 Mikko Hypponen talks on links between online crime, Windows trojans and funding the insurgents, explains the roots of some terrorist online publications and extremist malware.
Mikko Hypponen talks on links between online crime, Windows trojans and funding the insurgents, explains the roots of some terrorist online publications and extremist malware.
So my latest research has been into the Internet use as done by extremist and terrorist organizations. And when we start to think about extremist and terrorist organizations in the online area, people start to think about defacements or kids hanging around on the Net and spreading scary messages. I wasn’t really interested in that, I was interested in how real extremists group work, and what kind of things they do online.
Hi-tech terrorists… Many people believe terrorists are stupid Talibans riding camels in the middle of the mountains, who wouldn’t understand how to use a computer even if it hit them in the head. And sure there are people like that as well, but the truth is there are extremists online right now who perfectly well know how to use a computer just like you and I do, and who know their stuff around it.
Big part of these groups use the Internet like anyone else. They use it for communication, they use it to spread their message, they use it for recruitment. They do this on their own forums, on their own websites, on their own chat systems. Big part of this is perfectly available in the Web, you can find these by just doing a Google search and getting online. All of my research here is based on open source.
 One thing that showed to the world that extremists groups use technology in their attacks, in the actual attacks, was with the Mumbai attacks in 2008, which was an attack done by a Pakistani extremist group, in which 160 people died.
One thing that showed to the world that extremists groups use technology in their attacks, in the actual attacks, was with the Mumbai attacks in 2008, which was an attack done by a Pakistani extremist group, in which 160 people died.
These guys planned ahead using Google maps, they planned ahead using simulation systems, they were using satellite phones and VoIP1 systems to communicate during their attack. And I think it’s a good example that these guys are capable of using technology.
 Even a better example of the online work done by groups like these are the lifestyle magazines published by groups like al-Qaeda in the Arabian Peninsula, and their magazine is called ‘Inspire’ (see image).
Even a better example of the online work done by groups like these are the lifestyle magazines published by groups like al-Qaeda in the Arabian Peninsula, and their magazine is called ‘Inspire’ (see image).
These guys have put out 7 versions of this magazine in English language, some of them also translated into Russian. But the key part here is that these magazines are not in Arabic. They are really targeting Western audiences. And this is the kind of magazine which is not really talking to their existing members, it’s talking to the people who are on the verge of getting converted, who are interested in these ideologies, so they get converted further, to further this cause of theirs.
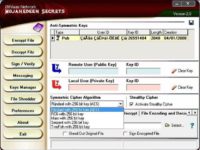 These magazines are impressive when you browse through them. They are PDF files, maybe 100-150 pages, nice big pictures, very well built, poems, stories, songs. And then right after them – bomb building recipes: how to build a bomb in your basement; and right after that, examples on how to use a public key encryption system developed and provided by extremists themselves. This is ‘Asrar al-Mujahideen’, an encryption system running on Windows, which uses 4 public key encryption systems, is capable of encrypting emails or files and so forth (see image). We’ve seen a couple of different versions of this software.
These magazines are impressive when you browse through them. They are PDF files, maybe 100-150 pages, nice big pictures, very well built, poems, stories, songs. And then right after them – bomb building recipes: how to build a bomb in your basement; and right after that, examples on how to use a public key encryption system developed and provided by extremists themselves. This is ‘Asrar al-Mujahideen’, an encryption system running on Windows, which uses 4 public key encryption systems, is capable of encrypting emails or files and so forth (see image). We’ve seen a couple of different versions of this software.
And there is quite a bit of paranoia in the extremist underground itself around the tool, like whether it can really be trusted, and which versions of this tool are real and which ones are trojanized by various intelligence agencies. We looked at some of these but we couldn’t find an obviously trojanized version out of the ones we had access to.
They also publish audio books, they publish videos and so on. In addition to this English language lifestyle magazines, there are also more technical magazines. This is ‘Technical Mujahideen’, published in Arabic, which goes into more details about technical aspects of hiding information on computers in case you get raided or somebody wants to find incriminating evidence on your computer. There’s been two issues of ‘Technical Mujahideen’ magazine, also published as a PDF file on the extremists forums.
 And here is an example of explaining to the readers on how to use ADS2, the Windows Alternate Data Streams, on how to hide evidence on a computer by hiding files on directories or existing files (see image). There are also resources where they discuss on how to use different rootkits to hide files on a computer.
