
 Ex-CEO of Symantec Enrique Salem explains his viewpoint on the concept of “digital natives” at RSA Conference, and provides his vision of IT security’s future.
Ex-CEO of Symantec Enrique Salem explains his viewpoint on the concept of “digital natives” at RSA Conference, and provides his vision of IT security’s future.
Thank you and good morning. I have somewhat of a unique vantage point as the CEO of the world’s largest security company. And there’s an unstoppable force coming this way. And it’s already hitting the security industry like a sledgehammer.

It’s not a new virus, it’s not malware, it’s not an application; it’s not software at all. It’s not a new device, and it’s not a new form of cybercrime. It’s her and it’s him, and him, and him, and her. It’s this large group of young people that we call the “digital native generation”. They have a different way of doing things in this digital age. It’s how they work, it’s how they think, it’s how they interact. And they’re completely changing how we think about work and business and security.
I’m constantly amazed at how this generation collaborates and solves problems. If you know any teenagers today, you already know what I’m talking about. They don’t rely on search queries the way we do. They don’t rely on a single source of information like books, or articles, or websites. They get their answers on YouTube, from their networks or posts. They reach out across their networks to find answers or collaborate on a solution, and in doing that they often find faster, more effective ways to get things done.
This generation will absolutely impact how we do business, how we collaborate. And it’s not 10 years off, it’s not 5 years off; it’s happening right now, it’s impacting us today. So we must understand this new generation and we must build a world that works for them.
But before we go much further, I want to paint a clear picture of what I mean by “digital native” – how they work and how they think. “Digital natives” were typically born in the 1990s, and they’ve never known a time before the Internet or before smart mobile devices. By the time they’re 21, they will have averaged 250,000 e-mails, IMs and texts; 10,000 hours on their cell phones; 14,500 hours online. And most of the time they’re online, 80% of that time they’re using social networks.

Now they’re starting to enter the workforce. And this is how they prefer to work: they’re always networked, they’re always sharing, and they’re always multitasking. But it’s actually beyond multitasking; it’s something that we call “continuous partial attention”, or “CPA”. They’re doing homework, they’re being online, they’re skyping; they’re doing it simultaneously, and they’re redefining multitasking. They’re always mobile. But when I say they’re always connected and they’re always mobile, I don’t mean that they like to spend a lot of time online. I mean that not having their mobile device at their side, not having instant access to the Internet and their social network would be like the previous generation not having their wallet, their ID or their glasses. A mobile device is the tool they use to connect with everything, not just Facebook and Twitter, but everything. “Connected” is simply the way they live, it’s the air they breathe.
Many of us in this room now also feel that way. The inspiration for how we’re going to work tomorrow is coming from today’s digital natives. In fact, we’re already starting to feel that impact. But the digital natives – they’re not like us. We’re different. We’re digital immigrants. We weren’t born into this digital world, we grew into this world. We helped build it, and many of you in this room are charged with securing it. So we have a different perspective on mobile devices. We have a different perspective on connectivity. We tend to be careful about our identity online, not quite trusting the digital world to always have our best interest in mind. Now let me tell you and describe this a little further. Digital natives don’t use landlines, they don’t use pagers, they don’t use postage stamps. While we might still look for a restaurant review or a movie review in a publication, a printed one potentially, they rely on their social network.
While we complain about our inboxes being crowded, a digital native might not even have one, and if they do, they rarely check it. So e-mail will change. While we might remember games like “Pong” and “Space Invaders”, and “Missile Command”, and lots of other early videogames, a digital native thinks nothing about picking up a controller and in real time playing a game across the world with somebody they don’t even know.
So we’ve talked about the world being flat; I don’t think we’ve seen the true definition of that. They don’t know the meaning of the word “reboot” because they probably never had to.
And here’s another difference. The digital immigrants came to work with the Internet at work – that’s where most of us got introduced to the Internet. We bought it home and eventually got connected. To digital natives there’s no distinction between the Internet at work and the Internet at home. So, while there is a tremendous benefit to all of these connections, there’s also a greater set of vulnerabilities. Most digital natives don’t think about identity and security the way we do. Their connections are free and open, and that’s how they like it. That’s the world they work in.
If you ask a digital native about security in the cloud, they might actually tell you that’s a foolish question. The most important thing about what’s happening around the digital native generation is they’re going to change how we do business. They’re already accelerating this notion of the consumerization of IT. They’re “bring-your-own-device” by nature. They’re blurring the lines between business and personal; always connected to work, always connected to the personal life – one individual with many roles and different sets of credentials. So, while the lines start to blur between work and home and everywhere, the digital native is planted firmly in the middle. So it’s important for us to understand that this way of working isn’t just a subset of the way business will be done in the future. This is the future of business. For those of you in this room, this is the freight train of change that’s heading this way and hitting like a sledgehammer. All the ways we conduct business will change. More of it will be in the cloud, both private and public. It’ll all be mobile. It’ll all be connected; well, maybe constantly connected. Because when first digital native took his or her first job, the world had already started to change.
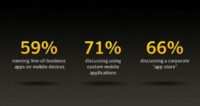
A recent survey that Symantec just conducted showed how real this change is, how being mobile and connected is the real world (see image). 59% of the people in the survey said they’re already running line-of-business applications on their mobile phones. 71% said they are thinking about building custom mobile apps; and 66% said that they are looking at creating a corporate “app store”.
Now, as we think about our employees and what they’re doing – they’re going online and using more cloud-based services with or without our approval, and so this change is real. And all of us in this room, we need to work together; we need to lean in and be more aggressive about embracing these changes. Countless times I’ve interacted with people who’ve told me: “I’m worried about how this consumerization thing will go”. The reality is there’s no fighting it. It’s only going to accelerate. We need to get out in front of it, and we need to get ready to protect it.

