
 Janice Niederhofer, founder and CEO of Peerage Consulting, Inc., gives a captivating presentation at RSA Conference, dissecting the subtle yet very significant components of online communication with scammers and other ill-minded individuals seeking preys on the Internet.
Janice Niederhofer, founder and CEO of Peerage Consulting, Inc., gives a captivating presentation at RSA Conference, dissecting the subtle yet very significant components of online communication with scammers and other ill-minded individuals seeking preys on the Internet.
Welcome to the session: “Luring Your Prey – The Art of Effectively Communicating with a Cyber Predator”. Today’s agenda is going to cover 4 basic areas on how to manage communicating with a cyber predator. Rapport – what is it, how to get it? Matching – and we’re going to match visual, auditory, kinesthetic, and language patterns. So, here we go.
What Is a Cyber Predator?

Very simply, cyber predators use the Internet to literally hunt for their victims. They hunt, they get on there and it’s like their playground, and they take advantage in any way of somebody who’s vulnerable, weak, has needs that they need to fill, including sexually, emotionally, psychologically or financially.
Now, in the cyber predator world we are all very familiar with cyber predators preying on younger victims. That’s a big deal and we don’t want to forget about that, they’re huge. And we have wonderful task forces out there, in the law enforcement arena, that are attacking these cyber predators who are looking for these young victims.
I also want you to keep in your mind that cyber predators aren’t limited just to the younger folks: you have cyber predators that are now stalking on all the social medias, chat rooms, in corporations, in inner workings of a corporation – they’re everywhere. As long as they have a playground and they can hide behind a computer to type away and search for victims – they’re good to go.
Now I’m going to give you an example of a cyber predator. I know someone who’s a 48-year-old female, and she was on Facebook, and this guy started communicating with her in a romantic way. And she has 2 children, divorced, ready to get into another full-time relationship. Well, this cyber predator manipulated her, feeling her needs, feeding back her keywords – all the things we’re going to talk about today is exactly what he did.
Eventually he got her to fall in love with him, and then the ball dropped. He gave her a big song and dance about how he needed money because he was in another country, so in order for him to be with her, she would have to send him a large chunk of change – that’s another type of cyber predator. So, cyber predators are anybody who’s taking advantage of the vulnerable, the week, somebody who needs something, the elderly – for goodness’ sake, the elderly are prey out there.
Cyber predators know how to manipulate their audience, whether the audience is one or more than one, in such scams. And they create trust and friendship through the use of their manipulation on the Internet to create friendship and trust where none should exist. And they manipulate their audience, their victims – I’ll call them victims from now on – in order to get what they want, whether it’s sexually, all the way to financially.
The ultimate goal is to stop a cyber predator, stop them in their tracks. Today it’s about luring them out through communication and stopping them. And the ultimate goal is to apprehend a cyber predator. Why we want to bring them to that is because we want to stop them and make an example out of them, because if you let them continue they’re going to find other victims. And if you have an opportunity, if you have the chance to stop a cyber predator, please, take advantage of it. And by all means, if you find yourself in this position or you find someone else who’s in this position in any context, get all the law enforcement; they’re really good at this, and work side by side, and make it happen.

Communicating with a cyber predator is exceptionally easy. Remember: it’s a human being behind that computer, and you’re communicating with a human being. And the trick is to get into their world, and we’re going to do it in a number of ways.
We’re going to realize if they’re visual, auditory or kinesthetic, and we’re going to speak to them in their terms, and we’re going to use their specific language patterns, and we’re going to get into the symbols, because Lord knows there is a ton of symbols out there in the Internet world nowadays. And the flow of the conversation, of the communication – how does it go?
The Invaluable Role of Rapport

The big umbrella for communicating with a cyber predator is rapport. What is rapport? I love this quote because it clearly states what rapport is, Theodore Roosevelt said it best: “The most important single ingredient in the formula of success is knowing how to get along with people.” And poor Theodore, he probably never thought that I’d be using his quote for this. But you’ve got to know how to get along with a cyber predator, communicate with them in their world so that you can lure them out, draw them out and get them where you need them to go, so you can apprehend them and stop them.

