
 ‘White Hat Defense’ CEO and popular podcaster Chris Hadnagy speaks at RSA Conference on how the bad side of social engineering may affect your company.
‘White Hat Defense’ CEO and popular podcaster Chris Hadnagy speaks at RSA Conference on how the bad side of social engineering may affect your company.
Here today I will talk to you about human hacking exposed – 6 preventative tips that can save your company. A little bit about me. My name is Chris Hadnagy, I am known online as loganWHD. I am a professional social engineer – that means means that what I do for work is companies hire me to find the vulnerabilities and weaknesses within their people networks, either through on-site visits, phishing, web, email, and things like that. I have written a book called “Social Engineering: The Art of Human Hacking”, as well as the podcast, and the framework, and other things that you can find out online about me.
But today the topic of social engineering is a very important topic, in my opinion of course, I am little biased. Before we can even talk about it, we need to define what social engineering is. I’d define it as any act that influences a person to take an action that may or may not be in their best interest. That’s a very broad and general definition, I know it, but the reason I define it that way is because I don’t always think that social engineering is negative. Your parents, your spouse, your teachers, your priest, your counselor – all of them use aspects of persuasion or influence to get you to take an action that is for your best interest, but those same influence principles, those same persuasion principles and manipulation tactics are used by the bad guys, and that is the type of social engineering that we are talking about today.

The reason this kind of a topic is so important is because the last year (2011) was labeled the year of the hack, and this is just a small sampling of the companies that fell victim to hacktivists and hacking attacks last year (see imege). And one interesting part about each one of these attacks was in an interview from a member of Anonymous, her nickname was SparkyBlaze; she said in an interview with Network World: “In my mind, social engineering is the biggest issue today”. Now, why did she say that? And the rest of the interview, she went on to say that in every attack on these companies they used some form of social engineering to gain access to the networks. So this is a very timely topic, it is a topic that we really need to discuss – how we can prevent ourselves and our companies, even down to our family level and our personal level, from becoming victim.
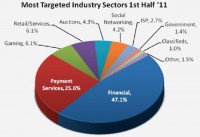
Why else should we care? Here is a website Apwg.org – it is an anti-phishing work group that does a report each year, talking about how phishing is affecting the markets. During the first quarter of 2011, you can see how the financial and payment services markets were hit heavily by phishing attacks (see chart). And if you can take a look there at the chart, you can see that almost every sector that we would be a part of was hit by phishing attacks.
This kind of calls to mind a report I read about the IRS1. It was two or three years ago, the IRS submitted themselves to a social engineering pen test. This was a legal, hired-for pen test, and in that pen test 60% of the folks that were tested from the IRS fell for this very simple social engineering test. I will demonstrate it for you: “Hello, this is Paul, I am calling from the Help Desk. We are doing a password upgrade due the new security policies, and I would like you to type in a new password that I am going to give you. Do you know how to do that? Okay, open up the password box and type in 1234password, click OK, and now you are secure”. 60% of the people who were asked to do that in IRS actually fell victim and did that. If this was an actual malicious attack, you can image the devastation it would have caused, many of us being tax payers and them having our information.
The former vice-president of threat research from McAfee said: “I am convinced that every company in every conceivable industry with significant size and valuable intellectual property and trade secrets has been compromised, or will be soon”. I actually subscribe to this belief, even though it’s a very bold statement, especially seeing what’s been happening in 2011 and continuing on into this year, the amount of organizations and companies that have fallen victim to hacking attacks, many of them involving social engineering.
So these six tips that we are going to discuss here are vital for us today. It’s very important that we apply them and we learn from them so that we cannot become victim of social engineering attacks.
But after reading Johnny’s book, I was looking for something, and that was in between the two doors – there was a gap maybe about half an inch to an inch big. Because of the engagement, I was wearing a tie, and in my knapsack I always have a coat wire hanger, it’s a social engineer’s best friend. I unraveled the wire hanger, put my tie off and shoved that through the little crack in the doors, waved in front of the motion detector – and, well, the two-thousand-pound magnetic locks got bypassed by the tie and the hanger.
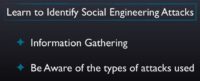
So what does this tell you? They wouldn’t have thought of that because they were not aware of the social engineering attacks that are being used today on companies. So becoming aware of these attacks, knowing what kind of attacks are being used and how they are being implemented is the first and essential preventative tip. If we don’t know what is being used, then we can’t possibly prevent against it. So becoming aware of it using information gathering tools upon our security teams, our IT teams or even personally, knowing what’s happening in the market – is a big preventative tip for us.
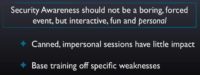
So security awareness needs to become something personal. In one engagement that I had, doing information gathering on employees, I found an employee who was running an RC racing car club – nothing wrong with that, company didn’t care, it wasn’t moonlighting, he just ran this little club on the side. People paid a small fee and they were able to come and race RC cars on the weekends. But he was using his corporate email account on his Facebook page where he advertised the service.
So we were able to play a part. I was now Jim and I was interested in learning how to race RC cars, especially the one I’d just got for my birthday. I had some pictures on this website of my new RC car that I wanted him to check out and see if he can help me learn how to race this car efficiently. And of course now we had similar likes, it was very personal. He clicked on the link – and the company was breached.
What does this have to do with security awareness? Well, the reason it worked is it was personal, it was something that was between him and me, and it was an interest of his. Security awareness needs to apply those same exact principles. If you want it to work, it should be something personal, something that is very deeply involving the individual that you are trying to train. And if you do that, then you’ll have success in your security awareness training.
In one engagement we called the Accounts Receivable department and we said: “Hey, this is Larry, I am calling from ‘ABC Waste Disposal’, a new company in town. I would like to send you a quote”. I built a conversation with her over the phone, and after a few minutes I was able to ask her: “So who is your present waste disposal company?” She gave me the name, and I said: “Okay, I will be emailing you a quote shortly”.
