Content:
Reflected herein is a study by the Florida State University researchers pertaining to the analysis of social engineering from a psychological perspective.
We’re going to talk about social engineering, and perhaps how you can use it to have more fun next week, if you’re not stuck doing work all the time.

Social engineering is essentially any act where you try to manipulate another person to accomplish a goal. The goal may or may not be in that person’s interests. So, in the realm of security a common goal for a hacker is get the victim to disclose information to him. It’s often used leveraging already known reconnaissance information for, basically, open source intelligence gathering.
Reconnaissance is the first little stage in the pentester and hacker-like lifecycle. It’s essentially exploration and probing to discover vital information about your target and their resources, and the layout of the terrain of the network.
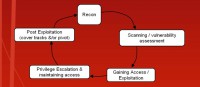
And so, social engineering can be used in actually any aspect of this terrain (see right-hand image). A very interesting use of it is in post-exploitation: I’m sure a lot of you guys have been getting emails from FSU helpdesk saying: hey, go to this Google document and give us your FSU ID number, your password and your other stuff. I got a well-crafted email from FSU helpdesk. It pointed me to a Google document, and the Google document was a form that just logged everything. And so I traced it down: I opened it up in my malware analysis VM to be safe, and they’re just logging all this to a spreadsheet that is hidden in the background. That’s pretty hilarious.
There are a lot of instances other than that where once attackers gain, say, access to someone who has a lot of authority in a network, like email, they will send an email to some other people saying: “Hey, I need this”, or “could you tell me about this, I forgot?” And because it’s sent with an account that has authority, and there’s a substantial amount of social engineering finesse and skill used in this spear phishing email, they often succeed with pretty high rate. That leads to compromising more of a network and more of system’s information.
Intelligence Gathering
So, in terms of intelligence gathering there’re three really main ones that pertain to penetration testing. There’s open source intelligence, there’s signals intelligence, and there’s human intelligence gathering.
1. Open Source Intelligence (OSINT)
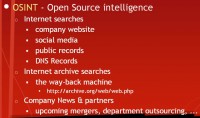
OSINT (see right-hand image) is essentially your standard Google search; searching perhaps even the company’s website, searching social media like LinkedIn, searching public records, especially financial records, searching DNS records, so that you basically know where the web servers are and what other IPs are registered to that DNS record.
Social media is interesting: you can find a lot by just looking at Facebook pages for employees of the company, looking at LinkedIn pages, and perhaps, if you want to get dirty, you can go on online dating websites and probably find some people there too.
But what people do with this sort of intelligence gathering is that they basically use maybe Python or Perl script, and they find everyone working for this company, and they scrape every single word off these pages, and they put each word online in a dictionary file and they use this to supplement any brute-forcing that they need to do to perhaps guess passwords. And it actually works with really high effect. People will list their likes and interests on their Facebook page, like I love this band and I love cats and I love everything else and all this other stuff. And so basically you take these things that they like and you permute them however you want. And you actually have a high chance of guessing someone’s password with this dictionary file that you’ve just gotten off of their social media page. And so that’s something that pentesters actually actively use nowadays.
Internet archive searches are very important: you can see perhaps an old version of a website, and that may reveal some backend data that wasn’t properly protected, like the IP, perhaps the name of the database behind it or some other information that was changed over time.
And also something that is really important to look into is partners of your target company and any news of the target company, perhaps merging with someone, because I’ve seen a number of successful social engineering competitions where someone would call the target company and say: “Hey, I’m Bob from Company B, we’re merging in a month, I want to make sure we’re on the same page with our security policy so we’ll hit the ground running”. It’s a pretty effective way to gain or disclose a lot of information that you shouldn’t disclose.
Another thing that is commonly done that I’m pretty sad about – it’s actually being done here – is that the management and the security of critical information, specifically sensitive information, is often outsourced to companies that sell these services. If you’ve noticed and got email registration for next semester for Summer and Fall – that’s been outsourced to some company in Ohio, and they’ll have your Social Security Number and all these other things, and they didn’t ask you before sharing it. So, in order to get this information, you’re not just limited to one target, you can get it in two places. But that’s more interesting for bad guys – obviously, pentesters are restricted by ethics and laws, and hunting for Social Security Numbers is not usually the specific goal of a penetration test.
2. Signals Intelligence (SIGINT)

