
Jeff Bardin from Treadstone 71 provides a detailed overview of the Jihadist activities on the Internet, including their software tools, online resources, etc.
Good day and welcome to this cyber jihadist use of the Internet from 2008 to 2011 overview by Treadstone 71. This deck, over 60 slides, will cover from a high level the jihadist use of the Internet through those years, actually starting well before 2008, but first delivered by myself in different seminars, discussions, talks from RSA and SecureWorld Expo.
These discussions are compiled here into one deck. I removed some information I thought was not important for this talk, but hopefully it will provide you some education on the level and types of use of Islamic extremists and their use of the Internet over those years.
This slide (see right-hand image) demonstrates their use of audio and video in multiple different languages. They’ll use German, Spanish, Turkish, English, as well as Arabic. You will also see videos out there that are meant to shock; others are meant to educate and teach and train, others are meant to brainwash and continue the standard view of the Salafi view of Islam.

This particular slide (on the left) is a series of animated gifs that focus on some more training, like the Mujahideen Poisons Handbook, which is a little bit like an instruction; the Mujahideen Secrets v.2, the encryption tool (there was version 1, we’ll cover that a bit later), as well as some other animated gifs here on 9/11 and ambushes throughout the Iraq war era.

The agenda for today is: we’re going to cover online training and look at jihadist media out there. We’ll look at the Salafi with respect to radicalization; also take a look at forensics and communicating jihad. And then we’ll close up for the day and wrap it up. This is over 60 slides, so it is lengthy, even though this subject could go on for days and weeks, if we had the time. Hopefully you’ll enjoy the presentation.

There was a great deal of training early on (see left-hand image). There was Al-Battar magazine, and they had several issues focusing on training, a training camp. The 6th issue, which you can see the cover here on the right, discussed cell organization and different command structures for their cells.
They also had a magazine that came out with two editions called The Technical Mujahid. These were all in Arabic and talked about more IT technical type of issues, as well as some violent type activities.
Then there was the Al-Qaeda University for Jihad Sciences that was electronic. It talked about e-Jihad, and we’ll talk about some of that a little bit later. There are training manuals out there and videos for explosives of all types, IED’s, surface-to-air missiles, flying planes – there were just 18 videos on flying 747’s back in the Al-Battar video days.
There was one issue here, issue #10 of Al-Battar that was a training manual focusing on special coverage of kidnapping. It had reasons for detaining one or more individuals by an enemy and forcing the government or the enemy to succumb to some demands, put the government in difficult situation that will create a political embarrassment between the government and the countries of the detainees; obtaining important information from the detainees, obtaining ransoms, which we’ve seen a lot of late. Such was the case with those in the Philippines, Chechnya and Algeria in the early days. They say that brothers from Mohammed’s army in Cashmere received a 2 million dollar ransom that provided good financial support to the organization, able to fund other terrorist activities.
I’ll bring a specific case to light; this happened at the beginning of the cases in Chechnya and Algeria with the hijacking of a French plane, if you remember that. And the kidnapping operations were performed by the brothers in Chechnya and the Philippines.
They also have requirements needed in forming a kidnapping group: a capability to endure psychological pressure in difficult circumstances. In case of public kidnapping the team will be under a lot of pressure, they say. And the detention must not be prolonged: “in case of stalling, hostages must be gradually executed so that the enemy knows we are serious.”
“When releasing hostages such as women and children, be careful as they may transfer information that might be helpful to the enemy. You must verify that the food transported to the hostages and kidnappers is safe – this is done by making the delivery person and the hostages taste the food before you. It is preferred that an elderly person or child brings in the food, as food delivery could be done by a covert Special Forces person.”
“Beware of the negotiator: stalling by the enemy indicates your intention to storm the location. Beware of sudden attacks, as they may be trying to create a diversion, which could allow them to cease control the situation. Combat teams will use two attacks, the secondary one just to attract attention, and the main attack elsewhere. In case your demands have been met, releasing the hostages should be made only in a place that is safe to the hostage takers. Watch out for the ventilation, or rather openings, as they could be used to plant surveillance devices, through which the number of kidnappers could be counted and gases could be used.”
“Do not be emotionally affected by the distress of your captives. Abide by Muslim laws as your actions may become a dower call to join Islam. Avoid looking at women.” These are just some of the training items in issue #10 of Al-Battar.

