Neither TeslaCrypt nor its copycat AlphaCrypt ransomware is new on the cybercrime arena. In fact, this infection first surfaced in early spring 2015, and it has undergone eight updates over the course of the year. The rather frequent iterations haven’t introduced substantial changes to the trojan’s code and the infrastructure sustaining its operation, with the most prominent tweaks relating to the way the encrypted user files are presented to the victims. The most recent version spotted around is assigning .ccc or .vvv extensions to the files it froze on the hard disk as well as network shares and removable drives. The virus has been invariable in terms of the cryptographic algorithm used for making one’s data inaccessible, where the Advanced Encryption Standard is the one of choice for the fraudsters.
As far as the distribution goes, TeslaCrypt happens to be backed by the Angler exploit kit, which encompasses an advanced toolset for finding and taking advantage of critical software vulnerabilities on the would-be-targeted computer. Before the users confront this stealthy malady, though, they visit a compromised website and get redirected from there to a page running the kit. The attack is then a matter of spotting and exploiting an outdated program on the workstation for the ransomware payload to be dropped on the PC beyond antivirus detection.
As soon as the trojan’s executable has been added to the AppData folder, which happens instantly after the trespass, a scan for data is launched in the background. During this scan the ransomware looks for files whose formats match a predefined list of about 180 extensions. In particular, some of the popular formats being targeted include:
.wma, .avi, .csv, .zip, .bkp, .mddata, .syncdb, .mov, .m3u, .flv, .js, .txt, .css, .png, .jpeg, .jpg, .pdf, .psd, .rft, .ppt, .pptx, .xls, .xlsx, .xlsm, .xlsb, .dwg, .pst, .ppt, .pptm, .pptx, .doc, .docx, .docm.
Obviously, these reflect the data that is personal rather than operating system-related. Meanwhile, the main criterion for the scanning is whether or not a specific drive is represented as a letter.
The workflow of encrypting the entirety of supported files is also a furtive process. The AES block-cipher encryption is uncrackable, which is why it’s the one the U.S. Government adopted for protecting classified information. Basically, this means that the victims of TeslaCrypt can only count on complete decryption after they submit a ransom to the people in charge of this plague.
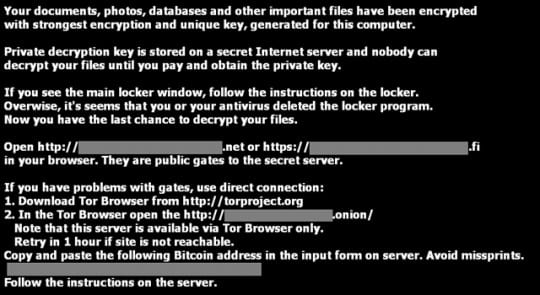
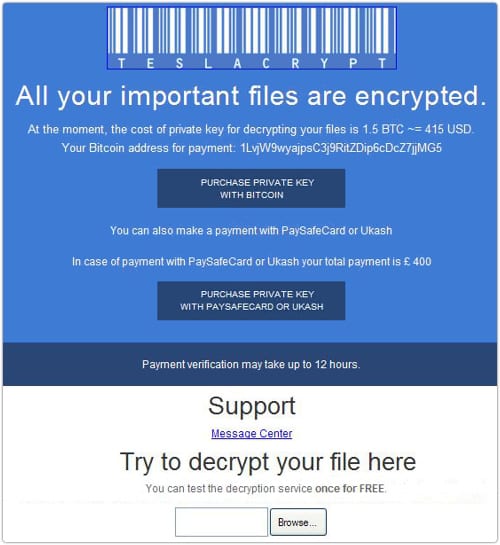
As mentioned above, all files distorted by TeslaCrypt get a new extension, which is either .ccc or .vvv at the moment. These attributes tend to change as new variants of the ransomware emerge. Having completed the information encryption part of its job, the trojan injects .txt and .html documents named “how_recover_(random)” into every directory comprising seized files. Also, the Windows wallpaper gets modified to a BMP file which provides TOR links to the secret server. The same details are provided in the ransom note documents. Each victim gets unique TOR gateway links and Bitcoin address to proceed with the payment.
