
Cybercriminals keep on devising intricate instruments in pursuit of a more efficient online extortion. Compared to the myriads of crypto ransomware floating around the worldwide web these days, the one named Cerber appears to be more advanced as it accommodates a few out-of-the-ordinary properties. Furthermore, it has been up and running for more than four months, which is a long time for the average file encoder. One of the reasons why it has been afloat without considerable declines is because it circulates on a RaaS (Ransomware as a Service) basis. This means that different groups of threat actors can get their custom build of Cerber ransomware on underground hacker resources and even rent a botnet or use a readily available exploit kit to distribute the loader.
This infection has some country restrictions built into its modus operandi. In case it determines that the host computer is located in one of the East European states, including Ukraine, Moldova, Russia and Belarus, the attack will not continue. Otherwise, the program adds a random-named executable to the AppData path. This technique, incidentally, is sort of a defensive mechanism that prevents some antivirus suites from intercepting the threat as most of them are configured to monitor directories like Program Files instead.
At the early stage of the breach, Cerber forces the target system to reboot several times, with rogue “You are about to be logged off” alerts popping up during the process. The offending program then launches a covert scan for personal data, focusing on local volumes of the hard disk, removable drives, backup drives and network shares. The basic criterion for this checkup is the list of file extensions predefined by the ransomware authors. Directories like Windows, ProgramData, Drivers, Boot, Recycle.Bin and AppData\Local are ignored during the scan for obvious reasons – the attackers need the OS running smooth so that the victim can follow their demands and pay the ransom.
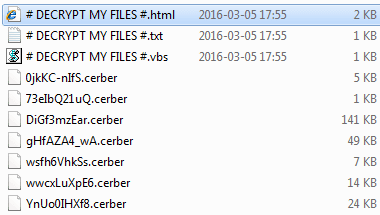
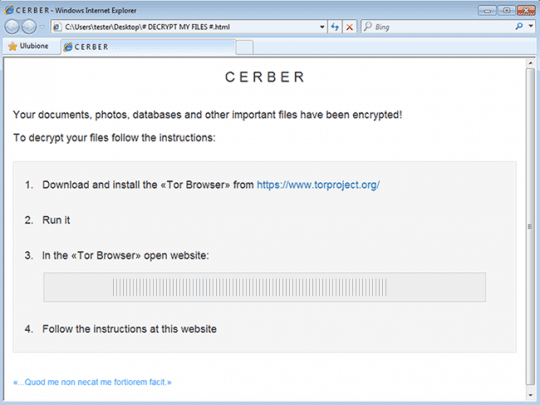
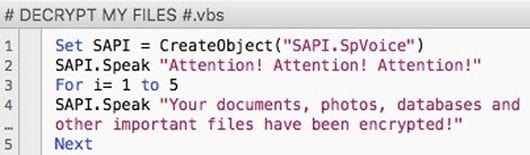
Every detected data files that’s most likely valuable to the user is then encrypted with AES-256 cryptosystem. Aside from becoming inaccessible, these files take a weird shape as well. The ransomware replaces filenames with 10 hexadecimal characters and then appends .cerber as the extension. This impact turns a ‘photo.jpg’ file into something similar to SwoHTB5ToP.cerber. The Trojan also throws in three editions of the ransom alert: # DECRYPT MY FILES #.txt, # DECRYPT MY FILES #.html, and # DECRYPT MY FILES #.vbs. The text in these notes says, “Your documents, photos, databases and other important files have been encrypted!”
The version named #DECRYPT MY FILES #.vbs deserves a special mention. It is a VBScript object that makes the computer generate an audio warning over the built-in or connected speakers. No other ransomware has this feature, which makes Cerber a one-of-a-kind computer pest. At the end of the day, the victim will navigate to a specially crafted “Cerber Decryptor” page via the Tor Browser. According to the site, the person needs to submit 1.24 BTC (about 800 USD) to a specified Bitcoin address during seven days, with the ransom size doubling afterwards. The countdown timer on the page shows how much more time the initial amount is valid.
Although Cerber has been on the loose for months, security experts have not succeeded in creating a free decryptor for it. This fact makes the victims confront a dilemma: to cough up a pretty penny and support the crooks financially, or try something else. Fortunately, there are methods that might restore some or all data encrypted by this ransom Trojan.
Cerber virus removal
As counterintuitive as it is, removal of this particular threat is not too complicated unlike the cleanup scenarios for screen lockers, which represent another group of ransomware infections on the loose. The main challenge in regards to Cerber is getting personal files back without having to do what the extortionists want. Basically, this means you can get rid of the malady using efficient security software without much of a hindrance, but options for recovering the encrypted data are a matter of a separate discussion, which we will touch upon in this guide as well.
Let’s now outline a rather easy and perfectly effective way of ransomware removal from a contaminated computer. Please follow the directions below step by step:
- Download and install HitmanPro.Alert
- Open the program, click on the Scan computer button and wait for the scan to be completed
- When HitmanPro.Alert comes up with the scan report, make sure the Delete option is selected next to the ransomware entry and other threats on the list, and get the infections eliminated by clicking on the Next button