Other training manuals (see right-hand image) covered many different lessons out there – from counterfeit currency and forged documents to weapons, measures related to buying and transporting them, special tactical operations, espionage, information gathering using open methods, open source in this case, or covert methods, and the secret writing with ciphers and codes, as well as assassination using poisons and cold steel. We’ll take a look at some of that with respect to cold steel in the next slide.
With respect to assassinations (see left-hand image) using cold steel they get very descriptive on where to actually place the blade: anywhere on the ribcage, both or one eye, the pelvis, the back of the head, the end of the spinal cord – directly above the person’s buttocks; made to disable and kill as much as possible, as quickly as possible.
In addition, they talk about the blow of a club between the eyes, veins and arteries, genitals and so on. They get into specifics of grabbing testicles, grabbing the ribcage, and how to actually perform the execution in a battle, in a fight. They also talk about castor beans and ricin in detail in multiple different documents out there and training manuals. This is just one, and it gets very specific in how to go about performing these actions. So what you have online is a basis for academic side of training, and then you have to go to a training facility in different territories where they have these camps, and actually learn how to do it firsthand.
I mentioned in one of the slides earlier the Mujahideen Poisons Handbook. This is the index (see right-hand image), one of the indices in the beginning here, actually, a table of contents. And it talks about homemade poisons from ricin, alkaloids of potato, arsenic, sodium nitrate, thallium, and phosphorus to chlorine and different gases. The edition starts with introduction: this file is dedicated to help folks learn how to put together different poisons.
“May Allah reward him every time it is used in his path and may He help him in his difficulties, amen. To the mujahideen of Afghanistan who’ve lit the flame of jihad in the hearts of every sincere Muslim. Throughout the world you will conquer Constantinople and Rome.” This is from the Prophet Muhammad, peace be upon him.
They go on to talk about the book dealing with poisons (see left-hand image), and poisons are substances which cause harm to human body, of course. It is an esoteric knowledge, and must only be passed on to those who truly intend to use it in the name of Allah. They talk about lethal doses that often have a question mark beside them – that is because the quantities given are not established truly; they’re only estimates based on experiments with rabbits.
It is hoped that the brothers who work on this subject will research further, care out their own experiments, and refer to medical books to fill in what is missing. So they do realize that there’re holes here and it’s actually just a starting point. The gentleman who publishes this goes on to say: “I was learning from people whose first language was not English; some of the names of chemicals, properties are wrong. Be very careful when preparing poisons: it is much more dangerous than preparing explosives. I know several mujahids whose bodies are finished due to poor protection. On the positive side, you can be confident that poisons have actually been tried and tested successfully, hehe.” So this is the mujahideen poisons; that’s been out for several years and it’s still available out there. And again, I’ll focus here on ricins, since it’s been in the news frequently lately in the United States.

Now, most people believe that Inspire magazine was the first jihadist magazine, but actually Jihad Recollections was (see right-hand image). Here in this edition we have “Obamaturk”, comparing Obama to Ataturk, the then leader of Turkey, the Ottoman Empire, who brought secular vews to Islam, which is directly an anathema to the Islamic extremists view, the Salafi view of Islam.

In addition we have some discussions here on Omar Hammami and his conversion to Islam and move to fight with the Shabab in Somalia. In addition we have Adam Gadahn, who had gone from Jewish to Christian values to Islam to extremist Islam coming out of Los Angeles, who is now married and reported to be living in Pakistan as one of the spokesmen (see left-hand image). Adam has been very adamant; many see him as quite a buffoon, but he still continues to communicate in English, as well as in Arabic, Salafi values. So the intent here is to demonstrate that many westerners have seen the light and have converted to Islam.
In addition, in this particular version as of May of 2009, we have a warrior trainer, the days of Abu Leith; we have the analysis of the architect of global jihad, which is from Abu Musab al-Suri who was released from jail in Syria during the recent activities over there.
Revisiting the global jihad media effort is discussed in this, talking about America being a bully among bullies, and different activities about technology with respect to: “Forget cell phones, the sixth sense is coming,” and 8 great reviews of iPhone 3.0. So they cover many different things in this from religion and biography, strategy and lessons, social issues, technology, and health, and the jihad recollections. There were four versions that made it before this magazine actually was retired.

Continuing onto this version of Jihad Recollections from May 2009: you see information here on the left from GIMF, the Global Islamic Media Front (see right-hand image), on a video: “Signs of Victory are Looming over Afghanistan.” At the bottom on the left you see a pointer that points to one of the online storage sites, at the time – FileFlyer. On the right you see more discussion on the war of atrocities from the same gentlemen, and a pointer down the bottom to FileFlyer again.
But the text here is from Abu Musab al-Suri, criticizing some of the issues with respect to current training and activities and success rates of the different schools out there, and really hitting home at this failure in education due to the lack of a program, and there’s a political failure, because there is absolutely no program.
In the Salafi view of Islam they offer no programs, no training from political viewpoint and no establishments from a political organization. So once they take over, it’s just pure chaos for the most part. They say that they’ll refer back to the Islamic law, but their interpretations are extremely severe, and people suffer at the hands of it.
You will also find that al-Suri is looking for more mobile training methods, such as in-house training. He also goes on to talk about online training and just-in-time type training using means that secret and subtle and creative while using effective methods to strike as much pain, loss and terror to the adversaries.

This is a screenshot from Teqany magazine (see right-hand image); it was in Arabic exclusively. It was a technical magazine focusing on teaching and training on how to use various tool sets available in the marketplace. First released in November 2006, there were only two editions of this particular magazine.

From the inside of Teqanymag you have methods on how to hide documents. On the top left you also had GPS utilization focusing on Iraq at the time. Use of wireless devices and video and media players out there was also part of their standard training set with respect to Teqanymag (see left-hand image).