So, signals intelligence, or SIGINT, really delves into the realm of Wi-Fi scanning, looking for access points at the company to hack into their Wi-Fi and get behind their firewall. It also falls into the realm of SMS eavesdropping – there’s no security in SMS and you can eavesdrop on text messages. If you go to Defcon, they have a wall of shame, where they have a projector on a 20-foot wall with really interesting text messages that they’ve seen fly across the wire in a casino, and you’ll find some really horrible ones, like: “Man, I got so drunk last night I woke up with this girl, I don’t know what happened”, and it’s like “Oh, man, this is pretty embarrassing.” And that’s just being posted there.
And also there is a lot of tools you can find and put together yourself to track other people’s phones if you just know their phone number and their IP address; you can GPS-track their phone. Phones, smartphones are like the greatest things for bad guys. They’re so good.
3. Human Intelligence (HUMINT)
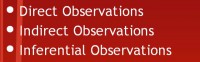
And then human intelligence – this is basically the realm of this talk on social engineering. There’re different types of intelligence you can gather (see right-hand image). You can gather direct observations – say I can snoop over your shoulder and see that you’re running Windows 8 and IE 10; I can see that just by directly seeing it. There’re indirect observations, like I can say: “Hey, are you running a version of Windows… does your Internet Explorer have tabs?” If you say “Yes”, that tells me it’s either version 9 or 10. So it’s an indirect observation I can make. And inferential observations are pretty self-explanatory.
Ties to Evolution

So, let’s talk about social engineering and exploiting the human’s mind, because there’re vulnerabilities in a human mind that you may or may not be aware of that we’ve basically evolved with. And even though we’ve grown to be sophisticated like this, we still have vulnerabilities from these days, from essentially the code that was used in the evolutionary process.

Our brains are actually not optimized for modern society (see left-hand image). As you can see in this population graph, basically it wasn’t until 1800 that there was roughly a billion people on this planet. And so, for the millions of years before that the man was on this planet, basically, man existed essentially in small tribal groups. So our brain evolved to be optimized for small tribal groups that were mainly endemic to the African plains, and they would meet maybe 4 to 5 strangers in their entire life. They would probably know 40 to 50 people throughout most of their entire life. They’d live with them, they’d hunt with them, they’d eat with them. It was small, it was tightened.

There’s a number of things that the mind evolved to do, and this brings me to biology. These trust relationships that were evolved in the mind also evolved in many aspects of biology. You’ll see symbiotic relationships where one fish guards another and the other fish cleans it (see right-hand image).
And for instance, with the case of the grouper and cleaner fish, the problem that faces the cleaner fish is that the grouper eats fish, especially fish its size. So how does the cleaner fish tell the grouper or make the grouper not eat it? Well, what happened – and I’m sure biologists can tell you more – is that essentially there evolved some sort of trust relationship.
And how the cleaner fish does this is essentially called the quiescence dance. It swims in front of the grouper and does this little dance. The grouper is then rendered into a slack jaw state. It just sits there passively, almost goes unconscious. It’s just some sort of trigger that happens in the grouper’s mind once the quiescence dance is done in front of the grouper. The cleaner fish then goes inside the mouth of the grouper, cleans out, gets its fill on bacteria and food and then leaves. Basically the grouper fish wakes up some time later and has no memory of what just happened, none. So this trust relationship basically evolved through natural evolution and is an instinctive behavior shared on both sides.

