were using these credit cards to actually buy material and then send it out to Afghanistan or Iraq, depending upon their persuasion. Most of this actually went to Afghanistan.
So now you are seeing virtual activities have turned into physical actions because you take night vision goggles and tents and different equipment out there. You start to even the battlefield by providing them night fighting capabilities; prepaid cell phone calls that are once used and thrown away so they can’t be tracked; airline tickets of course, to move their people around; 180 different web sites.
It was announced back in September of last year by Interpol that there were over 10,000 cyber Jihadist sites on the Internet and that’s continuing to grow exponentially. Most of them are located outside the United States but there are still some that pop up periodically in the United States. And if you knock them down, they pop up again very quickly.
And they were laundering a lot of this money that came from the credit cards through online gambling sites as one method.
So total fraudulent charges here, total for this group is 3.5 million dollars – that’s what was able to be tracked – significant amount of money that was made and distributed by this one group.

Also, there is Islamic banking. And in Islamic banking, it’s very strict on what you contribute to, but there is usually some fund that you can contribute to that’s not very clear where the money is going. Not to say that this happens all the time, but it is occurring, where once it goes to one of those funds, it’s distributed kinda blindly behind the scenes based on the discretion of those in charge of the money as it goes down into different layers of distribution in the supply chain of money. And it does make its way back to terrorist activities.
In addition, Saudi Arabia still has over 80% of funding coming out of its country into a lot of these terrorist functions. Those are chargeable statements, but it’s still proven: UN and different law enforcement agencies are tracking this and trying to put pressure on this trying to stop this method of funding.
But there are also interactions with the underground economy, and that’s what we are talking about here today, and they developed these alternative sources of wealth through illegal means: money laundering; even human trafficking where they are buying and selling kids in this case, or basically slavery; arms smuggling and diamond smuggling are also on the rise, as well as counterfeiting of money and identity theft – it’s huge.
And there’s also counterfeit IDs. That’s why there is such a big push to change passports, put new information and new stopgap methods within money as well as in passports.
So terror funding comes from a lot of different ways, most of which though occurs through the Internet.

They would fly in with their planes, and they would go on a hunt, bring their hawks to go on a hunt. And the thing is they were also there for other reasons. Their planes were being loaded up with opium and heroin, and many times it is just a quick hop from Afghanistan back across into the Gulf States. One location that has come up many times is called Ras al-Khaimah, or ‘Top of the Tent’, and that’s at one of the Emirates in the Persian Gulf. Most recently there was nearly 20 pounds of opium found embedded inside of wooden toys that came from Pakistan.
There is a lot of movement from Afghanistan to Pakistan and across, as well as these planes coming in. So, embedding 20 pounds of opium in wooden toys – that’s definitely a lot of drugs. So that money goes back into Taliban and different terrorist forces.
But they have to communicate over the Internet, they have to set this up through the Internet, so it’s not just a physical play. Internet and a lot of encryption are being used to send these communications back and forth. So, even though bin Laden is not in Southern Afghanistan, the opium still flows.

But the flow of drugs goes out and the money comes in. And they can actually control the price by restricting flow and making it harder to get, which raises the price, or they can drop it. So, it’s a pure supply and demand system here. And again, it flows a lot into the different Gulf States, as well as Saudi and other areas, and then into Europe, and into the infidel elsewhere – again, it’s Halal, it’s permitted.

If you follow it you can look at major industry identifiers where the 1 and 2 are airlines, the 3rd position is travel and entertainment, 4 and 5 numbers are banking and financial, number 6 is merchandizing and so on. And when you look at the first 6 digits you can tell where this credit card information is from.
So if you’re on a carders’ market site and looking to buy, you actually know what you are buying based on understanding this table. You know if it’s a MasterCard or Visa, you know if it’s American Express. You can even take it down to what industry or even align it to organization if you follow this type of information.
So this is the type of information they are putting on their site before you go in: how do you validate this credit card, how do you know who it is and where it’s coming from?
And this is pretty significant because there are different prices aligned to the different types of cards, and you wanna to make sure you know what you are getting.
So, this has been published out there, so it’s “How to break the credit card code”, just a small learning exercise before they go in.

So you know that the use of the Internet is significant: electronic stores, travel agencies we talked about, betting, track and casino, lotto, some of that is probably for money laundering; wire transfers, moving money around out there, and those wire transfer money orders – that’s 156,000 dollars, that’s significant. What is direct marketers? That is probably Internet sites putting up and creating their videos, maybe paying someone to do this.
Then it gets down into more benign things, but this is a breakdown of 2.3 million dollars of what they spent their money on that they acquired through stolen credit cards.