Back in 2007 there was an effort to take down different sites that were criticizing the Muslim sites, or, in particular, the Salafi-type sites. Raising e-Jihad was this effort (right-hand image); as you can read from the right here, they’re trying to get people to sign up. One of the unique things about this was the video game atmosphere around what they were trying to do.
It says that the program provides a number of hours for an attack, in this case 24. They are going to update their databases. They have features, such as direct communication with the leadership and business networks, especially from the heavens. And their names will appear on this page per period, each period between a month and two weeks after this is done with the authorization of Allah.
They had an option to register a username in writing of who’s been invited to participate, and it led up to 24 points, one per hour for each brother brought in to join the attack. The strategy here is to find locations out there, to have them withdraw data that is actually abusing Muslims or is against their values. And the attack that they wanted to hit them with is doubling or tripling their bandwidth usage for denial-of-service. And they would really prefer to push them into bankruptcy and close the site if possible.
They indicate that the attack will be open for 24 hours and that members can collect the greatest number of points, with each point being equivalent to one hour of attack. This never really matriculated, but the effort started early on, and that is what we see on the next slide. There was a tool put out there in several versions of a DDoS-type tool.
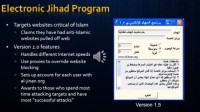
They followed on with a new Electronic Jihad program (see right-hand image) starting with version 1 to 1.5, eventually 2 and moving on to version 3. They made this much more simple to use. They made software downloads to simplify the denial-of-service attacks. It was designed by a Saudi national. They had chat rooms available to plan and coordinate attacks. And there was a forum that listed websites to be attacked and the potential impact they wanted to carry out.
So, unlike the first campaign of electronic Jihad where participants did not have prior knowledge of the websites that they were attacking until they activated the Electronic Jihad software, the main page of the then al-jinan.org site carried names of the websites to be targeted for the attacks. Also the e-Jihad software program 1.5, or the silver version, had been updated to v.2 and again to 3. The new version of the software was much easier to use. After a few seconds of activation it actually updates the targets automatically and is compatible with different connection speeds and capable of using different proxies to override different website blocking technologies.
The version also set up account name and passwords at al-jinan.org for every user. And they can register the number of hours the user spent attacking targets and every two weeks the names of those who scored the highest would actually be posted. At the time the highest score was claimed by user nicknamed George Bush, who spent 4211.5 hours, or 70 full days, trying to DoS anti-Islamic sites. Other users spent hundreds of hours running the program as well.
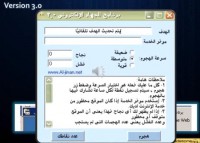
The installation process for the Electronic Jihad program is very simple, you just need to follow instructions and click through. In addition it shows you the interface for Electronic Jihad (see right-hand image), much the same as before, but this is a 3.0 version with more features.
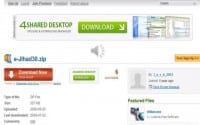
In addition, what they followed on with is where you at the time could download e-Jihad 3.0.zip, guaranteed by Kaspersky to be clean of any malware (see left-hand image). So, very simple to find at the time; probably, nowadays you’d find it at archive.org, the way back machine which continues to archive pretty much anything and everything of Jihadist value and makes it available for them.
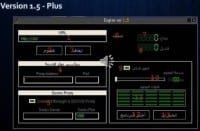
There was another tool made available at the time that was much the same with respect to DDoS, or denial-of-service type of attacks (see right-hand image). What they were really after here was conducting these different cyber attacks or hacking for money and organizational support, disruptive hacking for cyber Jihadist against different websites out there. And what they’re looking for is trying to acquire different low-level weapons for development and training here and distributing these hacking tools and information about them and educating people on how to use them, and then having statements as well about computer network attacking activities.
They would look for calls for action here, and formal education in IT. And they looked at cyber space experience as something that they were after here, and the extensive use of the Internet was what they sought. And again, the development use of cyber tools, including network and data security tools, were key areas that they were recruiting for in the online forums.

Some of their early methods that used network security tools out there – obfuscation, denial and deception – included the distribution of Asrar al-Mujahideen, or Mujahideen Secrets v.1 from GIMF, Global Islamic Media Front (see right-hand image). This had 256-bit symmetric encryption and 2048-bit asymmetric encryption used on thumb drives. There was some training, not too much, and they had it here as kind of packaged up on the image.
Regardless, they started communicating this on the forums, and they started spreading out into email, chat, instant messaging, blogs, forums and different groups out there, as we will see. They also were looking at steganography and different encryption uses, the use of anonymous accounts on various email sites. And they started realizing that all email was being targeted, therefore they stopped sending email and would use email for dead drops, placing draft messages, using shared email accounts and using them for a period of time before they stopped using them altogether.
This helped in their communication and coordination, and their command and control, and distributing different documents and videos. In addition, it also helped in their intelligence collection, or open source data collection leading to intelligence; recruitment, training, fundraising, offering jobs in IT, looking at ISPs that were actually sympathetic to their cause so that they could actually host their websites and operate their organizational online networks out there.

And they were also looking for insiders that had access to critical infrastructure. In the early days these were some of their initial activities (I guess I mentioned it): obfuscation, denial and deception.

The second version of Mujahideen Secrets had been advertised: as you can see here, when it blowed up, you can see the matrix in the background (right-hand image). In addition, you can see Cyrillic MYPppp. In addition, you have an upside down fish, or the symbolic of Christianity, and a dead fish in this case; multiple keys within it showing the use of various different encryption keys and the tool set, as well as new features in red down at the bottom (see left-hand image above), Jadid, or ‘New’ that was available in the tool set. In addition, you see an M16 with a key on the end of the circle – it’s part of their logo from the Global Islamic Media Front.
Mujahideen Secrets version 2 (see right-hand image) was a definite improvement over version 1. They added some new features in the tool set; speed was actually part of it as well – they came embedded with a public key, so they had it ready to go. In addition, they had greater help files, and you could search and look at the index of contents, table of contents of different help out there.
Symmetric cipher algorithms such as Rinjdael, Mars and Twofish were included as well as your standard file shredding and key management, all in a tool – basically an open “PGP on steroids” version that they developed themselves; could have potentially been developed by the Kavkaz-Center group out of Chechnya. It provides them a method of encryption that is still in use today, as advertised at the end of the Inspire magazines where they published their public key.
As part of the v.2 release of Mujahideen Secrets, they had the digital fingerprint of the actual software and the keys (see left-hand image). You could actually see the compression ratios in Mujahideen Secrets. But also they released this with the intent of encrypting video and potentially encrypting images and embedding them in steganography. So they had a combination of different things they were using at the time, encrypting different texts and media, embedding it in different images and steganography, and teaching people how to use different tool sets out there with respect to making videos and different images, where they could, in fact, embed their information and hide in plain sight.
Demonstrating further integration with some of their solutions out there: I mentioned earlier Teqany magazine as one of the early magazines. There’re only a couple of magazines out there, highly technical, all in Arabic. But in the Mujahideen Secrets training indices they actually pointed Teqany magazine as one of those that have been zipped up and encrypted as an example (see right-hand image). This was back in early 2007 and shows there their dedication to protecting information.

