
Security experts Lance James and John Bambenek tell the Black Hat USA audience how they got together on the CryptoLocker ransomware case and how it went.
Black Hat USA host: With no further ado, I will introduce our speakers today. We have John Bambenek and Lance James.

Lance James: So, everybody knows what ransomware is this year, right? Please raise your hand. Anybody get infected with it? Keep those hands up. No, just kidding. Has anyone actually had a problem with it this year, whether it’s clients or personal – grandma, whatever? In a room this size, at 9 am, we’ve got a significant amount.
John, really, gets most of the credit for writing this talk, because he’s not a procrastinator like I am. We aren’t going to talk about ransomware, obviously, from the perspective of people who don’t know. We are going to skip that, if most people got a clue there. We are going to talk about some history of ransomware.
And a study of CryptoLocker – John and I kind of put together the CryptoLocker working group when this whole incident last year came about, CryptoLocker coming on the scene. We are going to go through that (see image above). We will discuss the intelligence response to it and the success. And pieces that were difficult as well, slowdowns, things like that. The lessons you can learn and take for the next round.
And we have kind of a major theme we want to talk about that’s important – how to do takedowns right. Liaisons of law enforcement and the industry – where the industry plays and where the government or law enforcement may stop; how to work with international laws and also just in general how to work with people’s skills, really. And then, we’ll look at what we’re dealing with in the future.
By the way, I’m Lance James, Head of Cyber Intelligence at Deloitte.

John Bambenek: And he smells delicious. Afterwards you should really smell him, because it’s quite mansome. My name is John Bambenek, I run my own firm Bambenek Consulting and I’m also affiliated with the SANS Internet Storm Center.
Lance: Is “Bambenek” related to Bambenek you?
John: Yes.
Lance: Ok, cool. I was just double-checking.
John: I just lack creativity.
Lance: Got it. You’re going to have to work on that when we leave.

John: I’ll be right on that. So, a quick description of what ransomware is – you know, any attack that relies on extortion. It wouldn’t be a talk if it didn’t involve a lolcat, but this one is actually relevant (see left-hand image).
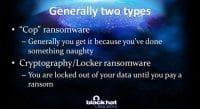
There are generally two types (see right-hand image). There’s “cop” ransomware – you know, we’re locking your computer, pay a fine to the FBI or NCA, or whatever particular thing. Generally, you get it because you’ve done something naughty. There have been a couple of cases where somebody has been perusing child pornography, gets ransomware that says, “Oh, thanks for reporting this problem; oh, by the way, you are under arrest for child porn. But no, thank you for reporting this.”
And the second type, which is mostly what we are going to talk about today, is cryptography/locker ransomware, where basically information is being held hostage for ransom.
Lance: Yeah. I’m going to bring up the first piece, even though it’s not the biggest theme in our talk. It’s ransomware in general, from a psychological perspective. We are going to go through CryptoLocker’s psychological effect to the user. The first type we’ve seen, actually, was a situation that I think was in Romania. Someone actually committed suicide over a piece of ransomware, believing it was real. I don’t know necessarily all the details or anything like that, but it has caused severe kinetic effects.
John: You actually jumped ahead. We’re talking about that in the next slide.
Lance: Oh damn!

John: Ransomware, despite CryptoLocker and ransomware generally being in the news since late 2013, is not something that’s really new. It’s not a new phenomenon (see left-hand image). The first known prominent case goes all the way back to 1989, where ransomware was spread with what’s called the AIDS trojan, or AIDS virus, on floppy disks. You had to send money to a PO Box to get whatever to unlock your computer. So, very slow – I guess it was effective for 89 – but there wasn’t a whole lot you could do with it. But this is a concept that has been around for a long time.

Early this century, because of ways technology developed, there’s all sorts of new means to leverage this particular attack threat (see right-hand image). You’ve got electronic delivery via network, watering hole attacks, which we’ve seen just recently and which I’ll talk about towards the end. There’s all sorts of naughty websites, where you get the “cop” ransomware. The means of electronic payment – sending money to a PO Box in Panama and waiting for something to come back takes time. With Bitcoin, you can process that fairly quickly. There are some other means of payment that we’ll talk about.
But generally, at least prior to CryptoLocker, the encryption was still unsophisticated. I mean, just think of how much we as an industry screw up encryption – the bad guys have basically the same problem.
Lance: Yeah, tons of it is usually homebrew. If you have never done any malware reversing and don’t really understand this, the difference between the symmetric and asymmetric in the effectiveness is that the symmetric key is usually a part of the binary of the malware itself. Historically, security researchers have recovered this quite easily and been able to provide a quick way to unlock one’s files. Today, with two-key encryption, this is something we thought probably would come a lot earlier than it did, I would say, but it actually came last year pretty much. And that was our big scare, like, when is that going to happen? Someone is going to actually implement public-key cryptography for malware in generally, and in this case ransomware.

