Jeff Bardin, the prominent cyber security professional and consultant with enormous background in intelligence, risk management and information security, shares his expertise at Hacktivity conference, delving into the methods and tools for open source cyber intelligence.
Conference Host: It’s my honor to introduce to you our first speaker, our first “rock star”. His name is Jeff Bardin. Jeff was awarded for Excellence in the Field of Security at RSA Conference. And today he’s one of the most recognized experts of cyber crime and cyber security worldwide. He is currently the Chief Intelligence Officer of Treadstone 71. Jeff sits on the Board of Directors of Boston InfraGard, Content Raven, Potomac Institute for Policy Studies, Journal of Law & Cyber Warfare, and Wisegate. And he was also the founding member of the Cloud Security Alliance. So, he’s a very well-known security expert. Moreover, he’s an Adjunct Instructor at Utica College; he is an instructor of master programs in cyber intelligence, counter-intelligence, cyber crime and cyber security. Today, in his presentation, he will cover open source intelligence, and he will talk about the methods of cyber espionage, sock puppet creation, infiltration, data collection, and data analysis.
Jeff Bardin: Morning! I’m not really a “rock star”; I don’t look like it, do I? I don’t have long hair; I have a belly – most rock stars don’t. But he talks about my background in cyber security. There was a time a long time ago where I was actually fired from a job because I hacked a mainframe in a VAX/VMS system1. Anybody here know what a VAX/VMS system is? There’s a few of you; most of you probably weren’t even born when I was fired from that job.
Anyway, today we’re going to talk about open source intelligence, and most of you here are looking at the cyber security arena from a hacking perspective – that’s why you’re here at Hacktivity. But the things we’re going to talk about today are a little bit different than just plain hacking. It’s how you get in to somebody’s site, or someone’s forum, or Facebook sites, and become resident as a friend to them, and stay there for years.
Since around 2005, I’ve been creating sock puppets, and most of my targets have been cyber Jihadist sites. My background – I was in the United States Air Force and I was a cryptologic linguist in Arabic language, and so I’ve carried that forward into the cyber world and been able to create these different sock puppets out there, or cyber personas, to access their sites and actually become one of them for quite a period of time. So, today we’re going to talk about some of those things, and I’ll actually give you some things to take with you so you can actually do this yourself, if you so choose.
So, today there’s a lot of different threats out there that we face (see right-hand image), but all of these are different types of threats that impact our cyber security. But there’s only one that we’re really going to talk about today that I believe covers all of these areas, and that’s actually Clandestine Cyber Human Intelligence.
That’s where we’re taking traditional spy tradecraft from the physical world and we’re applying it to the cyber world. And there’s a lot to be had in this area if you know how to go about doing it, so we’ll give you just a few tips today.
When you want to go and start to become a cyber spy, you have to create your sock puppet, your cyber persona (see right-hand image). Some of the first things you do is you create email addresses, you create who you’re going to be. Has anybody here ever acted in a play or been an actor, anyone? So, if you’ve been an actor, you definitely understand that you have to fit yourself into the role. When you create these cyber personas, you’re going to create many of them; not just one, you’re going to create several of these personas. We’re going to talk about that as well.
We’ll talk about anonymity, just briefly, because you want to maintain anonymity about your IP and who you are online so that people don’t know who you are when you’re actually penetrating their site. We’ll look at some other things: prepaid phones, establishing Twitter and Facebook accounts, YouTube, LinkedIn, and establishing your persona across the Internet so that it really ties together, so if you’re publishing something on Twitter it follows up on Facebook, it aligns with your resume online, and all these different resumes.
Some of the things you also need to do is really understand your targets; historical, cultural, linguistic and political background, so when you’re online talking to them you can actually refer to things that make sense in their view.
So, those are some of the things we’re going to talk about, but the main thing when you do this is actually patience; it takes a long time. There are sock puppets I’ve had out there for many years, and these sock puppets are still active today, and I have some sock puppets that are very active in the Twitter world, that I’ve actually had interviews with the press through my sock puppets, so it’s pretty interesting, some of the things we’ve done.
But it also follows the cyber intelligence life cycle. Intelligence life cycle is: you get your target, and with your target then you start to collect information; you produce that information and organize it in such a way that you can actually analyze it, and then, when done analyzing it, you produce a document that comes up with recommendations and opportunities, which can actually feed back into the cycle.