Rapport exists between you and a cyber predator, and it’s a medium and carrier wave in which communication and connection can occur. You’ve got to have that common wave of communication happening between the two of you.
And here is the deal: it intensifies outside of conscious awareness. What does that mean? Did you know that 4 billion bits of information come at us every second? Let me say that again. 4 billion bits of information come at us every second. Now, how do you process that? You don’t. In your aware part of your person, only 2000 bits of information can you process at any point of time. 2000 – what does that mean? This is what it means, folks: we’re only using 1% of our brain; 99% of our brain is the unconscious part of us, the unaware.
So, here’s the deal: you’re listening to me, you’re watching the video, you’re looking at the PowerPoint – that’s the aware part of you, that’s 2000 bits of information that you’re taking in. What about the other almost 4 billion bits of information? When I worked as an agent for the drug enforcement administration as an interrogator, they gave me a nickname – “The Terminator”. Why? Because I could get anything out of anyone anytime. Why? Because I spoke to the person’s unconscious part, the subconscious, unconscious, or what I fondly refer to as the “critter brain”, that part of you that drives you, that gets you to do things you don’t even know you’re doing.
Here’s an example. Have you ever driven somewhere and you get there and you don’t even remember driving there? That’s the unconscious part of you. And therefore, if I’m going to communicate with a cyber predator and I’m going to lure him out to apprehend him, I’m going to speak to that 99% of that person. That’s why I get my biggest bang for the buck. Why would I want to talk to that 1% aware part? Everything, folks, that we’re talking about today is addressing the unconscious part of the person.
Build Rapport, then Move Forward
For rapport to exist between you and a cyber predator, you have to have 3 things: understanding, appreciation, and respect in the interaction. And here’s the deal: don’t ever assume you have rapport. You’ve got to make sure. I call it “dipping your toe in the water”.
For example, to make it really simple: let’s say you have an intimate partner, someone you’ve known for a long time and you know each other well. And you come home one day and you walk in the door and you say: “I want to buy a new car.” And you intimate partner turns around and says: “What?!” Well, you didn’t have rapport. You’ve got to check it and make sure you have rapport.
Now, how do you apply that to a cyber predator? When you’re communicating with this, what I like to refer to as a cockroach, you’re communicating with this cyber predator, and you just spoke to them via communicating on the Internet yesterday, the day before, maybe a week before. When you start communicating again today, check in, build rapport, use some of the keywords and things we’re going to go over today, that you know he uses as the visual, auditory, kinesthetic. Build rapport, then move forward. Don’t move forward unless you have rapport.
Language, Symbols and the Flow of Conversation

Now, the quickest way to built rapport to get to that 99% of the person, the critter brain, the unconscious, subconscious part of that person, is three very specific skills that are simple, very simple to get. First of all, language: keywords are very important, phrases, and visual-auditory-kinesthetic.
The next part is symbols – for goodness’ sake, symbols are so popular out there on the Internet; you almost have to have a dictionary for symbols for the Internet.
And the flow of the conversation, the length of the conversation, the same tone and similar emotions is what the cyber predator has. So let’s break this down.
Now, you know that the umbrella is rapport, and under rapport we’re going to begin to match those three categories: language, symbols, and the flow of communication.
Match the Predator’s Reality

Now, matching, what specifically can we match? And what does matching mean? When you match the cyber predator’s communication, style of communication, if you will, then they believe that you know them in their world. Are they by chance a little different than you are? I would think so; maybe their values and rules are a little bit different than yours. But they’re going to begin to think that you know them in their world; that you appreciate and respect their life in their world. And they’re going to begin to feel that you understand what they value, which probably is going to be opposite.
And you’re speaking the same language. What do I mean by language? Not English, or Spanish, or Chinese; no, I mean the same communication language, the same world language, “you’re singing the same song” kind of language. Does that make sense?
There is appreciation, acceptance and respect in the interaction; and then when trust becomes appropriate and safe, when they feel that they can begin to trust, that they’ve now moved you into a solid victim and they’ve got you hooked, they’ve got you manipulated – then they begin to feel it’s ok to lower their resistance to outside influence. And guess who’s the outside influence? You. You’re the outside influence. And their main goal is to prey on you, manipulate you so that you become a victim.
VAK Senses