John: Ransomware generally was a growing threat. There’s Reveton, a couple of other things that I mentioned in the bottom of that slide (see left-hand image), that have been happening. Encryption is hard, and people get it right. Lance talked about it. Even when people did asymmetric encryption, there were ways to get the private key, either it was on the machine or there were some other means of recovering it. Or they used the same private key to encrypt all of their victims, so once you steal one key you’ve got everything done. So usually there was some way to recover the data.

With all these things in mind, there’s a research where somebody says, “Oh, ransomware – this is scary.” I’m not taking it particularly seriously. When somebody says “ransomware” I’m thinking something more along the lines of this (see right-hand image). A crying baby who’s got her Angry Birds stolen. It’s a marketing threat. Ransomware was kind of the purview, at least in my mind, of chumbolones and jackalopes. And right know you’re hearing a bunch of people look up chumbolones in the Urban Dictionary.
Those are unsophisticated actors. People who may have caused harm, because you don’t need a lot of skill to cause harm, but nothing that’s really going to cause large-scale, real things that would capture my interest. As somebody who grew up on MTV, when they still played music, I’ve kind of got ADD, so it’s kind of hard to capture my interest.

John Bambenek: In August 2013, CryptoLocker appears. I get a call from one of my clients – that’s how I first found it – from a local government agency. Their director told me that, basically, everything got encrypted. It stumped all over the disk, so there was no real forensic work to be done, but they called and said, “Hey, can you help us out?” I said, “Ransomware, all the stuff is encrypted – no, I can’t help you out.” Then they go, “Please, it would really mean a lot to us.” I said, “I can bill you but I’m not going to give you anything in return.” They insist, “Please…” I said, “Fine, I’ll do it, whatever.”
I never got the data back. Well, actually, they are getting the data back now, but we’ll talk about that later. But at the time, there wasn’t anything that I could do about it. But it captured my interest. There are lots of things that this did differently that captured the imagination.
Lance James: I’m going to share my side of how we came in to CryptoLocker and actually technically met, I believe. So, I get a call from a partner, a director at a company, a friend that was like a colleague, and he gets hit with it. And Mary Galligan, who is actually a Director of our company, came from the FBI, running the New York division for a very long time. So she gives our research group a call and asks us to take a look at it.
We start examining the crypto and everything, which we’ll go ahead and talk about in just a second, but the interesting part of it was that the person involved actually at first denied paying it and asked us for help. We started to look into it, trying to figure out how much it would cost them to pay versus do a forensics. As we all know, forensics is not a cheap process, nor is it a quick process.
At that time, Mary’s connections and some other stuff we work with, you know, she gave a call and we had sent our analysis over to her to open a case, actually, in New York. And then, from that point, the shifting stuff that goes on in law enforcement, it went over to D.C., because I believe they handle ransomware in general. And that kind of started the whole liaison of the FBI work and also with the UK’s NCA.
So, what happened then was John and I actually ended up being in certain circles together, kind of connected on this and both moved right about the same time on this. And we’re very diligent about moving forward quickly with this, and I think we both kind of synchronistically recognized the same issues need to happen: we’ve got to move on this, we’ve got to get the community going, so we started the working group.

John: Yeah, exactly. We met a lot of great people on the working group. We’ll talk about that a little bit more in a second. But CryptoLocker was the first, at least in my recollection, cryptography-based ransomware that did it right (see left-hand image). They were running C2 servers, or proxies, more accurately. They generated the public-private key pair, transmitted the public key to the victim, and everything got encrypted. The private key was never even on the proxy, it was on some backend server. But it never touched the victim.
They used a domain generation algorithm, generated a thousand domains a day, so there’s some resiliency in how they operated their command and control network. So they are thinking about things and they are like, okay, we are going to be able to move things fairly quickly. Gameover ZeuS was its sole delivery method. Initially it was some proof of concept stuff, but starting mid-August 2013, only Gameover ZeuS was how it was deployed.
Lance: I was talking to David Dagon last night from Georgia Tech who did a lot of the assistance on this part of the research, the relationship between CryptoLocker and Gameover ZeuS. And I didn’t want to post in his slides without bringing him on the stage. But basically, I advise that you reach out and talk to Georgia Tech a little bit about some of this research, because they put together not a suspicion of only Gameover ZeuS, but actually through the DNS research he did he was able to push together – this is GoZ, this is CryptoLocker, here’s the relationship. Some great work from him as well.
John: Yeah, there’s a lot of good people who did a lot of things on this. And the other aspect of this is it used Bitcoin for payment. It also used some other paycard systems. So it had some electronic delivery methods. I mean, Bitcoin – many of you know – is anonymous. It’s not private, but it’s an anonymous way of transferring money back and forth. Some of the paycard systems, again, operated outside the conventional financial system. So they were able to get money, to get paid. So it’s kind of a novel and interesting thing for me.

