
The tangible shift in computing which is steadily acquiring the properties of an overwhelming tendency is personal data protection. One’s real-world identity and its cyber counterpart are now merged to the extent where the former can be stolen by retrieving details of the latter. What is it that can allow criminals to learn your personally identifiable data such as habits, commercial preferences, private life details, credit card history, business occupation etc. – and put it all together to form a complete digital derivative of you as a person? This can all be exposed, directly or implicitly, by the contents of your computer’s hard drive.
The current relevance of privacy software is therefore perfectly well understood. Our today’s subject is one of such utilities, called East-Tec Eraser 2014 by the Romania based ‘East Technologies’ company. Without going too far ahead, we must admit it copes commendably with the targeted tasks addressing complete erasure of data. On the one hand, this product relieves the operating system from being encumbered by unnecessary files, thus contributing to substantial computer productivity improvement. On the other, more importantly, the application removes sensitive objects beyond subsequent recovery, no matter how smart and cutting-edge the tools are that identity thieves might apply. This software is smart enough to figure out which files to target – you run a scan, and get the complete list of those. By the way, those of you who are certain that it suffices to use the Windows removal options might get upset to learn that all they do is keep you from accessing those files, whereas they are still physically there.
The recognition of East-Tec Eraser is definitely on the rise: it got awards from the renowned and unbiased software evaluation portals and magazines such as Softpedia (Five Start Excellent Review), CNET (Editor’s Rating: Outstanding), Computer Shopper, PC Advisor and a number of others. Some more facts: this product has been around since 1998; it was used by the U.S. Marines within an experiment on information protection enhancement conducted by DARPA (Defense Advanced Research Projects Agency) in 2001. Well, quite intriguing, isn’t it? Let’s now get down to some specifics and see what East-Tech Eraser 2014 has got in store for the average customer.
System Requirements
Operating System:
- Windows: XP / Vista / 7 / Server 2003 / Server 2008
File Systems Supported:
- NTFS / exFAT / FAT32 / FAT16 / FAT12
Hardware:
- CPU 300 MHz or higher
- 128 MB of RAM
- 10MB free space on HDD
Usability
The distributive for East-Tech Eraser 2014 goes in two versions: commercial and the 15-day free trial. Installation and setup went smooth, trouble-free and surprisingly fast. There’s no reinventing the wheel here: the procedure implies downloading the 5.7 MB installer file and then clicking through the regular things such as the License Agreement acceptance and selecting the destination location. It took us some 15 seconds to complete the install – actually, the download of the stub installer was even a little more time-consuming than that. That’s pretty amazing in terms of the speed and ease. The welcome dialog box that pops up right after the setup gives a brief preview of the key features.
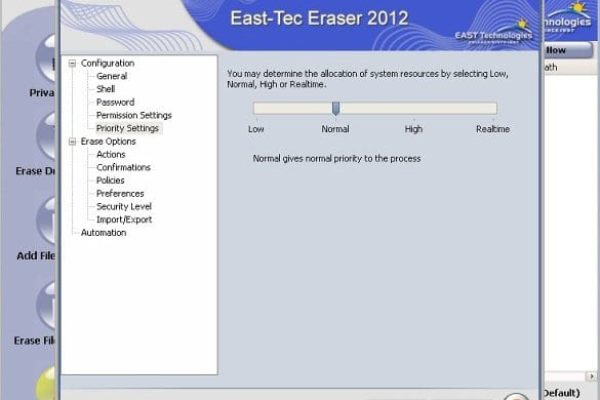
CPU usage was not significantly affected during the test – in fact, it never exceeded 85% on our lab machine which has pretty average hardware. Even though the application does inform the user of the possible appearance of a ‘Low Disk Space’ warning during the ‘Erase Deleted Data’ task, we didn’t get one. Moreover, East-Tec Eraser provides the option of setting the custom allocation of system resources: Low, Normal (default), High and Realtime – thus giving it at the user’s discretion to determine the system productivity impact. In regards to the program’s speediness, it’s generally great as far as the scanning goes. However, the actual removal takes a while even when the app works in the Normal mode: wiping the 33 GB free (unused) disk space on C drive was a 20-minute-long procedure. Erasing deleted data is a yet more time consuming routine. Of course it all varies depending on the data destruction algorithm being applied. The good thing is that the application does notify you of the possibly long wait time, so it’s all pretty transparent. In any case, the wait is worth it as the thoroughness is splendid.
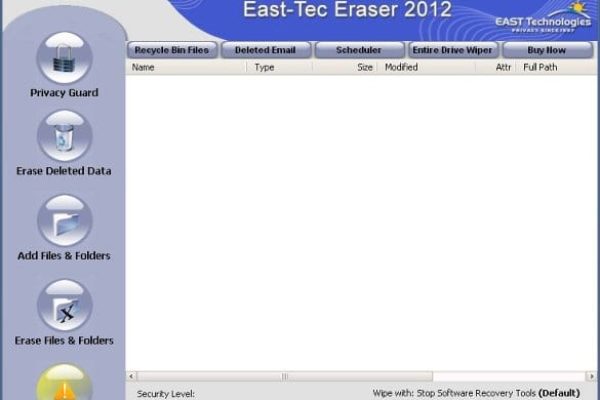
The graphical user interface makes this software easily understandable and comprehensive. It has 5 main buttons in the left-hand part (Privacy Guard, Erase Deleted Data, Add Files and Folders, Erase Files and Folders, and the current security status of the system); and some quick access buttons on the top for the scheduler, erasing the contents of the Recycle Bin, deleted Email and entire drive formatting. The grading scale for customizable security level is available in the bottom part of the GUI – the default one is ‘Stop Software Recovery Tools’.