But now we’re getting to what’s going to be difficult. Yesterday’s enterprises tried to be more locked down. Today’s enterprises are more open, more distributed and less secure than they need to be. And I think many of you are frustrated by how much complexity has been introduced. But this new world is one where we don’t control the devices. With the expanded use of the public and private cloud, we don’t know where our data necessarily resides. With the increasing use of virtualization, it’s not always clear where a specific workload is being run. So the digital native generation brings into sharp focus 3 questions:
1. How do we manage online identities when our employees maintain dozens of them?
2. How do we protect information when the workforce shares information freely and isn’t that concerned about its security?
3. How do we keep track of a substantially higher volume of online activity?

If we can’t answer these questions, it will be a barrier to the new world of business. It won’t work. We’ll be held back by the threats we already can see today. Of course, there are some benefits to this new workplace. We’ve already seen how mobile devices and virtual desktops can enhance IT productivity. However, this starts to further stretch the already conflicting requirements on the security professional. We’re being required to offer more services and mobility, and access, while at the same time dealing with more requirements around governance and compliance, not to say all the other things we have to do from an IT perspective.
What I’d like to do at this point is I’d like to bring up a guest and say a little bit more about this topic; someone who deals with the digital native generation every day. He has a very good perspective on the future of business, and he has got a clear view of how this world is really changing. So please help me welcome Joe Sullivan, the Chief Security Officer of Facebook.
Alright, Joe deals with digital natives every day, and you’ve told me some great stories. So how do you think digital natives are going to impact business?
Joe: I think they are already impacting business every day. First, working at Facebook, we have to design our product for those digital natives. And so that means we have to understand what they want. And they want something different. We talked a little bit about how, when Facebook launched our new messaging product last year, we actually had to design it differently. We looked at how our teenagers communicate. You mentioned that the inbox is not something they look at, and we needed to get rid of the “Subject” line. When you think about that as a company, the idea that we’re going to change e-mail and take away the “Subject” line – that’s a hard thing to do. But we did it and no one noticed, because it made communication better.
Enrique: So, here’s the topic, obviously, that this group is very interested in, because if we believe that digital natives are working in the way that our own employees are starting to work, how do digital natives, in your perspective, think about security?
Joe: In terms of security for us, the digital immigrants, I could say we grew up in the Wild West of the Internet. We learned about carrying our own guns, about hiring guards when we’re on the stagecoach, about ducking when there’s a shootout in a bank. But I think the Internet’s changed, and I think expectations of the community have changed. I think at a service like Facebook we’re expected to build security into our product; we’ll be judged if we don’t. And so we need to work with companies like Symantec to bring a secure experience to everyone who uses our service.
Enrique: When you think about this notion of trying to drive a new security model, what do you think the implications are going to be in the future as these folks get into workforce?
Joe: Well, like you said, we’re seeing much more integrated experiences across devices, we’re seeing a lot more mobile. One of the guys on my team has a great interview question for new candidates. When people show up and sit down, he asks: “Use this whiteboard and draw the Internet for me”. And people respond to that question very differently. As a technical information security professional, you would draw the Internet very differently than I would as someone with a legal background. But if you take a digital immigrant and ask them to draw the Internet, it’s very different than a digital native. I wonder if in 20 years we’ll even use the term “Internet”, because we’ll be so connected all the time. So we’re seeing this dramatic evolution in definitions and expectations, and we’ve got to figure out how do we secure that identity as it moves from the mobile device to your Bluetooth in your car, to your office in a single stream of interaction.
Enrique: Makes sense. Now, before I let you go, you told me a great story the other day. You and I were talking about a local elementary school who had tried to control the whole school from being able to use chat and collaborate online; and you told me how the fourth-graders got around it.
Joe: Sure. This is a neat story. There’s a school district that thought: “We’ve got to keep these fourth-graders away from having a private chat that we’re not supervising or moderating”. Well, the kids were using a collaborative document tool, and it turns out that the default on the document tool is that there’s chat inside the document. So the kids were creating a doc called “Conversation”, and then they would all go home, and they were sitting at their computers at home telling their parents: “Yeah, I’m working on my research report”. But they were all inside the same doc having a conversation, sponsored by their school district.
Enrique: I think it really brings home the point that we’re talking about, which is: the way they work – we can’t stop it. It’s going to drive real change. You’ve given us some great examples of how this next generation think, and we need to figure out how to collaborate and work with them. So, fantastic, Joe, thank you very much. Ladies and gentlemen, Joe Sullivan, thank you!