First thing you want to match, as I began to mention earlier, is visual-auditory-kinesthetic. Now, we all have 5 senses: visual, auditory, kinesthetic, olfactory, which is smell, and gustatory, which is taste. We’re going to work with the three main ones that you see commonly throughout written communication (see image). And keep in mind that all of us tend to favor one or two of these modalities. Like, I’m very visual-kinesthetic, I have to see it and feel it before I move on.
Visual, obviously, is the sense of sight; auditory is the sense of hearing; kinesthetic is two-pronged: it’s people’s emotions – you cannot not feel; and the other prong of kinesthetic is tactile – like bright lights, the heat, the feel of your clothing on your body. When we speak tactile, that’s what we’re talking about – emotion and tactile; kinesthetic.
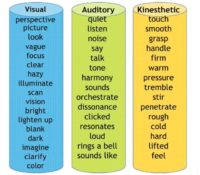
Now, when you read people’s written communication, they’re going to give you big clues of where they live, so to speak: whether they are visual, auditory, or kinesthetic, or a combination of a couple of them. And here’s just a few simple words to demonstrate, out of the hundreds of thousands of words that they can pick, to let you know if they live in the auditory, visual or kinesthetic world (see image).
Here is an example of what they might say in written communication: “I can see what you’re saying,” “Oh, I can get a good look at that”, “Did you get a glimpse of that?” That would be visual.
Auditory would be something as simple as: “Did you hear that?”, “I can really hear the sound of that”, “That resonates with me.” That’s auditory.
Now, kinesthetic folks – I love these guys – they’ll say: “Hmm, I can wrap my mind around that”, “That feels good to me.” They can mix the two, for example visual-kinesthetic: “I see what you’re saying and it feels really great to me.”
When the cyber predator begins to use this language, which is immediately, you begin to match it. For goodness’ sake, don’t mismatch it, unless you’re doing it for a reason.
Match the Language