And so, these sort of trust relationships have actually been exploited through mimicry behavior in a number of different animals. There’s a number of different mimicries: batesian mimicry, mullerian mimicry, and aggressive mimicry (see left-hand image), which we’re going to talk about. Batesian mimicry is essentially a prey, say, a fish learns the scare-off tactics and behavior that a predator uses to scare off bigger predators. He then uses those to scare off predators with some degree of success.
Mullerian mimicry is basically groups of poisonous prey collaborating together. Distinct species – they learn because they have a common predator between the two species, or two, or three, or so many. They observe that essentially the predator strays away from something. Say, A and B are poisonous species, and Charlie is a predator. B observes that Charlie backs off from prey A after prey A exhibits some behavior, some scare-off behavior. Prey B then mimics this behavior to some degree of success at scaring off the predator.
So, aggressive mimicry is not for the purpose of scaring off the predator; it’s for the purpose of defeating the predator and eating the predator.

Now, in the case of Sabretooth Blenny, which is the fish on the bottom right (see right-hand image), the Sabretooth Blenny learned the quiescence dance. It is also a fish about the size of a cleaner fish, and it’s a pretty fish – it’s on the top right. That’s a dead one on the bottom right. It’s about as long as your hand to your thumb, and entirely half of it is a jaw bone. What it does is it swims in front of the grouper fish, does the quiescence dance. The grouper just slumps into a slack jaw state, and the Sabretooth Blenny goes in and just eats the inside of the mouth, gets its fill, can’t eat the whole grouper inside out, and then swims out. The grouper wakes up and has no idea what just happened, it just hurts like it’s a hangover, but from the mouth.
So, Sabretooth Blenny have actually evolved over the years to basically follow around the herd of grouper and exploit them. They don’t eat enough in any one instance to do a significant amount of damage, to cause it to die. They basically farm what they need at the time, but just enough to keep it alive; very parasitic and very interesting. And it’s very interesting because it exploits the evolutionary trigger in the grouper’s mind.
Persuasion: Exploiting Evolutionary Triggers

So, let’s delve into exploiting evolutionary triggers in human mind. I am going to start with a Harvard study that was done in the 70s on compliance (see right-hand image). The study of compliance has basically revolved on what is the absolute minimum we need to do or say in order to get someone to do us a favor.
For the test in this study, it was basically in the Harvard library and they had grad students doing the test, and they would approach people in the library who were already using a copier machine. The goal was to get them to stop and let them use the copier machine instead, to basically interrupt them. And so, the goal is to find what is a minimum needed to say in order to get them to comply with their request of: “Hey, can I make copies?” The control group is: “Hi, I have 5 pages, can I use the copier?” That’s it, no reasons given. And so, they would experiment here with basically: “Can I use the copier because of X?” then “Can I use the copier because of Y?” and so on.
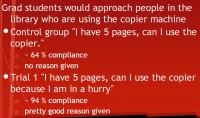
The control group: “I have 5 pages, can I use the copier” had 64% compliance, no reason given. So, hundreds of students were interrupted to see if they could use the copier instead, and 64% of them said: “Sure”. That’s not been done during finals week or midterms week, so I don’t know.
Trial 1 was: “Hi, I have 5 pages, can I use the copier because I am in a hurry?” This had 94% compliance, and that’s a pretty good reason: anybody can be sympathetic to that; you’re in a rush, you need to get somewhere, we’ve all been there. So, 94% of people would comply with this. So they basically have a super high success rate compared to no reason given. Then they had this range that they wanted to experiment with.

Specifically what they were trying to experiment with is: “Can we vary the lameness of our reason and explore how that affects the compliance rate range?” So they explored with more and more increasingly lame reasons, less compelling reasons (see right-hand image). And the results still yielded relatively high compliance.

And eventually they came down to their final trial (see left-hand image), in which just said: “We need to stop and look at what’s going on here, this is something amazing”. Because the trial was: “Hi, I have 5 pages, can I use the copier because I need to make copies?” Clearly, that is logically equivalent to “Hi, I have 5 pages, can I use the copier?” It’s completely specious reasoning, and they got 93% compliance, 1% less than: “I need to use it because I’m in a hurry”.