And here is an example of explaining to the readers on how to use ADS2, the Windows Alternate Data Streams, on how to hide evidence on a computer by hiding files on directories or existing files (see image). There are also resources where they discuss on how to use different rootkits to hide files on a computer.
Another example of the kind of magazines these guys put out is ‘Al-Shamikha’, which is a lifestyle magazine in Arabic for the female audience. It’s very obvious when you look at the magazine that it has lots of pink colors and flowers, and the whole look and feel is totally different, and the articles typically gather around on how to be a good wife to a Jihadist or so on, or glorify female suicide bombers for example.
One interesting detail I found while doing my research was that 66% of Chechen suicide bombers are female, typically masked to be pregnant so they can carry more explosives while doing their task.
 Big part of their communication happens on forums, and these are almost always forums operated with the vBulletin software which is a very popular PHP script you can upload to an existing site, and you end up with a forum looking like this (see image). And the forum typically has areas for different languages. Many of the most popular forums have English areas in addition to Arabic, or maybe Russian or other languages represented.
Big part of their communication happens on forums, and these are almost always forums operated with the vBulletin software which is a very popular PHP script you can upload to an existing site, and you end up with a forum looking like this (see image). And the forum typically has areas for different languages. Many of the most popular forums have English areas in addition to Arabic, or maybe Russian or other languages represented.
Then there’s quite a bit of different blogs, many of them operating for example under Google’s Blogspot service, which means they are basically hosted, at least partially hosted, right here in the United States.
It’s quite clear that these groups also have, over the years, recruited members who are skilled in producing nice-looking content, the ‘Inspire’ magazine is a good example of that, although it’s unlikely we’ll be seeing new editions of the magazine right now because the two main authors of the ‘Inspire’ magazine were killed in a drone strike in September 2011. And they were both American citizens, which explains the language skills; they were native speakers, and that’s why they were able to produce an English language al-Qaeda magazine.
 But the branding goes beyond the magazines. For example, this is the logo for Iraqi resistance (see image) with a cartoon look and feel. In fact, cartoons are seen further, there is a whole cartoon magazine published by Iraqi resistance, again furthering their cause and making the message accessible to a larger audience.
But the branding goes beyond the magazines. For example, this is the logo for Iraqi resistance (see image) with a cartoon look and feel. In fact, cartoons are seen further, there is a whole cartoon magazine published by Iraqi resistance, again furthering their cause and making the message accessible to a larger audience.
And then we have the ‘Baghdad sniper’. ‘Baghdad sniper’, also known as ‘Juba’, is either one individual or actually more likely a set of individuals who are portrayed for propaganda reasons to be this superhuman sniper who snipes Western – mostly American – troops in Baghdad. ‘Baghdad sniper’ releases are produced and released through Baghdadsniper.net, a website hosted in Turkey. And on that site they release posters and kill statistics, like how many Western soldiers have been sniped, how many of them were officers, how many have been wounded. Posters like the one you see right here, which is an X-ray image of a wounded soldier with a bullet in the head.
They are trying to make the enemies scared with a very traditional propaganda message, and the message is that you are always being targeted; no matter where you are, you always have a cross-hair on your head – and that’s actually a very scary message. It’s very hard to get that out of your head once you realize that it could actually be true.
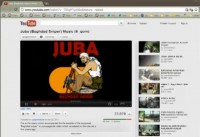 So for example on one of the posters, the message from the ‘Baghdad sniper’ to the Allied Forces is – “Hide or not, you are a target. Believe there is always someone aiming at you”. There are similar scary things are back at sniper’s website. That’s the YouTube channel (see image). In fact, YouTube right now contains several videos containing real kills, recorded and posted online by ‘Baghdad sniper’. Those are videos with music playing in the background, and over and over again, a cross-hair doing the headshot on a U.S. soldier who will fall down, and you know that this is not a movie, it’s a real person getting killed or maimed for life over and over and over again.
So for example on one of the posters, the message from the ‘Baghdad sniper’ to the Allied Forces is – “Hide or not, you are a target. Believe there is always someone aiming at you”. There are similar scary things are back at sniper’s website. That’s the YouTube channel (see image). In fact, YouTube right now contains several videos containing real kills, recorded and posted online by ‘Baghdad sniper’. Those are videos with music playing in the background, and over and over again, a cross-hair doing the headshot on a U.S. soldier who will fall down, and you know that this is not a movie, it’s a real person getting killed or maimed for life over and over and over again.