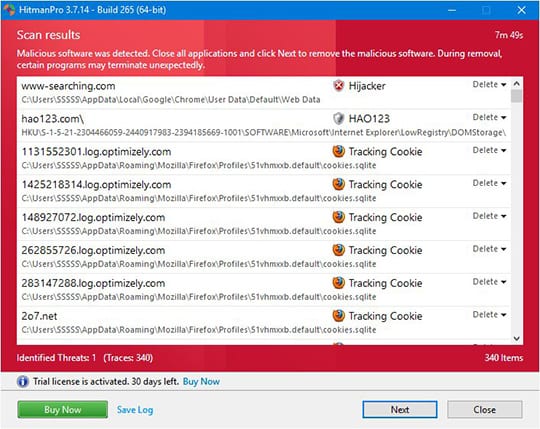
Now you’ve got both some good and bad news. On the one hand, Cerber is gone from your computer and won’t do any further damage. On the other, your files are still encrypted, since elimination of the malware proper does not undo its previous misdemeanors. In the next section of this guide we will highlight methods that may help you restore your data.
Restore encrypted files using Shadow Copies
As it has been mentioned above, despite successful removal of Cerber the compromised files remain encrypted with the AES algorithm. While it does not appear possible to obtain the key for decryption in this case even with brute-forcing, you can try to restore previous versions of these files either using the native Windows functionality or the application called Shadow Explorer. Please note that this method is only applicable in case you have System Restore enabled on your PC, and the versions of the files that you can recover this way may not be the most recent. It’s definitely worth a try, though.
Getting your files back using Previous Versions functionality
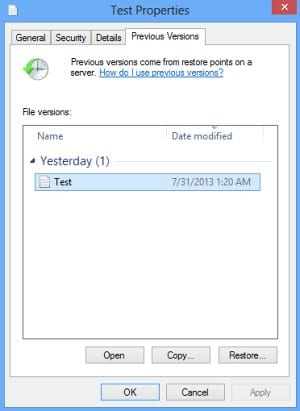
Windows provides a feature where you can right-click on an arbitrary file, select Properties and choose the tab called Previous Versions. Having done that for a particular file, you will view all versions of it that were previously backed up and stored by the so-called Volume Shadow Copy Service (VSS). The tab also provides the history of these backups by date.
In order to restore the needed version of the file, click on the Copy button and then select the location to which this file is to be restored. In case you would like to replace the existing file with its restored version, click the Restore button instead. Conveniently enough, you can have whole folders restored the same way.
Restoring encrypted data with Shadow Explorer utility
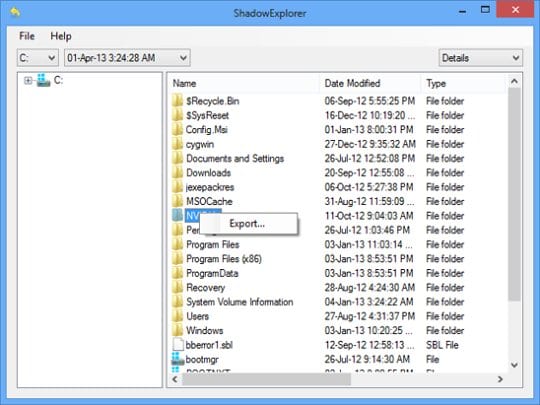
Besides the built-in Windows functionality highlighted above, you can use an application that will restore previous version of entire folders for you. It’s called ShadowExplorer. Once you download and launch this program, it will display all of your drives as well as a list of dates when Shadow Copies were generated. Simply pick the desired drive and date for restoration, as shown on the following screenshot:
Right-click on the directory you wish to restore and choose Export in the context menu. This will be followed by a request to indicate where you would like to restore the information to.
Use automatic recovery software
It might sound surprising, but Cerber does not encrypt one’s actual files. It deletes them. What does get encrypted is the copies. This brings us to the point where a specific type of software can be used for dragging the original data out of memory, where it ended up after the erasure. Efficient recovery tools can work wonders in these ransomware scenarios.
Download and install Recuva by Piriform to give this restoration vector a shot. By running a computer scan with Recuva, you will get a list of all recoverable files and be able to reinstate them to their original location or another place of choice.

Bottom line
Cerber poses a critical risk to one’s personal information therefore the focus security-wise should be made on prevention. In this context, some basic precautions can do the trick: refrain from opening email attachments from unknown senders and schedule regular antivirus software updates. Furthermore, performing data backups is a remarkable habit that will help evade the adverse aftermath of this attack.





























It the times of increased hackers creativity and new viruses everyday, new dangers and social media (yup, that too!), it’s good to know that there is someone good in the world. Someone who thinks about protection and means to fight back if and when your computer gets infected.
Also, love the name Hitman Pro :)