Sharon Conheady, professional social engineer from First Defense Information Security Ltd., shares her experience at DeepSec Conference, talking about the past, present and future of social engineering.
 My name is Sharon Conheady. I am based in London where I work as a social engineer, so I trick people, I manipulate people, I try to bypass security controls and ultimately gain access to sensitive information or sensitive facilities. And I think one of my favorite jobs over the last few years was when a client came to me and said: “Sharon, we are a bit concerned about how much our employees are talking in the pub. So, every Friday they go to the same local pub after work. We are really, really worried. So we would like to pay you to go and sit in the pub, and listen to what all our guys are saying about work”. I said: “Fantastic, that’s a great job!” I am Irish, so it’s really, really expensive.
My name is Sharon Conheady. I am based in London where I work as a social engineer, so I trick people, I manipulate people, I try to bypass security controls and ultimately gain access to sensitive information or sensitive facilities. And I think one of my favorite jobs over the last few years was when a client came to me and said: “Sharon, we are a bit concerned about how much our employees are talking in the pub. So, every Friday they go to the same local pub after work. We are really, really worried. So we would like to pay you to go and sit in the pub, and listen to what all our guys are saying about work”. I said: “Fantastic, that’s a great job!” I am Irish, so it’s really, really expensive.
But the next week they came back to me and said: “Yes, that was great, we got loads of information back, we were right. And people also frequently go down to the sports club, and we are a bit concerned about what they are saying when they are sitting in the sauna or sitting in the Jacuzzi. So we would like you to go down and sit in the Jacuzzi and the sauna for the day.” And I had to draw the line there because no way was I giving them the photos of that particular social engineering engagement.
Social engineering refers to efforts to influence popular attitudes and social behaviour on a large scale, whether by governments or private groups.
– Wikipedia definition
So today I am going to talk a little bit about where social engineering has come from, and in particular where social engineering is going in the future. So, first of all, the term ‘social engineering’ has been around for quite a while. And it was brought in towards the end of the industrial revolution when a Dutch industrialist named J.C. Van Marken realized that in order to run an industrial plant you needed both the mechanical engineers to look after the machines, and you needed the social engineers to look after the people side of running an industrial plant. So it’s a term from political science that goes back quite some time.
How the Eiffel Tower was sold several times, or the classic cases of social engineering
So I am going to give you a tour about social engineering over the ages. We will start with social engineering 100 years ago. And I think the turn of the twentieth century was the golden era of the con artists. There were so many fraudsters, so many con artists, and they had beautiful, beautiful scams. And many of you will be familiar with the film ‘The Sting’ starring Robert Redford, I mean that was a standard scam that they had going around this time.

This is one of my favorite con artists of all time, his name is Victor Lustig (see photo). This guy managed to sell the Eiffel Tower not once, not twice, but several times. So after the First World War, I think it was about 1925, this guy decided he would represent the French government. And he gathered some scrap metal dealers into a fancy room in the Ritz hotel in Paris, and he said: “Look, I am representing government, we are running short on funds, we have just paid for a big war, so we are thinking about dismantling the Eiffel Tower and selling it for scrap metal”. So he got some pretty good offers. And it happened several times, he was successful with this several times because the first couple of times it happened people were too embarrassed to go to the police. So he got away with it. But he was caught eventually.
But really, it was classic social engineering, it used current events. Every second virus that we get today is related to current events, that’s how they get people to open emails in the first place. There is malicious search engine optimization. So for example when the news about the Apple iPad was released, I think the first 3 or 4 results actually linked to malware sites.
So, you know, it’s a similar kind of technique. This guys Victor Lustig impersonated someone in authority. We see that all the time. And of course it was a very, very good deal for buyers. They thought they were getting a bargain, and that technique has worked throughout the ages. And again he was able to execute that attack again and again.
And it still happens today. Some of you might have heard of an English guy, a lorry driver, who was put in prison a couple of years ago because he tried to sell the Ritz hotel in London. And he was pretty close to selling it. It happens all the time.