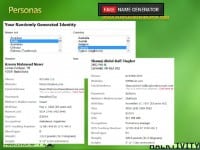
When you create a sock puppet, if you’re having a hard time with this, you can go to fakenamegenerator.com and start with your own sock puppet (see right-hand image). It’s a great space to go to. You put in what you’d like, whether it’s Australian, Chinese, Arabic, male or female, and it gets you a good start in creating your sock puppet, which you can then start loading up into an Excel spreadsheet.
But you have to add more things into this, you have to tell all about yourself in there: what your education level is, what your interests are, your religious preferences, your political leanings. And all of that needs to be in line with the people you’re going to target, or the foreign intelligence services, or the different folks that you’re after out there.
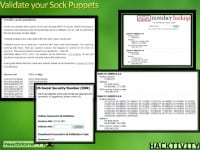
And when you do this as well, at this site, fakenamegenerator.com, you can also create credit card numbers that aren’t real, but they will pass a sniff test: MasterCard, Visa – they’ll look like a real credit card; they’re not, but they will pass the first test if someone is looking to validate your credit cards out there. And you can get those right off of fakenamegenerator.com as well (see image to the left).
They will also generate for you in the US and Canada what’s called the Social Security Numbers or national identity numbers that you can use. So, it’s a good little site that I recommend you go to when you start creating your sock puppets, so you can start creating this persona that will get you into their sites.
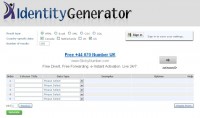
There’s another site called Identity Generator that you can go to as well (see right-hand image). This one is not quite as detailed as fakenamegenerator.com, but it’s still a good site to go to. You can put in certain parameters, as you can see here, and it can export it out to .csv or SQL, if you want to really build a huge database of sock puppets; and what you get when you create it is just a whole list of names, addresses, emails. To get the email you have to go out and actually create this; it does not automatically create it for you. But it gives you a good start.
This is kind of a spreadsheet that I use that actually extends (left-hand image). I have about 39 active sock puppets, so sometimes I forget who I am and my names. If you’re actually psychologically challenged or schizophrenic, this is good, because you’re used to having multiple personalities.
But when you create these sock puppets, again, they’ve got to be key towards your target, and they have to talk to what sites you’re actually using this sock puppet on, and who you are friending on those sites. And sometimes it becomes tough to keep them separated, but it’s something you have to do, it’ll at least give you an idea of what you’re using out there. These are actually some I’d used in the past and I’m no longer using; but blood types, height, weight, you name it – you want to detail this out as much as possible so you really know who you are when you’re doing this.
Now, when you want to become anonymous, there’s a lot of different things out there, and these are just a few tools – most of them are free, some of them cost – that you can use to hide your IP. Some of these plug right into Firefox; they can plug into other tools out there as well. If you really want to find these, you can just go into Firefox extensions or add-ons, and search for “anonymous”, “anonymity”, and it will give you a whole listing of tools.
Some of these are like IPredator that was used by LulzSec and Anonymous. IPredator is actually a VPN out of Germany, and it costs a few bucks, but Anonymous group and LulzSec actually used this to try and penetrate my site and actually get into other sites. So, if you see IPredator coming into your website when you look at the logs, I’d be a little bit worried, because it usually means someone is after you.
Crypto.cat is a tool where you can have encrypted chat back and forth, and when you’re done with that chat, about 30 minutes later it just all goes away. There is no record of it; it’s a good little tool to use as well. There is one here called CoDeeN that is actually a proxy server out of Princeton University that you can plug into your browser.
Either way, of course you want to use a virtual machine to set up in case you go to a site and you might get infected, possibly; this way you can just wipe it clean. There’re multiple different ways to hide your IP, but it’s really required when you want to make sure that your IP looks like where you’re coming from. Some of these tools out here allow you to fast flux your IP, much what botnets do; your IP will change every so many minutes and jump around the world to different locations, and change your IP just like in fast flux on a botnet, and it’s hard to track it down. You will never lose your connection when you have this type of solution out there. Most of those cost, but you can actually daisy chain some of these as well.
So, you’ve got your sock puppet; you can set up a Windows-based machine. This is kind of a sample of that (see right-hand image); I know a lot of folks here probably use different types of Linux and like command line interface, but in hacking that’s probably more appropriate; in more of the cyber intelligence arena you don’t need to have that, because you’re not going to hack them, you’re going to get inside and become them. This is a sample set up with a Windows 7 machine, setting up a virtual machine and using different Tor solutions out there that hide your IP.