And this was baffling. We’re at Harvard, clearly these people aren’t idiots, what is going on? At the end of the study they effectively discovered that the magic word here is “because” (see right-hand image). The word “because” exploits this evolutionary trigger in our brain. Our brain is optimized for small tribal life, and it’s just like the Sabretooth Blenny: whatever follows doesn’t really matter. The simple existence of the word “because” statistically increases the chance of you complying with that request.
Obviously it’s not going to work every time, because we’re talking about statistics. In small tribal life there would be a few liars, and if they were found out they would often get exiled or shamed in some way. And so, given that we’ve basically only had 2000 years since civilization has been established and everything has changed, we still have millions of years of this code reuse from the evolutionary process in our DNA.
There have been other studies to find out quirks of the human brain, other than the magic word “because”. These 6 quirks I’m going to talk about are relevant to social engineering, because they can help you disclose info, they can help you get a job, and they can help you get a raise. And I’m going for a job interview tomorrow, so I’m probably going to be using these.
1. Reciprocity

So, the first one is reciprocity (see right-hand image). We tend to return favors regardless of the original favor. Even if we didn’t want the original favor, our brain is rather flattered by the fact that someone tried to do us a favor. So, this is exploited commonly by charities. Before they ask you for donating money, they usually hand you flowers or a drink, maybe bourbon, your favorite scotch or something, or snacks, or a souvenir. Then they ask for a donation. It exploits the temptation to give back.

Unfortunately, it doesn’t work for the Nigerian scammers, I just don’t know why. But this also works in negotiation (see left-hand image). When negotiating, if you make a concession and then ask for one in return, you’re more likely to have the person you’re negotiating with comply with you, regardless of what that concession was. You’re being seen as basically taking a step forward to make the process work, to make an agreement, and you’re giving something up.
This is commonly exploited in bartering: you see all these Pawn Stars and other ridiculous shows on TV that take over what should be some History or Discovery or learning show. In every instance of those people arguing about price, always the guy who’s the shark offers an outrageously high price first, or an outrageously low price first. So if they’re buying, they’ll offer the low price, if they’re selling, they’ll offer a really high price. And then the other person is like “No, I’m not doing that; most I can do (or least I can do) is that”.
And so when they make that first concession down to that top range of what they’re willing to sell this for or the bottom range of what they’re willing to buy this for, the brain is tricked into thinking: “Ok, there’s some progress here, we’re getting closer to an agreement”. Just by the very act of that one concession people leave the negotiation, the bartering feeling happier.
There have been studies where people were allowed to negotiate a price, and they’re getting ripped off in the same way. And there are studies where people have to pay a thought price and are still getting ripped off. But in the first trial where there’s negotiation they make it so it never drops below the second trial’s price. So you’re actually still paying more in the instance where you’re able to negotiate. And then they asked people after each: “How happy do you feel?” Everyone felt happier in case 1. Really interesting.