The next part you want to match is language, when you match the cyber predator’s language patterns, what he is using, what he is saying. When he communicates with you, you can feed back exactly what the subject wrote with a brief preface, or you can use the exact sentence as summary, or a symbol, or whatever he has – you can feed back something specific in the communication.
You never want to go outside the frame of what the guy is saying; you want to stick in his world, you want to stay in the 99% of his unconscious brain; you want to stay in that and appeal to that part, because when you do, he’s going to feel safe, he’s going to trust you, and you’re going to be able to move him forward to where you want him to go. You can get him to do anything. I’ve gotten crooks to tell me things that they swore they wouldn’t tell anybody, and they had a lot to lose, including their entire life, all their assets, their family, everything; and I would get them to tell me the truth. How? By doing exactly this.
Keywords, here we go. When people communicate they choose certain words to carry the meaning and the values of their experience based on their model of the world, based on their world, based on their past experiences. These words have value for the person and they’re not choices.
When you speak you think you’re kind of creating new stuff – no, it’s all coming from up here, and they’re not choices. Whatever comes out of your lips, comes from your world, from your experience. Same with the cyber predator. And it’s their memory, it’s the memory that the cyber predator has of their experience, not ours. It’s what’s important to this guy, not what’s important to us. What’s important to us is stop the guy, obviously. But we want to get into his world and find out what’s important to this cyber predator, and speak to him in those exact terms.
Cyber predators are master manipulators, and will match your communication to enter into your model of the world to gain your trust. You become the victim because they’re so good.
Cyber predators are master manipulators, and will match your communication to enter into your model of the world to gain your trust and make you a victim. They hunt, they’re like a con artist. Have you ever met a con artist? Hopefully not. I have. They are phenomenal master manipulators. They can manipulate anything.
Let’s move on. Conversely, if you want to decrease rapport, you can deliberately mismatch. We’ve been matching the cyber predator’s communication and all the different elements up to this point. Now, if you want to break the rapport, you can mismatch their words, their writing style, their symbols – their anything.
Why would you want to mismatch a cyber predator? Well, here is an example; not limited to though. Let’s say you’re leading that cyber predator to apprehend him, you’re moving him out, you’re getting him out in the open, and you’re getting close. And all of a sudden he starts moving in a different direction, he’s barking up the wrong tree. Then you just simply mismatch, instead of saying: “Listen, I don’t want to do that” – for example, straight up, now you broke rapport, massively. Well, I don’t want to backtrack that far, I don’t want to get my feet in cement. I want to move forward quickly, so I will speak to his unconscious part, the 99%, and I’ll tell the cyber predator by mismatching a keyword, mismatching visual – if he’s visual, I’ll do auditory; I will mismatch certain parts of his communication – doesn’t really matter what, to let the unconscious mind know: bad boy, bad boy, you’re going the wrong direction. Then you come right back and you begin to build rapport again and lead him where you want him to go. It’s a pristine tool, don’t forget about that.
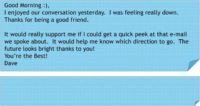
Now I’m going to give you a very distinct example to pull in – the symbols, languaging, VAK. I’m going to be looking at the screen so I can read this with you (see image). “Good morning” with a smiling face on top would be the predator. The communication on top is the cyber predator; the communication below would be you communicating to your cyber predator. Now, the opening: “Good morning” with a smiling face.
Response – exactly the same; match it. Now, if you noticed, there’s no space between “Good morning” and the first sentence with the cyber predator – match it, this is the flow of the conversation. Don’t put a space there, match it, remember that you’re dealing with this unconscious critter brain.
Now, the cyber predator says: “I enjoyed our conversation yesterday”, and you’re going to reply something close to this: “I too enjoyed (keyword) our conversation (keyword).”
And now we’re going to combine the sentences, so go back up to the cyber predator, and the second sentence is: “I was feeling really down.”
Now you combine both sentences, no problem with that; but you’re matching him massively, very distinctly and skillfully, and you say: “I too enjoyed our conversation, and sorry you were feeling down.” See the emotion? Completely matching it.
Now he feels like you’re singing the same song. Then he says: “Thanks for being a good friend.” And then she says: “Glad I could help, that’s what friends are for.” She’s acknowledging the friendship. Now he thinks he really has her hooked.
There is a space between the first and second paragraph; you do the same. Just match the way the communication is visually written on the correspondence.
Now he says: “It would really support me if I could get a quick peek at that email we spoke about.” And she says: “I would really like to support you (match the word Support). Can you give me an idea of which email you want a peek at.” She didn’t say anything like: “What correspondence do you want to read?” That’s a complete mismatch. She completely matches him and stays in his world.
By the way, this is a corporation. Two different corporations: a cyber predator is in one corporation, because there is that type of cyber predators out there; and she’s in another corporation, and he’s trying to get ideas from her, from the inside. So he’s trying to break confidentiality, that’s what’s going on here.
Now, the last sentence. He says: “The future looks bright, thank you.” And she says: “Good to know your future looks bright”, completely matches him. And he signs off: “You’re the best!” And you’re going to do the same. It doesn’t have to be identical, but look how close it is: “All the best.” And then no space, and sign off.
Even if you just look at this correspondence, it just looks the same, and it flows exactly the same, and it ties in the symbols, keywords; the guy is very visual and kinesthetic, and you just respond to him in visual-kinesthetic words, and it’s identical.

So, what you’ve accomplished, the summary, is this: you’ve accomplished building rapport with the cyber predator by getting into his world, very strategically, skillfully, and it’s so simple to do. And when you do this, the guy then feels totally safe, he lowers his resistance, out he comes, and you can start doing whatever you want with him: you can discover him, you can bring him out in the open, you can pretty much do whatever you want with this guy. So, there you go.
Thank you for your time today, it was great fun for me and I hope it was great fun for you. If there’s anything I could ever do to support you, just find me. Thank you!





























I have went through this very thing quite a number of times These people are despicable.
This idea was done by our website in 2005
http://blogcritics.org/scitech/article/the-lures-of-the-online-predator/