In a move towards mobile they actually came out with TRSC, one of their technical units came out with Asrar al-Juwal, or Mobile Secrets (see left-hand image). This was a Java tool set that was able to run on Blackberry. It had some bugs, it was still in beta format, and they never seemed to get the second release in the marketplace. I am not sure if it was used very much; it pops up from time to time. As you see here, this is version 0.4. But it was a move that area, and it did have a small footprint, and you could actually use it, but it was a little buggy.
Jihadists were also concerned about information security (see right-hand image). They used many different types of anti-viruses. They were using Kaspersky here, and they actually cracked and provided the key, made the key available, as well as pointers to where to download and how to install Kaspersky.
During the Iraq war the ‘Baghdad sniper’ was glorified (see left-hand image). This person, if, or more than one person, actually – it was attributed to one, had videos taken of his actual kills and shots, mostly in urban areas. You have some cutouts here on this particular screen of US soldiers prior to their being shot. The distance seemed to be pretty decent. Distance here can be estimated, they would blow it to being several hundred yards. In addition, you can see the distance because there’re cars going back and forth in the urban areas within the video shots. Regardless, Baghdad sniper had many videos; he had his own site baghdadsniper.net. They were training that one with online trainings, whether it was written, as well as video, and then combined with the actual exploits of the Baghdad sniper.

A little bit more on the Baghdad sniper (see right-hand image); the weapon of choice was the Dragunov, a Russian-made weapon. In addition, his kills were 24, 3 officers targeted, and 16 different wounded out there. And you could actually get the high resolution video of his actual exploits, all these different sites at the time. They usually would post them as high, medium and low resolution; low targeting for the most part mobile devices. Many of these sites carried them for years; they carried them without dropping them until finally there was pressure put against them. Nowadays they still are used, but they are dropped fairly quickly, except for archive.org, the actual way back machine.

Other parts of their training regiment also include the use of US military manuals, one such here: Cyber Operations and Cyber Terrorism, was found in many links off their sites (see left-hand image). In addition, many US army field manuals were made available and are still available through archive.org, and they pop up periodically, depending upon need. So overall, their education was pretty sound with respect to the academic side of the house, and they followed through with multiple media solutions: web 2.0, email, chat, instant messaging, blogs, forums, groups, use of audio and video, animated gifs to the strength. They had a very strong Jihadist media organization and a propaganda machine that was very effective.
The main Al-Qaeda site at the time was Ikhlas (see right-hand image). Ikhlas is no longer around, but it was the main site for communicating Zawahiri and bin Laden information. It was a vBulletin site, and you could actually enroll in the site, but you could have junior-type status until you actually proved your worth and your alignment to the Salafi views of Islam. It was just their enrollment forum, here you put a username and email address, and it was fairly easy to get tied to it. This site was eventually taken over by some western organizations and republished, discovered within 24 hours and taken down again soon after. I think it was 2009-2010 when this occurred. But Ikhlas today does not exist in this form; many other forums are out there that are still in use.
This is your standard vBulletin enrollment form for one of the forum sites (see left-hand image). You put your username in, then your email address, email address second time, and then your password twice; then some more information about yourself: your location, male/female, your time zone. Then it would actually send the enrollment link to the email address and you could enroll.
Nowadays you have to be invited to many sites; if you have not made it in already, it’s difficult to get in. But this was standard enrollment at the time. Some would actually send an email and then start asking you questions about your views of extremist Islam, or Salafi view of Islam. If you couldn’t answer those questions correctly, then you wouldn’t make it in. So it was a little bit of a test. Nowadays it’s much more strict; they’ve gotten fearful of allowing people in. There are other ways to get into the sites, but for the most part it’s much tighter nowadays.
As I mentioned vBulletin software earlier, in the early days it was actually owned by a UK company, just about 96 clicks into the West of London, but it was actually hosted at theplanet.com in Houston, Texas. You notice (see right-hand image), on the site they have different languages available: German, Chinese and Hungarian. They used to have Arabic here as well, they do fully support it: if you go into the forums, you can find out information about the actual language support for it. They kind of pulled it after a lot of attention. Now this company and software is actually owned by Internet brands out El Segundo, just north of Los Angeles. About 180 dollars for one license; if you buy a quantity, you get it much cheaper. It’s a fairly easy to use and set up forum-type solution that jihadis prefer.