So, reciprocity can be exploited for initiating tricky conversations (see right-hand image), especially when asking for a raise, which is a tricky subject. If you’re seen as basically having done something for someone else – perhaps, done a favor for someone else: “Hey, I fixed that printer for you. Is this a good time to talk about my performance evaluation”, – it actually eases the initiation of a tricky conversation. And so, this can actually be used to get information disclosed perhaps about the target network, and so on, perhaps a boss’ schedule, I’ll let you guys imagine.
2. Consistency
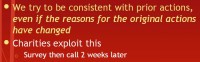
The next trick is consistency (see right-hand image). The human mind tries to be consistent with its prior actions, even if the reasons for the original actions have changed. Charities have really successfully exploited this, I think the American Cancer Society – there is a paper. I heard a story about American Cancer Society. What they do is they get a list of people that they’re going to call and ask for donations. Before they call and ask them for donations, they call them and they don’t identify themselves as the Cancer Society. They say: “Hey, we are center for American charity, and we just want to ask you 2 questions: would you be willing to donate a small amount of your time for charity that you like if you were asked to?” Mostly people say “Yes” to this. And then they ask some other irrelevant question to throw the trial off.
Two or three weeks later the ACS would call and say: “Hey, we’re the American Cancer Society. We fund cancer research, we’re for curing cancer in children and all sorts of people. Would you like to donate money to us? And if you do donate money, could you spend a little bit of time calling other people you know for us?” And they actually get a much higher compliance rate with that prior phone call than they do just by cold calling people with this question, because the human mind is tricked into being consistent with its previous decisions.
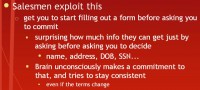
Salesmen exploit this (see left-hand image), and I’ve fallen for this myself. I’ve disclosed a retarded amount of information myself, especially when they visit me and it’s too early in the morning for my brain to start working. When they’re talking to you, they get you to start filling paperwork before asking you to commit, but still telling you the details: “Let me just get this paperwork started with you”. And as you start filling out, you probably leave some things blank, because you don’t want to give your Social Security Number right away, because you don’t know what they’re selling just yet.
And so it’s really surprising how much information you can get. You usually can get someone’s Social Security Number before you tell them what you’re selling. After they start filling out this information, the brain has unconsciously made a small commitment. Studies have shown that by using this paperwork technique they can get a higher sales compliance rate than just by saying: “Hey, this is our product, would you like to make a decision, yes or no? Yes? Ok, start filling out this paperwork afterwards”. They actually get a higher compliance rate because when you start filling out the paperwork beforehand, your brain has made a small amount of commitment and it likes to justify its previous actions. This is just an evolutionary flaw that our brains have.
3. Social Proof

The next flaw that our brains have is that we try to do and think what other people who seem like us do and think (see right-hand image). So this is why laugh tracks work. Everyone knows what a laugh track is, you’ve all seen some corny sitcom, and laugh track plays in the background, and you just sometimes also laugh too. So, laugh tracks are so effective that they even work when people who know about laugh tracks and know about this social proof flaw still fall for it. They still fall for it when they know it’s being used.
There have been a number of studies where they basically take a comedian and they have a control group where they play the comedian’s stand-up with no laugh track, no laughter. And they play the same comedian for the next trial with laugh track over. Everyone thinks in the second trial that the comedian is funnier. That’s just how the social proof flaw works.
Now, the social proof flaw also goes the other way. It’s the main reason for crowd theory. And it’s the main reason that if you’re going to have a heart attack, do not have it in a group of people. People like to act like the majority of the group. When something goes wrong, everyone is looking for what other people are doing, all at the same time, which is why when you’ve been trained in incident response and EMT stuff – not cyber incident response – you’re supposed to cut the ice, cut the anonymity, so you call 911, you get the water. It cuts the ice and it breaks the problem of human mind trying to do what other people are doing.
There have actually been a number of studies where the test subjects would go up to people and they’d fake a seizure. So they go and fake a seizure by a single person standing all alone. The single person will be like: “Oh my god, I should go down and help him.” Then they would do it to two people. It would take longer, about 30 seconds before someone would actually try and help, on average. I can imagine this to be on average: this means that some two people probably took, like, five minutes to throw up all the statistics and they’re probably sitting there laughing, being complete assholes.

