Specops Password Policy is an amazingly flexible toolkit that hardens your organization’s authentication practices to minimize the risk of compromise.
It’s common knowledge that threat actors think of enterprises as juicy targets and prioritize these types of incursions over spray-and-pray campaigns that zero in on individuals. Unsurprisingly, businesses are on the receiving end of cyberattacks that run the gamut from phishing frauds and intellectual property theft, to ransomware-borne extortion and supply chain exploitation. In this paradigm, ensuring secure access to corporate digital resources is paramount.
Let’s face it, the human factor is arguably the weakest link in the average org’s security posture. Employees are prone to error and have pain points that can be piggybacked by crooks, with poor sign-in hygiene setting most cyber incidents in motion. That said, the precautions to avoid such foul play traditionally boil down to stepping up password-related practices, and this is the area where Specops Password Policy claims to yield tangible positive results.
Specops Password Policy at a glance
I’ve heard a lot of good stuff about this long-standing software and finally got a hands-on chance to zoom into what’s under its hood. Geared toward specifying and applying password rules for Active Directory users and groups, it additionally gives you visibility across your entire IT territory authentication-wise.
Microsoft’s default password policy features for Active Directory are warmly received by network admins, but there’s always room for improvement. I’ll fast forward a bit here and emphasize that Specops Password Policy delivers more intuitive controls, provides more robust layers of protection against weak and compromised credentials, and enables a more granular style of handling passwords.
Here are a few extra features that I believe make Specops Password Policy stand out:
- Readily available password policy templates for hassle-free regulatory compliance
- Passphrase support
- Real-time dynamic feedback accompanying password change events
- User-friendly administration console
- Password entropy scores
- End-user messaging options
- Support for 25+ languages
In this review, I will describe the ins and outs of installing this product’s components, configuring them, and creating a new password policy that meets industry standards. I will also illustrate how the software responds to scenarios involving noncompliant passwords so that you get the bigger picture. But first, let’s go over the prerequisites for deploying this toolkit in your environment.
System requirements
Administration tools:
- Windows 10 or newer
- .NET Framework 4.7.1 or newer
- Active Directory Users and Computers (ADUC) snap-in
- Group Policy Management Console (GPMC)
- Windows PowerShell 5.1
Specops Password Policy Sentinel:
- Windows Server 2012 R2 (Release 2) or newer
- .NET Framework 4.7.1 or newer
- Writable domain controller
Specops Authentication Client:
- Windows 10/11 x64 systems supported (Windows Server 2016 or newer required when running on a server)
- .NET Framework 4.7.1 SP1 or newer
Specops Arbiter:
- .NET Framework 4.7.1 or newer
- Windows Server 2012 R2 or newer
Getting started
The installation of Specops Password Policy is a multi-step process that involves setting up several key components of the software. What makes the workflow seamless is the setup assistant that combines all the required elements under the same umbrella, namely the Administration Tools, Specops Arbiter, Domain Controller Sentinel, and Specops Authentication Client.
The setup assistant is a lightweight download of only 14.8 MB. The default path it goes into is the Temp directory on the machine – I had no issues keeping it that way.
Version 7.7 was the latest one when I was initially installing the product for testing, but a few days later the publisher rolled out an update to v7.8 that comes with a few enhancements and GUI tweaks. I will be illustrating the updated Specops Password Policy Domain Administration controls further down, and where appropriate, you will see the differences between the two.
Circling back to the setup, you need to select the self-explanatory Start Installation option to proceed, or if you are a scrupulous admin (which is a commendable hallmark), familiarize yourself with various aspects of the product by clicking “Read More” first.
This stage is followed by a garden-variety EULA window where you can peruse the technicalities and legal aspects of the product if you so desire. Click Accept to continue.
Installing Specops Password Policy components
Once you have completed the preliminary customizations and expressed consent with the terms and conditions, you will see an interface that streamlines the installation of the software’s four main modules. Let’s go over the nuances of getting each one of these elements up and running.
1. Specops Administration Tools
Aiming to manage a series of important domain-wide configurations, this is the pillar of the product’s usability.
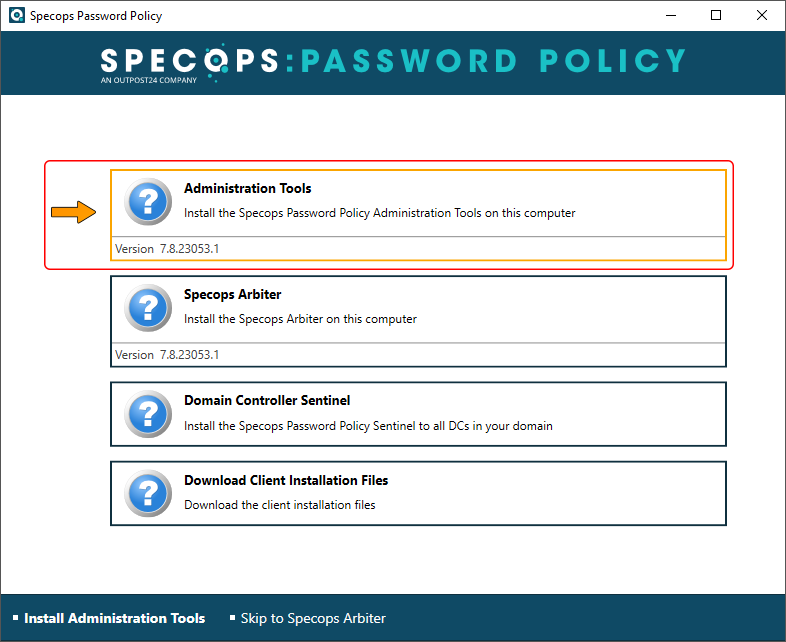
Once selected, the Administration Tools box triggers a window that lists the required conditions and displays green checkmarks next to the ones your environment meets. To enable the feature that adds Specops options to the standard context menu for ADUC snap-in, click Add menu ext.
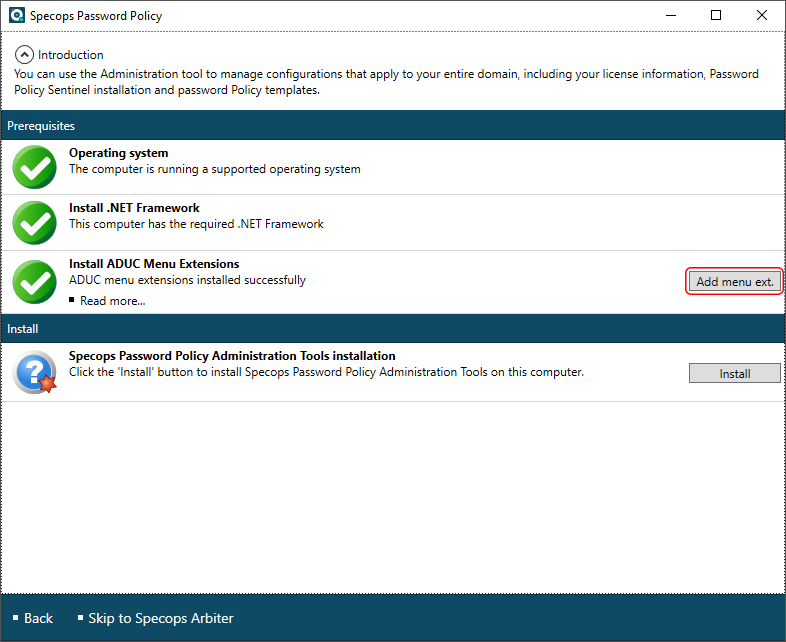
Proceed by clicking the Install button to install Admin Tools on your machine. Wait for the process to finish.
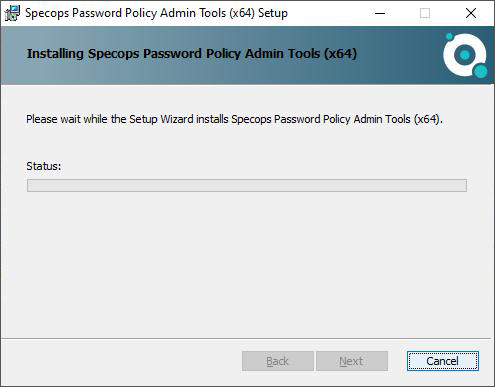
The software then displays a confirmation that all constituents of the Admin Tools have been installed and are all set to come into effect. Click OK.
2. Specops Arbiter
From where I stand, the experience with an enterprise-grade password management solution is half-baked unless it’s enhanced by a regularly updated database of leaked credentials.
In the Specops ecosystem, this extra layer of security is delivered by a feature called Breached Password Protection. If you are planning to leverage it down the line, then go ahead and install the Specops Arbiter component.
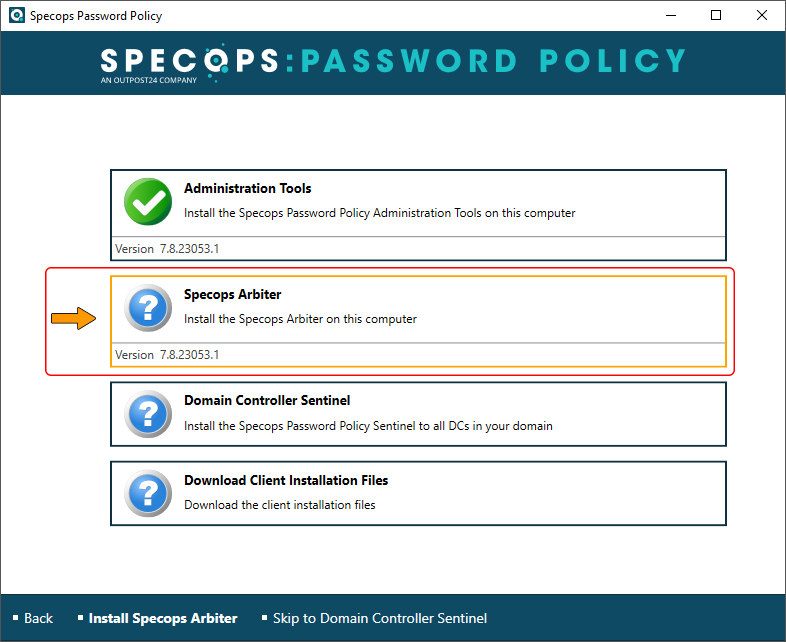
Once you click the corresponding setup assistant option, you will see a screen that tells you whether you are using a supported Windows Server version and the required .NET Framework build. If there are no question marks on the checklist, click the Install button.
Thankfully, the installation only takes about a minute (you will see a progress bar to keep abreast of the routine).
Click OK on the pop-up that signals a successful installation.
3. Domain Controller Sentinel
This module stays on top of the scenarios where a user is trying to change their password and verifies if the new secret combination complies with the corporate password policy’s criteria.
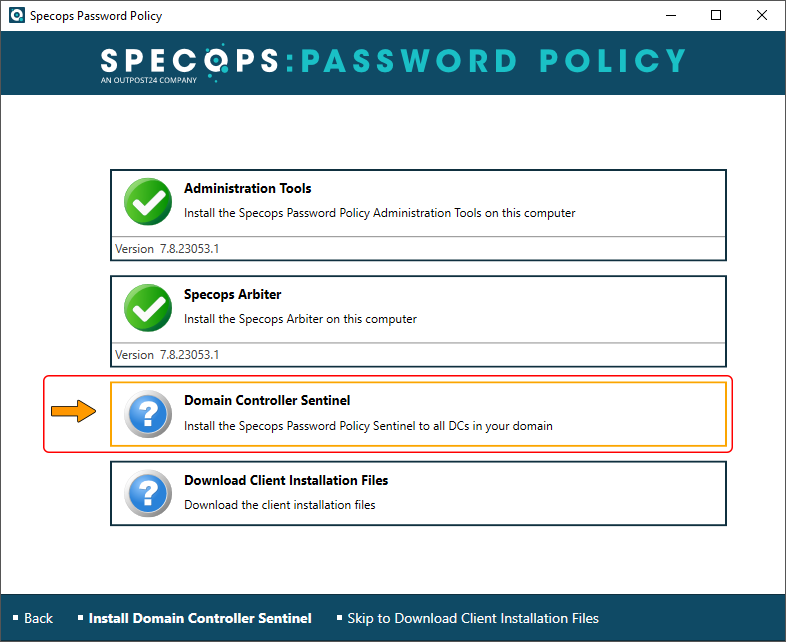
On the follow-up screen, put a checkmark next to the domain controller (DC) you want to be supervised. Since the use of noncompliant passwords is a serious matter, installing the Sentinel on every writable DC within your domain is strongly advised.