These three gentlemen (see left-hand image) were involved in a lot of posting of Jihadist material coming out of Iraq. Younis Tsouli, aka Irhabi007, aka Terrorist007. You see this was a picture after he was arrested. They were involved in a lot of criminal activities that helped support and fund their actions. For the most part they would distribute a lot of different setups and were the precursor to all these different forums out there.
They were eventually caught, and now they are in prison. They provided some great support to Zarqawi and others in Iraq, as the videos would come to them and they would actually compress them, dress them up and post them online on these different sites.

The celebration of their physical exploits were all over their forum sites, videos, pictures, congratulatory and slaps on the back, and different animations that would take our information and post it on their site, demonstrating how asymmetrically, from a guerilla perspective, a couple of Jihadists would sacrifice themselves.

Much of their training comes from online learning and education on how to make bombs. Different types of these were actually using different Mitsubishi phones to trigger the explosives from backpacks: what you saw there was a video of the Madrid bombings, very well planned and how they actually herded people towards the stairwell and had the bombs go off in sequence, knowing for well that they would be herding and moving that way. A very good example of how cyber terrorist activities in learning and training, command and control and communications and different technologies can be used and learned about online and taken to physical execution.

The next slide (see right-hand image) has some very graphic photos, so I’ll warn you right now: if you do not have a strong stomach, please do not proceed to the next slide. These are images taken directly from the Madrid bombing in the aftermath as they lined up the bodies.
What’s interesting here is that these would be taken by the law enforcement, not by the public. How would they make their way out to the public, and in fact into the hands of Jihadist folks and, in particular, Al Qaeda? Now, the group that performed this bombing was not part of Al Qaeda at the time – it was actually trying to gain entry. As a result of the bombing they were admitted into the fold as Al Qaeda members. Regardless, they’re very gruesome images. You’ll notice that there are some black boxes, where they’ve redacted some of the parts – this is tradition in Islam to blackout and to redact the eyes, as well as genitalia, or anything of a sexual nature.

One of the key features for Salafis is, of course, the use of the Internet. But using the Internet requires some skill and direction. Per this, the Salafis have written and posted documentation on how to start a Jihadist media organization (see left-hand image). The image here is a snippet of the translated version of that document. It covers many aspects of media creation and can service a role model for counter-intelligence replication, as well as intelligence infiltration. The methods are not earth-shattering, but nonetheless are written to define a roadmap for almost anyone wishing to create a Jihadist media organization in several easy steps to follow.

Now, the Internet is used for many different things, in this case communication, of course. But it also has a flow with radicalization process (see right-hand image). There’s complements of the NYPD; they did quite a study out there. It’s drawn some heat in some circles, but it goes through different phases, as you see here: pre-radicalization, self-identification, indoctrination and jihadization.
Each of these phases is unique and has specific signatures allying to it. All individuals who begin this process do not necessarily pass through all these stages, of course. Many stop or abandon this process at different points. They just lose their desire to go further, and they don’t believe it. Some pass through the entire process and are quite likely to be involved in the planning or implementation of a terrorist act.
The pre-radicalization is the point of origin for individuals before they begin this progression. They can do it online. It is their life situation before they were exposed to an adopted Jihadist Salafi Islam, it’s their own ideology. The majority of individuals involved in these plots begin as unremarkable, and they had ordinary jobs, they had lived ordinary lives and had little if any criminal history.
When it comes to self-identification, this phase is where individuals are influenced by both internal and external factors. They explore Salafi Islam and gravitate away from their old identity and begin to associate themselves with likeminded individuals and adopt this ideology as their own.
Some of the triggers are the economic situation, losing a job, or block from mobility, or not working at all; social alienation, discrimination, racism, whether it’s real or perceived, they have that idea of being victimized; political situation, or international conflicts involving Muslims, and they are being treated poorly, such as possible Abu Ghraib, or they line themselves based on political situations in certain countries – we’ll see a video here from Lars Vilks shortly. Or there may be deaths in the family, someone close at the hands of westerners. Regardless, these can all be triggers, as are caricatures and are images of the Prophet Mohammed, peace be upon him.
The indoctrination phase is a phase in which an individual progressively intensifies his or her beliefs. They wholly adopt Jihadi Salafi ideology and conclude without question that conditions and circumstances exist where action is required to support and further the cause. User is driven by the spiritual sanctioner, someone like Anwar al-Awlaki, someone ordained, if you will, and seen as someone very well educated in the Quran. In Awlaki’s case, he was an imam.
While the initial self-identification process may be an individual act, as noted above here, association with likeminded people is an important factor as the process deepens. By the indoctrination phase this self-selecting group becomes increasingly important as radical views are encouraged and reinforced.
It also starts to get down to much smaller group and relates to the Dunbar’s number. Take a look at Dunbar’s number on Wikipedia, you’ll understand the trust factors around the human mind, and as we get to greater trust, we have fewer groups of people in that circle.
Then there’s the jihadization phase, in which the members of the cluster accept their individual duty to participate in Jihad and self-designate themselves as holy warriors, or Mujahideen. Ultimately, the group will begin operational planning activities for the Jihad or a terrorist attack, and these acts will include planning, preparation and execution. While the other phases of radicalization may take place gradually over 2 or 3 years, possibly, the jihadization component can be very rapid, taking only a few months or even weeks to run its course.