The interesting thing about the hosting these guys use to get their information on the Net is that quite a bit of these are actually here in the United States. There’s several sites which have been historically hosted in places like Malaysia or Indonesia, or Ukraine, or in Dubai, or in Turkey, but the truth is there is quite a bit of hosting on U.S. servers. We mentioned YouTube and Blogspot as examples, but Archive.org is another site which most people know as the Internet archive for mirroring existing websites, but it can also be used as a hosting service, and these guys use it extensively.
But what about examples of something going beyond just online communication and online propaganda, and online recruitment? Well, there are examples that go beyond that. For example, during my research I found two very active members of extremist jihadist forums, who both post in Arabic, and they continually post about tools like Metasploit, BackTrack 5 and MultiGo, explaining to other how to use these tools to do exploits, how to gain access to computers, how to do forensics examination of an infected system, how to build botnets.
They have even, apparently themselves, created their own Arabiс words for Metasploit and for BackTrack.
 And then we have cases of real extremist malware. I tried finding examples of these, I could only find one, and even that’s not very recent, this is from 2007, case from UK where Tariq al-Daour (on the photo) with two of his partners in crime were using a Russian-made, Russian tailor-made trojan to target Internet users around the world. They were not targeting anyone in particular because their target was to gain access to computers and use a keylogger to collect credit card numbers from those infected computers when people where doing online shopping, after they had been infected.
And then we have cases of real extremist malware. I tried finding examples of these, I could only find one, and even that’s not very recent, this is from 2007, case from UK where Tariq al-Daour (on the photo) with two of his partners in crime were using a Russian-made, Russian tailor-made trojan to target Internet users around the world. They were not targeting anyone in particular because their target was to gain access to computers and use a keylogger to collect credit card numbers from those infected computers when people where doing online shopping, after they had been infected.
And this is a very successful scenario; we see this over and over again from traditional profit-motivated criminal gangs. But these guys were not motivated to make money for themselves. What they did with the stolen credit card numbers is that they went to online poker games such as absolutepoker.com, and they used the stolen credit cards to play poker in the table where all the other players in the table were their own accounts. So when they were playing with the stolen credit cards, they were losing money on purpose, and this was done in order to launder the money.
Now, when somebody comes wondering why you have all this money, you can explain it that – ‘Well, you know, I got lucky, I won it in the game of online poker, here’s the receipts, here’s the logs’ – everything looks real.
And this was so successful they managed to launder 3.5 million U.S. dollars, and that money was used to buy knives, hiking boots, sleeping bags, tents, plane tickets, over a hundred satellite phones, hundreds of prepaid phones, and all these were shipped to Iraq to the insurgents.
So what we have here is a link between online crime and Windows trojans and funding the insurgents. But even this is still far away from what we would categorize as cyber terrorism.
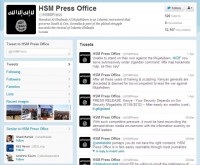 And there are many more examples. ‘Al-Shabaab’, the extremist group from Somalia, they run their own Twitter account (see image), they publish their own music videos in YouTube (rap, hip hop music), explaining their cause.
And there are many more examples. ‘Al-Shabaab’, the extremist group from Somalia, they run their own Twitter account (see image), they publish their own music videos in YouTube (rap, hip hop music), explaining their cause.
And I guess the takeaway is that we shouldn’t underestimate these guys. Not all the extremists are stupid villagers riding a camel on the mountains. We shouldn’t assume they all are because they all aren’t. They know how to use a computer just like you and I do. They know how to photoshop stuff, they know how to make movies, they know how to host servers, they know how to run PGP3, they even know how to make their own public key crypto systems. They run Metasploit, they run BackTrack.
And while we haven’t seen real cyber terrorism yet, and while the situation isn’t really too bad at the moment, I don’t think the situation is going to get any better.
1 – VoIP (Voice over IP) commonly refers to the communication protocols, technologies, methodologies, and transmission techniques involved in the delivery of voice communications and multimedia sessions over Internet Protocol (IP) networks, such as the Internet.
2 – ADS (Alternate data streams) allow more than one data stream to be associated with a filename, using the filename format “filename:streamname” (e.g., “text.txt:extrastream”). Cyber criminals are known to use ADS to hide malware code on computers.
3 – PGP (Pretty Good Privacy) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, e-mails, files, directories and whole disk partitions to increase the security of e-mail communications.




