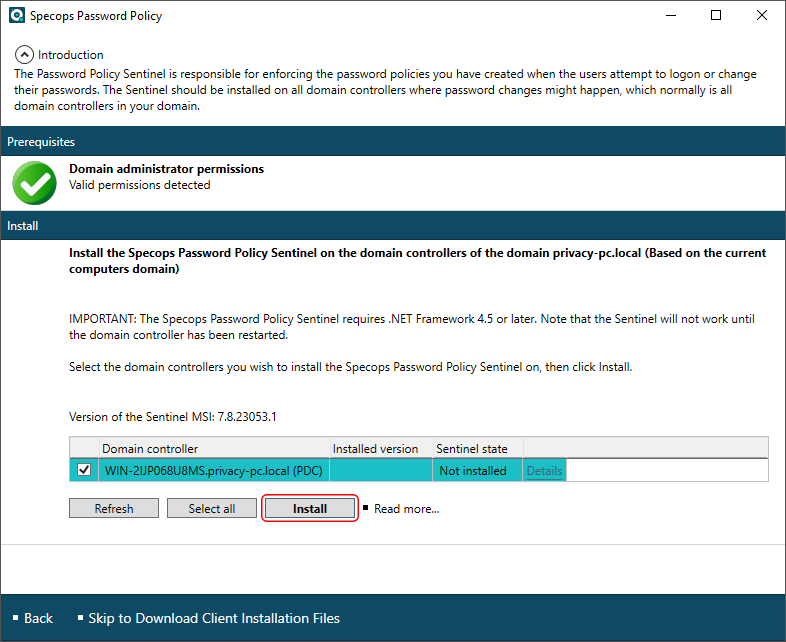
Select the right domain controller and click Install. You will now see the following dialog:
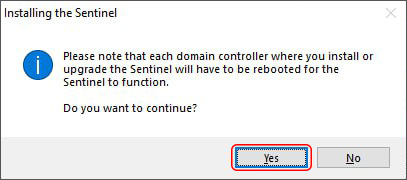
Click Yes and wait until the installation is completed. The only thing left to do is reboot the DC, after which you will see Ok under Sentinel state.
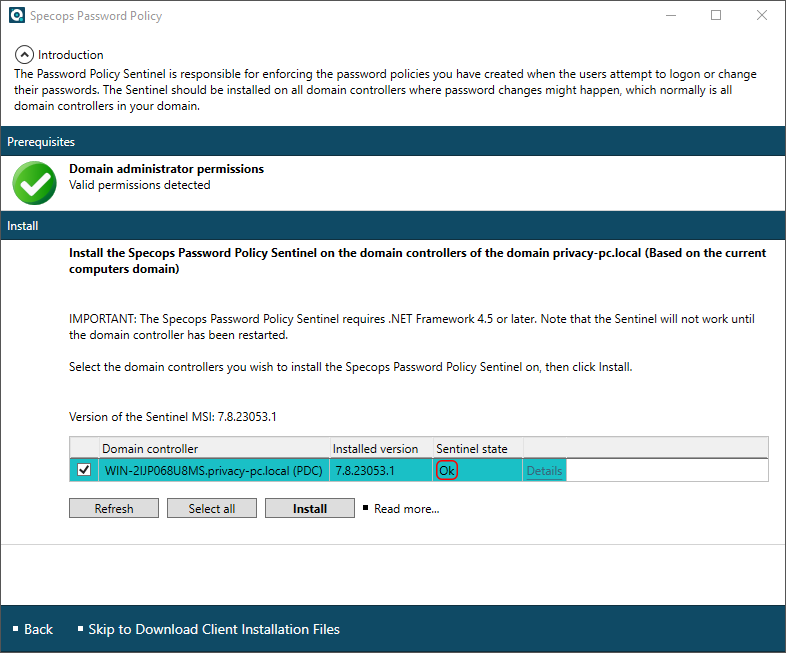
4. Specops Authentication Client
This component gives password hygiene a boost across your organization’s environment. It is supposed to be installed on client machines and plays a significant role in achieving proper user interaction as your team members create new passwords or change their existing ones.
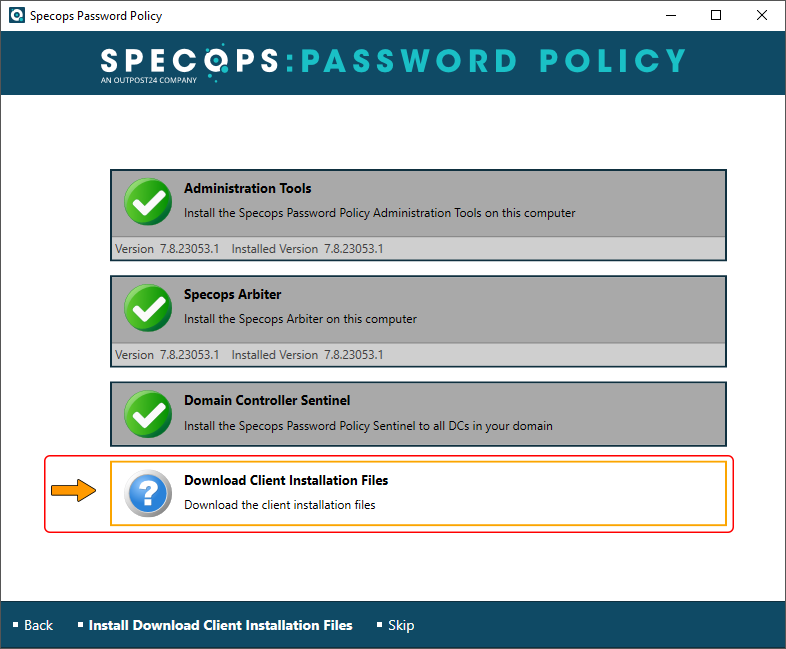
Installing this module is a breeze. Just follow the amazingly intuitive installation prompts to complete the procedure.
Click through the following slideshow for illustrations:
Activating the fully functional version
To be able to use the whole spectrum of Specops Password Policy’s features, you need to import a valid product license. Open the Start menu on your machine and select Password Policy Domain Administration.
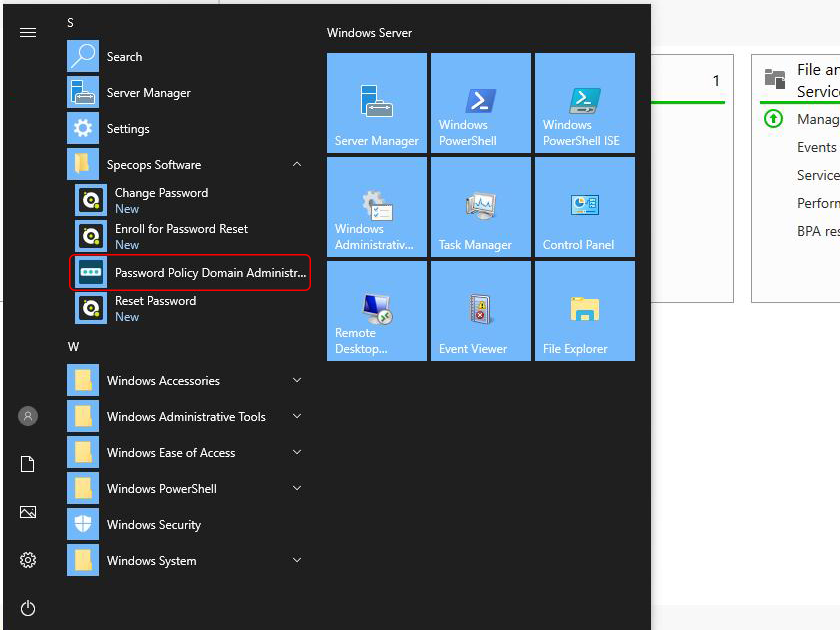
The console displays a Disabled status and a license error from the get-go. Here is what you should do to change this. First, close the alert and click Import license file.
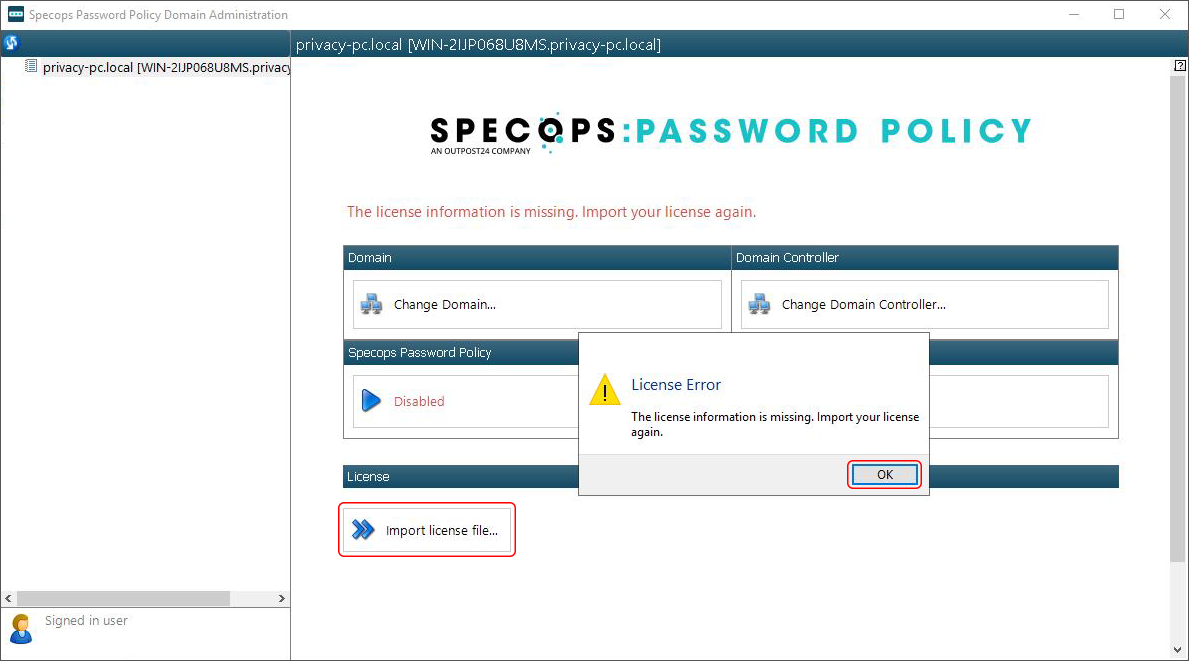
Then, use File Explorer to browse to the Json license file obtained from Specops. Select it and click Open.
That’s it! The status of the software has now been changed to Enabled, and you’ll also see the full list of the available features appear in the sidebar.