Pre-radicalization, from a cyber perspective, used to take place in the forums (see left-hand image), where they’re well-organized and publish Jihadist-related media and publications, as well as Mujahideen press releases, communicate statements out there, many of which are just pure propaganda and false in nature.
They also organize their forums into science and applications, different Quranic verse, historical and biographical information on people and places, the basic tenants of the faith and methodologies and principles and teachings are there, as well as different ways to behave yourself, and purification and manners, since Islam is part of your everyday life that absorbs your life.
In addition there will be different requests and information and conversations amongst different participants on the sites, poetry and media postings, different discussions, as well as, of course, IT and communication technologies some of which we’ve shown here that is available for download.
There was a video spread online to demonstrate that the West and Israelis are nameless, faceless, cold, steel, remote controlled from a distance who kill indiscriminately, targeting women and children. The idea there is to fully indoctrinate and self-identify with this and align with the victimization mentality. This video was done a couple of years back and targeting Obama after he was elected, showing the Statue of Liberty burned down and torn down from the top, as well as the skyline in New York City. There was a message to an “old enemy”.

With much of the education on pre-radicalization left to the forums, budding Jihadists begin to align with religious figures that are vetted to communicate the words of the Quran. One such imam was Anwar al-Awlaki (see right-hand image).
Alignment to a religiously vetted figure provides validation that their cause is righteous and just. Awlaki recorded many sermons that are available in mp3 format for download on many sites that seem to be normal Islamic sites. But they are not normal, only posting as such to deceive and deny. Very deep within these sites are messages that support the Salafi viewpoint and make available sermons of hate for the solidifying the position of victimization, and all-out warfare by the West on Islam.
Awlaki also wrote 44 ways to support Jihad that ensures education starts at a young age to indoctrinate and brainwash children in the ways of the cyber Mujahed and those who someday may take their cyber views to actual physical action. Having achieved rock star status, Awlaki could not show up in person at his lectures due to threats to his life, but would instead deliver them via phone to packed crowds in theatres or other gathering places, such as colleges and university lecture halls.
There are many interpretations to Jihad available online. In particular, the Salafi created their own e-books that convert those looking to become radicalized or learn about Jihad and the views from the Salafi standpoint. They can download these e-books and go through them.
There is one such section in a chapter in this particular e-book on Jihad, and it regards Muslim prisoners of war. In the States if a Muslim POW is able to escape, then it’s mandatory for him to do so. And if he can escape and capture with him any enemies, take any of their property or kill them, he should do so. If the POW is released with the conditions that he agrees to, then he must fulfill those conditions in order not to end up harming other Muslim POWs or causing the enemy to think that Muslims are untrustworthy.
Interesting statement there: the Muslim POW is not allowed to marry a Christian or a Jew in the land of disbelief, because the children in this case might follow their mother’s religion. And he is not allowed to marry a Muslim because they could force their children to apostate or they could be enslaved. The Muslim POW should be patient until they return to Muslim lands.
Regarding enemy POWs, a stronger opinion is that the imam should do what is most beneficial for the Muslims: to execute them to free them without anything in return, or to free them in return for freeing Muslim POWs, to charge for their freedom or to enslave them. The ruling on women and children POWs is that they become slaves by default. If a Muslim kills a POW, the Amir has the right to punish him; the punishment less than the least punishment of a major sin, usually is less than 10 lashes, and so on. So you get your view of Jihad and different rulings within these different e-books out there. These, again, help educate and help in the radicalization process, all available online on the Internet.

Now getting to more of an academic view of explosives: there’s all kinds of documentation on how to actually create explosives using various chemicals (see left-hand image). All these books that you see here listed have been painstakingly scanned or in PDF format made fully available on different sites as linked from the Jihadist vBulletin forums.
In addition, they have instructions on where and how to place bombs in public places, giving instructions on how to hide the packages, how to bring them in, how to ensure that you are fully hidden with respect to your clothing, and you blend into the marketplace. It is a step-by-step methodology on how to place these bombs in public places, and it is definitely a highly trafficked article. In addition, you combine this with the academic side of explosives. Eventually you’re going to have to go to test these out from a physical perspective and ensure that you can actually build them adequately without harming yourself.
One such budding Jihadist was asking where he could actually find the Mujahideen Handbook, or any video demonstrating how to create the suicide belt (see right-hand image). Well, response came back very quickly from another junior member, who said: “This is where you can find it, my brother. You can find it at this location, archive.org,” which is still there today. And here’s a snippet as well of some of the images from that video that shows the glue, the actual board with ball bearings set in the glue, how to slide it inside your belt and put the belt on. It also shows how effective it is with putting it on a dummy and then blowing it up around metal devices, so you can see how it hits. They also get into pounds per square inch and how much explosive it actually takes to have a significant effect on the human body.