But ultimately, this came down to the following: they had a viable business model (see right-hand image). I mean, we are talking about criminals, yes. But organized crime operates like a business, albeit one without morals.
Lance: Yeah. And one of the things in the highlighting from the previous slide as well as this business model – resiliency, if you haven’t noticed, is the theme in the last couple of years. Not only DGA, C2, all this stuff, but we saw a three-tier architecture. So, when we were looking at the C2, we called it “C2” but ended up calling it “C3”, because we had two layers of proxies, and then they were actually hiding the actual mothership for the data. So this actually took a lot of time extra for us security researchers and increased their business model efficiency quite well.
John: Absolutely. Maybe people don’t understand what I mean by “mob rules”, but these guys operate not in kind of your standard mob rules. The analogy I use is, for those of you who have watched “The Godfather” movie or anything involving the mafia, you know, you walk into usually a highly immigrant neighborhood and say, “Hey, you got a nice store here, it’d be a shame if anything happened to it. You pay us a little bit of money, we’ll take care of your business for you.”
So these guys – you pay them $300. I mean, prior to this, you may pay the ransom and you get nothing out of it. These guys made sure, as much as possible, you did.
Lance: You forgot the Russian accent there.
John: I was trying to do Italian.
Lance: Yes, but the point is … Russian mob. I’m just sayin’.
John: My accent sucks. But you smell great.
Lance: Thanks!
John: The other part of this business model you compare to credit card fraud or financial fraud. There’s an entire network that’s needed to really pull off credit card or financial fraud. You’ve got your kiddies in your watering hole stealing credit cards. You’ve got somebody buying them, people who are cloning them, you’ve got money mules – you’ve got all sorts of different roles involved in this.
With ransomware, all you need is a kit and somebody who’s walking to an ATM or whoever who can monetize Bitcoin. A very flat organization is necessary so that you’ve got high margins and low maintenance. So it’s something that really has ended capturing imagination of many other groups out there, which has led to the proliferation that we’re seeing.
Lance: I’ll bring up this – and it’s a speculation – but I feel that CryptoLocker, now that we’ve seen the success, if another returned, I can sense that the developer is going to be charging a lot more this time.

Okay, I’m going to cut through the tech details on CryptoLocker (see right-hand image). Let’s talk about the DGA for a second. I don’t want to rush into how the working group got together and all this stuff – but some of these little technical pieces we are going to kind of run to, but I’m going to fit them in between some of the stuff we’re talking about. There’s some funny stuff that comes up, for instance, the DGA that was used, which we’ll talk about as well later, is also a variant off of, if you look up domain generation algorithm on Wikipedia, minus a mod certain number is actually the one on Wikipedia as an example. There’s a little fast fact I wanted to give you.
Also, I’m going to kind of step into the relationship that occurred for us helping. The interesting piece with this was all the OPSEC involved in this. From the tier 1, tier 2 an tier 3 down to the public-key cryptography, down to the Win32 API – the crypto API was actually the native Windows system. So the architecture thought out with this was actually very clear. It wasn’t something that we just did overnight. The people working on this were really set down, architected and then engineered something actually.
One of the biggest concerns we had was, when we saw this from a security perspective and the slowdown it took us, it took a lot more people and quality and quantity to do it than maybe a few researchers could do to some other ransomware out there. One of the big pieces was that we were concerned about this epidemic. It was going to impact high. We saw the money and the actual copycats.
But how do you prevent something that works so well from suddenly being the next thing in the future? This was a big concern for us, and so a lot of the technical stuff, including the reversing of the DGA, and also the demise of the DGA in the first place – it really cleans up your viable business model we’re talking about. And it kind of scared us, because the word “CryptoLocker” has become synonymous with ransomware as a brand name for just ransomware. And we’ve seen a lot of copycats as well.