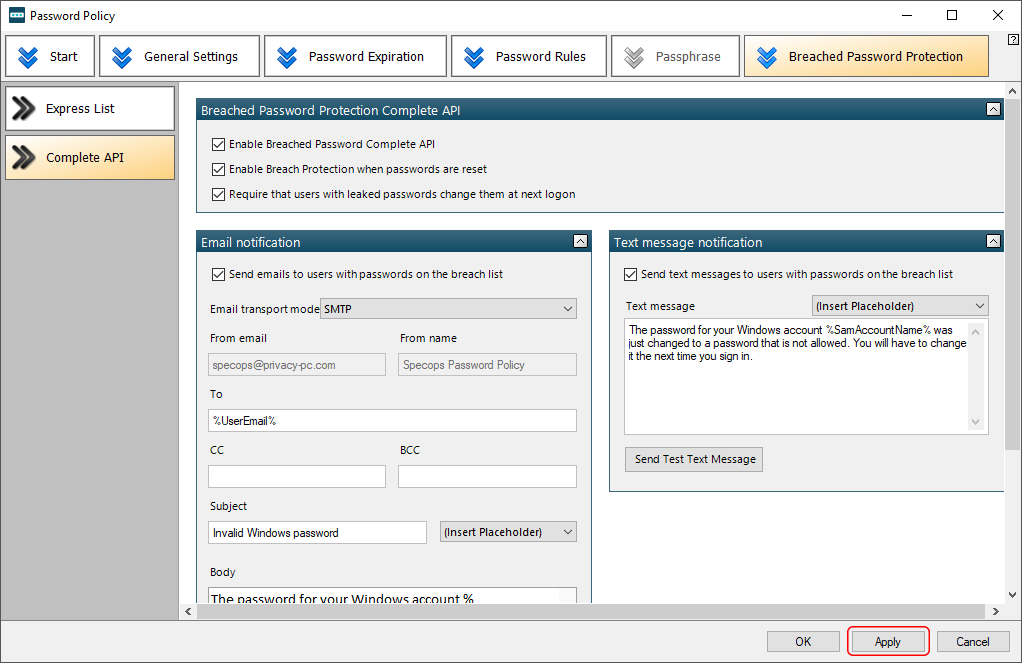
Turning on Breached Password Protection
To make sure nobody on your network slips up by specifying known-leaked authentication data, it’s in your best interest to enable the Breached Password Protection feature. It checks passwords against a huge database of compromised credentials so that your users stay in the clear.
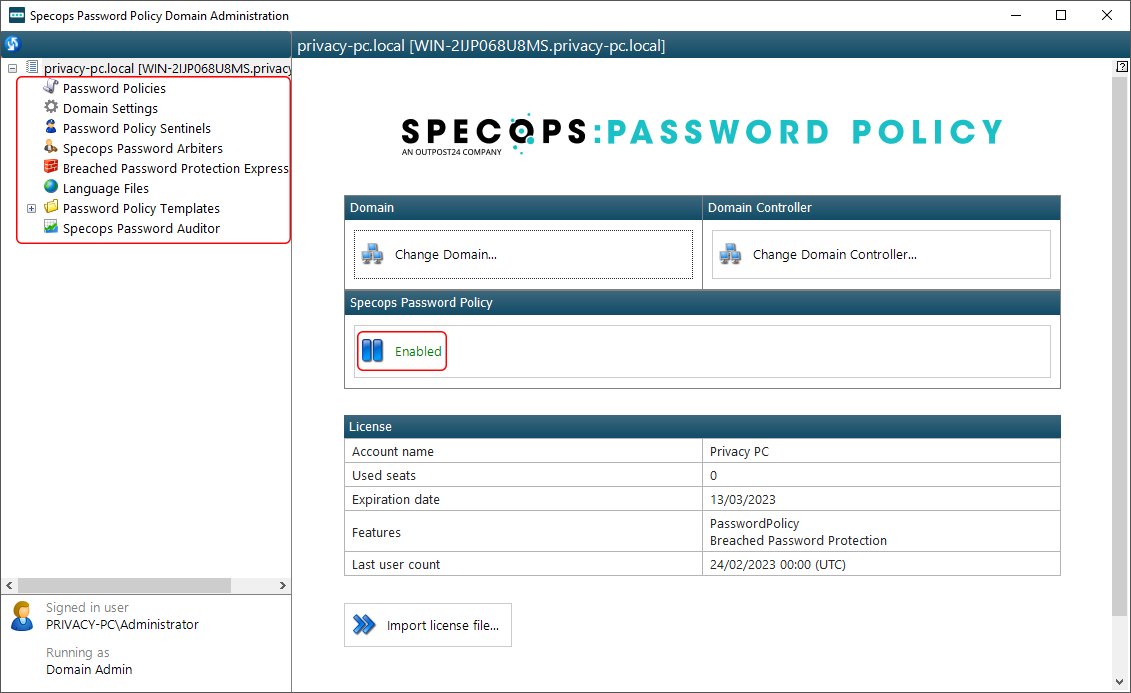
1. Registering new Arbiter
To benefit from this remarkable functionality, first you’ll need to enroll an Arbiter MSI on your server. Go ahead and select Specops Password Arbiters in the main menu and click the Register new Arbiter button.
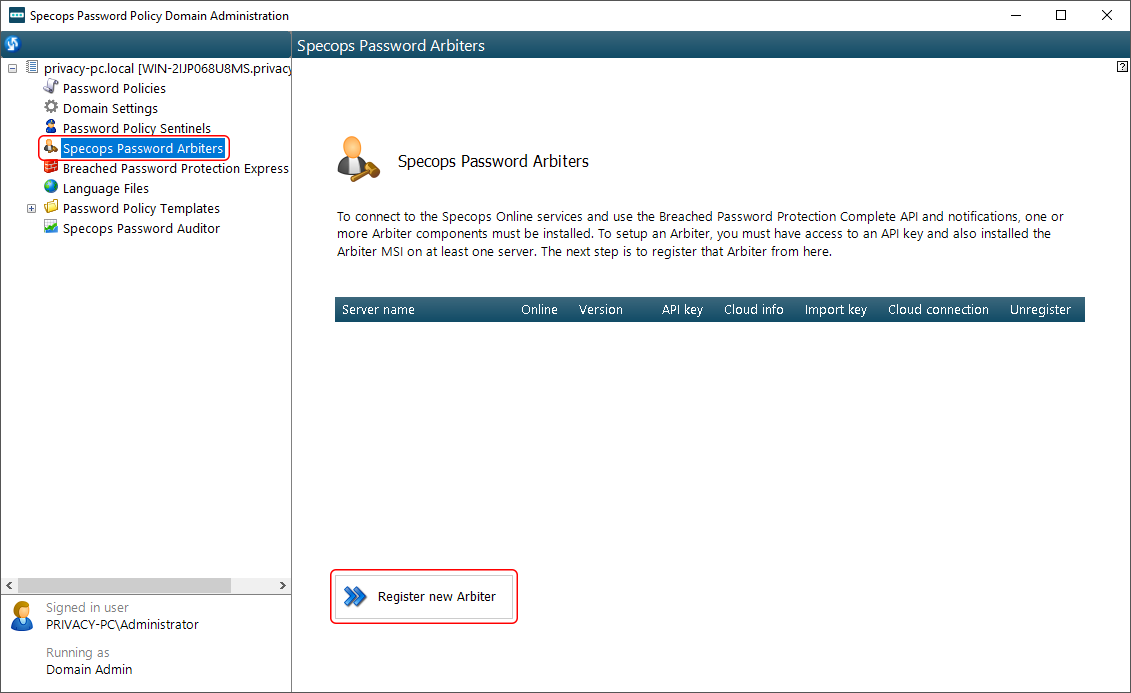
In the next window, type the name of the computer that will be performing Arbiter functions and click OK.
Once the just-added Arbiter appears in the “Server name” field, click Import API key if you have already received the key from Specops.
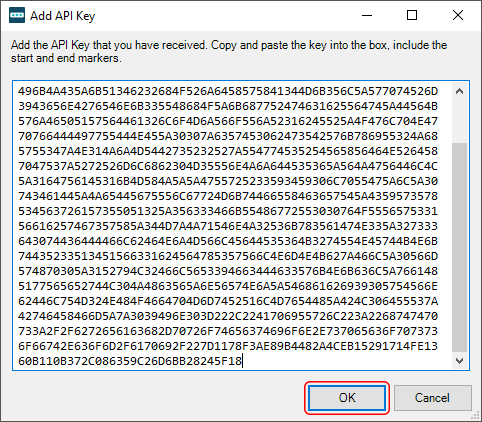
Locate the text file that contains the key on your computer. Open it with Notepad or another text editor at hand. Copy your unique key (importantly, you should omit the “— BEGIN API KEY —” and “— END API KEY —” strings) and paste it in the Add API Key window as shown below. Click OK.
You will now see a green checkmark for the API key field, which means the feature has been successfully activated.
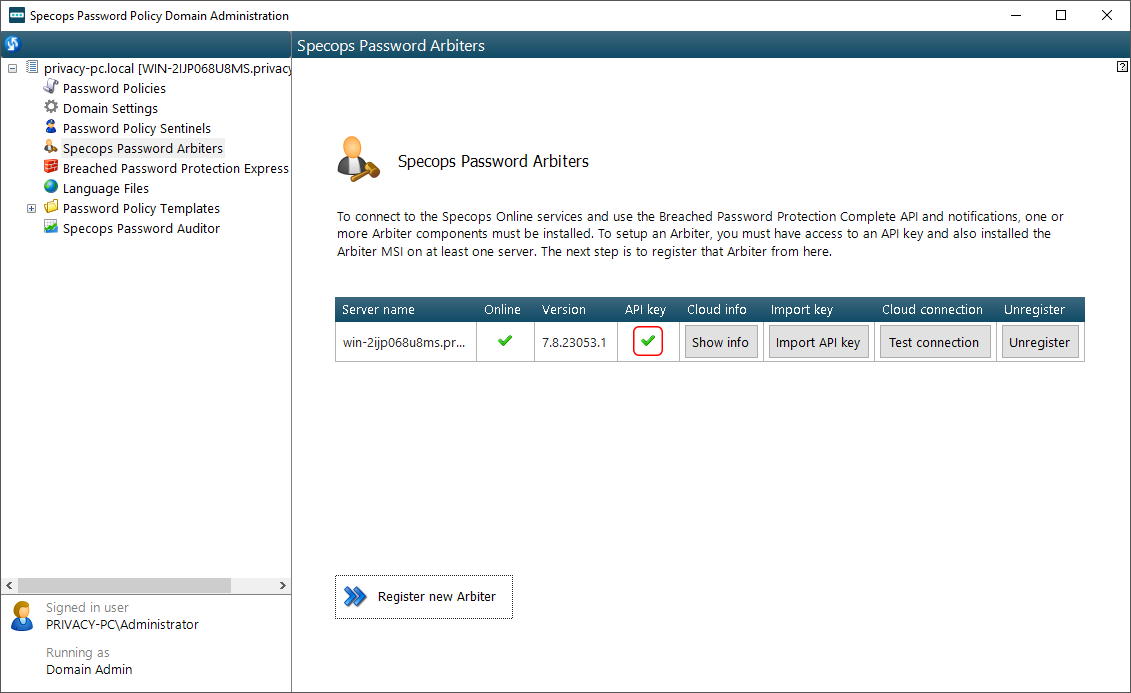
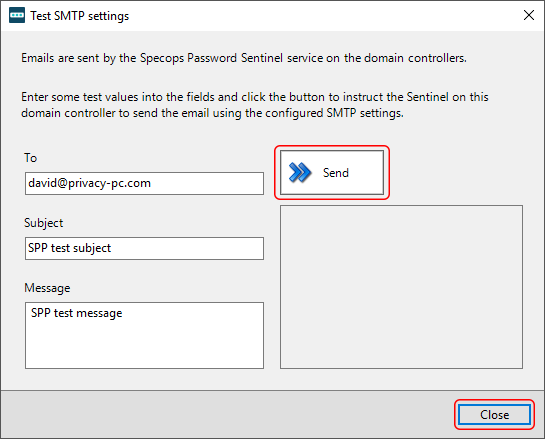
At this point, you can also click the Test connection button to check if the Arbiter can reach the Breach Protection API. The following pop-up indicates that the process went well.