Whose life story inspired creators of the film ‘Catch Me If You Can’

So 40 – 50 years ago, I would say the most famous social engineer was this guy, Frank Abagnale (the man to the left on the picture). The film ‘Catch Me If You Can’ was based on his cases. So Frank Abagnale was a fantastic social engineer. He is a really, really intelligent guy, he did all his research. He would always play an authoritative role as a lawyer, a doctor, or as he is probably most famous for, playing an airline pilot.
Someone may be wondering if this would still work today. Most definitely, so a Swedish guy was arrested recently because he had been flying passenger airplanes for 13 years without a license (see news report snapshot). He had the right documents, he looked the part, he had his stripes. And the police went in as he sat in the cockpit and was about to take off, the police was going to arrest him and they saw the look of relief on his face to be giving up the deception after 13 years. Just fantastic. It happens all the time, it happened in China as well. Look it up in the news, you will get so many examples.
I fancied trying this myself, I thought I could try my hand at maybe being an airline pilot, or more possible for me, I guess, an air hostess. So Frank Abagnale in his time had big difficulties getting his airline costume. Anybody who has seen the movie will know that he had to go direct to the manufactures and social-engineer them as well.
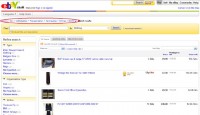
Well, it’s much easier today. You get the costume on eBay. And eBay actually had a section: Collectables > Transportation > Aeronautica > Airlines > Clothing (see image). They make it really easy for you. You can look it up according to whichever airline you want to be. But I am warning you: these costumes, the air hostess costumes, are really expensive, they sell for hundreds of EUR. Who is buying them? I really don’t know. So I don’t have one yet, but I’ll get one someday.
Taking advantage of emails from ‘friends’ and spreading spoof sensational information
So 20 years ago, Kevin Mitnick was the big name in social engineering. And he was the first person who kind of brought the term into IT security. This is his definition:
Social engineering is a term used to describe the techniques hackers use to deceive a trusted computer user within a company into revealing sensitive information, or trick an unsuspecting mark into performing actions that create a security hole for them to slip through.
10 years ago, social engineering started to get really interesting. We had the Love Bug virus, which is the first time we received malicious emails from our friends. So because they came in from our friends, why wouldn’t we open them? There was no reason not to. We had never seen malicious emails coming in from our friends.

And of course we had the first phishing attacks, phishers trying to take over AOL accounts. And now, some of the major social engineering headlines of last couple of years, of course the Google.cn story. And what was interesting about this is that the attackers didn’t target Google staff directly. They identified who Google staff friends were on social networks. And they took over their friends’ accounts. Then when they sent a message from the friends’ accounts to the Google staff members, they were far more likely to open it or click on the URL or download the attachment – again, because it came in from a friend.
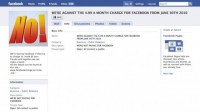
Then we had the Facebook charges. So people got emails saying Facebook was about to start charging for monthly access. People were really, really angry: “Facebook has always been free, how dare they start charging 4.99 a month for access?” So they objected, they were able to join groups on Facebook to object to this (see image). They were able to click on this Like. They downloaded malware all around the place, so it’s great social engineering.
How security experts fell victim to social engineering, sharing their own sensitive information and corporate secrets

Anybody recognize this lady (see picture)? Anybody friends with this lady? Because if you are, start worrying. This is supposedly Robin Sage. It was a security project done by Provide Security. They decided to set up a fake profile on social networks for this lady. They set up her profile on Twitter, on Facebook, on MySpace, on LinkedIn. And they decided to give her the title of cyber threat analyst. They let the project run for 28 days during which they tried to connect to various security people around the world.
And they were pretty successful. In the course of 28 days, they connected to over 300 security professionals. They got the photo from an adult website, they thought that this Robin Sage might appeal to many people in the security industry. So over the course of the month, Robin Sage received dinner invitations, job offers, and really, really sensitive information, including troop locations, what time helicopters were taking off.