And then you do it in a group, and no one will help, unless someone has a training to say: “Hey, you call 911, you do this, and you do that”. And so, it’s fascinating. This is also how riots work, because people on their own usually don’t go about protesting by themselves, unless you’re a Tibet monk. And they also usually don’t go off vandalizing things and burning cop cars by themselves and, obviously, trying to flip cars by themselves.
4. Liking

The next flaw that the human mind falls for is liking (see right-hand image). We tend to cooperate with someone who seems to like us. And this is how “good cop, bad cop” works, and it works so well, and I don’t even need to explain that.
It’s also exploited by salesmen: after a salesman closes a deal, he or she usually asks the customer: “Do you have any friends you can recommend that would be interested in this market?” And if they say “Yes” and they give a number, they’ll be like: “Hey, I’ll give you a 50-dollar gift card if I make a sale, or give you some sort of incentive for providing that information.” And the reason they give money and they give incentive to disclose that information is that the human mind falls with this liking flaw. Because when you get a call saying “Hey, I’d like to sell you this,” as opposed to “Hey, your friend Bob told me I should call you and tell you about this great deal,” you’re actually more likely to comply with someone saying: “Hey, your friend said this and that.”
Studies on the flaw I have delved into explore how lame your flattery can be in order to be effective. And it shows that there is some sort of strange inverse bell curve, where really accurate, good flattery is pretty effective, crappy flattery is not so effective, and then absurd flattery becomes more and more effective.
It does not make any sense for how the human mind works. Like, if I were to say: “You have really nice long flowing hair” – I just made you smile, it’s kind of funny, it’s wholly absurd, but it’s a little more flattering than “Your hair looks kind of ok today.” The brain interprets the very attempted flattery as flattering itself. And if you can get the person to laugh at the same time by being absurd, it’s actually more effective than being crappy in flattering yourself.
5. Authority
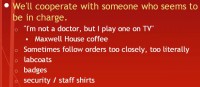
The next thing the brain falls for is that we tend to cooperate with someone who seems to be in charge (see right-hand image). And this is so well exploited by advertisements. We’ve all seen an advertisement say, like: “I’m not a doctor, but I play one on TV.” Right away he tells you: “You shouldn’t trust me.” I think, I’m not sure, some coffee company, I think it’s Maxwell House, did this, and it sold more of the product than any other company’s advertisement of all time. And so, this is basically the case study time for marketing to create programs, and no one has been able to beat it today.
There’s also a problem that this flaw often causes people to follow orders too closely or too literally. So, in the realm of social engineering for the purpose of penetration testing, perhaps there is a small little nuance in the terminology for their policies. You might be able to exploit that nuance by either impersonating someone who has an authority, or by citing someone falsely that has authority, saying: “You need to make this happen because of this, so maybe you need to let me in the server room.”
In the case of an upcoming merger, that would work perfectly: you already established yourself as someone who seems like they have authority. So, simply establishing yourself as having some sort of seeming authority makes you more trustworthy inside the human brain.
This is why lab coats, when people are wearing them in a commercial, look like it’s legit, as opposed to a bunch of people trying to sell you a pharmaceutical drug in a lab, and they’re just wearing jeans and stuff – they obviously don’t look like they know what they’re doing. So just by looking like you know what you’re doing, looking like you belong and looking like you might seem you are in charge, you get a higher compliance rate with generic questions.
6. Scarcity

The last one I believe the human brain really does fall for very well is the notion of scarcity and that we tend to overvalue apparently scarce-seeming resources (see right-hand image). This is why holiday Christmas toy crazes happen: “Oh my god, they’re all sold out, I have to buy it now, because it’s worthless after Christmas.” And this is why limited time offers work so well.
There have been experiments with cookies and jars, and every single time this experiment is replicated with normal people, it gets the same results. They take the same bunch of cookies in two jars, and they put, like, 50 cookies in one jar and 20 cookies in the other. And they go over to a supermarket or some place and they say: “Hey, we’re doing a taste test sample for a company. You’re allowed to try a cookie from both jars, but you have to form up in line.” And so the line for the shorter jar is always longer, and when they try the two, they always say that the cookie from the smaller jar always tasted better. And it’s the same damn cookie, it’s just that brain makes it seem so much better.
And so, in other aspects of the world, censorship is actually information scarcity. If you see knowledge that has been censored, your brain values it more. It could be something that is completely false, like: “Aliens were responsible for the Moon landing.” And if I were to censor that, even if it’s completely false, and people were to discover it, and discover the fact that I censored it, they would value it greater.
This can be used for counter-intelligence purposes quite effectively. This also backfires in court rooms: when a jury is asked to ignore dismissed/invalid evidence, when they go back to make deliberation, most of the people in the room can’t stop thinking about: “Why did they dismiss it?” and can’t stop focusing on that. And there’ve actually been studies on mock trials with legit juries that were called in for jury duty just basically science-funded by the judicial system that showed that this actually backfires more often than not. And it always influences their decision.