So you say – okay, if it is Alitalia, where they were flying from and to, if it is Air France – from and to, because you can track it and find out maybe some of the movements of some of the people associated with it. So this information at face value looks like these are just some transactions, but you can dig down a little bit deeper and get more information around this, I believe that’s what the FBI did.
And as you dig deeper into this you get a lot more information. You have to enroll on the site, you have to create an ID, and you have to start to be trusted. Sometimes you come in and you’re kind of a junior partner on this site. You have to build up a reputation on this site as someone that’s being trusted, which means you start buying this information and using it out there because you start to buy.
Along with English-speaking carder sites, there are Spanish, there are Russian ones – there are a lot of different sites as they put it in multiple languages since it’s a worldwide underground cybercrime effort.
So ‘Carderplanet’ was one the first ones out there. And you can get all the information on anonymity and security: how to make sure you are anonymous when you come on these sites and maintain that when you’re acquiring this information and then using it.
So why would they offer this type of information? Because they want repeat buyers, they want them to come back, they don’t want these folks to get caught, so they offer them instruction on how not to, so that they can continue to feed the cycle of fraud.

So, they participate in these sites. Now, a lot of these sites though were owned and managed and delivered by people here in the U.S., so unbenounced to them or known to them, they were actually aiding terrorists activities by allowing anyone to come in with the money to acquire these credit cards and to go ahead and be part of the forum.
So this one here – ‘Shadowcrew’ – was definitely known to be used by Younis Tsouli and Tariq al-Daour. And so, they were on this site, they tracked it on their PCs and laptops when they were arrested back in 2003, and found that they had used it heavily, that they had participated here, and that they had stolen credit cards here. They’d learned how to do this stuff through these sites. Some of the hacking instructions came from Iran, IDs and passports were acquired through these which they then in turn used within the terrorist environment.
What eventually happened is a gentleman came around. This gentleman was known as Max Ray Vision, and he’s cited, you know: “There is no honor among thieves.” He had his own site called ‘CardersMarket’, and these other sites were up there. So what he decided to do is, you know: “I want to take them over” – basically a hostile takeover.
He hacked each one of these sites, he stole the credit card information, he siphoned it to his own database, he deleted their databases, knocked down these sites and created just one credit card forum.
So, that was basically hacker’s overthrow of this and hostile takeover. That upset a lot of people in the community out there but it made him the kingpin.
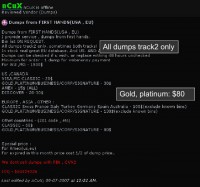
And if you want, you can look at Europe and Asia, get different information out there. And then you’ve got ICQ in the red down on the bottom, that’s an Internet relay chat ID, and when you start communicating, they will give you some other information as we build some trust and before we start the transaction.
Again, Gold, Platinum cards here – 80 dollars. Why? Because they are unlimited, unlimited spend on it in a lot of cases: American Express, Gold – unlimited. You have to pay every month the full balance, but if it is unlimited spend you can really make a lot of money quickly off those types of cards.
So, we go back here, one thing here is Max Vision – ‘DarkMarket’ was actually dropped and knocked offline, but it was brought back online by the FBI, and my colleague Keith Mularski was one of the main people on this site. He actually had developed a persona, where he was accepted on this site.
Eventually, Max Ray Vision, better known as Max Butler, who is now serving jail time – he believed that Keith and company under his persona was a federal agent, but he couldn’t get anybody to believe him, largely because he’d cried wolf before. So Mr. Mularski was able to maneuver around this. And eventually, there was no one who knew who Max Ray Vision was, except one person. And they were able to arrest that person, that person gave up information on Max Ray Vision known as Max Butler, and eventually he was arrested. And most of that occurred right here in San Francisco. He was set up sharp in hotels, in the financial district, in stealing information off of wireless networks amongst other things that are setting up these markets.
So ‘DarkMarket’ came back up and eventually was used to help take down Max Butler and company.
But in the meantime, it was too late for a lot of information that had been siphoned off to terrorists and used by them to fund their activities.
So let’s go back to the ties to terrorism. And we talked here about some of the malware and botnets where they siphon this information off. And of course it’s the path of least resistance, and lots of the days it’s been consumers, because banks have hardened their perimeter, but they are getting in through consumers who don’t necessarily take care of their desktops the same way as the corporate accounts do.
So, path of least resistance – we install the software there, we keystroke log, follow the information back. The cybercrime ties to terror are definitely significant, and they are allowed to do this because it’s for a cause, and it is Halal, it is permitted, and therefore they can buy drugs and credit cards to use to fund their activities.
And the funding from drugs that comes from out of Afghanistan through opium and heroin is still huge, and that goes back into the pockets of Taliban and al-Qaeda and different extremist groups. And they use the Internet to communicate securely back and forth to set up these transactions and drops, or to launder money.
The airline fraud was huge, it’s not quite as bad today as far as I know, but it was at that time and it still can happen: you steal a credit card and you go and buy yourself a bunch of different tickets out there.
And then there are the online cybercrime markets. And they still pop up from day to day, they have gone into buying and selling software that actually goes out and does this, so it takes the cybercriminals and removes them from the direct activities in a lot of cases by getting others to buy into it. And if they go down, this is just a skin off of their back, and they are still generating their revenue.
So, this is continuing to occur but there is a significant effort to defend against it, the FBI has had some successes. And of course there are other activities, I am sure, that are going on but that they cannot discuss.




