There were a few clues in Robin Sage’s profile that might have made you suspicious, if you did any research on her at all. So firstly, if she was trying to connect to you, no way do you know her, she doesn’t exist. Robin Sage is actually the name of a military exercise. And Robin Sage said she was 25 years old but that she had 10 years’ professional cyber threat analysis experience. So maybe she did, maybe she was some kind of wiz kid, but the chances are…
So I am just going to give you some thoughts on the future of social engineering as I see it. First of all, we’ve seen with the pilot thing, we’ve seen with the selling the Eiffel Tower – it’s the same tricks that work over and over in history. We’ve got the same scams, the same cons repeated again and again. It’s just they change with technology. So 10 – 15 years ago, phishing attacks appeared. They took place over email, they took place over social networks. Now we’ve got Vishing, that uses the VOiP technology, we’ve got SMiShing that uses SMS. I am sure we will get whatever ‘ishing’ comes next.
How old are the Nigerian scams? Why are they called that way?

The beautiful example is the advance fee fraud. So the Nigerian 419 scams that we see so often today actually date back hundreds of years. The first example I could find was about 500 years old (see image). It used to take place in the UK, at around the time of the Spanish Armada. So they were targeting the members of aristocracy. The con artists would find a noble man, find a beautiful Spanish-looking lady, go to the noble man and say: “This beautiful lady’s father is imprisoned in Spain. We need some money to bribe the guards to help release him. And if you give us the money, not only will you be reimbursed with hundreds and hundreds of Pounds and gold jewels, and rubies, but you can also marry this beautiful Spanish lady.” Quite an offer! So lots of people fell for this. They’d give the cash advance, they’d never see the money or the beautiful lady again.

So we skip forward to I think the 1700s, or maybe earlier 1800s, and the guy named Eugene Francois Vidocq started his life as a criminal, spent years and years in jail and then interestingly went on to found the French police force as we know it today.
So Eugène François Vidocq published his memoirs, you can read them on Google or you can buy the book. And he mentioned a scam called ‘The Letter from Jerusalem’ (see image). And again, it was very, very similar. They’d target a member of the aristocracy or someone with a lot of money. They’d write them a letter giving them some reason to advance some cash to them. It might be something as silly as saying: “We are the assistant to this aristocrat, and he lost a box of jewels. We need to find them somewhere, so we need to pay the searchers. If you give us the money, we will share the jewels with you.” So I like the statistics that Vidocq mentions, he says of 100 letters, 20 were always answered. Because they were very, very targeted attacks, possibly the first example we saw of spear phishing.
And my favorite quote from Vidocq is that sometimes even the Parisians would fall for this scam. So it was very, very serious. Throughout history, again, they repeated, and we skip forward to the 1980s – that’s when these scams first started appearing out of Nigeria. The oil based economy was in decline. So some Nigerian students thought maybe they could get advantage of this. And they’d contact usually U.S. businessmen, sending them letters or sending them faxes, or even telexes, saying: “We can get you in this really good business deal if you just let us have a little bit money in advance.” So the same thing over and over. And of course it eventually turned into email attacks.

So this is the typical 419 scam that we see today (see image). Attackers will often try to make their victims feel some kind of emotion, because when we are emotional – whether it’s being angry because Facebook is starting to charge for account access, or whether it is because you are feeling obsessed or sympathetic because this guy’s clients all died in a plane crash – once you feel that emotion, you are more open to suggestions. So this guy says his bank clients and his entire family died in a plane crash and he needs some money, and actually if you click through or even type in the URL provided in the email, it shows a story. So this might not work for people in the security industry, but it could work for a lot of other people. So this is the Concord crash that happened in Paris about 10 years ago.
Why is the ‘Friend Scam’ getting widespread?