When I first started doing this, this is an example of some of the things out there that I’ve done. One of the targets I was after was Anwar al-Awlaki, who’s no longer with us, and the target here was his sermons – his talks that were all recorded in MP3. I wanted to find them and find the sites that were actually hosting these sites. So, he was my target.
I went to this tool called touchgraph.com (see image). This tool costs 4000 to 5000 dollars, but if you look on the site there is a little button that says Demo. You click on that, and actually you can operate some of the tool there, and it’s a linked analysis tool.
So, I put in his name, which is right in the centre of circle, and I hit Enter, and it explodes out into this Java screen, that every circle I can double-click on, and it explodes out into more screens. And it actually goes out and analyzes the name and where it finds it throughout the Internet for you. It saves you a lot of time in trying to find where Anwar al-Awlaki has been popping up in different sites.
When you look at this, you say: “Ok, where am I going to find his actual sermons out there?” And I don’t think it’s going to be at Huffington Post or New York Times. I don’t think I’m going to find his sermons there, right? So, I can eliminate those pretty easily. I keep going through these, taking a look, and he probably won’t be there. But what I will find is that he’s probably at sites like Kalamullah, or Anwar Al-Awlaki, or Salaat Time, or even Hoor-al-ayn.com. These are typical sites that might have his information on them. Makes sense to take a look at those.
This tool can also come out and give you URLs, and it ranks the URLs by the number of times his name pops up. So, I can take a look at these URLs and say: “This looks like somewhere I want to go with this tool that is actually costly but free.” So, I’ll use that and I’ll start going through these URLs. This is a very fast way to find out where your target may be hiding information out there, or have data.
So, you go to this site, and sure enough I can find that here are all his sermons on the front page of this site (see right-hand image). You would think it was just a very benign site, but underneath it you’ll find all the sermons, all in MP3 for download or on DVD if you want to get those. So, an easy way to target and find out is using tools like Touchgraph.
In addition, there’s a tool called Maltego if you go to paterva.com. Have any of you heard of or are a member of the Cult of the Dead Cow, hacker group from a while back? They’re an older group. They created paterva.com and this tool called Maltego (see left-hand image). It’s another great link analysis tool; there’s a free version of it, called the Community Edition that you can download and use.
With that tool you can go find out information on email addresses, Twitter accounts, phone numbers; it actually builds these links out for you. It takes a little bit to learn this, but I recommend taking a look at this if you haven’t already. It can help you find some of these different tools out there. Silobreaker is another tool that helps you with some different links and getting your information together.
Now, once you find their sites, being hackers you want to hack the site, right? Isn’t that what you want to do? You want to hack it, but if you are in cyber intelligence, you don’t want to hack it – you want to get inside it. You want to become a member of that site and somebody that is very respected in that site.
At one time I had multiple different sock puppets on a cyber Jihadist site; one of them had a lot of experience on this site and was well respected. And I had another junior member on this site, and I wanted to get another layer into this site with my senior member, so what I did is I set up my junior member, my other personality, and I made him make some things that were contrary to bin Laden. He said it online. And over here at my senior sock puppet I called him out, got him kicked off this site, and because of that I got better street credentials on this site. So, it’s a way that you can use tools and techniques to get in and penetrate further into these different sites.
In addition, there are tools out there that you can use, where you can actually target a site, and you can download the whole site if you know how to configure this tool, HTTrack (see image). There are some ways you can configure, where you can bypass the robots.txt and you can copy the site in mass, and it may take a few days to do it, and you’ve got to be careful so it doesn’t go too far out to copy other sites. But you can get SQL server databases, PDF files, everything that you can then gather as you’re collecting this information, so then you can go through and produce it, and organize it, pull out what you want, search it, index it, and start organizing this information before you start analyzing it. So, HTTrack is a free tool as well that you can use, and there are some configuration settings that are actually fairly easy to find, but doing this with your anonymizers, hiding your IP, is a good way to go and download these sites before you go in.
I mentioned earlier the historical, linguistic, cultural, political types of aspects. It really pays to know your target inside and out. Sun Tzu said a long time ago that you need to know yourself in war, but you also need to know your enemy. It’s the same thing here: if you understand this, you can use these different aspects of your target to penetrate.