John Bambenek: So, a little bit of recovery and defenses (see right-hand image). A lot of this is best practice stuff. If you get your files encrypted, well, if they are important you should have them backed up and you should be able to recover them. If you run Windows 7 and greater, there are shadow volumes, where you can restore previous versions, assuming you can do it in a reasonable time frame. There are some ninja forensics tricks that can be done.
Lance James: Right. For instance – and the probability of it was really low, so again, backups are the number one thing – there was a Temp file that was generated while it was actually encrypting your data. The problem with the NTFS journaling file system is that the overwrites are pretty quick. So we recommend people to shut their computers off the minute they know about this in hopes that we may be able to get still available “deleted” files. This was an off chance of getting some or getting not. And in some cases, memory analysis can recover some files that were in use at that time. So, these are some of the tricks.
John: You can prevent execution out of the updated directories. There are more precise path names you can use that you can look up online, but keeping things executing randomly out of there isn’t recommended. You know, a lot of email-based malware and the like would be executed out of there if you’re mindless enough to do it.
Could you save it to your desktop? Sure. And some spam campaigns actually tell you to do this: “Oh, here’s your shipping invoice. Please save this to your desktop before you try to run it.” But this provides at least one layer of defense that requires the user to do something else to override it. And then, obviously, you can block the C2 addresses with whatever is provided for intelligence.
Lance: This actually goes into that reversing DGA. The C2s in this case were over 1020 domains per day. Most of you guys understand the domain generation algorithm concept, right? I’m going to kind of break it down very simply. Basically, the idea is to be resilient and autonomous, very little hands on when it comes to opportunistic stuff, Gameover ZeuS also being like this. DGA generates domains every single day, the strings. Those are usually random strings. When the malware gets on an environment or on an asset, it will go out and scan, based on the timestamp, for 1020 domains out there. And it will go and look for the one that hits and actually says, “Hey, I’ve got this.” So they don’t register all the domains, they register a few, maybe one or two or three. Now, also we registered a bunch, including Georgia Tech, and registered most of them on purpose so that we actually have daily stats and a low minimum window here.
In that case, though, when you want to look at prevention, one thing we did was we reversed the DGA and made sure that it was current and accurate. You did a lot of testing on those things, John. So we did this and we provided it in a feed, a different way. Some people threw it in their feeds. I think you had a free feed. We wanted to get it out to everybody. Once that feed hit in and you’ve got that in your proxy, if it blocked it then it could not get into those, because we were generating one day ahead every day. That was preemptive, you had detection – oh, there’s that box, it has Crypt0L0cker on it. But it can’t reach out. If it can’t reach out, it can’t get the key from the C2. So it’s a very important piece.
John: And something we noticed is that there were periods when they simply had no domains registered. CryptoLocker would keep scanning and keep scanning. They didn’t need to have domains registered. As soon as they popped up on the radar, you get your key, they get paid. For instance, the Russian New Year – there was nothing registered for about 8 days. We thought they just went away until somebody realized that’s a week when Russians pretty much drink non-stop. So they are just not worried about it.
Lance: Stereotypically, they drink non-stop. I want to say one thing, if you actually heard what was just described here, what John just described, whether it’s stop or not. Is everybody familiar with randomness and entropy, like we see this in passwords and things like that? Entropy, for anybody who doesn’t know, is the measurement of how random or pseudorandom something is on a computer. In this case, the strings here, your average domain, the properly used non-malicious domain is about 3.4 bits per byte in general, but it goes up to 3.7, and it can go down based on the string size.
In this case, these things were raised to over 4.0 bits per byte for each string case. Now, also what’s interesting is, as it’s getting none of those things during the Russian New Year, you would see NXDs, non-existent domain responses. So if you see an asset throwing 1020 DNS requests in less than a minute pretty much and get a ton of NXDs back, or non-existent domain responses, you might want to make a rule for that on your network and say, “Why is that even occurring?” Especially if you look at your cache and say, “I’ve never seen those domains in my life, they haven’t been on our network before.” So these are the kind of things that you would want to do for use cases, or prevention as well, preemptively, because it also might pop off other malware that you’re not aware of yet.

John: As I said, as a community we responded about a month late to this, but we eventually woke up and saw the threat for what it was (see left-hand image). Seeing police stations infected with this and getting news media coverage – that certainly helped, you know, that was certainly inflammatory. The sophistication got noticed. Ultimately, it was something novel and new. I mean, it was ransomware done right, this is something new. So we started paying attention to it.
And it also made a good case study on how to do threat intelligence. A lot of people talk about how to do it, but not much in the way of nitty-gritty of how to do it. This particular campaign – and we’ll go through some of the steps – made that very easy. I’ve spent time traveling around teaching people, using this as my case study of how to profile a threat actor and a threat to create an intelligence product and take action to disrupt it.

Eventually, as I said, we woke up, we saw the threat, and we created a working group specifically around it (see right-hand image). I don’t know how many people were on various kind of private intel sharing lists, but there are several of them where there’s an overlap to a degree, but not completely. So, while many of us are on all of the lists, some of us aren’t. So eventually, I just got frustrated because they all have their sharing rules, where one group can’t share with another unless authorized. It’s four different groups talking about it, and I got tired of trying to keep track of what lists I could talk about what on. And I just said, “You know what, one threat – everybody who’s interested, talk here,” and created a working group around it.
Ultimately, about 160 people worldwide took part in this group, and each brought their own special skillsets. When you talk about reversing a DGA, that’s a different skillset because that’s math. Then, reversing malware or tracking the infrastructure takes a lot of different skills to holistically go after one particular threat. And this provided a venue to do something.
Lance: And the industry to law enforcement relationship very quickly bidirectional for this on that working group. The industry and law enforcement really teamed up very quickly with this working group to work together. There would be phone calls left and right from different people to different people doing different pieces, still keeping it somewhat in the community and not everybody on the working group would know about every piece. But it actually encouraged law enforcement to be very much involved and utilized the industry very quickly, which is something that needs to be starting to happen, but with, obviously, some set expectations.
John: Absolutely. You know, the FBI is talking, “Oh, please, share data with us,” but there’s nothing in return, and that’s a frustration. That’s something that changed with this. I’m sure it happened in other threats. This is just the one I had visibility to.