But today it has turned into more of a friend scam (see image). We often receive emails from our friends now, saying that they have been stuck abroad. The first time I received this attack, even I had to think twice about whether it was real or not, because I received it from an acquaintance rather than a friend, so I didn’t know the lady that well, I didn’t know her background. I didn’t know that she wasn’t in Nigeria, maybe she could have been in Nigeria. So she says that she was on the way to the hotel and she lost her bag. And she now owes a sum of 2000 USD, but she needs me to help out with a sum of 3500 USD, urgently. So no way was I handing over that kind of money. But the interesting this is that with a lot of these friend scams, the amount is often the exact same. You will see these 2000 and 3500 amounts repeated over and over.
So it’s old attacks reworked, and when the request comes in form your friend, of course you are more likely to comply with it. So they are getting very effective.
The latest one appears to be the London mugging. This comes in via social networks or via some kind of chat. Your friend will say: “I am sorry I forgot to tell you I was visiting London, but when I was there I was mugged, they stole my money and stole my wallet, so I need you to give me some money, again, to pay for the hotel.”
But I thought I was surprised that year when we got the whole volcano thing going on. Everybody was stranded across the world. That was the ideal time for social engineers to take advantage. And you can imagine if you were after a particular organization, most global organizations had people stranded somewhere because of the volcano. So find who these people are, offer them a lift, offer them some kind of assistance. There were tons of carpools set up. People disclosed their email addresses, they disclosed their telephone numbers.
This guy here writes: “I am in Amsterdam and I need to get to Dublin. Can anyone help?” He is going to accept a lift with anyone going that way. I didn’t hear of any attacks that used this, but you know it was the prime ground for social engineers.
Spear phishing – very targeted, very effective
Next on social engineering, the attacks are getting a lot more sophisticated and a lot more targeted. So take phishing for an example. Now, we still get those blanket phishing attacks that are sent out to everybody, but we are seeing more and more spear phishing attacks that are very, very targeted.

This was an example of an email that executives in big companies in the U.S. received recently (see screenshot). So it was a subpoena telling them they needed to appear in court the following week, or the following month. Now, first of all you get this email, you’re gonna be kind of worried. Do you need to appear in court? It looks pretty professional. It’s a long way from the early phishing attacks. It looks really, really good. It’s issued to an individual. It isn’t sent to groups and groups of people. It’s issued to particular individuals. So I think this is a very effective attack.
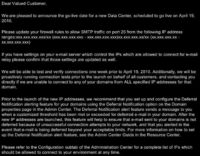
Another example we have was quite effective because the fraudsters identified the names of vendors that dealt with particular companies, and then they emailed them (see image). They didn’t have malicious URLs in the email. They didn’t have suspicious attachments. They actually asked them directly to open up particular ports on the Firewall or to accept particular IPs into their company. So that’s a really good attack. And the reason it’s good is because the sender knows a lot of information. So they knew the vendor name, they knew the name of the IT administrator, and in certain cases they knew the name of the project that the IT team was working on. So you can see that was a whole combination of social engineering attacks that must have taken place before they sent this email – very effective.
Parking tickets with malware URLs – scammers go beyond the IT in their social engineering attacks
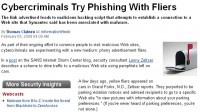
But of course the bait is not always going to be online. It could be in the real world, maybe nothing to do with IT at all. There was a really good example of attackers leaving parking tickets on some cars in the U.S. And when the people came back they saw they had parking tickets, and they were instructed to visit a certain URL to identify the photo of their car, click on it and pay their fine. And of course when they click on it – they download all kinds of lovely malware to their machines. It has absolutely nothing to do with IT, I think it was really effective.
So people are beginning to suspect some of the phishing emails they receive. They are beginning to expect some of the crazy pop-ups that appear on their screens. So if it’s on the computer screen in front of you – you are suspicious. If it’s in a car park and there is a piece of paper left there for you – you are not suspicious.
So I think that’s where social engineering is going. It’s open to such creativity now: the more creative your attack – the more likely it is to succeed.