The overall impression from usability is close to outstanding. The long wait time for thorough data wiping did seem a bit discouraging, but, like we said, it’s worth the salt when it comes to identity protection.
Features
Sufficiency is probably the most precise term to describe the feature set built into East-Tec Eraser 2014. The product appears to be balanced in that it gives you basically all you need to permanently erase both sensitive material and unnecessary junk cramming up the system. Once again, the features are not many, but they are enough.
Here is the list of capabilities you get if you end up choosing East-Tech Eraser as your privacy software:
- Privacy Guard is meant to erase personally identifiable information hailing from your Windows and web browsing activity. In other words, this feature prevents your computer activities from being tracked, and your private data from being stolen. The scope of objects processed by this function includes the so-called locked Windows files, e.g. swap file or index.dat. You can configure the cleaning reliability by selecting the ‘Advanced’ option here, other than the default ‘Basic’ settings.
- Erase Deleted Data – this feature enables permanently removing the items you deleted using Windows options. This might sound like a confusing assertion, but here is the thing: the operating system makes deleted files inaccessible – in the meanwhile, they stay inside the OS, so the known forensic software can still retrieve such information. That’s not a cold comfort though. East-Tec Eraser 2014 is capable of wiping the removed stuff irreversibly. The menu item corresponding to this feature enables selecting some options (targeted drive, wiping the slack of existing files, scrambling deleted files and folders properties etc.) to optimize the cleaning process.
- The Add Files & Folders and Erase Files & Folders are two mutually related features. First, you add an item to be erased, and then trigger the elimination process proper. As simple as that.
- Entire Drive Wiper is a response to Windows formatting, meaning that a whole system drive will be cleaned up using the algo that allows for no further data recovery, while the partition used by the operating system stays intact. The additional benefit you get here is PC performance improvement. Another good thing about the Entire Drive Wiper is the ability to securely wipe data (or remnants of it) from CD/DVD disks and USB drives, so you can now pass your removable media on to others without worrying about anything personal leaking out.
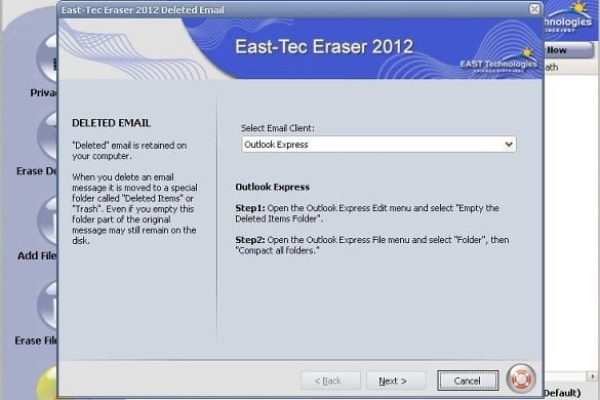
- The Deleted Email option irrevocably eliminates the traces of Email letters that you removed but which are retained on your computer, whether you are aware of it or not. East-Tec Eraser works with the following Email Clients in this context: Outlook Express, Microsoft Outlook, Mozilla Thunderbird, Netscape Mail, IncrediMail, Pegasus, Opera Mail; and processes the data generated by web-based Email services such as Gmail, YahooMail, Hotmail and others.
- Risk Monitor component checks the system for potential privacy issues in real time. Being integrated in the main program GUI, it notifies the user of new risks spotted, and suggests the appropriate action to get those fixed.
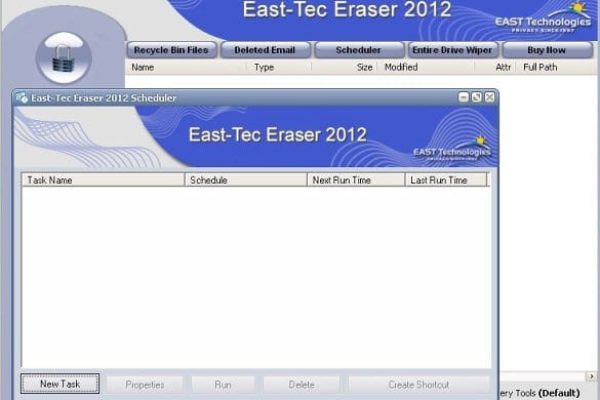
- Scheduler is exactly what it sounds like: you pick tasks and assign them to be completed at the preferred time. East-Tec’s scheduler provides extensive options to best organize your privacy measures.
It’s clear that the entirety of features privacy software is supposed to supply is qualitatively and fully delivered by this product.