The example I’m going to give here is on the cyber Jihadist site; that will cover you through this. There are certain historical aspects that you need to know (see image), like the Five Pillars of Islam. You need to know these inside and out, whether it’s Arabic or English. And the Sixth Pillar is Jihad here, and we know Jihad for the most part as being a holy war. But Jihad in fact is a word that comes from ǧihād in Arabic that has the meaning of “struggle”. And we all face struggles in life. There’re different types of struggles: economic struggles, intelligence type of struggles out there. And so, understanding this, you understand it’s more than just holy war, it’s a background of struggle that we all face, and it’s something that is very prevalent in the Holy Quran.
In addition, you need to know things what’s called Minhaj (see left-hand image). Minhaj actually has to do with the Salafi view of Islam, that Islam was perfect back in the days of Mohammed, peace be upon him, and that there should be no change because of modernity, and any modernity attempts to change Islam as it was. But these are the types of questions you may be asked to get further into some of their sites. You need to be prepared to have this understanding to get into the site. You may have it with different targets out there, wherever your adversaries are; you need to know this type of information in order to answer the questions to get you further into their sites and be accepted.
There’re also different personality types that you need to know about who you’re talking to: things that are relative to the culture that you are targeting, or the people who you are targeting. In this case, there is a concept here called Taqiyya (see item 3-c on the right-hand image) that’s been referenced in movies, the two here: “Body of Lies” and “Traitor”. Taqiyya is such that it’s okay if you’re a Muslim living in a Western land to drink and smoke and sleep with women, as long as the end game is in the eyes of the Salafi view of Islam; it’s okay to do that, and that’s called Taqiyya in short.
So, understanding these personality types of who’s online, you can use this information when you’re in their forums with your sock puppet to help penetrate further and represent that you are, in fact, one of them. Again, this is an example on the cyber Jihadist site; you could do the same thing in any one of your targets that you so choose to go after.
There’re social and cultural values you’d need to know (see left-hand image). So, if you don’t have this skill, maybe you’re more skilled in targeting and collecting, and you’d have someone else who is a subject matter expert in that area help you devise a scheme with your sock puppet to get deeper in so you can actually start leveraging the open source tools and collecting the information, and building out your personality and who you are online when you’re on these sites. It’s very critical to do this.
Other activities in this case are the 99 names of Allah or the Call to Prayer that you need to know (see right-hand image). In addition, there’s, again, the Life of the Prophet Mohammed, peace be upon him, that you would need to know: every aspect of his life, and every war, and every major issue you would need to know so you can reference this online when you’re having these conversations.
It pays to have that historical background, that cultural understanding. So, if you were to target the United States, you would have to look at us from a cultural perspective, look at us from a historical perspective, build the cultural aspects, know the language and be able to understand us, so when you’re on our sites, like many people are, because we are hacked like there’s no tomorrow, then you have to know these things to get in and get in deeper, because you’ll reference these in your conversations.
And you have to know the biographical vignettes of the Prophet as well, and you need to fully understand everything that happened in his life, because it becomes a matter of speech on these sites. You also need to know all the different contemporaries that surrounded this person back at that time. As I’m giving you the examples here, just from the cyber Jihadist perspective, it pays to understand and know this, because you will be quizzed on it. You will be tested when you’re on these sites.
People are going to come after you and ask these types of questions. And if you can’t answer them, then you will be exposed; you’ll be exposed as someone who shouldn’t be there, and you’ll be kicked out of the site, and all this work that you’ve done, all the hours, the months, the days that you’ve spent, will be for nought if you make a mistake that way, whether it’s a mistake of not using your anonymity and exposing your IP, or making a mistake in your conversation from a cultural, historical, even linguistic perspective.
And there’re different characteristics about Mohammed, peace be upon him, again, that you need to know, as well as some of his background; you can get some understanding here about him also, the fact that he had 14 wives. I feel bad for the poor guy if he had 14 wives. How many people here are married? How many people here have been married more than once? How many people here have two wives? Two husbands, anybody? 14, it’s just amazing; you need to understand all these things as well: the names, the names of the children, when they were born. All pays because it comes up in conversation; or you can bring it up in a conversation to find out if the person you’re talking to is next door in the house next to you possibly. It pays to have this information and this background on your targets.