2. Downloading the Breached Password Express list
To stretch the potential of this feature, it makes sense to additionally download the latest version of the leaked passwords database onto your server.
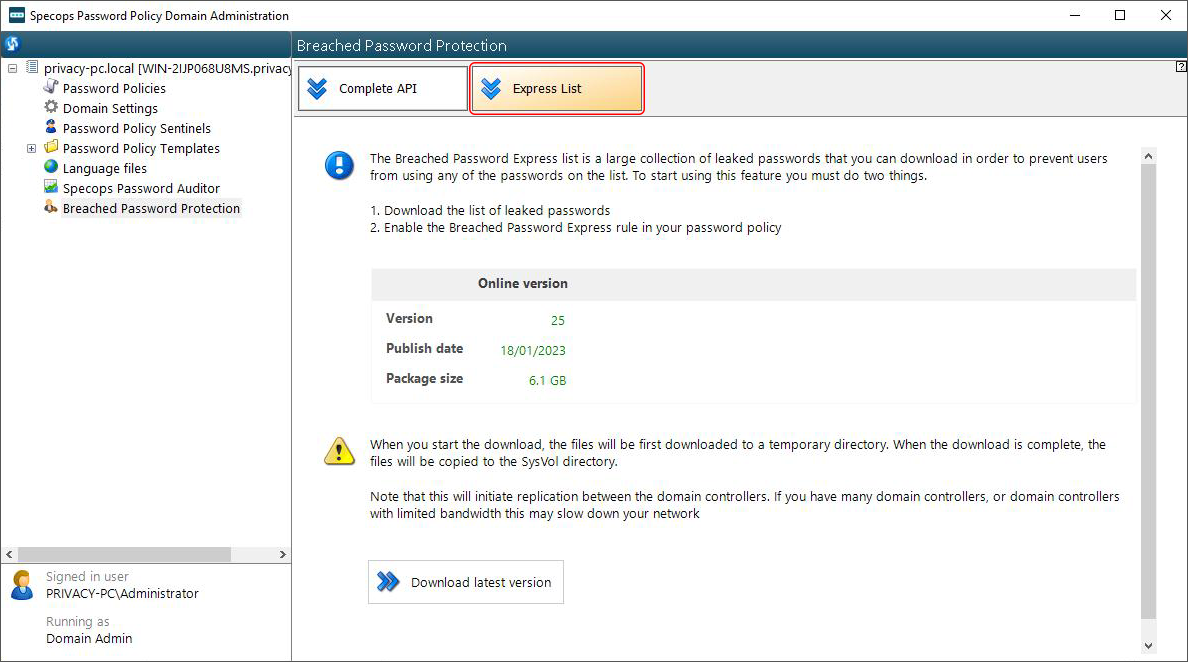
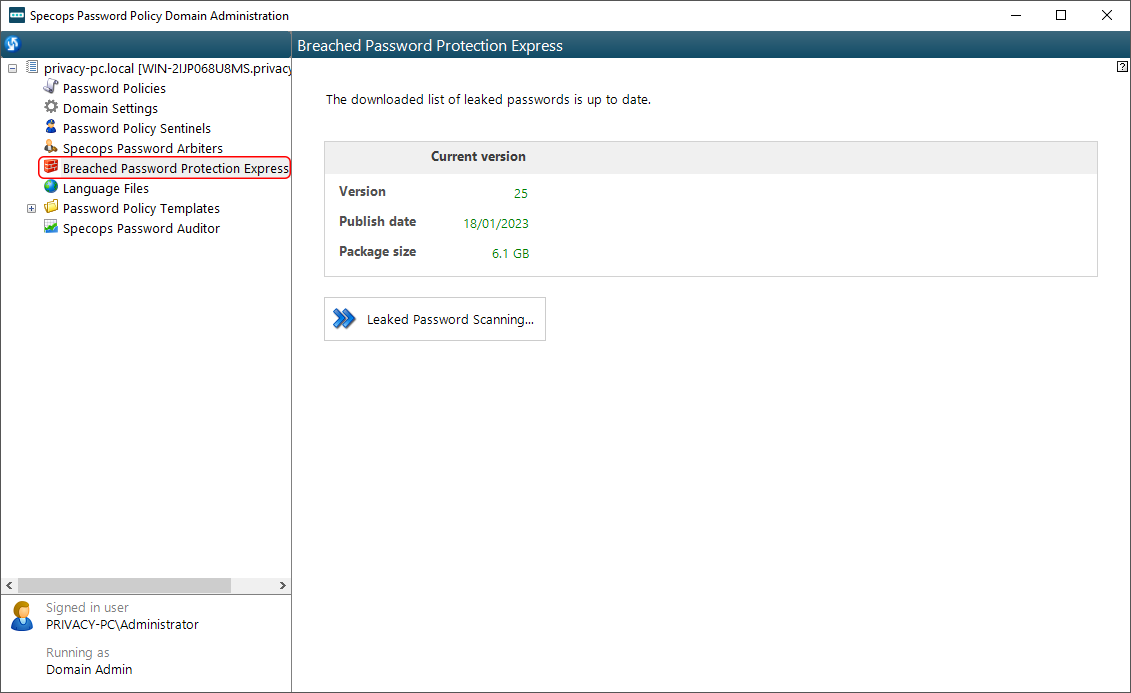
In Specops Password Policy v7.7, this option resides under the Breached Password Protection section’s Express List tab. In the newer version 7.8, it got a separate spot in the main sidebar menu named Breached Password Protection Express. The following two images reflect the previous and new console variants.
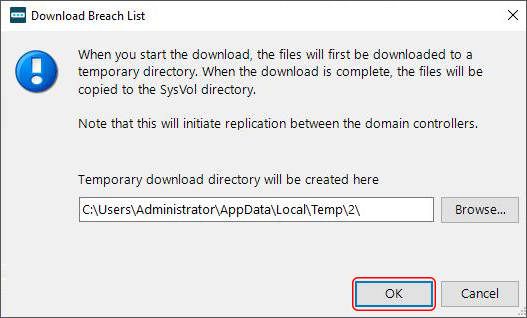
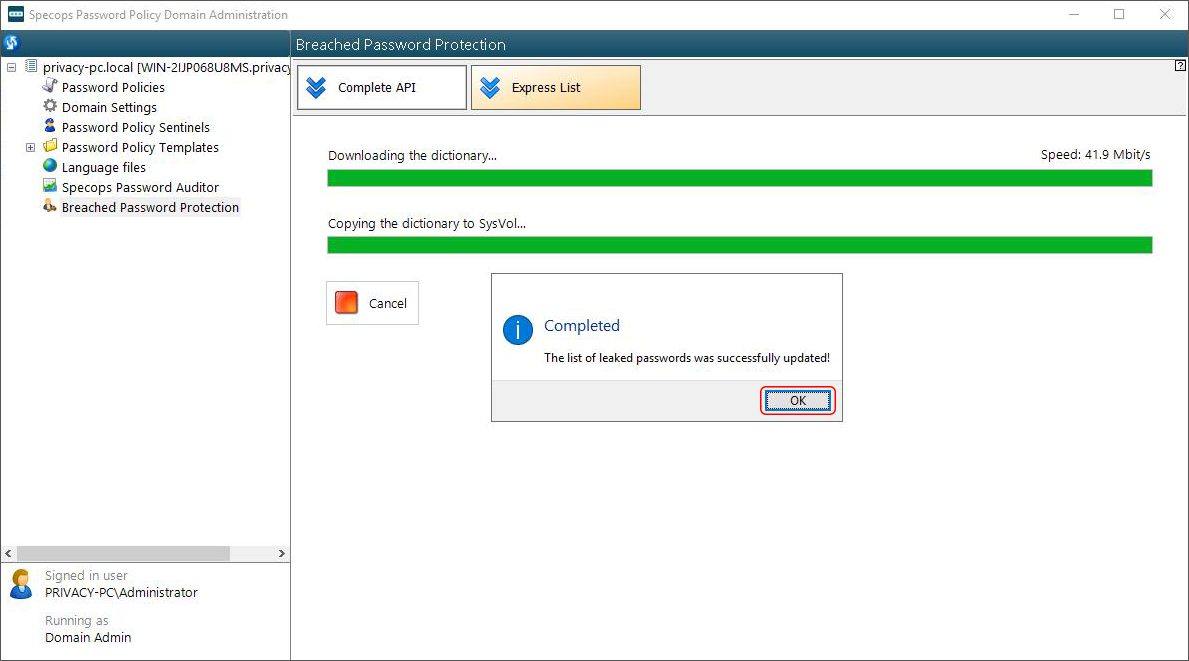
Click Download latest version and follow further prompts to complete the process. On a side note, the list is several gigabytes large. Moreover, once it’s downloaded to a temporary location, a copy will also appear in the SysVol directory. So make sure you have enough free disk space to proceed.
Click through the following slideshow for illustrations:
Specifying mail server settings for notifications
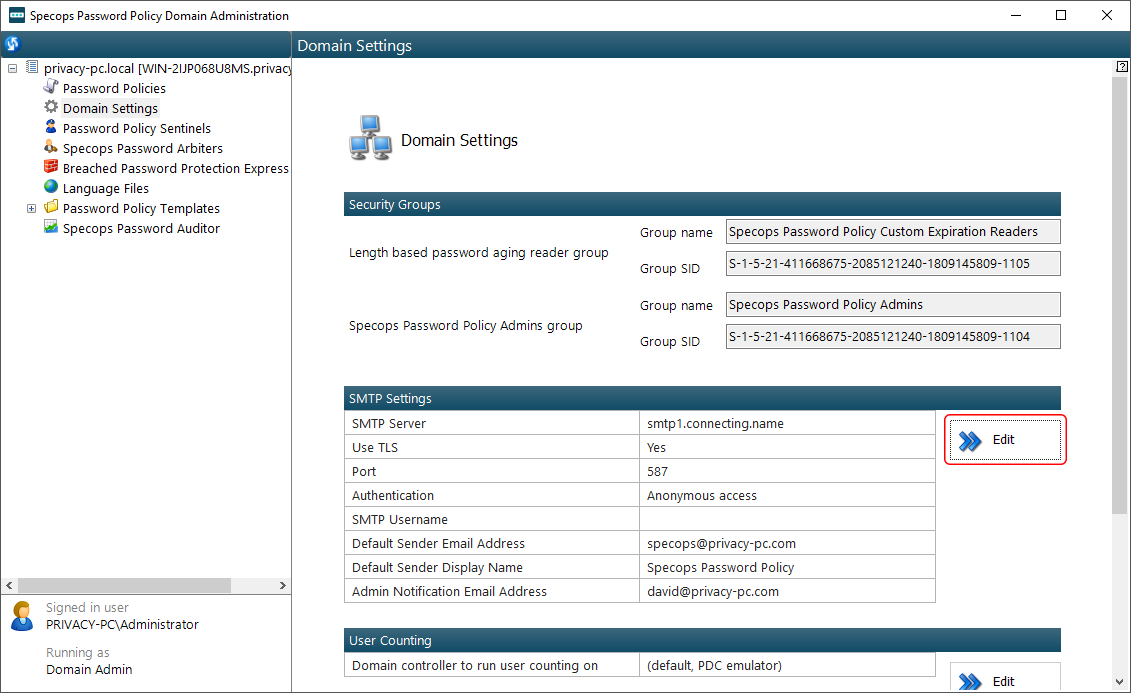
To bolster user-initiated password workflows with email notifications going forward, you can have Specops Password Policy send relevant messages to employees in these situations. If this is something you want to enable, go to Domain Settings, find the SMTP Settings area, and click Edit.
