
Avast Software officials Lukas Hasik and Jiri Sejtko present their observations and insights into the prevalent web infections in the wild during their talk at RSA Conference. The key points in this part of the discussion are the ‘trust phenomenon’ explanation and the analysis of ‘Ill-family’ malware propagating in the ‘grey’ zone of the Internet.
 Lukas Hasik: Hi, I am Lukas Hasik and I work as a Quality Assurance Director at Avast Software. Next to me is my colleague Jiri Sejtko who works as Senior Virus Analyst and Researcher at Avast Software too. Avast Software is provider of Avast Antivirus – the antivirus with over 130 million users.
Lukas Hasik: Hi, I am Lukas Hasik and I work as a Quality Assurance Director at Avast Software. Next to me is my colleague Jiri Sejtko who works as Senior Virus Analyst and Researcher at Avast Software too. Avast Software is provider of Avast Antivirus – the antivirus with over 130 million users.
Today we will talk about web infections. So, on our agenda we have a short introduction, and then Jiri will talk about three most widespread web infections in the last year. And at the end we will get to some conclusions.
So, our presentation’s name is “Browsing Known Websites is Safe – True or False?” Most people think that they are safe when they don’t go to the ‘grey’ part of the Internet. This is the part where you can usually download illegal software like some keygens1, or you can browse some porn websites, or some warez2 sites.
So, most of the users think that when they don’t go to this ‘grey’ part of the Internet, when they stay in the ‘safe zone’, how we call it, they cannot get infected. However, it is not completely true. These people trust their websites more than the alerts from the antivirus that they are using or other security software. That is something that we call ‘trust phenomenon’.
Also, the website owners complain first to the antivirus companies that their site has been blocked before checking their HTML code for the infection.
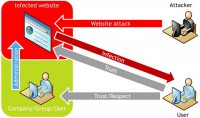
Let me show you a short example of how it works (see image). So, we have a trusted website owned or provided to users by some trustworthy company, and we have a common user, we call him George – ‘George’ is ‘Jiri’ in Czech. This user trusts the website, he visits it regularly, and there is no reason why he shouldn’t trust it.
But there is a bunch of bad guys sitting in the ‘grey’ zone of the Internet, who recently infected the website, and user George will not notice it because the website still looks the same. Visually, it is the same website, only the bad guys injected some iframe3 tags or scripts to the web page.
And when user George visits this infected website, the infection gets to his computer through exploits and from his browser. When an antivirus alert appears, he thinks: “Oh my God, what is it? This must be some false positive, I used to go to this website regularly, I’ve been there a hundred times.”
So, we expect that user George turns off the antivirus protection, and this opens a hole to his system for the exploits, and he gets infected. This is the main principle of the web infections, and now we will talk about the most widespread infections in detail.
JS:Ill-family description
 Jiri Sejtko: Let’s start with ‘Ill-family’ malware. ‘Ill-family’ has been one of the most widespread infections over the last year. It uses simple iframe tags at the beginning of the attack, and during the attack the bad guys added something new into each new generation, so the injected scripts went to be really anonymous. The web is not the only spreading channel for ‘Ill-family’ malware, but today we will talk only about web infections.
Jiri Sejtko: Let’s start with ‘Ill-family’ malware. ‘Ill-family’ has been one of the most widespread infections over the last year. It uses simple iframe tags at the beginning of the attack, and during the attack the bad guys added something new into each new generation, so the injected scripts went to be really anonymous. The web is not the only spreading channel for ‘Ill-family’ malware, but today we will talk only about web infections.
‘Ill-family’ is commonly known as ‘Port 8080’4 infections, because injections target malicious servers on Port 8080.
‘Ill-family’ uses the normal infection flow. So, our user George has his own website which he uses for sharing his life ideas, life stories with the rest of the world. He often uses similar web pages, he often searches the Internet, he often reads newspapers. He never goes into the ‘grey’ zone, so he thinks he is safe without any antivirus protection.