The scarcity flaw of the human brain can be exploited to gain access (see left-hand image). For instance, if you’re doing an onsite penetration test, you could say: “I’m only here until noon, so if you don’t authorize me to fix your problem, you’ll have to wait until next month for me to return.” Good luck explaining that to your boss. Exploiting scarcity is a great tactic for getting a raise. You can say something like: “You know, Google has been asking me to interview with them, just so you know…”

So, in reality these are just tricks that statistically increase the odds of compliance (see right-hand image). And they’re obviously not going to work every time. Who’s played DayZ? One, two, people know what I’m talking about. Anyone that has played DayZ seriously knows that it’s perhaps one of the greatest psychology experiments, or “should-be” psychology experiments in the world, because basically you start off, you’ve got nothing, and there are zombies everywhere, and they are insane, and it’s a fight for your life.
And so when you meet someone else that’s also in that fight for their life, the psychology of how you cooperate is influenced by who gets the gun first – it’s ridiculous. And so, people will often yell: “Hey, I’m friendly, I have supplies,” and unwitting survivors will come in and sneak into the building, waiting for the zombies, and then all you hear is a gunshot. I can’t count the number of times that’s happened, but it’s such a funny game.
This stuff won’t always work, because the magical word isn’t going to work 100% of the time. You can’t just say: “I need to fix stuff, so let me in the server room because I need to fix stuff.” I mean, it may actually work. If you ever do that in your life and it works, I’ll buy you a beer. That would be so awesome. It’s also definitely not going to work if you say: “Remember how you gave me a raise last week? Well, it’s about that time again” – to try and exploit the consistency flaw of the human brain. It’s definitely not going to work.

In reality, however, social engineering is usually the easiest way to get into a system to gain access to a network (see left-hand image). If you see the vast majority of breach reports and penetration reports, you’ll see that there are some aspects of spear phishing or social engineering that are always exploited somewhere in that attack chain, and it actually worked quite well and exposed way more information or access than it should have. And this is why post-exploitation spear phishing works so well: “Hey, I’m the CEO, could you give me my username and password to the system – I completely forgot, I’ve been drinking too much over in Vegas” or something.

How can you defend yourself and the company that you work for against this stuff? It’s really hard (see right-hand image). The best you can do is raise awareness of these principles, of these evolutionary triggers that can be exploited. And the best way you can protect yourself is practice by resisting advertisements – so you see some delicious food on TV and you find yourself in the drive-through line – steer out of it, practice resisting or something like that. And also practice by using these flaws on your friends.

The topics talked about today were from the book “The Psychology of Persuasion”, and a lot of my presentation was influenced by a brilliant scientist Philip Kegelmeyer (see left-hand image), and he gave a presentation two times over this Summer, and he gives this presentation several times a year, it’s a wonderful presentation, and you can view the video for it at this link: http://www.social-engineer.org/.
And so, there are actually technical toolkits to augment your social engineering tactics. Social-enginner.org is related to the Metasploit offensive security project, and they specifically focus on providing technical tools to augment social engineering. So, for instance, phishing scams, like getting you to go on a website and enter you login information, there are basically social engineering tools to take a website, scrape it, clone it and produce it in a working replica that can phish passwords and stuff, as well as taking company’s headers and papers and cloning them and email to make it look legit as well. So there’s actually a surprising number of tools that can do this sort of stuff, and they are actually quite effective.




