Click through the following slideshow for illustrations:
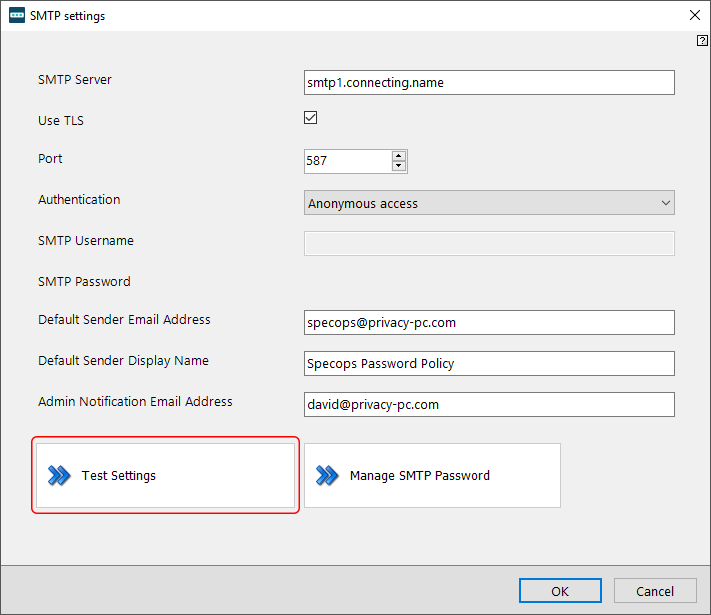
Next, enter your mail server configurations and fill out the additional fields, such as the default sender email address, display name, and admin email address. I recommend clicking the Test Settings button when you are done. This will allow you to send a test email to check if the values you entered are correct and the feature works as intended.
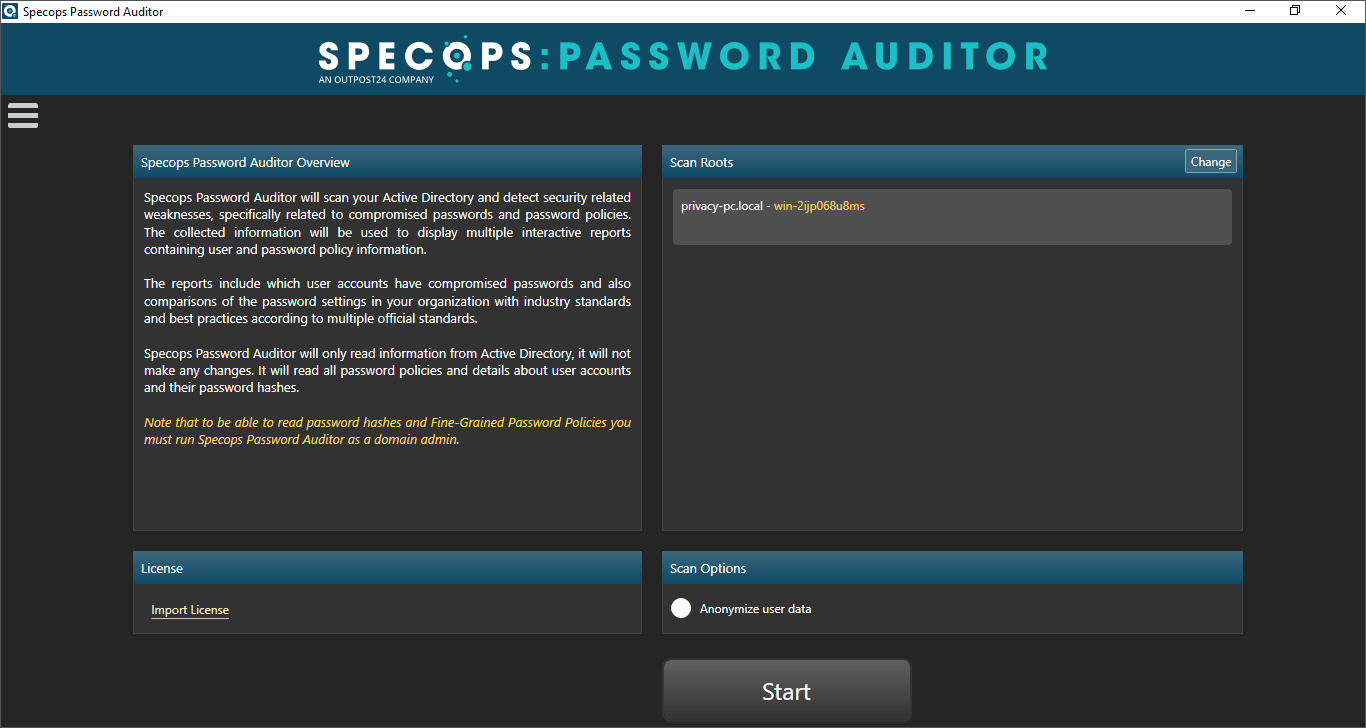
Specops Password Auditor
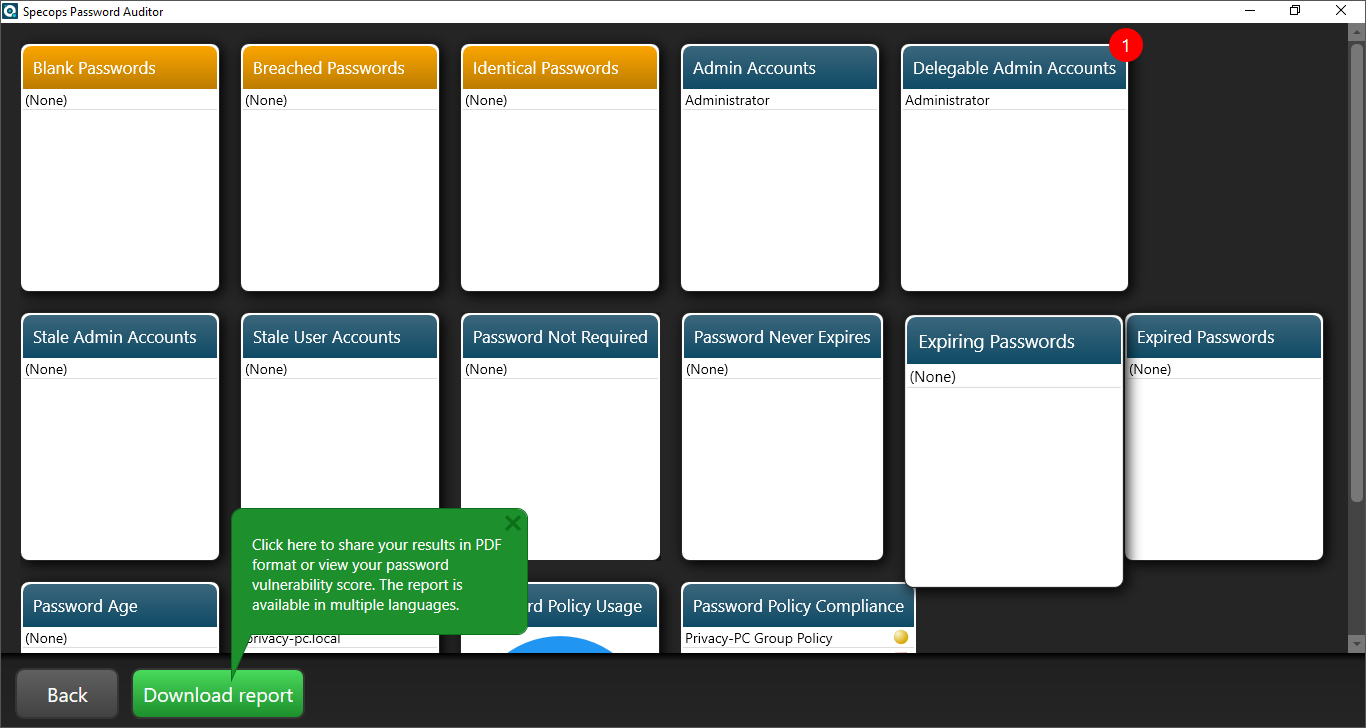
A tool that’s worth a separate mention is the Password Auditor. In addition to complementing Specops Password Policy’s built-in feature set (see image below), it is also available as a standalone free download with no strings attached.
You can use this instrument to scan your Active Directory for nearly 1 billion leaked passwords and pinpoint other vulnerabilities related to authentication workflows within your ecosystem. The scan report is easy to interpret and can be downloaded as executive summary in PDF format for further reference.
Click through the following slideshow for illustrations:
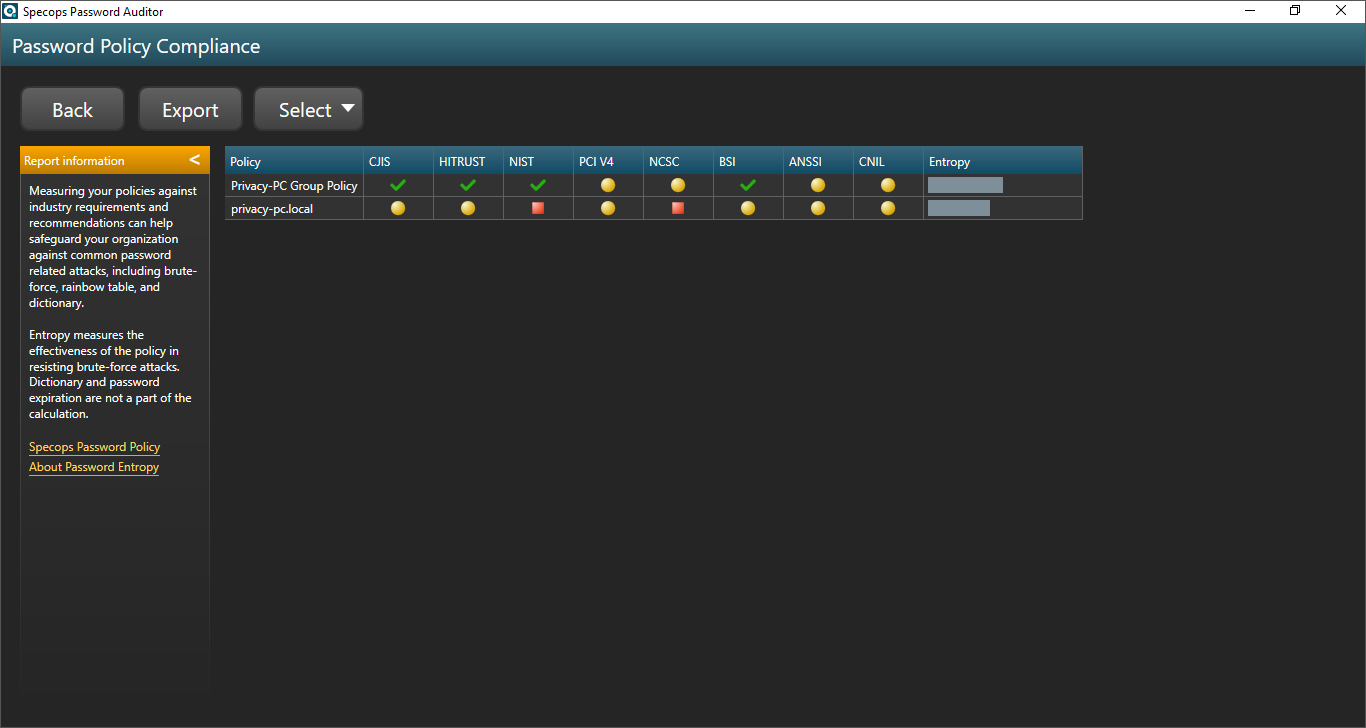
One of the benefits of using Specops Password Auditor lies in the zone of regulatory compliance. The scan results give you actionable insights into the areas that require enhancements so that your organization’s password hygiene meets industry criteria.