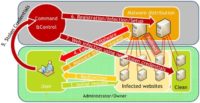
One day, just after he came back from the office, he started to do some usual business, checking his friend’s website. But recently, his friend’s website was infected with the ‘Ill-family’ malware, and when user George connected to this website he was immediately redirected to a malware distribution domain, from where exploits and malware were sent to his computer. And because he doesn’t use any antivirus protection, malware is installed on his computer (see image).
One of the basic functions of this malware is to steal credentials. So, credentials for his website are sent to the command & control server. This command & control server is used by bad guys to create new malware distribution domains and of course to infect new innocent websites with new stolen credentials.
At the end of this approach, user George is infected, his website is infected as well and used to spread infections over its visitors. This approach repeats again and again, and the network, the botnet is growing.
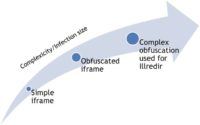
‘Ill-family’ is very well known for its evolution because the bad guys started using simple HTML tags, simple iframe tags to redirect victims to malware distribution domains. And then, in each new generation they added something new. They added some simple obfuscation, and at the end their scripts, their injections were about 4 kB long (see image).
Lukas Hasik: 4 kB of text? I would definitely notice such long text in my HTML.
Jiri Sejtko: Yes, that is right, it is much more noticeable to see that there is something wrong with your website. But anyway, bad guys are using this approach till today because it allows them to make the scripts and the injections undetected by simply changing the rules of obfuscation.
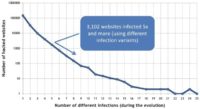
On this graph, you see the infection rate showing how active the bad guys are (see image). It actually shows the number of domains: how many times and how many domains were infected with how many variants of ‘Ill-family’ malware. The remarkable point here is 5, so more than 3000 domains have been infected with 5 or more variants of ‘Ill-family’ malware.
Lukas Hasik: So, 3,000 domains were infected 5 or more times? It looks like the bad guys really have their favorite domains.
Jiri Sejtko: Yes, that’s right. It’s more likely domain owners or administrators really don’t know their websites are misused by the bad guys to spread malware, so they don’t care or they don’t know. But this is the point you should care about because many of these websites remain infected forever.
JS:Kroxxu description
Jiri Sejtko: The second infection I will talk about is Kroxxu. Kroxxu is a multilayered botnet. It uses only compromised websites to host itself. It comes with indirect cross infection vector, which I will explain later. Kroxxu is a self-reproducing botnet, which means that it distributes password stealers, and the credentials stolen by these password stealers are then used to support the growth of the botnet.
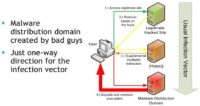
Indirect cross infection is actually a special type of drive-by download1. I will explain the differences that caused us to create a new term for it. The picture shows the usual drive-by download (see image), where you have a legitimate website which is hacked. When the user goes in there, he is redirected to the malware distribution domain from where he gets infected through the exploit kit2.
This malware distribution domain is owned and operated by the bad guys only with purpose to distribute malware, and there is no other chance to get into this malware distribution domain without previous redirection.
Lukas Hasik: So, it should be quite easy to block the malware distribution domain when we discover it.
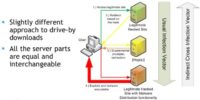
Jiri Sejtko: You are absolutely right. The easiest way of protecting users is to block the domain that distributes malware. But in the indirect cross infection, this is not exactly possible because all the parts used in the infection vector are interchangeable (see image). It means when one part, one domain is used as a malware distribution domain one day, it might be used as an initial redirector another day. Indirect cross infection actually means the ability to interchange any part of infection vector in order to create a new direction of this vector.
So it is not as easy to block the targeted domain because all these parts are hosted on the compromised websites. These websites are legitimate, you can’t simply block them.

This graph shows how long the currently living domains are used in the Kroxxu botnet (see image). We estimated the average lifespan of each domain used in Kroxxu to be around 90 days – just three months. And more than 300 malware distribution domains live more than 3 months. These two numbers are really big in comparison with other approaches of normal drive-by downloads, so this is the point we should care about because administrators and domain owners probably don’t know their websites are misused to spread infections.
