
The fundamental logic of the VPN technology comes down to covering one’s tracks online. Great VPN comparison websites like VPNRanks offer deep insights into popular VPN services to choose from.
Essentially, VPN is a secure tunnel used to transmit encrypted data. It prevents your ISP from snooping on your browsing history, web search requests, etc. Furthermore, it keeps your actual IP address secret by replacing it with a VPN server address when you are visiting a site. The stars seem to align and it looks like there is nothing to worry about. Unfortunately, things aren’t really that way.
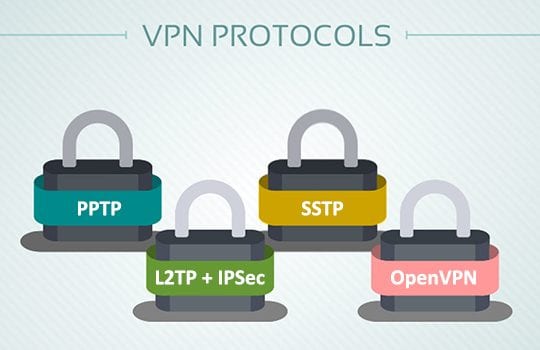
Commercial providers leverage the following VPN protocols nowadays:
PPTP is the most commonly used one. It’s fast and easy to configure but doesn’t provide as much security as the rest.
L2TP + IPSec. L2TP does the data “transportation” job, while IPSec performs encryption. This combo boasts a more reliable encryption than PPTP and has hardly any vulnerabilities PPTP is susceptible to. It also ensures message integrity and stronger authentication.
OpenVPN is safe and open source – no wonder it’s one of the most popular protocols. It allows you to circumvent a lot of locks and restrictions. The only caveat is that you need a separate software client to use it.
SSTP delivers just about as much security as OpenVPN does while not requiring a separate client.
Predictably, most people use free VPN services. These solutions tend to leverage the PPTP and OpenVPN protocols. If there is no separate VPN software client installed on your computer or tablet, then you are most likely using PPTP. As mentioned above, this protocol is the least secure one available.
At this point, I will explain what happens on the browser level when you are visiting a website. Every time you enter a site URL in the address bar or follow a link, the alphanumeric domain name is converted into the site’s IP address, which is a 32-bit number string. The common pattern of an IP address consists of four sets of numbers with a value from 0 to 255 separated by dots, for example, 175.164.0.9. This is the conventional structure of what’s called the fourth version of the IP protocol (IPv4).
Meanwhile, not everyone knows that there is also the sixth version (IPv6), where IP addresses look different. They consist of eight strings of four hexadecimal characters separated by colons, for instance, 2001:0db7:74a2:0001:0000:6a3e:0170:8865. Importantly, the IPv4 and IPv6 protocols are incompatible.
Keep in mind that some VPNs do not support IPv6.
How does this affect your online security? Let’s suppose somebody wants to find out who you are and determine your whereabouts. They can set up a phishing site that resembles a popular cryptocurrency wallet service – for example, blockchain.info – and assign it an IPv6 address. In case your VPN doesn’t support IPv6 protocol and you go to that site, its owner will see your real IP address. Likewise, your ISP will know you visited that particular web page.
Whether you use VPN or not, be sure to exercise reasonable caution when surfing the web. Refrain from clicking on links received from questionably trustworthy sources, otherwise, you may put your privacy at risk or get infected with malicious code.

To be confident in your anonymity, figure out what VPN protocol you are using and whether the service supports both IPv4 and IPv6.
If you are privacy-minded and use a VPN service during your web surfing sessions, your anonymity may still be at risk due to a gaping security hole discovered in WebRTC (Web Real Time Communication). This is a feature built into web browsers to support voice and video calls without any third-party plugins.
A few years ago, a group of researchers unearthed a critical flaw in this standard that might disclose sensitive details of VPN users. Specifically, it allows websites to reveal the actual IP addresses of visitors, even if they are browsing with VPN enabled. This bug is an issue for major web browsers, including Chrome, Firefox, and Opera, and it appears to affect Windows operating system only.
Consequently, advertisers, media services and governments can simply use a few lines of code to make requests to STUN (Session Traversal Utilities for NAT) servers, which will return your real IP address. Although there have been no official reports of online services taking advantage of WebRTC leaks, it continues to be an issue – unless, of course, you use a secure VPN solution and an up-to-date browser.
In order to check whether you are affected by this glitch, consider visiting the ipleak.net service when you are connected to your VPN, and you will see whether or not the IP address displayed on the site matches your genuine one.
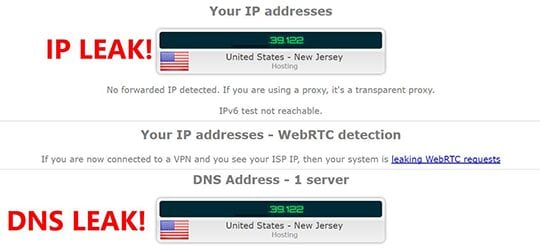
Another concern has to do with logging. Most VPN services use the “no logging” mantra as part of their marketing strategy. Of course, you don’t want your online activities to be logged by any party, including your VPN provider. Unfortunately, these might be misleading claims.
Whereas some vendors maintain logs only to troubleshoot connections, handle DNS requests, thwart abuse, or restrict VPN accounts based on your subscription, others may do it for outright surveillance.
Therefore, it’s definitely a good idea to find a reference on your VPN provider’s website that explains what types of information they harvest about users and what exactly they do with it. If they retain too much data, your privacy might not be intact.




