John Bambenek: So, taking a look at CryptoLocker. A lot of this was a study in contradictions, because there were indicators that did not seem, at least on the surface, to reconcile with themselves (see right-hand image). So you think, Gameover ZeuS, silent threat, financial fraud – it wants to persist a long time. There is no subtlety or ambiguity about whether you have CryptoLocker. I mean, it’s “Hi, all your files are encrypted,” – you’ve got a big splash screen. So at a certain point – and we’ve talked about this relationship between the GOZ crew and CryptoLocker, the people who are responsible for it – why would people who run Gameover ZeuS expose the infection so loudly?
Lance James: I have a theory on this thing, and I think we all somewhat suspect this as well. In many attacks, in many types of malware, you have exploit kits out there. It’s a website, a drive-by download, it hits you and drops the stuff on you, right? And the solution is, we go after the exploit site, shut it down – done. The effectivity of CryptoLocker detection was actually usually after someone got infected and reported it. The reason why they may have used Gameover ZeuS for this was because it’s almost like a tunnel with a low footprint, something that we couldn’t just shut down. You need to shut down the entire peer-to-peer network to make this effective, and so they were actually winning the race, getting there before detection. And ZeuS being the most prolific and most successfully infiltrating into a network or onto a computer, this obviously proved successful and economically viable for CryptoLocker and the Gameover ZeuS actors.
John: Absolutely. Basically, they were set up for single-flux networking, so they were able to move IPs really quickly – they just never did. They’d sit on the same IP addresses for days, even though they had 300 TTLs. Why? It’s an open theory. The point of this is that, you know, if you are doing intelligence, figuring out and resolving these contradictions is where your intelligence value is. A lot of stuff is obvious. People want to make money – great, that’s a motivation. Does it really give you any real information? But figuring out why you have indicators that are contradicting each other and resolving that is really starting to get into the mind of your attackers. We can kind of deliver that intelligence value.

Following the money – obviously, a key part of this. Law enforcement was really helpful on this thing. One thing that kind of surprised me is that while many victims would talk to me and say, “Hey, can you help us recover our files”, they would not necessarily share the details of their payments. They were like, “No, no, no, I don’t want to give that out.” I think that goes to the psychological aspect Lance was talking about. Ransom is a scary thing; somebody saw some mob movies somewhere and thought, “If I shared this information with law enforcement, somebody would kill my cat or something.”
Lance: Another thing we saw was CryptoLocker targeted businesses. It was almost opportunistic but very spear-ish in its phishing email lists. It would pose as transportation type emails like ones from mail companies and such, and it would very effectively get into that. You know, in business your number one tool is email, you’re trying to move on your day. It’s effective, it gets in your email system, you download the attachment, it looks like some kind of a UPS email. And what would happen is you just want to move on your day. You’re a CTO in your company, or you’re VP, and you want to move on, but you’re also embarrassed, you don’t want to be like, “Oh man, I just got owned completely, my boss is expecting this report tomorrow.”
That, just like phishing is, where it gives this urgency, the sense of movement, was effective psychologically for that. We’ve met a lot of people that were like, “You know what, $300 – moving on, it’s my work laptop, I don’t want to get fired.” And that was actually the approach that we would find.
John: They accepted MoneyPaks, we saw that stuff be withdrawn at the same place. But they preferred Bitcoin. In fact, tracking some of their Bitcoin logs we saw, for lack of a more accurate word, “seed” money, where, you know, here’s some money transferred into your Bitcoin wallet, get all the infrastructure in place that you need. So they preferred Bitcoin, but we also used this to derive the estimates that you saw. That said, I think most people paid in MoneyPaks and other things, because Bitcoin is not really an accessible currency to general unsophisticated computer user.
Lance: Not yet.

John: Not yet… So, the DGA, while it provides some resiliency, also provides a good means to track their infrastructure. If you had the DGA and you wanted to protect your network, you can simply create RPZ zone, block all that stuff so that nobody in your infrastructure is going to get it, get an alert – you want to know that something is happening so that you can go clean that machine.
You could register sinkholes that would be accessed by anybody on the Internet. And we actually really had an OPSEC fail on this one. With more than 1000 domains that were registered, we were operating about 125 sinkholed domains to about 1 actual C2 proxy, basically waving, “Hi guys, we own your stuff.” They never moved, for whatever reason. And DGAs are not hard to tweak. Once you have an algorithm, they could have simply set “year equals year minus 2” – new 1000 domains, and we would have to reverse engineer that. They never did that. But we certainly got out of control on sinkholes, and that’s something that we need to get better at.
Lance: One of the neat things about this was the fact that we were so obvious about this sinkholing and the stuff we were doing. We were kind of letting them know. In some ways, we realized that with a really good strategy we could force them to move to a new DGA. Humans don’t have while loops, they don’t last very long. So, if we force this, register all these domains and then do this again, after a while they are going to change this entirely, because the success is only going downward. We didn’t have to end up doing this, we were in the process of doing it, and there was a shift in the Gameover ZeuS side of things. So, luckily, we didn’t have to really push that part, but that was actually one of the things we were being loud on purpose about: we’re letting you know, you’re on a cyber dogfight with us, we are going to play hard.