So, as you just heard from Joe, the workplace is going to continue to change, and we need to find a way to protect identities, information and the interactions between the two of them. And we all know that there is potentially one simple approach we call “lockdown”, locking sites and blocking ports, and saying: “no personal devices”, “no mobiles allowed”. Some companies have certainly tried to go this way. But there’s a couple of big problems with this lockdown approach. First is, it slows down creativity and problem solving; your employees today are trying to use these great resources to generate solutions; they have vast networks and resources that they can use to find answers. So this notion of the lockdown environment closes off lots of these great resources. I believe that the next generation workplace will need to be wired for social, because your employees will be more productive in what we’re calling the social enterprise. We have to make sure that we take advantage of their unique perspective and make sure that we provide the tools to enable further collaboration.
The second problem with lockdown is that it’s not fault-proof. People are finding workarounds today. Your employees are storing company files in places like Dropbox because it’s quicker and easier; or they’re consulting Twitter to figure out how to solve a business problem.
If we want real protection, we have to let go of the lockdown mentality, and we have to think about this notion of what we’re calling “wired for security”. Now let me talk a little bit about how this works. As we look at what the digital natives are doing, they’re creating a lot of complexity. And so our current security model on its own will not get the job done. We need something new, we need to rethink how do we secure the enterprise. More than just bigger and stronger protection, we need to stop being the people that say “No”, and partner with our user communities. We need an entirely new layer of security, as connected and as mobile as your workforce, that allows us to maintain strong governance, compliance and control without impeding good work.

We need a layer of protection that is wired for social and wired for security. But it’s one thing to say “wired for social” and “wired for security”. But the question is: how do we make it happen? How do we make it possible? I think we need to start by defining it. What we’re going to need to do is deliver authentication, authorization and auditing, but in a new way. This new layer of protection will have to have a very sharp focus on a few things.

The first thing you’re going to need is very flexible identity management. It will have to be built on an expanded definition of identity established through credentials, through device, through geo and policy – as close to a single sign-on as possible, with access control and user management across all cloud-based services, including your employees, your business partners and your customers. It will need to handle all forms of sign-on that are being used every day. It will need to be able to de-provision users when they leave your organization – not just their accounts, but also remove the information that they were accessing. It will have to work with our existing identity management solutions. This new layer of protection requires a new kind of information security, an access control point, a new place to control where information leaves and comes into your enterprise. It will be a software gateway that recognizes identity and has an understanding of every piece of information that goes in and out of your enterprise.

And that’s what’s key here. We’ll need a new notion of the old firewall. We need a reverse firewall to keep critical information in. It has to be able to watch the outbound flow of data. And that means this notion of “bring your own device” isn’t really about the device. It’s about how you organize and categorize information. It has to watch outbound flow of traffic, and it needs to look at it file by file, with more than just a binary “yes or no” control. It’ll need to be content aware, it’ll need to be intuitive and policy-based, with the ability to block when necessary, but also to encrypt without getting in the way of what your users are trying to do. And this new approach will also require complete auditing; full visibility into the flow of information between individuals in one company and another. It needs policy enforcement, clear definition of management, and it needs to work ubiquitously. It has to keep track of who is accessing what, to what level, with what device, depending on where they are and who they are. It has to record all access and information security events, monitoring the interactions between people and information, creating a cloud audit trail, giving you consistent visibility across internal and external IT resources.
Now, you and I both know what I just described is not an easy task. We’ve been talking a lot with our customers about how to do this, what’s worked and what hasn’t. And one of the things they continuously bring up is that we have to reduce the administrative burden to make this possible. We can’t depend on the end users tagging the information. So we need a broader set of policy. We need a system that can learn and adjust. It needs to be transparent, but always active, so that you always know what info you have and where it’s going.

But the approach I’ve outlined is critical, but it’s not the only thing we need to do. Why is that? Because with this new generation come new vulnerabilities. We’ve seen every time there’s a new technological advance, it has brought an associated number of exploits. We know about Brain and Code Red and SQL Slammer, even Stuxnet which I talked about last year. The approach I’ve just outlined will not be enough, because advanced persistent threats have become more targeted. And this new generation assumes that the connected world is safe. They place so much information online that we must change how we protect identities, information and interactions.