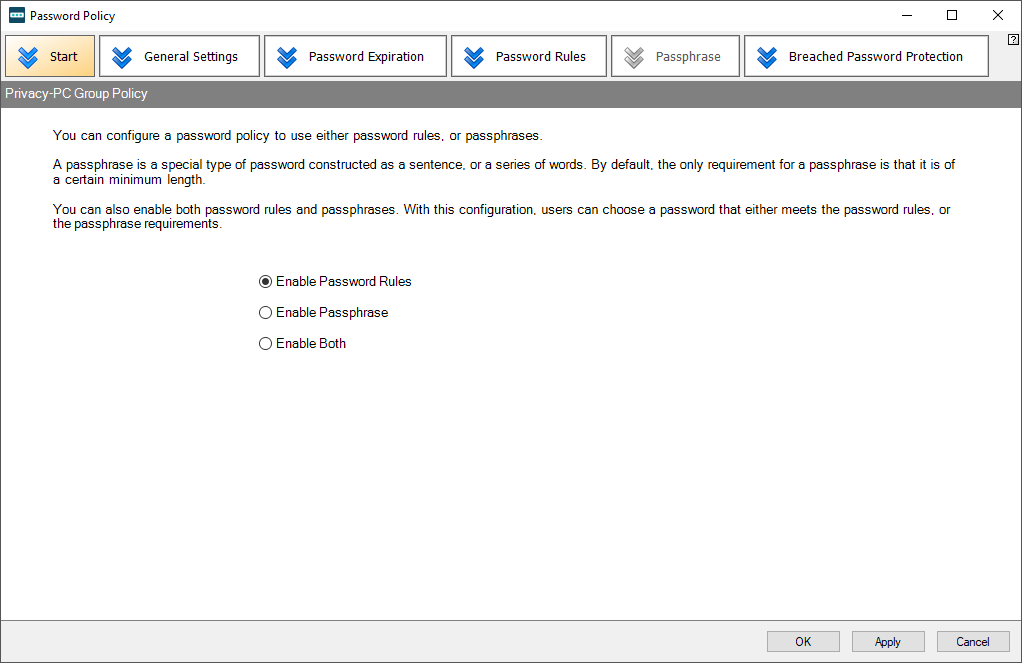
Create a password policy of your own
Now that the installation has been completed and all preliminary customizations are in place, let’s look into the nuts and bolts of adding a new custom password policy that fits your org’s security philosophy.
Click Password Policies in the Domain Administration GUI’s sidebar. You will see the Default Domain Policy already available, but I’d recommend you take it up a notch and create your own with a higher entropy score. Go ahead and click the Create new Password Policy button to get started.
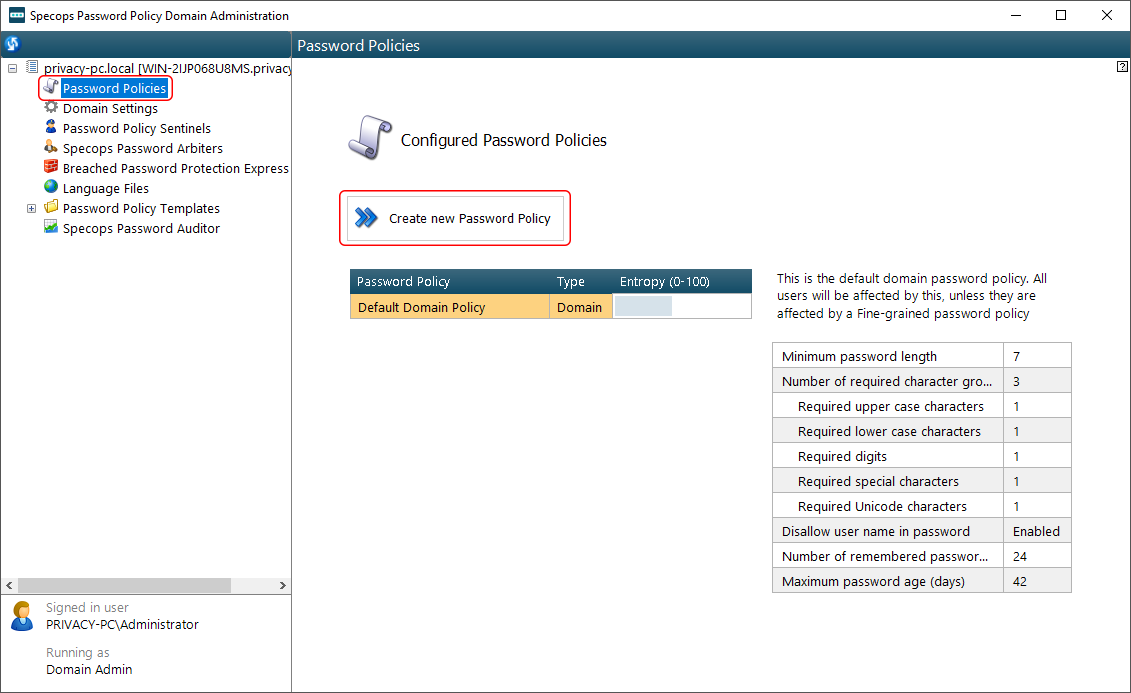
Select New Group Policy object.
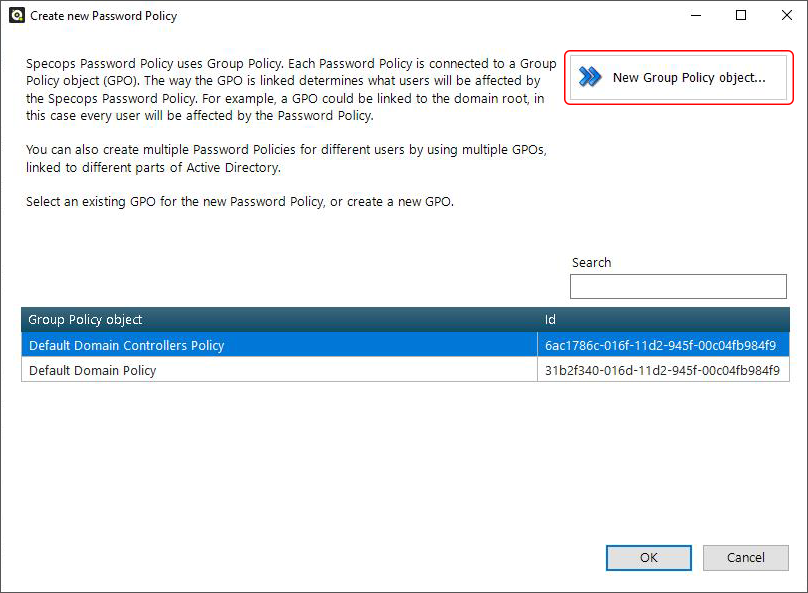
Assign a name for your Group Policy object (GPO), make sure your domain root is selected so that the rules apply to all users, and click OK.
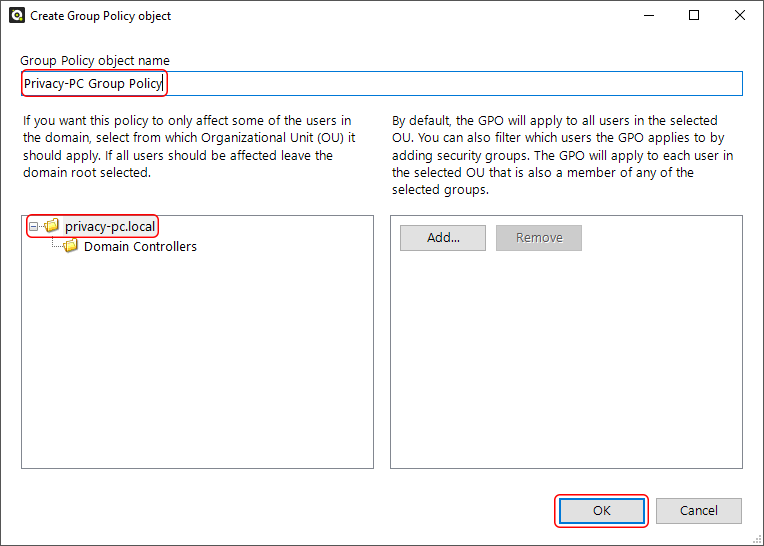
As soon as you see the new GPO listed with a unique ID, select it and click OK.
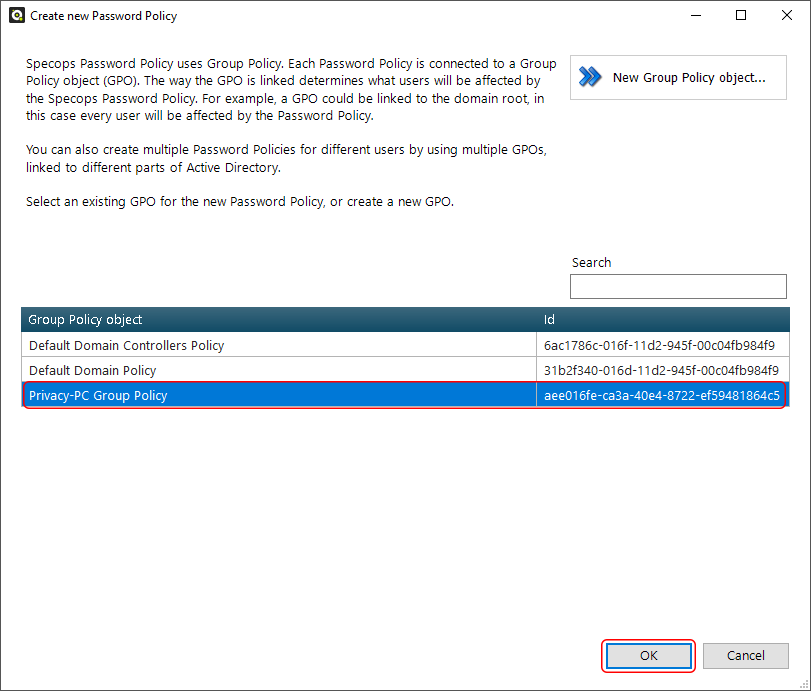
This brings you to a window providing templates that can be used as the foundation for your password policy. These include recommendations from Microsoft, NCSC, NIST, and NSA. Pick the one you’d like to build your password practices around. I decided to stick to NIST criteria. Click Next.
If the template of your choice requires a dictionary of words that should be prohibited in passwords, be sure to specify these strings here. It’s a good idea to include words associated with your company, such as its name and address. I also entered a few that are ridiculously easy to guess and, as such, must be disallowed. Be advised the dictionaries are case insensitive by default.