The quote never came, but what I did is I went to the website of the company that they used. I grabbed the logo form the website. You can go online, you find a 5 dollar shirt printing company, and you get a hat and a shirt printed with that logo on it. I then called the security desk and said: “Hey, this is Jim over at your waste disposal company. I am going to send Paul down tomorrow because he has to check out your dumpster as we got a call from environmental department saying it was damaged”. He puts the name Paul on the security checklist. The next day I come with my shirt, my hat and the clipboard. Clipboard makes you official, doesn’t it? No matter what you’re doing, if you have a clipboard – you’re official. So the clipboard made me official, I didn’t even need to go through security, they let me right in, pointed me in the direction of dumpsters – and now I am doing a dumpster dive in the middle of the day, collecting all of their paper trash, able to go through and find the documents that we needed to perform the breach.
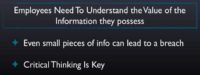
Critical thinking is key in this preventative measure. Teaching employees to understand that the value of the information that they possess, even what seems like a very little and unimportant piece of data, can cause a breach. It’s important to know when we give out information whether that person we give it to deserves that information. And the question that should be asked is: “Do they have the right to ask it?” It’s a very important tip here for prevention of social engineering attacks.
But there was a company that I worked with, a printing company that when we scanned their servers we found that on their public web server they had a couple of PDFs. Looking at the first file gave us info on type of PDF software they used, the version, and because it was comparatively the recent one, we figured that it is probably still the one they use now.
The second file was from a local cancer drive, a charity drive for cancer for children. I know it sounds horrible to do this, but we used that in the social engineering test because that’s what a malicious person would do. We called the company playing that we were from a local cancer drive, we wanted to send them a PDF that would outline the benefits of going with us as opposed to other cancer drives. Of course the CEO accepted the PDF because it was something very personal for him; and while on the phone, we were able to cause the breach due to outdated software.
Vulnerable software is the key way that attackers find their way inside your network. If they can scan and they can see an old FTP server, old browsers, old PDF reading software, any kind of software that is old and has public exploits – then you are definitely vulnerable. And that’s just the public exploits, there are also exploits that are not public – zero days that may be just coming out. So this is a very big preventative tip – it’s important, even though we know it is difficult and it can be expensive.
I am talking about thinking ahead critically about things that will happen and how you will handle them when they happen. I worked for the company that had no policies and procedures on how they would handle things: something very simple, like when you have to fire an employee, it’s an unfortunate event but it happens. Well, this company had an employee that was moonlighting, and it was something that broke company policy, and they decided that they had to let him go.
They called him in the office, and they sat him down, and he was agreeable, he actually understood. He was so friendly, he said: “I know what I was doing was wrong and I knew that if I got caught I would have to leave. So I am with you guys, thanks for being cool about it”. Meeting was about 4:30, the end of the day. He said: “Is it okay if I just take 30 minutes and clean up my office, take my pictures home and head out?” All the managers and CEO patted him on the back, and they let him do it. Well, before he left he erased 13 servers and all of their backups. 13 servers – I don’t know if you can afford that, this company could not.
Why did that happen? Because there were not scripts in place. There were no policies in place to say: “Here is the way we should handle it when this threat presents itself”. Let’s bring this down to a personal level. In your company, do you have a script in place on what to do if you’ve been social-engineered or if you suspect you’ve been social-engineered? You got an email, you didn’t think, you clicked the link, something came up that wasn’t what you were expecting. What do you do with that email? If you are not thinking of the answer right now, you don’t have a script in place.
These are the kind of scripts I am talking about. Having things in place that when you click the link, when you get that phone call, when someone approaches you, when you see someone shoulder surfing over when you are at the ATM – what are the next steps, what do you do to protect yourself from becoming a victim of social engineering? These are the kind of scripts that are necessary, and critical thinking is key in this preventative tip.
Audit is key thing that I always like to promote, just because you get a 300 page report doesn’t mean that the guy did a great job, quantity does not always measure quality. So social engineering audit should be something that is purposeful, that is directed towards your company, and the audit report should show you exactly what you need to do in order to fix the problems.
That brings us to tying it all together. When you want to tie something together, I would just work backwards in these 6 tips. The first step is having the audit. Once you have the audit – you see where you are weak, you see where you are strong. You will know what scripts to develop. You will know where to train your people. You will know what the security awareness should be about. Again if your employees are great about phishing, they don’t click on suspicious links in emails, they don’t fall for those kind of attacks – so giving them a 60 minute DVD to watch about phishing may very well be a waste of their time. But if they are weak on the phone, then that’s where you need to spend you time educating your employees. So having a clear action plan to put it all together is very important. Knowing what needs to happen, and when it needs to happen, and how it needs to happen is really what every company should strive to do.
Working backwards towards success means taking each one of these 6 steps and making a clear written plan – I like written plans, that’s an important piece for me: once you write something down it seems to be committed to memory and you’ll follow through. Once you do that, I can’t guarantee, again, that you will never fall victim to social engineering. But there is an old comic that kind of makes my laugh. There was a guy who was going to run from a hungry bear, and he had 2 choices, who was going to run next to him: one was a marathon runner, and one was a big guy like me. Who do you want running next to you when you are running from a hungry bear? Me, right? Because I’m gonna run slow. The comic makes sense because this is what’s happening today in the hacking world. When you are running your business, when you are running from the hackers, what you want to happen is you want to not be the low hanging fruit. You want to be as secure as possible so that when they are looking for the target; their eyes are not set upon you. These 6 tips can help you do that.




