Once again, using US specifications: these are actual images of the Oklahoma City bombing (see left-hand image); they’ve translated it into Arabic, and also some of the specifications that were provided as a result of those actions by Timothy McVeigh. It also gets into best practices for pounds per square inch and how much explosive you need to have based on the size of the vehicle, whether it’s a compact sedan all the way up to a semi-trailer; the number of kilos of explosive and the feet that will be effective from the red, yellow or white perspective, and their effect on the human body based on certain distances. This has been published and made available out there as well, so they have an idea exactly what the impact would be based on how much explosive they pack into whatever particular device they’re going to use.
This particular site (see right-hand image), Pillars of Khilafah, as it existed then on Google Groups, is no longer available. But it was something that was referred to through a Muslim forum, and you could go in and participate in the Google Groups out there on the Pillars of Khilafah. Now, what is Khilafah? It’s basically the political system of Islam; under the Khilafah the entire breadth of the Islamic system: social, economic, educational, foreign policy, etc. are implemented.
Khilafah is also responsible for spreading the message of Islam to the world. And the Islamic state, which the Prophet, peace be upon him, sought to create and worked for in Mecca for a period of 13 years until he, peace be upon him, established it in Medina, served as the first model of the Khilafah. It’s ruling by Islamic laws, and it’s basically the way of life, and the representation of the one who has the right to adopt the divine rules. The representation here of Pillars of Khilafah, you could find it through multiple different links and sites at the time, and it is now gone. It also had a WordPress site that corresponded with it.
One of the Jihadist videos created in August of 2009 was pure propaganda. The whole point there was the alignment of the US with Pakistan. Trying to look very academic, one can see that the person speaking has got medical books down the bottom left, different Islamic books. He’s trying to show that he is very learned, and it was definitely quite a prop put up there to set that up. He’s actually a medical doctor. He is not an imam or related to religion in any way, such as Awlaki was.
Interesting observation here is that doing a search on the Path to Doom soon after it was posted, I found 1,63 million instances of the Path to Doom around the Internet (see left-hand image), whether it was archive.org or muslim.net/bb, vBulletin Bahraini forums, Flickr, all the different forums and sites, as well as news sites, were actually carrying links to or information about the Path to Doom. It spread very fast and became viral.
One of the well-known Jihadist videos is very interesting in how it starts out very idyllic and cherubic – green grass, very contrary to location; this was done in Iraq. But it was trying to tie very closely the idea that the West and Christianity is at war with Islam. So, constantly trying to make this tie as part of the indoctrination process, part of the alignment to something that doesn’t exist; the crusade type of mentality.

There continues to be an obsession with aircraft and flying. This particular site (see right-hand image), although relatively innocent, covers anything and everything you could think of relative to flying. It’s amazing what is out there. You name it – it is there, relative to flying.
A recent posting in translation about this particular site related some information on how to get involved in this activity: “We need to study and learn military industries, engineering and technology for the next stages of Jihad. Each one of us can become the owner of a specialized training through the systematic study at a university or institute for specialization, which is required for the Mujahideen. But a warning to those who enter a university to study dentistry and then say that this is for the sake of Allah. To study any discipline, the Mujahideen must choose something really useful to prepare for Jihad, and nothing less. Attend study and sessions held by the specialization centers in engineering, aviation, chemistry and computers. This is characterized by two things: short duration of the study, focus on practical applications of the topics, and enroll in institutions for working professionals in your current craft, if possible”.
The whole idea here is to use it always for the needs of the Mujahideen with Jihad in mind. Again, this site has anything you can think of, from remote control aircraft to simulators, training, location, online training, flight safety, simulators – it’s all there. One of the things they also warn on is not coming to the US to study; to do it in the Gulf States for the most part and to stay clear of the United States and any identification of this activity.

Other training includes more militaristic-type training, such as ambush techniques (see left-hand image). This particular document translated is a detailed study of various types of ambushes: kill members of the enemy and set up choke points in ambush areas. One here in particular is L-shaped ambush that they view as pretty successful in various locations, including Iraq and Afghanistan. This is from 2010 translation, and it’s pretty detailed and explains how to go about performing these ambushes; most likely taken from US field manual that was made available online. Regardless, it continues the education process prior to actual physical training and execution at a terrorist camp.

There’s been great innovation when it comes to bombs and bomb making relative to the Salafis (see right-hand image). In this case it’s actually a Yemeni and his brother. But the phone shown here down on the bottom left were the phones used in Madrid bombings that killed 200 people. The phones can be set up as self-timed triggers, devices that can be triggered by phone call or text. There’s a detailed instruction online on how to use these devices in videos and in text.
And it demonstrates proper methods to deploy explosives without harm. Such phones have been used as human anal inserts in one such instance in Saudi Arabia, where the brother one still sought the enemy bomb maker behind the underwear bombers and placing explosives in printer parts was used as a human explosive. The phone serving as a remote triggering device inserted in the rectum, while the bomb triggered the device inside his rectum remotely.
He passed through two sets of airport security, metal detectors and police security in the Kingdom of Saudi Arabia, and it’s reported that the conversation was recorded by Al Qaeda. You hear a beep in the middle of two identical phrases that are repeated by the bomber and his handler, and a text message then activates the bomb. Luckily, the Saudi royal family member was not injured much beyond an arm and hand here. Others did die; this shows splatters from the lower half of the body of the gentleman here (image above). It was very innovative in using the human body. We hear things about planting explosives inside of people, but it actually already has happened, and it’s not that far-fetched.

One such individual who took his online training to actual execution was Tarek Mehanna (see left-hand image). There are lots of “Free Tarek” sites out there. This took place in Massachusetts, where Tarek was set up by a friend of his and recorded planning and plotting to possibly execute a Columbine-style hit on the mall in Massachusetts.
Regardless, here is some of his indictment and things that he did. Here one of the things actually was translate the 39 ways to serve and participate in Jihad, and he was trying to educate others on this. So, he was moving from a relatively online training to an execution and finding ways to get others involved in this and to align others in his effort. Regardless, he’s now serving prison term, but he was caught with a lot of this information in hand, and was participating in different activities at the local mosque.

Somewhere along the line the Jihadis were able to get hold of the FBI Field Kit for forensics (see right-hand image). This was posted online on several sites, 71 MB per section, 17 sections, created on a DVD as an ISO image, exposed over 4 GB worth of data. You can see some of the information here listed in the forensics kit: Cryptcat, Netcat, different tool sets, many of which you might have been able to put together yourself. But there’s much more to it than this; we’ll show you in the next couple of slides.