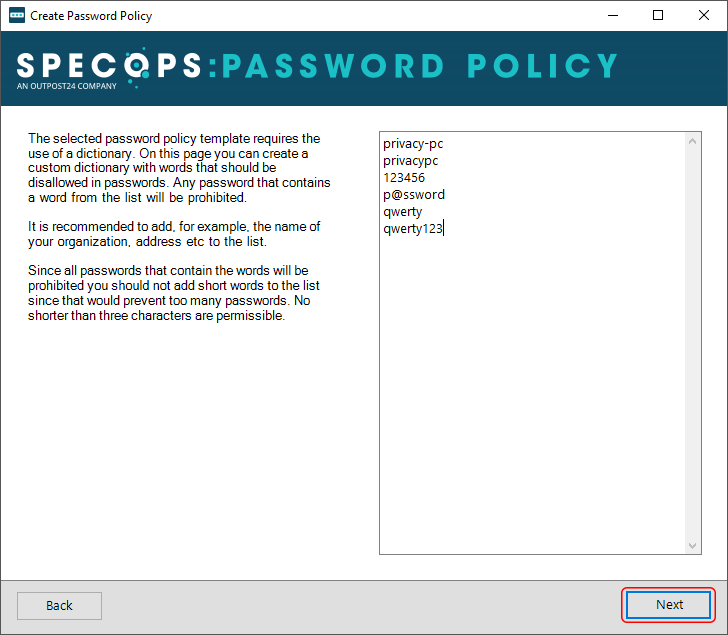
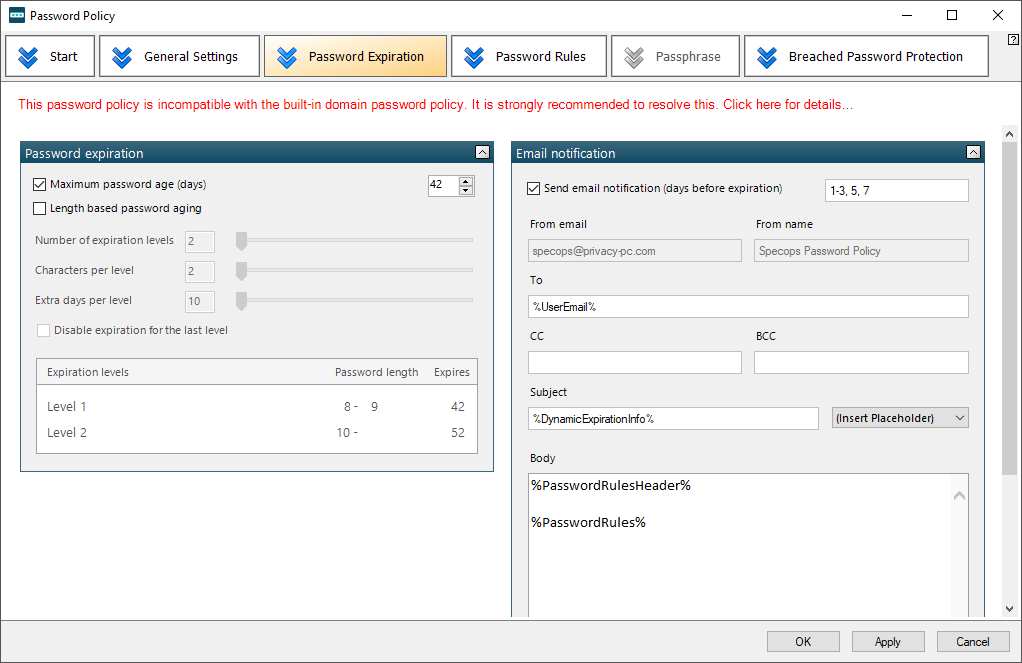
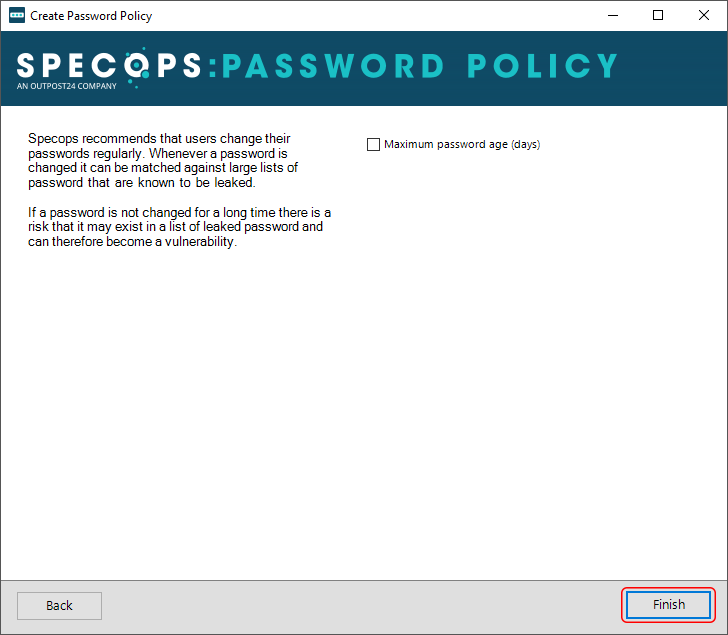
Next, define the maximum password age if you want to (you can do it at a later point, too) and click Finish.
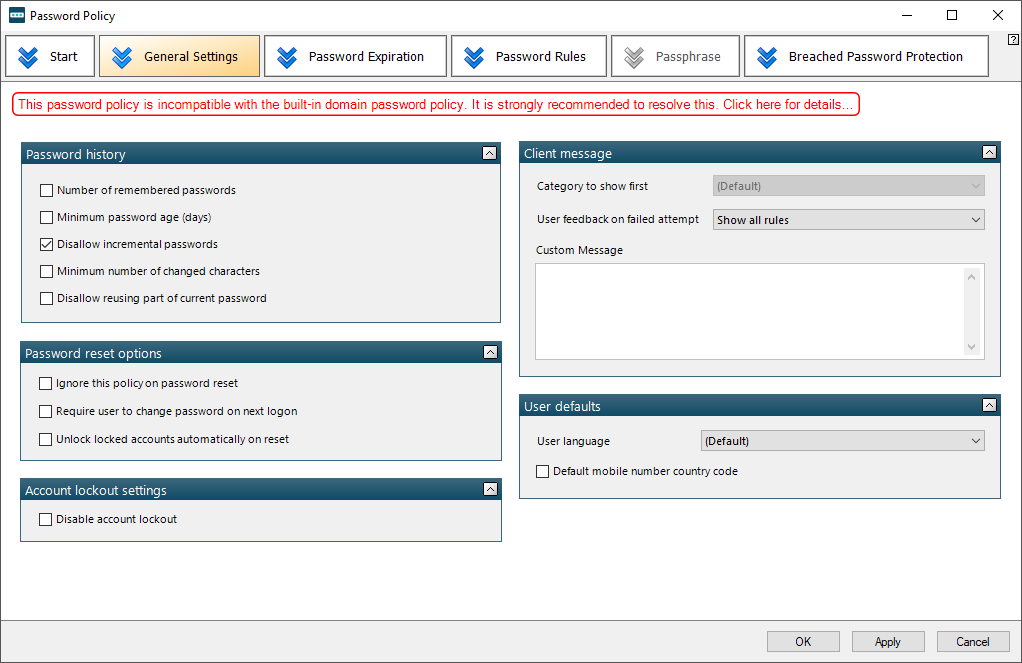
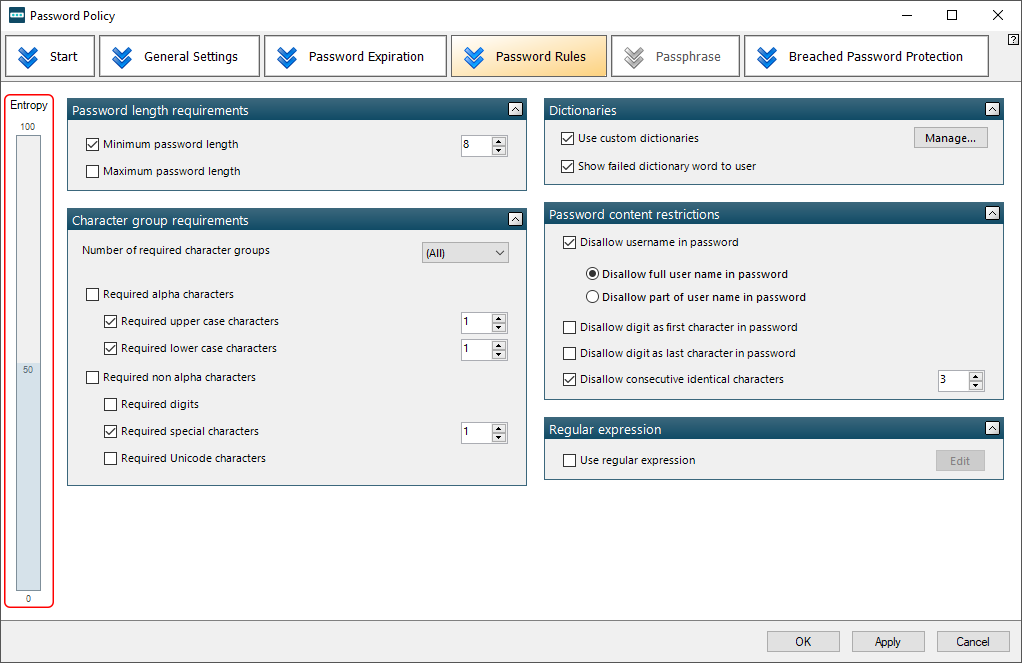
You aren’t done yet. To fine-tune the newly created Group Policy, use an interface with tabs for in-depth settings related to password expiration, password rules, passphrase, and the Breached Password Protection feature.
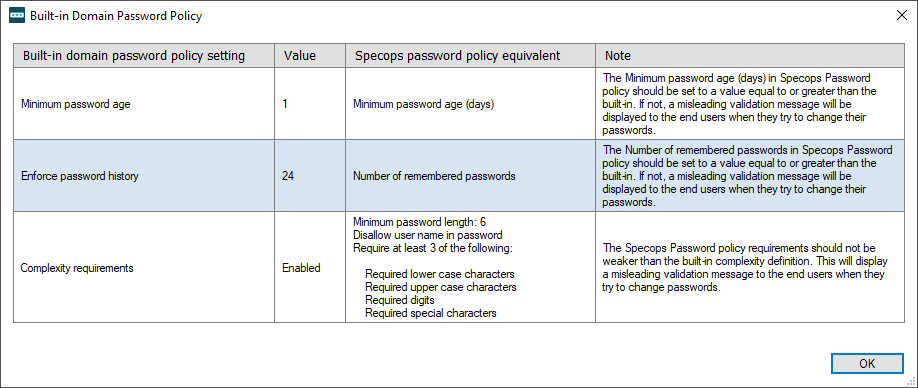
In case your current template fails to meet the criteria of the built-in domain password policy, you will see an incompatibility alert in red font (scroll through the slideshow below to view it). This warning is clickable and brings up a summary of the specific settings that could use enhancement. I made the relevant tweaks until the inconsistencies vanished one by one.
Notice the Entropy bar displayed within the “Password Rules” and “Passphrase” tabs. Simply put, it is an indication of how strong and hard-to-guess your policy-enforced passwords are going to be. On a separate note, the passphrase option gives the entropy an instant boost, so it’s by all means worth considering despite the obvious user experience caveats.
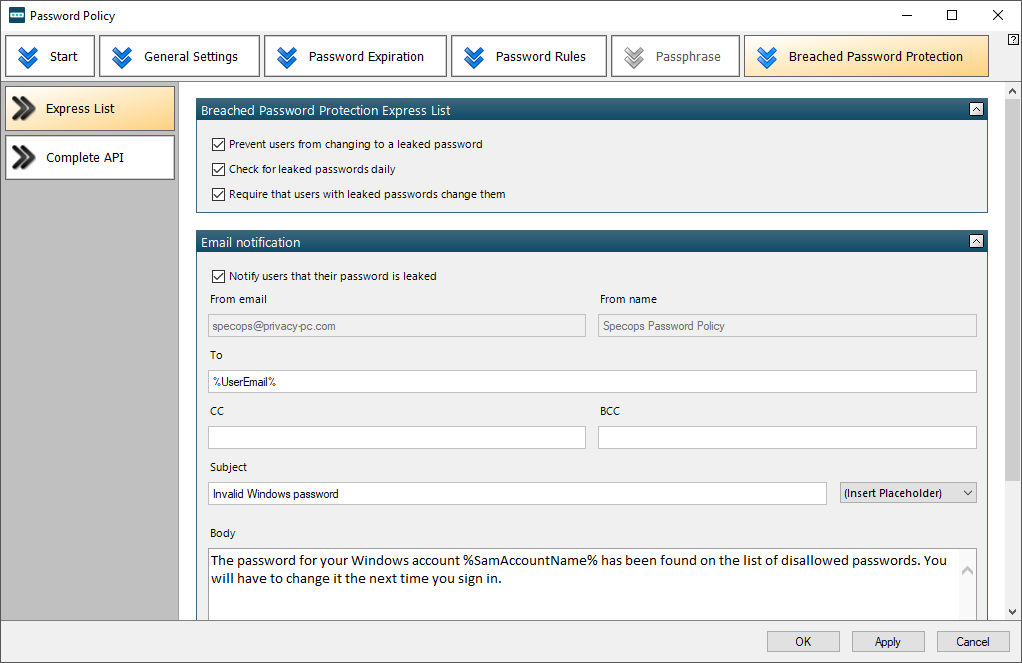
To ascertain that your employees cannot use compromised credentials, take the settings under the “Breached Password Protection” tab seriously.