John: The DGA also provided a nice means to surveil their infrastructure. Ultimately these domains had to resolve to something. So, given a list of domains, you could do a ‘for loop’ if you really wanted to, if you like slow scripts. Currently, my surveillance scripting goes through 33,000 domains – imagine how long doing nslookups on those individually would be. But with a bit of technical tricks, you can use a package called adns-tool, which does asynchronous DNS queries, to basically spam your DNS server for 500 request, they come back when they come back. It allows you to do these things relatively quickly. For 33,000 domains, it takes me about 30 seconds to get nslookups back on all of them.
Lance: If you use Haskell, it’s actually built in natively.
John: Yeah, there you go. If you do this, consider setting up passive DNS. You know, not to commercial, I have no relationship with Farsight, but I use DNSDB because it’s a great resource. Consider that. That’s one way to passively give back with no real information, because this is the kind of stuff in passive DNS that I like being able to do as a researcher.

As an example, this (see left-hand image) is a feed that was generated out for simply domains registered in plus or minus two days. So if you’re looking to surveil their infrastructure, there it was. That was, obviously, from December of last year.

But there’s a little bit of bias in the way I generated this (see right-hand image). Every time you do some intelligence exercise you bring bias to the table. The way I generated this was I stripped off the sinkholes. I don’t care, because that’s not the business I’m in. My intelligence objective is to smash things. I don’t really care about detection. I mean, I feel sorry for people who became victims – you’ve got to protect your infrastructure, but I want to disrupt these people and just kick these people off the Internet. So I stripped out the sinkholes.
Now, if you’re doing it, or if you’ve got a network to protect, you don’t care if they’re talking to a sinkhole, nxdomain or a C2. You’ve got a problem – you need to address it.
Lance: I’m not going to bring up too many times about how you just want to just burn. Burn was your thing that we kept talking about.
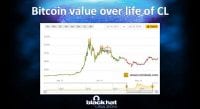
John: Yeah, burn all the things. Pillage first, then burn. As another particular aspect of showing how they changed over time, this is simply a chart of Bitcoin value since roughly July 1 of 2013 (see left-hand image). This had nothing to do with CryptoLocker, except that CryptoLocker liked Bitcoin payments. They, for whatever reason, thought their sweet spot value was $300. So, about the time where you see a Bitcoin at $1200, they chose 2 Bitcoins as the hard-coded value to get your files back. It went from $300 to about $2500. They kept releasing new binaries that changed that so that it would change the value over time to be something around that $300. So they did have some decent situational awareness.

Going back to my earlier point (see right-hand image), I’m not really interested in white paper or blog post or whatever. People do that, it has value. I’m not saying it doesn’t have value. What I want to see is bodies in the street, because I’m tired of these clowns.
Lance: I do want to mention something, though. Speaking of the politeness about their $300. The actual pop-up was also extremely polite. It was kind of like “hey, guess what’s happened, we’re going to just let you know that we kind of have your files.” And it was funny because it was sort of polite, it was like “this is the situation.” So, almost makes us want to definitely burn them more in that sense and shut this down, because the politeness was kind of too much.
John: It’s not personal, it’s just business, I’m sure they’re nice people. But no, they’re not nice people, but they might be nice to have a drink with.
Lance: … And say: “We know who you are.”
John: Yeah, exactly. One of the problems that we ran into is a problem that I call ‘sufficiency’. I mean, at a certain point, if I could say it’s talking to these domains and these IP addresses, you can put these rules in your IPS, most people are like “You know what, that’s good enough for me, I don’t need to do anything more, we can tolerate that threat.” When they get enough to satisfy these short-term objectives, they move on to what’s next. And if you’re fighting fires all day long, I don’t fault people for that. But we tolerate the continued existence of threats.
But the problem is that the people most in need of this protection aren’t the ones who are paying for it. And quite frankly, every organization has people who go home and have personal laptops – they’ll probably be using the same password for Facebook or Gmail or whatever, and they may get access to the stuff at home, and that’s leveraged to access people at work.