Why social networks drastically changed social engineering techniques
And of course you can get so creative now; you can find so much information because of social networks. I mean social networking has really changed the face of social engineering over the past 3 – 4 years. Social engineers like to use social networks because it’s such a huge attack surface. We’ve all seen the statistics on the number of users. Of course it’s quick and it’s easy, sometimes you can even automate it to look up phone numbers that you can use in your vishing attacks for example.
It’s got a low barrier entry point, you don’t have to be technically skilled to do social engineering attacks via social networks. You just have to be a bit imaginative, or you just have to copy somebody else’s attack. You hardly need any technical skills at all to work this way on social networks.
It relies on publicly available information, people publish so much about them and they don’t realize it can be used in a social networking attack. And what I like about it is I don’t have to do so much dumpster diving any more because the information is available online, and I hate dumpster diving, it’s so dirty.
So you know loads of examples of people publishing their information. This person lost his phone and he asked all his friends to send their telephone numbers through. So they all did, and they all shared their friends’ telephone numbers as well. There are tons of examples like this.
Social engineering via social networks works because social networks are based on trust, and that’s exactly what social engineers like to exploit. It’s really easy to impersonate somebody on social networks.
Real-world impersonation as an effective social engineering trick

This example of impersonation in the real world took place in London (see screenshot). Some guys dressed up as policemen, went into a data center in the middle of London and said: “We’ve had reports of people on your roof, we need to go in and investigate.” So they went into the data center. Because they were dressed as policemen, they had handcuffs. They handcuffed the security guards to their chairs and they walked out carrying the servers.
But to execute an attack like this takes money. Well, first of all you are probably from a gang, you work in groups, you don’t go in on your own. You need to procure the policeman costumes somehow. So either you need to purchase them or you need to get them illegally. There is the potential for physically harming people, I mean they had to handcuff the staff to the chairs. As far as I know, nobody was hurt, but one person had to be treated for shock. This takes a lot of planning. And of course when you are doing a physical attack like this, it’s much easier to get caught. You compare this to setting up a fake profile online, it’s so much easier.
Really easy social engineering with the help of social networks
Social networks are fantastic for performing your research and your reconnaissance. So once you’ve identified who you are going to social-engineer, whether it’s a particular person or a particular organization, you are going to try and gather as much information as you can about them. And I will always start with LinkedIn. LinkedIn is superb for social engineers.
First of all, you can start by building an organization chart of the company you are trying to get into. You are going to establish who reports to who; who is the head of each department; you go through it and you identify the names of individuals working in there. You could target them, you could pretend to be them, or you could name-drop their names, like if you know the name of the CEO, if you know the CEO is on holiday, because maybe he has posted it with a TripIt plug-in for LinkedIn, so you know he’s out of the office and say: “He wanted me to do this work”, or “He is away in Spain and he needs this document, please send it to me so I can get it to him.” It gives you so much information.
Of course you can set up a fake LinkedIn profile and link in to your target. It’s pretty easy to image who should know who in any particular industry. And if people are friends on Facebook, like if John and Jane are friends on Facebook, and Jane doesn’t appear to have a LinkedIn account, set one up under her name and then send John a LinkedIn request, he is probably going to believe it. Lots of people accept LinkedIn requests from whoever sends them anyway, so you may not even have to set up a fake profile. And of course we receive LinkedIn requests nearly everyday, you know exactly what that email looks like – just spoof it.
So once you’ve got the name of individuals who work for your target organization on LinkedIn, look them up on other social networking sites, see what they have on their Facebook accounts, their Myspace accounts, do more tactical research on that person. Here is an example, you know these surveys that people fill in and like to publish online, they like to give away their dates of birth, they like to give away their home addresses, and more.
Examples of targets social-engineered using social networks
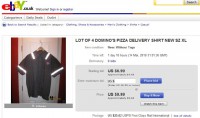
So this guy Bob, I noticed that his perfect pizza is the Domino’s Meat Feast pizza, so I thought about how you could use this in a social engineering attack, it’s very similar to one I did do in a company. So you know what company Bob works for and you know what city he works in. They have several branches in that city, so you call around to each branch until you identify which one he works in. Then you buy your Domino’s delivery shirt, they are really cheap on eBay, you can get 4 for 9.99 USD, buy it now. So share them with your friends.