So, now that you’ve got your sock puppet created, you’ve got your anonymity in place, you’ve got your cultural, social, political background and linguistic understanding, religious understanding, you can use these open source tools. I’m going to cover a few here and go through some examples. If you want to find adversaries, they’re on Facebook, they’re on Twitter, they’re all over the place.
This site (see image) is no longer up, the Mujahedin channel; it’s long gone. But at the time I actually used one of my sock puppets to friend this channel, and you can get the list of folks here that you can actually start following them, and they follow you. You follow their Twitter accounts, you get to know who they are. And there are some different tools that you can use to actually track this information; tools that give you trending and tendency analysis as well as link analysis, as you go down the road and try and make this happen in a way that doesn’t bury you with information.
Because when you use this type of technique, open source intelligence, you’ll just be under a huge amount of gigabytes of data. So much information makes it difficult to actually sort through it. But some of the tools you’ll use will sift through that and give you this information in a much faster way.
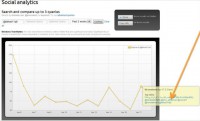
So, when I look at the site, I feed it through a tool called Topsy.com (see left-hand image), and there’s some social analytics there, and at each peak of this graph I can mouse over it and it’ll highlight some of the activities and who they are within this tool set. In his case I find Abulhasan and some others here, so now I can track those folks on Twitter or possibly on Facebook and start looking at them as they pop up, as they’re referring to some of the words here that I’ve put in.
This gentleman here is Fahad11q8 (on right-hand image). When I stated tracking him, I used this tool called Twopcharts.com, and it gives me all these capabilities where I can compare him against others, I can see the images that Fahad11q8 has used, I can see the frequency of his tweets, when he tweets, the time of day, what he tweets about, who’s following him, who he follows; I can look at the first 10 tweets, the first 10 followers. There is a great deal of information just in this one tool. I can compare his Twitter account against another Twitter account, and overlap them, and see the similarities in it, and it saves me a lot of time.
So, I look at Fahad11q8, I get some information about him, and I can also take this out to his Twitter account and see that he’s on Twitter, where I can go and look at more images there, and get an idea of what his content is, if you can read Arabic or run it through a translator. Regardless, I can see the types of images that Fahad11q8 is using – it gives me a better idea: is Fahad11q8 a cyber Jihadist or not? That’s what I’m trying to determine here. Or is he just someone interested in this; or is he an active participant; or is he, too, a sock puppet like me, trying to gather information? You have to determine this, and you have to look at relevancy of your sources to make sure that your sources are valid. And that can be difficult sometimes.
Regardless, I start looking at some of his images, and I pull this up, and this one here is actually about a Muslim brotherhood in Syria. And I look at another image here (see left-hand photo) and I say: “Ok, where does this image come from? How do I find out where this information comes from, where this image originated from?” Well, there are some great tools out there as well for that. They plug right into your browser, whether it’s Chrome, Internet Explorer or Firefox, or you can upload it directly to the site.
I can use Google, or I can use a tool called TinEye. I right mouse click on the image, send the image out to TinEye. TinEye will go out and search 2 billion records of images in about 4 seconds to find out that this particular image was originally located on a well-known Jihadist website (see right-hand image). And so I’ve got a good idea now that Fahad11q8 has activity on that particular website, that forum. I go on to the forum where I’ve actually already established a sock puppet, and I start to find that he is there, and I start having conversations with him, so we start building a relationship. In the meantime, I am following him on Twitter; I’m hashtagging; I’m retweeting some of his tweets. I’m also cozied up to him on Facebook and we start building this relationship out there.
The other interesting piece there, and I’ll show you: some of the tools that you can take with you are actually in this PDF (see attached Zip file). There’re 33 pages of tools out there that will be made available to you in this PDF, and they just go on; some of them are link analysis tools, some of them are Google tools.
How many people here search using Google? But if you know how to really search on Google – some call it Google hacks – you can find information like that. If you don’t, then you’ll be searching and you’ll never find the information. But if you use particular Google search tools, the capabilities, then you’ll actually be able to find information very quickly if you know how to do this.
I want to make sure that you get those tools so that you don’t get yourselves in big trouble when you go out and create your own sock puppets. I actually created sock puppets on Facebook to follow my kids when they were in high school, so my kids don’t like me very much when they find that I have more friends on Facebook than they do; at least my persona does. But I find out where the parties are, who’s in trouble in school, who’s pregnant, who’s drinking, where the parties are – I find out before they do.