To protect against advanced persistent threats, we need advanced persistent protection. And advanced persistent protection is not a product. It’s a mindset, it’s an approach. It’s built around 4 key things:
1. You need a reliable early warning system that allows you to understand when a new threat is potentially going to attack.
2. You need state-of-the-art protection, one that recognizes threats without impacting your users.
3. You need fast remediation – solutions that can move faster than the threat can spread across your company.
4. You need a response plan. Now, this can be an internal plan, but it has to also include outside resources, including law enforcement, because at times they will be required to help with the ultimate solution.
This is our vision for security, and it’s new, it revolves around this new workplace that I’m describing. But what we need is a new secure ecosystem. We’ve been working with multiple partners, including carriers and manufacturers to make this new approach a reality. We’ve been working with VMware, as virtualization is key component of building a lot of these cloud-based systems. And we’re working with them to deliver better security. As an industry, we need to establish security practices around the cloud. We need standard APIs that will allow us to work across all of the different cloud-based services. Today we have interfaces like SAML, OAuth and OpenID. We must go further. What I’d like to do now is I’d like to introduce another guest who can speak about the importance of security in the cloud. So please help me welcome Marc Benioff, CEO of salesforce.com.
 Mark: Good morning everybody.
Mark: Good morning everybody.
Enrique: So, Mark, one of the things that you said is there’s been a barrier to the adoption of cloud-based services of security. Tell me more about that.
Mark: Well, I think everyone in this room knows that when you’re a cloud provider like salesforce.com, trust is our number 1 value. Nothing is more important than the trust that we have with our customers. And a critical part of that trust is the security infrastructure.
Enrique: So, Marc, I’ve been talking about this new enterprise, and I talked about digital natives and how they work. They don’t use e-mail the way we have historically; they collaborate more in a social way. So tell me more about what you think, how does the social enterprise impact business going forward?
Mark: Well, you’re right; we are going through a massive transformation in our industry, and that transformation is this move to the world being more cloud, but also being a lot more mobile and a lot more social. And to me what social means, and you and I have talked about it many times, is that everything is going a lot faster, you just see that events happen and things spread, and consciousness happens rapidly. And things are also a lot more open, more transparent, things are more collaborative. Individuals who maybe didn’t have a platform for empowerment and excitement are getting elevated. And alignment has achieved the levels that we have not seen. You see that in the Occupy movement, where they’re able to coordinate their activities through the social paradigm, and not just leaders, you know, like we have in this room, but also leaderless organizations like Anonymous and Occupy and others, who are empowered and enabled and get created through the social paradigm. And the power of all that together, which I call “SOCIAL”, which is speed, open, collaborative, individuals, alignment and leaders (I need something to build to remember it) is transformational. It’s transformational to exactly what we were talking about – the youth and society; but it’s transformational in our businesses, with the social enterprise. Our companies have to learn now how to become new kinds of organizations, because we have these incredible new tools.
Enrique: So, Marc you and I are both passionate about this new way of working. So how do you balance security and social? Because I’m going to want to put out a lot of information, using corresponding tools; how do you think about balancing security with social?
Mark: Well, the two things that I constantly focus on are trust, which is a different way of doing business, you know, it’s a level of openness and partnership with your users and your customers, that everyone in the organization has to get to a higher level of; and transparency. Everything that happens has to be an open book, no secrets. And that’s the critical part of trust. It’s the yin and yang; they have a symbiotic relationship. There is no finish line when it comes to security, we all know that. Everyone here in this room knows that, you know, we’re holding it all together, but that it’s all a highly dynamic and rapidly changing environment, and that we have to pull it all back together again. And because there is no finish line with security, trust is ultimately the most important thing. That’s my perspective.
Enrique: And I think that makes a lot of sense. So, Marc, we’re already collaborating on solutions together to help secure the cloud and secure a lot of services, so I look forward to continuing to work with you.
Mark: Thanks for having me at the Keynote. Enjoy the conference.
Enrique: So, as we just talked, this new generation of workers, the digital natives, are dramatically changing how we work. So make no mistake about it. They are the sledgehammer of change. And together with the digital immigrants, you and me, we have to look at how we work inside this fundamentally different workplace. This new world cannot be a choice between social versus secure; it has to be both. It has to be wired for social and wired for security. We’ll protect this new enterprise; we’ll provide a pervasive security model, one that protects identities, information and interactions. And we’ll provide advanced persistent protection across devices and across the cloud – because the future is clear; because the future is already here, and because the only way we will secure that future is to embrace it, to enable it, to protect it and to extend it. Thank you very much.




