So you got your delivery shirts, order the Meat Feast pizza from Domino’s, collect it, go somewhere else, put on your delivery shirt and bring the pizza to Bob’s office. If he objects and says he didn’t order it, tell him one of his friends did, you got the names of all of his friends from his Facebook account. So you are in the office, plug in a wireless access point, plug in a keylogger, actually physically take the information away.
If you think this is too risky, how about you email Bob a voucher for a free pizza, maybe his birthday is coming up next week: “Hi Bob, thanks for being such a loyal customer for Domino’s pizza. We would like to offer you the next one on the house, print the attached voucher.”
This is another guy Joe, and Joe was really, really useful to us. Not only did he publish all the information about where he worked, where he was born, what school he went to – he also says what his income is as well. So from an attacker’s point of view, you know exactly how much you can take this guy for. So here are a couple of things on his survey that caught my eye: his goal this year is to give up smoking; his deepest fear is creepy-crawlies; and again, he’s got a favorite pizza in there. So how could you social-engineer this guy?
Here are a couple of ideas. He has got 45 friends on his Myspace page, you know when his birthday is. There are lots of birthday cards now that come with CDs in them. So send him a birthday card on behalf of one of his friends with the CD or USB key in it that supposedly has dancing ladies or something like that in it but obviously goes on to compromise his machine. Send him a ‘stop smoking’ pack – again, it’s some kind of media that he needs to plug in, or maybe even a link to a site he should visit. Or finally, you can threaten him with creepy-crawlies until he gives you the information that you want.
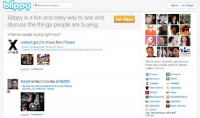
Blippy.com is another fantastic resource, again, for social engineers (see screenshot). So you can register your credit card accounts to Blippy, you can register your online purchasing accounts like eBay or iTunes, or Netflix to Blippy, and every time you make a purchase, it appears there and people know exactly how much you paid for their gifts, or how much you paid for a bottle of wine that you’ve just brought to the party. It can be really useful for social engineers.
So take this example, this guy just rented a couple of movies at Netflix. He rented 2 ‘Spartacus’ movies. So email him or call him, say you are calling form Neflix and ask how did he like the ‘Spartacus’ movies, offer him the next one free of charge: “We would like to send you the third ‘Spartacus’ movie. What’s your email address? I will send you a voucher.”
Foursquare.com, a kind of geotagging social networking site, is useful not only for social engineers but for burglars. And I am sure you’ve all seen the Pleaserobme.com project that knows the location of people and therefore when their houses are likely to be empty, using Twitter, Foursquare and other services. Here is an example: so you take this first guy; he left home and he is going to this lovely Irish pub in Paris. So if you are after this guy, go to that pub. He has got his photo there, you know what he looks like. Strike up the conversation with him, steal his bag. Or while he is out, rob his house, break in and probably he has lots of work stuff at home. There are so many things you can do once you have this information.
So social networks are great, but there’s loads and loads of technology now that you can use to improve or automate your social engineering attacks to make them more effective or to make them more fun from the social engineer’s point of view as well.
Gadgets and apps that help implement social engineering attacks
You’ve got Photoshop and GIMP, you can make your own ID cards, you can make your own business cards, actually there are lots of sites that you can use online to produce ID cards and business cards as well, that’s not a problem. You can use Maltego or Pipl to do some passive reconnaissance. So you’ve got the name of an entity, whether it’s an organization or an individual, Maltego will give you really good graphical representation of links between that entity and other entities. So you put in the name of an individual, it may come back with email addresses, physical addresses, telephone numbers, etc. It’s really useful.
The Social Engineers Toolkit from Social-Engineer.org – again, it’s fantastic for social engineers, it’s a one stop social engineering shop. It’s really good for running any particular phishing program for example. It can recreate entire websites, it can automate sending a payload via a phishing email, it’s really good.