So, when they go to that party, I’m just sitting there: “Hey, how you’re doing?” because I’m already there. So, if you have young kids, I urge you to create a sock puppet on Facebook and go out there and friend all of their friends, because the whole game in Facebook is the more friends I have when I die more than you, the better person I am. That’s it, that’s how it works. So, you can use this not only for adversaries, you can use it for your kids.
As a matter of fact, a friend of a friend of mine was going through a divorce, and he thought that he had this really locked down: his wife had been sleeping around on him, embezzling money from the business. But every time he went to the judge, he got a setback. He thought he was going to have an opened/closed case through the divorce, and he would get the house and everything, but every time he went to this judge, he got a setback.
So, he asked a friend of his, who had actually gone through the cyber intelligence courses that I teach, to help him see what’s going on: “I can’t believe what’s happening here.” His friend used some of the tools and techniques here to find out that the judge was sleeping with the guy’s wife. When he found this, he presented this to the judge, and then the divorce went his way very quickly. I’m not saying that you should do this; I always maintain legal aspects of this. If you want to be unethical, that’s something else; but maintain legality around these activities.
Another thing I’m going to mention is that you need to validate your sources. This can be kind of difficult. Sometimes you find that everybody’s saying the same thing, and as you take this down, you find that it really came from just one source. That’s not enough; you need more than one source. You need to be able to rate your sources and determine: are they valid; are they credible; is this something I can bet on; and how do I rate these types of sources out there?
There is a reliability and validity rating scale that you can use (see image). Some of it starts with a bottom – you know, it’s kind of ok, it’s relative to a certain degree. But they are largely unreliable; there’s great doubt, so I need to reference that, because as you analyze, you need to make sure that you’re referencing information that is something you can stand behind.
As you go up the scale, it gets better and better as you move towards the top, so you can use this reliability scale from usually reliable – completely reliable – to improbable, doubtful, confirmed and validated. There are some sources out there. How many people here have heard of the hacker called The Jester? If you follow the folks from SecureNinja, they’re actually doing a Q&A online off their YouTube site. They opened this up lately; you can actually ask questions online, they will organize this and have a little contest.
But a lot of people wonder: “Is The Jester real? Is he reliable?” And usually, if you look at what he says, he follows it up by knocking down the sites that he says he’s going to knock down; so I would look at him as definitely a very reliable source and someone you can trust: if he says he’s going to do something, he’s going to do it. If it’s targeting against you, then you’d better shut your site down and run, because he’ll definitely hit you.
But take a look at the SecureNinja folks, because they’re starting this: if you want to have this conversation with them, they’ve got a video out there that Alicia Webb has actually done, and you can actually have this conversation. But the source reliability is something you need to really take a look at, because if you’re actually doing your targeting and analysis for a policy maker, or a boss, or some manager, you’ll need to prove that in fact what you’re providing is valid and true to stand behind it.
Now, in the past, several years I have had direct communications; so now you’re into the cyber spying side, you’re using your sock puppet, you’ve established yourself, and you want to start having direct conversations with your target. In this case I use the tool called Mojahedeen Secrets v.2, which is an encryption tool that they created based on a lot of US or RSA-type encryption keys. They actually posted it, and I believe it’s still out there at gimfmail.blogspot.com (see left-hand image).
There is a public key that you can plug into this tool, share with them your public key, and start having conversations with them if they choose to respond back to you. So, here are some of the things that they say. Here’s Asrar al-Mujahideen v.2, or Mojahedeen Secrets, sometimes it’s hard to find nowadays; if anybody wants the tool, just send me an email, and I’ll send it to you if you’d like it. It’s fairly easy to use, it’s like PGP on steroids; it’s a really good tool.
But you can have these conversations with them, and again, you need to be careful with it, but you need to represent one of your sock puppets and explain to them what you’re after when you send it. There’s their public key that’s been out there. It’s changed a few times, but it’s available for you to use and copy and load it right up into your tool. It was in the Inspire magazines, although I was warned at one point not to email any of these accounts. There’re some 3-letter agencies in the United States you may have heard of that said: “Don’t email to these accounts, it’s probably a bad thing to do.” Most likely that’s because they’re watching these accounts. Regardless, you can go in and start this conversation with them.