Efficiency
The metrics we used for measuring the degree of East-Tec Eraser’s reliability are pretty unambiguous: data deletion techniques employed; the scope of tasks and activity areas covered; and the privacy protection results you get at the end of the day.
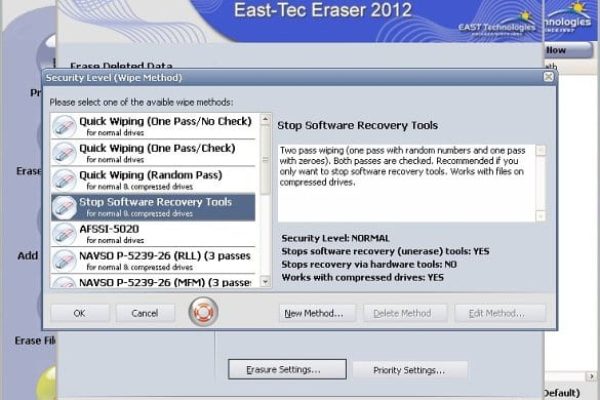
In terms of the data erasing effectiveness, the product accommodates a set of ‘Wipe Methods’, i.e. sanitize algorithms: Quick Wiping, Stop Software Recovery Tools, AFSSI-5020, NAVSO P-5239-26, Russian GOST P50739-95, German VSITR, Stop Hardware Recovery (DoD and Gutman), Bruce Schneier’s algorithm, and 3+7+3 Beyond DoD Standards. From where we sit, this appears to be an exhaustive list of algos for the average user to not feel short of identity protection. Of course the more advanced wipe methods imply longer wait times if picked, but here you have a choice depending on your needs, which is great news. Actually, unless you are a secret agent or a government official, the Stop Software Recovery Tools algorithm should do the trick.
There are over 400 sensitive areas and applications that East-Tec Eraser 2014 is now capable of permanently removing private data from. Just a few of those are latest versions of Mozilla Firefox, Internet Explorer, Google Chrome, America Online, MSN Explorer, Netscape Navigator, Safari, Opera, Yahoo / MSN / AOL Messengers, ICQ, Outlook, Limewire, Windows Media Player, RealPlayer, Winamp, Google Toolbar, MS Office, avast! Free Antivirus, Norton 360, ZoneAlarm, CorelDRAW Graphics Suite X6, TeamViewer, WinRar, WinZip and a lot more.
The output of East-Tec Eraser’s data processing activity is simple – everything personally identifiable vanishes for good, plus the PC starts running faster.
Help & Support
Contacting the East Technologies support staff is not an issue. Here you have, once again, a number of options to choose from: telephone support for United States and internationally; Email support via support@east-tec.com; and a ticket you can submit through www.east-tec.com/support/, with a detailed description of the problem you encountered. In case your inquiry is more trivial, click ‘Help’ on top of the product’s interface, then hit ‘Help topics’ or ‘Support’ to open up the interactive self-help window and look up the problem in there. We didn’t find an online chat option though. Still, considering the responsiveness of their team, you shouldn’t run into complications seeking help.
+/- (Pros/Cons)
- Light-weight and fast
- Easy to install and use
- Covers over 400 sensitive areas and apps
- Erases files beyond recovery
- Applicable for CDs, DVDs and USB cleaning
- Extensive choice of wipe methods
- Enables configuring security level
- Quick to identify targeted material
- Handy scheduler
- Reasonable cost
- Restricted support for free version users
- Lengthy erasure of deleted data at high security level
- Nag screen when using trial version
- No online chat with tech support available
- Customer support might be faster to respond
Bottom line
The one thing we can assert with confidence after testing East-Tec Eraser 2014 is that this software is trustworthy, easy to use and reliable. Maintaining one’s privacy is the realm the reviewed product fully covers without a hue of failure or burden for the system’s productivity. Overall, it is an excellent tool ensuring identity protection with immaculate efficiency by irreversibly deleting sensitive material.


































One software that works on MAC(intel based) and PC is ErAce. It works memory of 128MB and Pentium and higher also AMD equivalent is ErAce. It can be downloaded from erace.it . It will over write disk 1-100 cycles(user definable). It will write last cycle zeroes so hard disk shows like factory fresh and data can not be recovered.
One of the worst license schemes ever written. in 2014 & 2015 editions, license keys disappear after a few months, need to be typed back in, result: message stating license is no longer valid. Endless messages to support, regeneration of keys only produces problem again in a couple of weeks.
Good product when it runs. When there is a license problem, even when this user purchased a 2nd continuous 1-year license to use product, problem simply arose again.
I had the same problem after I renewed my license in January of 2016. I purchased a new computer then entered my key and I received a pop-up box saying that my license was no longer valid and I purchased it 5 months ago. I sent 5 requests for help and didn’t even receive even one acknowledgement. I gave them my order number, current license number, and all the info about my OS, Windows 10 and they totally ignored me. I contacted them via the form on their web-site each time. This is a very good product but their tech support is worthless.