For instance, don’t fail to enable the options to prevent users from changing to a leaked password, check for leaked passwords on a daily basis, and notify users over email that their password is leaked (make sure the mail server settings have been specified and verified as described in the dedicated section of this review).
After applying the GPO you have just customized, you will see it listed on the Configured Password Policies list. Consider this a new milestone in your corporate security. Note that the policy with a greater entropy score is the one that applies to your domain.
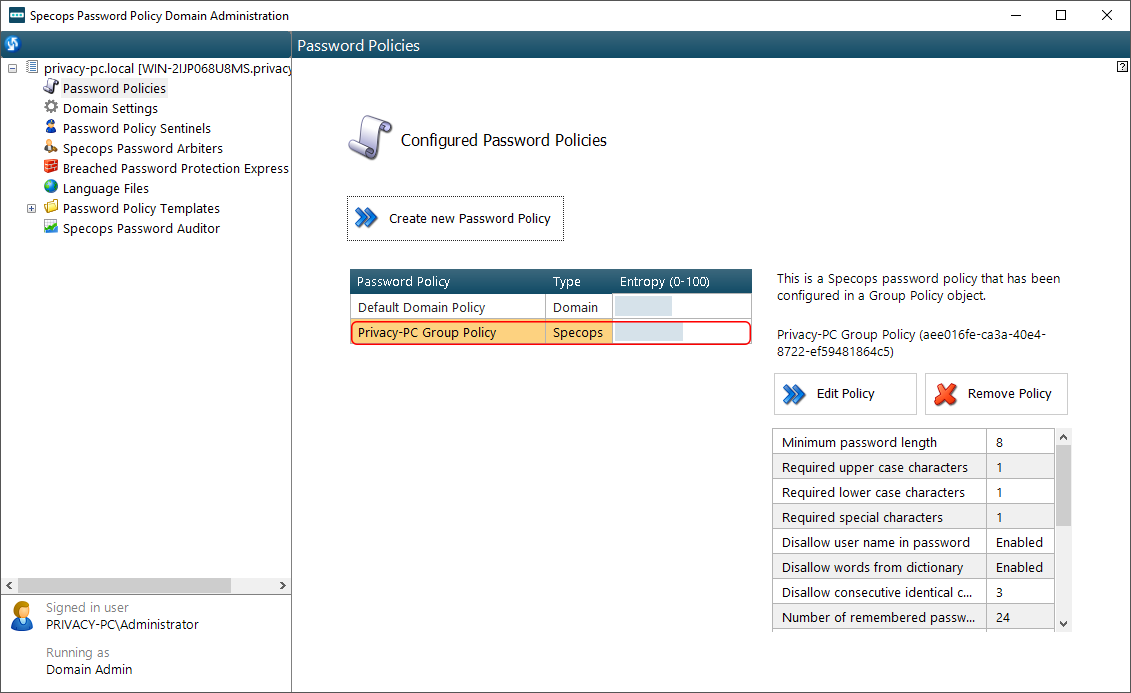
Specops Password Policy in action
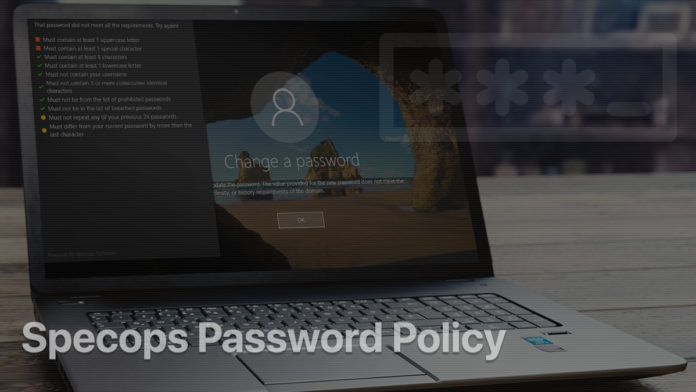
With the policy now in effect, the software provides intuitive real-time feedback whenever your users initiate password-related events. When changing a system password for example, they will henceforth be seeing a checklist of requirements as shown below.
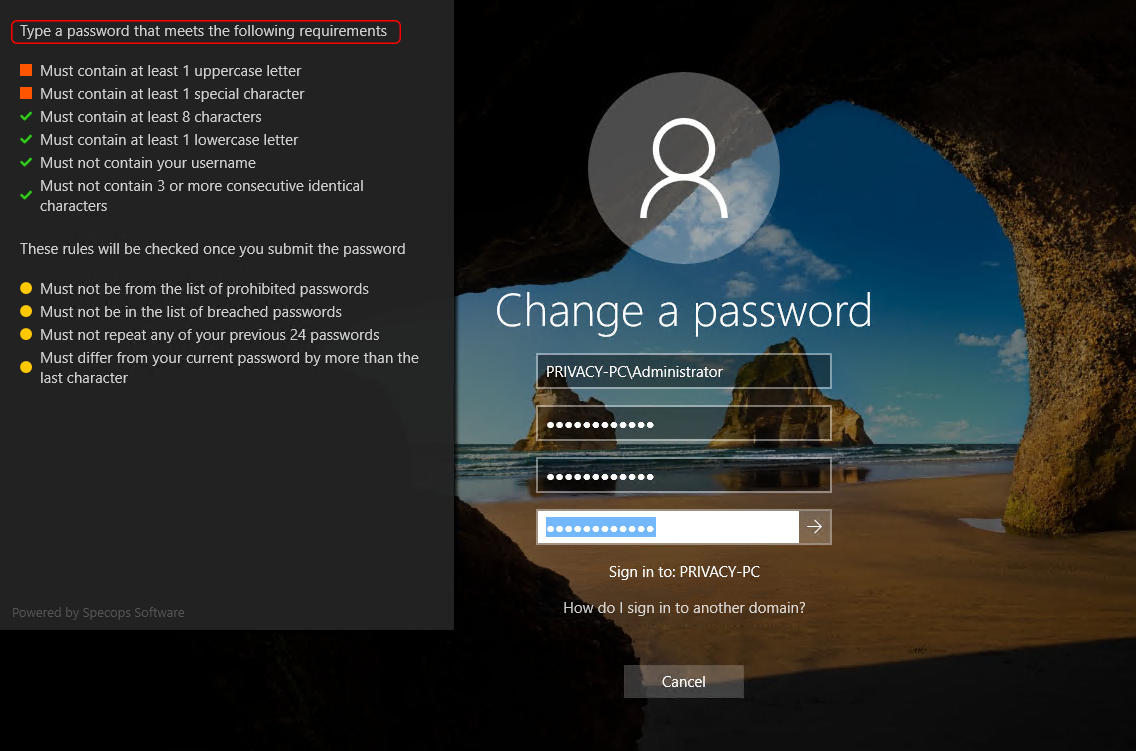
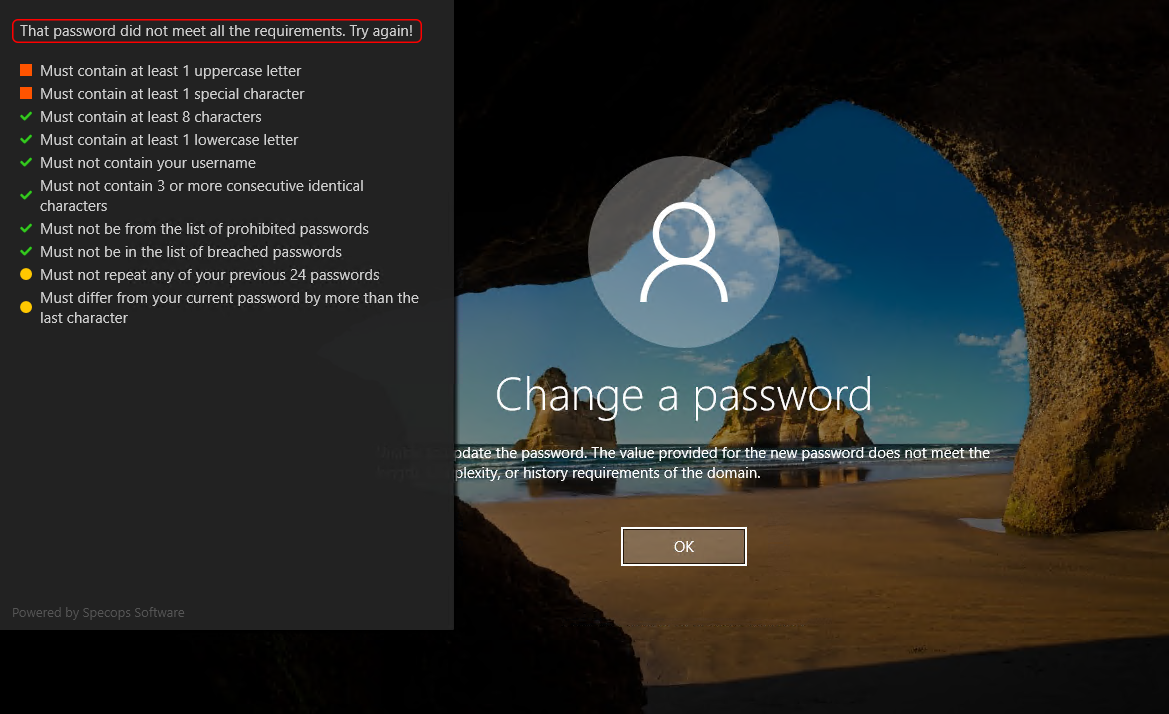
If the new password doesn’t conform to the current policy, you will see a relevant alert. Not only does it state that the entered combination is a no-go, but it also explains what specific requirements weren’t met (see the image below).
This raises the bar significantly for those on your team who happen to specify weak access credentials and contributes to autonomous password routines where users sort things out without administrator involvement.
Pricing
When it comes to the price tag, Specops sticks to a case-by-case approach, which I think makes a lot of sense for a product used in corporate environments. The license cost is calculated individually for each customer based on the number of Active Directory users in scope. That’s an inversely proportional (volume pricing) model in which the price per license goes down as the number of users goes up.
The publisher’s website provides a form that allows you to submit a pricing request. The software can be purchased as an annual subscription that covers tech support along with product updates.
The takeaways
They say an organization’s security architecture is as strong as its most vulnerable segment. I couldn’t agree more. Specops Password Policy prevents authentication from being that vulnerability. It’s a comprehensive solution that takes your experiences with passwords in Active Directory to the next level, both in terms of security and usability.
An important thing on the plus side of this software is the availability of policy templates. This way, you don’t have to go the extra mile to create a fine-grained password policy that meets the standards of the industry your company represents. With precise targeting at its heart, Specops makes it easy to implement a policy that applies to any GPO level – whether it’s a specific machine, user, or group.
Based on my testing, I like just about everything about this toolkit. It makes complicated things simple, with each component saying exactly what it does and giving you informative tips at all stages of customization. Perhaps the only thing I believe could use a tweak is that you can’t run product updates directly from the Domain Administration interface. When a new version is released, you need to find and relaunch the setup assistant to install it – this can take some digging beyond your computer’s Start menu. That’s no big deal at all, though.
The corporate password management routine can barely be described as a “set it and forget it” type of thing, but this software brings it really close to that condition. To recap, Specops Password Policy is definitely worth its salt, and I highly recommend it as a one-stop solution to solidify your authentication procedures in light of the escalating scourge of cyberattacks that target enterprises.