Lance James: We’re also sending a message quickly, and we need to keep that message going. You even saw the FBI has been doing it lately, they’re sending a message. They’re getting progressive, they’re moving forward, they’re trying to say, “Hey, we’re here and we’re not stopping, we’re going after this.” And the interesting thing is, we’re also trying to say we’re not going to let this keep going, we’re going to take this back. A lot of people say “offensive” and imply hacking back, but it’s really taking back. That’s what I think this was, offensive meaning proactive maneuver to actually really aggressively get this shut down. I mean, it was less than a year that this thing lasted, which is kind of a record breaker there.
John Bambenek: Yeah, and I feel bad about it, because we should be able to deal with this in weeks, not years.
Lance: There were a lot more events than we anticipated, it took us by surprise. I think it forced a difference in how we did things. We didn’t just have single, lone wolves doing things. Everybody did work together on this. In some ways, you think it’s a miracle, because it’s tough when you have competition between all these different people, but that all disappeared, which I think was a remarkable part.
John: Yeah, absolutely. And one last point is that there’s only so much you can do with passive intelligence. Every now and then you need to poke the bunny and see what they do.
Lance: Please consult your lawyers and your local sheriffs.
John: You know, and there are some things you can do without law enforcement. At one point, they were using a DNS registrar that was known for hosting APT. Somebody gave me the email contacts and I emailed over there, “Hey, these domains are hosting CryptoLocker. By any chance, do you have actual, real identifiable information for them?” They ended up just shutting the domains down. So, at that point, alright, how do they react to that? Well, they kept going back and kept going back. After a week of me shutting their domains down, they moved to another registrar, and then a month later they moved back to the other one in China. So, another contradictory indicator is saying, okay, what are these people doing? It didn’t make a whole lot of sense.

… Which kind of goes into some human intelligence of trying to get inside their heads, seeing what’s going on (see left-hand image). And ultimately, this was a very lucrative cash crop for them. They didn’t necessarily have this as their primary motivation. This was something they were using to fund something else. We know what that is, but we can’t tell you. But this is something that we were able to find in observation and poking the bunny.
Lance: It’s not personal, we just can’t tell you.
John: Yeah, strictly business. But they also had some good OPSEC skills to a degree, they made some mistakes. They had the framework for fast-flux and double-flux. Once we got our hands on their proxies, they spent a lot of efforts scrubbing things that we could otherwise use.

Another thing, I believe they bought their DGA from another provider (see right-hand image). They never changed it, it’s really easy to change. I think they bought it, somebody plugged it in, they ran with it.
Lance: Wikipedia…
John: Yeah, exactly. And that Wikipedia article with that DGA example was posted about the same time, literally, as CryptoLocker emerged using that DGA. An individual outed himself as probably more involvement than he cared to, just by posting to Wikipedia. Thanks for that, buddy!
Lance: The code is clean and simple.
John: Exactly. Again, you paid your ransom – you got your files. Standard mob rules, you know. They’re crooks, but they’re honest crooks.
Lance: Well, I still have a debate on this. You get infected, you get your files unencrypted, but you’re still infected with ZeuS, which does something else like bank stealing and things like that. So, what do you do next? Those are the things that, in an environment, you have to ask yourself. If you’re at home, you probably don’t know ZeuS is still on your computer. There was always an interesting debate on that: well, they’ve got you there, but some other piece of it also has you. Obviously, the effectivity of shutting down the ZeuS piece with this was one of the agendas for us.
John: Absolutely. So, some other stuff, sitting there and searching out, finding the stream of communications of victims that they had with the attackers. You know, there were people reaching out, “Hey, let’s try to work something out,” they didn’t tend to show mercy, but they tended to do troubleshooting.

Lance: Yeah. I’m going to read this. Basically, we collected some of the communication that had gone on for the ransomware (see left-hand image). And one of them kind of hit me hard personally, it said, “I’m a single mother and we three live thanks to my work, and I can’t lose it.” But ransomware had infected her work computer. It continues, “There’s a lot of rich people but we aren’t, and I have to work 10 hours from Monday to Sunday to take care of my children. Need your help, tell me as soon as possible how to get my files without Bitcoin, please help.” And this was an issue with both the availability of Bitcoin to a layperson, and also people living at $300 can’t afford this, and it is their work, and it could cost them their jobs. I made my own opinion on this, and I think it was right, where these people are just the lowest of lows, and this kind of highlights why we got aggressive very quickly.

John: A couple of fast facts about the DGA (see right-hand image). It’s something that was seen before. It was actually used on a previous campaign dubbed Flashback, which was a Mac based malware. You know, Flashback, CryptoLocker, Windows stuff gave us the idea that this was bought and then just implemented, and this was not something that they developed.

Lance: It’s known as Taus88 randomness. There’s a lot of academic papers, actually, on the technique for this. Really simple, mostly modulus-based. This is the actual algorithm based off of Wikipedia. The actual modulus was slightly different, but this is just a tweak. That’s how they would do this (see left-hand image).

John: So, here’s the map of infection to give you an idea of the heat map (see right-hand image).
Lance: These were actually obtained through sinkholes. This is the importance of sinkholes. They are the things that gave us a lot of this information.