And of course there are so many other things, like physical bugs that you can put into rooms. They are so much slicker now than they used to be. I’ve got a handbag with a secret hidden camera in it that I bring around, I can use it for shoulder surfing people when they type their passwords, or I can use it for recording an entire social engineering attack. And of course you’ve got caller ID spoofing which anybody could do these days, you just buy an application to do that. You can buy a spoof card or you can buy an application for your smartphone. And spoof cards are often the number 1 seller on sites like Spy Associates (see image).
So it’s really easy to do. I feel like James Bond sometimes when I am doing my social engineering attacks because I have so much cool equipment. I really like this one – it’s a memory card inside a coin (see image). So sometimes when you are going to data centers, you have to hand over all your media and your mobile phone, everything like that, but they are hardly going to check every single coin you have in your pocket. You do have to be careful not to spend it.
But what about the technology and the equipment that we might expect to see in the future? A couple of months ago scientists made another development with regards to invisibility cloaks, so very Harry Potter style. Can you imagine if you had an invisibility cloak and you were trying to get into an organization?
Also there is a laser camera that takes photos around corners – what fantastic technology! So the whole idea of this laser camera – this is a quote from one of the guys that invented it – is: “You could generate a map before you go into a dangerous place like a building fire, or a robotic car could use the system to compute the path it should take around a corner before it takes it.” So it does have some pretty good uses. I thought – how fantastic would that be for shoulder surfing from afar!
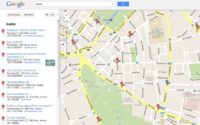
So this is where we are we are the purple spot just here (see screenshot), the red spots are banks nearby, presumably with ATMs. So how about you put a laser camera around the corner from each of these ATMs? You are not even near the ATM and you can get people’s PINs! A few complications at the moment are that the laser cameras are about the size of a room, and the picture quality is pretty poor for the moment. Can you imagine in the future, how useful that would be?
Social engineering as a service: outsourcing options
So finally, with social engineering, if you don’t want to do it yourself, you can outsource it now. They set up call centers all over the place that will do your social engineering for you. So they will provide you with professional callers, male and female, any language, any age that you want. And it’s approximately 7–15 USD per call.
So the whole idea behind this is obviously it is really easy to buy credit cards online. But getting a credit card, what do you do with it? It’s not actually that useful. What you want to do with it is buy valuable equipment, valuable things online and then sell them. So you’ve paid 2 USD for your credit card, you want to buy a laptop online, maybe the latest Mac, but you want to sell it for 500 USD, everyone’s getting a good deal, you make quite a good profit out of this. But the problem is the credit card is registered to a 77-year-old Italian lady, and you need to call up the bank to change the delivery address and to change the billing address. Well, the chances are; I don’t see anybody here that looks and sounds like a 77-year-old Italian lady.
So what do you do? You get one of these call centers onto the case. They’ve got some pretty slick ordering screens now where you provide the type of order, what age group, what you would like the person to sound like. And you pay 7–15 USD per call. So this particular professional call service example will make calls for 12 USD. They’ll only accept money for full calls. And if an operation fails because of insufficient data provided by the customer, they hold no responsibility: for example a question about the card holder’s neighbors, they might not have this info. So again, it’s encouraging you to research more and more about your target so that you can increase the chances of this call being successful.
Scareware has been a huge issue over the past years. We often see a pop-up saying: “Would you like a free antivirus check of your PC?” But lately what we were seeing here in the UK is people are receiving telephone calls saying: “This is Microsoft, we’ve noticed that you’ve got a virus on your computer. Would you like to outsource the management of your computer to us? We will keep it safe. You just have to pay a small monthly fee.” Of course you give across all your user credentials, as well as paying them a monthly fee (see image). This is all happening via call centers as well. So if you don’t want to social-engineer directly, just outsource it.
