Home 2016
Yearly Archives: 2016
Remove OSIRIS ransomware and decrypt .osiris extension files
A brand-new iteration of the deleterious Locky ransomware is out. Expert reports about the update started to appear on December 5, which is almost...
Bitdefender 2017 Black Friday Up to 60% off
Privacy-PC is officially opening the Christmas shopping season with a fantastic deal. With the featured promotion in store for our esteemed visitors, Black Friday...
5 Reasons to Use a VPN Service
There are so many benefits to using a VPN service when browsing the Internet, it shocks me that so many people do without. If...
Remove Thor ransomware and decrypt .thor extension files
As the recent Thor ransomware release has demonstrated, the threat actors in charge are adding a fair degree of incoherence to the average time...
Recuva review: Piriform Recuva Free&Professional download
Recuva, a lightweight freeware applet by Piriform, is one of the world’s most effective solutions aimed at reviving deleted data. The usefulness of file...
HitmanPro Alert 3.5 with CryptoGuard review
While the world’s largest antimalware labs are at their wit’s end trying to contrive a solution that would efficiently combat crypto ransomware, the Dutch...
The New Scourge of Ransomware: A Study of CryptoLocker and Its Friends
Security experts Lance James and John Bambenek tell the Black Hat USA audience how they got together on the CryptoLocker ransomware case and how...
Cerber ransomware: virus removal and file recovery
Cybercriminals keep on devising intricate instruments in pursuit of a more efficient online extortion. Compared to the myriads of crypto ransomware floating around the...
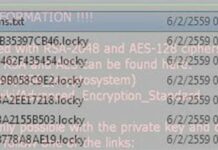
Locky ransomware: virus removal and decryption advice
The victims of ransom Trojans incur a great deal of damage because the thing at stake is their personal data. The indicators of compromise...
Zepto extension virus: files restoration and ransomware removal
Crypto ransomware programs come and go, but the idea of online extortion stays and perseveres with its progress. Having vanished from the antimalware radars...