Here is a bit more extensive listing of what is actually in the Field Kit (see left-hand image); this time from forensics tools and security tools and field kit manuals out there. These manuals are actually full PDF books, fully available. There are still more interesting things coming up with respect to what is out there.

One more view on what is actually available on the toolkit – again, some standard security tool sets out there (see right-hand image). Nothing earth-shattering here when you look at this particular listing; fully aggregated, though, and built into an effective toolkit.
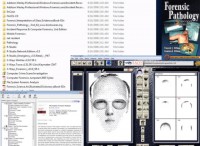
Other toolkit combined physical, as well as cyber type of activities, crime scene investigation, all kinds of different books (see left-hand image). The most interesting piece was the faces tool set, which allowed you to do sketch art right from your PC. That was a pretty interesting tool out there, fully made available out there, and has been in use for quite some time and downloaded by the Jihadis.
Here’s a full breakdown of the parts for the particular disk (image to the right), the Field Kit through 17 different parts; the ISO image, 1.4 GB, overall explodes out to about 4 GB. I’m not sure if it’s still out there.

Another snippet on communicating Jihad here (see left-hand image); I will be doing a separate write-up on Jihad overall that will be forthcoming in the next couple of months here. Regardless, Inspire magazine first came out in Arabic language and eventually was translated into English, and we’ve seen now 11 versions of that, and it’s become quite well received in Jihadist circles, and it is something that the West is always looking for to getting its hands on to see what it can actually endue and deliver. So, it is full of the usual propaganda and information out there; there’s plenty other magazines available as well. This Inspire, though, gets our attention because it is, in fact, in English.
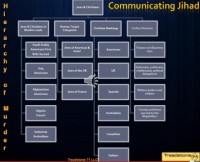
Now this particular diagram (see right-hand image), or the hierarchy of murder, as I call it, is actually a way of communicating Jihad, and also sets things up almost like a video game. It starts with who to murder and who to kill. We’re looking at Jews and Christians. If we start moving from left to right here, Jews and Christians in Muslim lands will come first, in particular, Saudi Arabia. Americans are first and Brits are second. In Iraq they want Americans, Afghanistan – Americans, Algeria, of course – the French, and Indonesia – the Australians.
They have human target categories as well: the Jews of America and Israel, as well as Jews of the UK and Jews of France. As you go down the line, the points scoring on this video game would actually be in place and would go from high to low. Christian rankings: Americans, UK, Spanish, Australians, Canadians and Italians, as well as further divisions in the hierarchy of murder: they take you down in finance and businessmen, diplomats, politicians, intellectuals, political delegations, and so on.
The goal of targeting humans here is to provide clarification of the nature of the conflict: by targeting Christians and Jews it shows that it is a religious struggle and that’s, again, what they want to make this. To show the main enemy and to deter others is what they’re after; to spread fear in the enemy – and this is a requirement documented in the Quran. To raise the morale of the Islamic nation, destroy the image of the government that was targeted, and after the 9/11 attacks they believed America’s nose was in the dirt. Disrupt the plans of the infidels, like the time when Italy refused to send troops to Iraq. Also, like what happened in Spain, where the challenger of the Prime Minister promised to pull the troops out of Iraq after the attacks in Madrid, the train bombing set we covered earlier; and to punish them for killing Muslims. So this is the hierarchy of murder that helps communicate Jihad and lay out the architecture of who to kill first.

So, we’ve covered quite a bit in this talk today, but there is much more that we could have covered. The 60 slides is quite a bit to review, so excuse me for the length of this, could have spent a whole day in discussion, and the information has been collected over the years. Regardless, what we did cover is that we have to know that cyber attacks will continue and cause economic harm as much as possible, and they will continue to disrupt websites.
They intend to make money through online fraud and they desire to conduct more damaging attacks as much as possible, and they use the Internet for command and control. They not only use it for command and control, but their strategic and operational objectives. This doesn’t necessarily translate into hacking capabilities, but it does provide the opportunity for monitoring and disrupting their activities. Hacking is definitely coming on its own as a state-sponsored activity through the use of cyber proxies – we’ve seen that most frequently.
There are some caveats to this as well – the information is based on open sources, and open source provides a plethora of data out there, if you can sift through it and find little pieces and nuggets that you can organize into something that’s possibly actionable.
They are skilled in various technologies, and this is increasing significantly. Their medium propaganda is key to their recruitment and has been for some time as they follow the radicalization process. And they’re innovating all the time; most recently they’ve come out with some new technologies relative to encrypting Pigeon and other pieces that may not be known to others. They have malware encryptors and they have other tool sets that have been around for some time.
There was a heavy use of forums up to 2011; then they started to move more towards Facebook, YouTube, Twitter for faster communication setup. And this fits the lone wolf mentality of setting up my own. That will come in different discussions down the road as we move forward from 2011 up to current days. And they understand that 90% of the war is information, and if they can control it, if they can manipulate it, then they have the propaganda edge and they have quite some time.

And of course, their intent on slaughtering anyone who doesn’t believe as they do; they’ll use human activities, open source, culture, history, religion, language – any way, shape or form to move their goals ahead. I urge you all to study more on this topic and subject. Wish I could spend more time on delving deeper into this. Hopefully, this is an overview that has been worthwhile. You have my email address, should you wish to contact me further, available for cyber intelligence training services, counter-intelligence activities. Thanks very much, we have one more slide (see right-hand image above).






