So, this is the Mojahedeen Secrets tool here (see right-hand image). I imported their key, shared my public key with them, and we started having conversations through my Hushmail account, and that was actually the email address at the time; it was about 2.5-3 years old, the email is no longer valid. But we started having conversations. These conversations is where they started vetting me to find out who I was. So, they started asking some of those questions that I talked about earlier on the cultural, linguistic, historical, religious backgrounds to validate that I was who I was.
This took about 2 or 3 months to go through that vetting to prove that I was, in their mind, one of them. As I went further in these conversations, they handed me off to another person; I made it to the next level. And in this next level of conversations we started talking more, and what they were really after is they wanted me to provide funding to them, funding for the folks in Palestine to help out their play.
This conversation continued on back and forth; this first started all in English, then it was Arabic and English, and then the third person was all Arabic. And as we had these conversations, we kept swapping new public keys back and forth to have these conversations. And again – patience, it takes time.
So, after about 120-150 days they offered me up the fourth level that said: “Ok, now it’s time to start paying us money, and we’re going to send you information on how to transmit the money.” Well, I certainly didn’t deliver the money, or else I would be in Guantanamo right now. What I did do is I turned this over to authorities; I gave them all my information; I gave my sock puppets, I gave my public key information, and gave that to them so they had all this information, so they could take it over from there.
But it shows that if you really want to do this, if you’re patient, if you know your target as you know yourself, that you can really get into these areas and take that physical tradecraft and penetrate into their environments to a point where you actually are fairly trusted. The next point is then to commit the dollars, or the money, to them, which, typically in the Unites States, when you give information over to law enforcement, nothing comes back; it’s just a one way street.
Another gentleman here; this is an Iranian person from Ashiyane Digital Security Team, Behrouz Kamalian (see right-hand image). Behrouz is known for many different things, primarily back in the Green movement of June 2009. He took a bunch of pictures of protesters on the street, posted them up on Facebook, infiltrated Facebook, and all those people disappeared, so the European Union is now looking at this gentleman here for these violations.
Regardless, he was one of the targets I was after to find out information about Behrooz. And he’s got different Ashiyane forum sites, so I was able to get in and get all this information about them: their names, their handles, their ages, their titles, by becoming a sock puppet in their forums. Information intelligence can be used later on if I know who they are; I need to find who these people are. In addition, I have his phone number, his address, his fax number. If you want to go visit him, call him up, give him a jingle if you’d like. But this is the information that you can gather on your targets to give you an idea.
Now, from an analysis and assessment perspective – again, this is looking at the quality of information and validating your data, not so much the source – but there’re different ways out there to look at it, whether it’s above standards or if it’s below standards, the type of information you can use. And there’re several things that you need to look at with the intelligence you provide: timeliness around it, the accuracy, the usability, relevancy of your information based on the targeting that you’re giving or that you’re after. This particular chart here will give you some guidance on how to validate that information and go forward with it (see image to the left).
So, in summary on this: if you really want to be a cyber spy, whether it’s to your kids or to an adversary out there, there’s a series of things you need to do, from creating your sock puppets, maintaining anonymity, knowing how to use these open source tools, knowing the cultural, historical, linguistic, religious backgrounds of your targets and who they are, so you can apply that craft to them before you actually go to source validation, direct communications out there with these folks, and gathering this information.
There’re a lot of great tools out there that you can use on this. Hackers want to take down the sites; people like me want to get in and become resident on these sites. And I’ve been in sites before that have been hacked; I’ve actually been live in those sites before they’d actually been taken down with DDoS tools from The Jester. So, every once in a while I send him a direct message: “Could you at least give me a heads up?”
With that said, I thank you very much for the opportunity to speak to you, and to kick off this conference here in Budapest.












































The term “open source intelligence” (OSINT), not to be confused with “open soource information”(OSIFF) is obviously not understood by the speakers or editors of this web site. Please get your act together and stop misrepresenting cyber-subterfuge as open source intelligence. What you are talking is relevant and important in your domain, but it is neither open or intelligence (decision-support).
Dear Robert,
This article is a transcript of Jeff Bardin’s speech “So You Want to Be a Cyber Spook – Open Source Intelligence” at Hacktivity 2012 conference. That’s why it has this title.
It is well understood and used in context of the discussion, taught at the Master’s level, commercial level and used in live operations. Sometimes it is best to fully read and understand the content before shooting from the hip, especially when you are seen as an expert in the field…