John: These are raw infection counts. But a really better intelligence indicator was doing this per capita, showing the infections per country (see left-hand image). And what we noticed was that for Canada, Britain and Australia, there were identical infections per country. Canada was about 75% of that, and that gave us an indicator that they were using the English language as being the primary language on the PC. That’s how they were doing their selection, because part of Canada is, obviously, French-speaking. There are plenty of other places that speak English, and that’s why you see the noise, kind of trail of other countries, like Thailand, France, whatever. There are some English-speaking expats, or whoever, there. So, that gave us some interesting information.

Lance: So, we were able to access seized drives and we did some hard drive stuff (see right-hand image). Given the time constraints and some of the details of continuing investigations, we can give you some highlights. The OPSEC was higher than was expected. I mean, we didn’t really not expect it, but in most situations when you find seized drives most people don’t think about the fact they are “seized” in that they’re removed from the computer and moved into another environment. So, for the tier 1 proxies it was all in memory configs. They had nginx going on and they would actually run the config and then delete that config. If this got removed off of it, that’s gone.
We were lucky to use memory analysis to actually find a lot of this separate information in bits and pieces. In tier 2 – same way. The mothership used dm-crypt to encrypt the drives. We also had to use memory analysis and tweaking of some mounting issues that it also had, because they were kind of trying to obfuscate some stuff. But we were able to pull some keys, IPs – the locale was Russian – and a bunch of other stuff. Hopefully, further on we will be able to give a lot more information about the entire thing, which can be its own talk. But it was very interesting stuff.
John: And the proxies may or may not have been vulnerable to Heartbleed at certain points in time. That’s unclear on that point.

John Bambenek: Operation Tovar, going on to takedown (see right-hand image). Law enforcement agencies of 13 countries and lots of individuals and organizations participated. This took Gameover ZeuS and CryptoLocker offline whole and entire.

As of this writing, CryptoLocker is dead and has not yet to emerge (see left-hand image). There are some GOZ attempts out there. We don’t think there are any victims, but it’s clear that the bad guys are probing what we’re doing to see how we’re doing to prevent them from coming online, to see what registrars, what techniques they can use to get outside of our visibility. Again, we are providing near-time surveillance of that, too. The domains are being taken down.

So, did it work? Yeah. The reason? Law enforcement was involved, private sector was involved – there are true partners. But there was a lot of intelligence footwork done (see right-hand image). What’s the collateral damage? How will they react to it? Going into it, we know what’s going to happen.

We ended up waiting on the CryptoLocker takedown and merged it with GOZ, for reasons we already talked about (see left-hand image). But we spent a lot of time talking about the impact. What happens if we take the server of the private keys offline? Well, victims can no longer pay. You know, that is something that’s relevant. That’s a slower process than I would like, but it’s there. That said, as of about 6 hours after writing this slide, there is Decrypt CryptoLocker which uses techniques to, basically, decrypt those files. So, if you have a victim, even going back to August or September, now there’s a means to recover those files if they didn’t pay.
Lance James: And again, that’s a combination of the seized drives themselves working with the industry. Just visit decryptcryptolocker.com. I think Fox-IT and FireEye kind of worked together, and I’m sure law enforcement in Europe did as well. That’s exactly the kind of thing we are wanting to see more of.

John: How these techniques fail is somebody goes it alone, doesn’t care about collateral damage and breaks everything (see right-hand image). They burn before pillaging. In the absence of the rule of law, all you have left is tribal justice. But that makes it hard for people to do well-thought-out takedowns.

Regarding the future of ransomware (see left-hand image), you know, CryptoLocker is dead, but it captured the imagination. There will be other things out there.

There are a couple of examples out there (see right-hand image). There is a technique of locking iPhones for ransom using the Find My iPhone service. There was a cloud service company where somebody basically said, “Pay us this, or we’re going to delete all your stuff.” They didn’t pay the ransom, and an entire company went out of business. So, protecting cloud services matters, that’s an extortion-based attack. There are couple of other things that use Tor and Bitcoin.
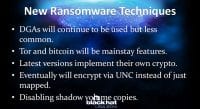
On to the techniques – I think DGAs will be out there for a while (see left-hand image). Tor and Bitcoin will still be used. Bitcoin provides a lot of benefit to the bad guys even if it’s not accessible to everybody.

Lance: Most of the ransomware techniques are really about resiliency and staying persistent: Bitcoin, anonymity, disabling shadow volume copies to prevent recovery and things like that.

John: Absolutely. The good news is that a lot of the intel tools that we developed for this can simply be used for other threats (see right-hand image above). We’ve got a to-do list of other things we want to continue working on (see left-hand image).

Here’s the call to action: there are more problems than there are people to solve them (see right-hand image). This takedown worked because a lot of people contributed their time, their effort and their skills to it, even if it wasn’t full-time work. Again, the short-term actions – okay,

I blocked this from my network, let’s move on – might yield value for an organization, but they don’t yield long-term results. If you would like to help us with this, get in touch with us.
Conclusion of every security talk ever given in the history of security: “Technology is risky and people don’t like you.”




