JS:Prontexi description
The third infection I will talk about is Prontexi. It uses a little bit different approach to spread. It uses infected ads. Previous approaches target mainly small websites. Well-known and big websites are usually well secured to be infected that way. Their weak point stands in advertisement. It is the only content the owners cannot influence, and they shift the responsibility for the content to the ad companies. And ad companies probably don’t care about what they are distributing, because in case of Prontexi we have detected on our user base more than 5 million infected ads that redirect users to the malware distribution domains.
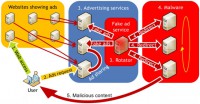
So how does it work? Let’s get back to our user George again. User George often reads newspapers. And these newspapers use ad services to profit from them. So user George connects to his favorite newspaper and he is redirected immediately to the ad service. These ad services share content with fake advertisement services that spread only fake ads and share fake ads with each other.
So, user George is redirected through this fake ad to the malware distribution domain. There is usually more than one malware distribution domain, and fake advertisement services rotate these – that is the reason we call them Rotators. And from these malware distribution domains, user George gets malicious content through the exploit kit.
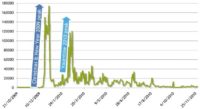
On this slide, you see how active bad guys are, and that they are targeting main events during the year. In the Prontexi case, they targeted mainly Christmas 2009 and New Year 2010, and of course Valentine’s day 2010.
Lukas Hasik: These are the dates when most people search for some presents, and they usually follow the ads to go to some websites.
Jiri Sejtko: That’s right, but in this case you don’t need to follow the ad. Once the ad is displayed, infection begins. So, that’s all about the three most spreading infections over the last year, and let’s move to the conclusion.
Conclusions
Lukas Hasik: We’ve finally got to our conclusions. So, now you probably know the answer to the question in the name of our presentation: “Am I safe if I browse only known sites?” – actually, the answer is “No”, as you probably know. So you can be sure that the infection comes from everywhere as the bad guys really like legitimate websites, because you don’t expect that the infection can come to your computer from these trustworthy and legitimate websites.
The bad guys also use the advertisement services because it allows them to get to your computer from sites that are visited by a lot of people, or that are operated by some huge companies, because they don’t have control of the advertisement provided through advertisement services.
And we haven’t mentioned the search engines that the bad guys really like to confuse with their blackhat SEO. These are the main channels that they use to get the infection, the exploits to your computer.
So, what should you do at least to keep yourself safe from the infections? The first thing is to keep your operating system and your software up-to-date. The reason is that when your operating system and your software is up-to-date, it will close the security holes for the exploits spread by the bad guys. And of course don’t browse or don’t download the ‘grey’ zone stuff. The infection ratio in the ‘grey’ zone is definitely higher than in the safe zone.
And the last but not the least, you should definitely use some good antivirus software, and when you are using antivirus protection you should not turn it off when an alert appears because you can be almost 100% sure that the website is infected. And if it is a false positive, you can be sure it will be fixed by our virus analysts in hours usually.
During our presentation, we spoke about the trust phenomenon, so one thing that you should remember is that even the most reliable sites can be infected, and sometimes they are really infected by bad guys, because it is the main channel to spread the web infection over to your computer.
Jiri Sejtko: We have seen the bad guys move many parts of infection vectors into the compromised websites, and in case of Kroxxu all of these parts were moved to the compromised websites. Malware authors are quick in adding newly discovered exploits.
So, there are two answers to apply. One is for domain owners – there are some tools, there are some products and services that will help you protect your site and keep it clean. And for users – be paranoid, even the most reliable sites can be infected.
Lukas Hasik: Jiri mentioned it a few times and you have seen it on the graphs that many infected sites remain infected almost forever. Once the site is infected, the web owners or the domain owners don’t remove the infection, or when they remove it they don’t change the credentials, so the bad guys can infect it again and again.
Jiri Sejtko: And some simple steps you should take when you find your website is infected: change your credentials, however it has to be done from a clean computer; remove the infection from your website – remove it from HTTP code, PHP code or SQL database; find the way your website has been hacked, to prevent future attacks; fix the holes in the software used on your server; and of course you may use some protection services that will help you keep your site clean.




