Future prospects of social engineering, plus some real-world cases
So again, about the future of social engineering. It’s always gonna be the same tricks repeated again and again with different technology. It has become a lot more sophisticated and a lot more targeted, frequently because of social networking which has provided us with a whole new attack surface and so much more information about our potential targets. There is more and more technology that will help you improve or automate your social engineering attacks. And now we’ve got social engineering ‘as a service’. Of course for me that means that social engineering has become an even bigger problem lately. And there is going to be a lot more social engineering testing.
So that’s it from me on the issue, but I would like to share some cases with you that happened to me and which I liked. So I really like the physical social engineering attacks when you actually physically have to break into an office or a data center, because you get such an adrenaline rush while you are doing them. I am a pen tester as well, so when you penetrate a system online or you get into a web application – you get a bit of a buzz, but it’s nothing like social engineering when you have people after you in the office. You are in somewhere, and the security guys could be right there, they may know you are in there, so you get such a buzz.
For example I was in one place, and they were recruiting temporary workers for an event that they were throwing that weekend. So the reception was very busy because people were filling in application forms. So I just went in and I sat there, and I had my laptop with me. I saw that there were lots of network points around the room, I plugged my laptop into several of them but they were dead.
 There were about 3 security guards at the reception desk in this room but they were quite busy, so they didn’t see me. But they had a computer where they registered everybody coming into the organization and that was just standing in the middle, and it was obviously plugged into the network, so I thought it was obviously live. So I went straight up to the security guards and I said: “Do you mind if I check my email? It only takes a second, just need to take your network cable out for about 2 minutes.” And he said: “Yes, no problem at all.” And he brought me over a chair. So I really liked that.
There were about 3 security guards at the reception desk in this room but they were quite busy, so they didn’t see me. But they had a computer where they registered everybody coming into the organization and that was just standing in the middle, and it was obviously plugged into the network, so I thought it was obviously live. So I went straight up to the security guards and I said: “Do you mind if I check my email? It only takes a second, just need to take your network cable out for about 2 minutes.” And he said: “Yes, no problem at all.” And he brought me over a chair. So I really liked that.
For remote attacks, I was quite proud of an attack I did when I found on the company website that they had some people who entered the charity marathon the previous week. So I spoofed an email that looked like it came from the marathon organizers and I said: “Congratulations to Joe and John who came 8th and 9th in the marathon; if you want to see where you came, please see the attachment.” It was pretty successful, it was targeted.
And we should be very careful about not stopping any business services. I was once in an office and I sat in the team meeting with 6 other people, and surprisingly no one asked me what I was doing there. And they were having their meeting and again, I took the network cable out of one of their computers, I’m not sure what service it was used for. And half-way during the meeting this guy goes: “Oh, I don’t have Internet access anymore.” And I said: “I am really sorry, seems I’ve taken your network cable, but here you go.” And he didn’t care at all.
But you do have to be careful, we have really tight statements of work that outline exactly what we are going to do, and what the client wants us to target, and what kind of trophies we are to gather. So sometimes they don’t even want us to plug in to the network, sometimes it might be a case of leaving some evidence in there, like a sticker saying: “Sharon was here on a certain date.” Sometimes they want you to plug in and simply get an IP address to prove you’ve been in there, or more often than not it’s just a question of sniffing some network traffic for 10 minutes – just as a proof of concept.
Another example from my early days of social engineering, so I decided I’d pretend to be a fire warden from the local council. So I went in with my clipboard, because sometimes the local councils actually do spot-checks to make sure you’ve got all your fire equipment in place. So I went in and I had the document printed off which the council would usually have, because it is on their website. I went into the office, went through it, ticked everything off, and I asked them whether they had some specific fire emergency policy. They said: “We do, but we can’t find it now.” So after I was gone they decided to ring the local council to say they had the policy, and asked where Sharon was as they wanted to send it in. So that’s when I found out that impersonating public officials is illegal. I don’t do that anymore.




