There seems to be no way of restoring the data encrypted by this threat except for paying. There are things, however, that anyone infected should try before falling for the extortion. We have singled out several techniques that have the potential of file recovery depending on peculiarities of the compromise and the ransomware version.
TeslaCrypt virus removal
As counterintuitive as it is, removal of this particular threat is not too complicated unlike the cleanup scenarios for screen lockers which represent another group of ransomware infections on the loose. The main challenge in regards to TeslaCrypt is getting personal files back without having to do what the fraudsters want. Basically, this means you can get rid of the malady using efficient security software without much of a hindrance, but options for recovering the encrypted data are a matter of a separate discussion, which we will touch upon in this guide as well.
Let’s now outline a rather easy and perfectly effective way of ransomware removal from a contaminated computer. Please follow the directions below step by step:
- Download and install HitmanPro.Alert
- Open the program, click on the Scan computer button and wait for the scan to be completed
- When HitmanPro.Alert comes up with the scan report, make sure the Delete option is selected next to the ransomware entry and other threats on the list, and get the infections eliminated by clicking on the Next button

Now you’ve got both some good and bad news. On the one hand, TeslaCrypt is gone from your computer and won’t do any further damage. On the other, your files are still encrypted, since elimination of the malware proper does not undo its previous misdemeanors. In the next section of this guide we will highlight methods that may help you restore your data.
Restore encrypted files using Shadow Copies
As it has been mentioned above, despite successful removal of TeslaCrypt the compromised files remain encrypted with the AES algorithm. While it does not appear possible to obtain the key for decryption in this case even with brute-forcing, you can try to restore previous versions of these files either using the native Windows functionality or the application called Shadow Explorer. Please note that this method is only applicable in case you have System Restore enabled on your PC, and the versions of the files that you can recover this way may not be the most recent. It’s definitely worth a try, though.
Getting your files back using Previous Versions functionality
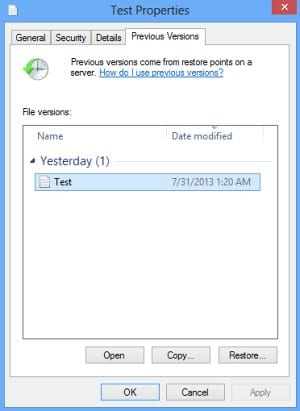
Windows provides a feature where you can right-click on an arbitrary file, select Properties and choose the tab called Previous Versions. Having done that for a particular file, you will view all versions of it that were previously backed up and stored by the so-called Volume Shadow Copy Service (VSS). The tab also provides the history of these backups by date.
In order to restore the needed version of the file, click on the Copy button and then select the location to which this file is to be restored. In case you would like to replace the existing file with its restored version, click the Restore button instead. Conveniently enough, you can have whole folders restored the same way.
Restoring encrypted data with Shadow Explorer utility
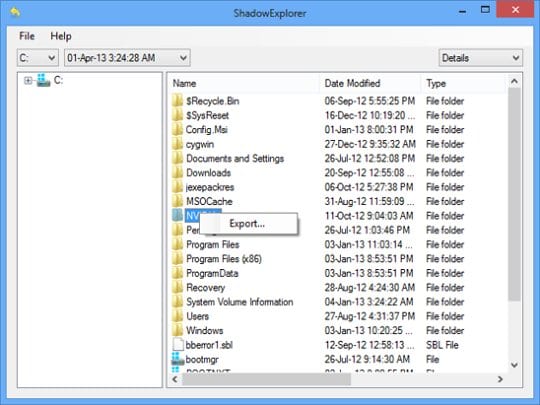
Besides the built-in Windows functionality highlighted above, you can use an application that will restore previous version of entire folders for you. It’s called ShadowExplorer. Once you download and launch this program, it will display all of your drives as well as a list of dates when Shadow Copies were generated. Simply pick the desired drive and date for restoration, as shown on the following screenshot:
Right-click on the directory you wish to restore and choose Export in the context menu. This will be followed by a request to indicate where you would like to restore the information to.
Use automatic recovery software
It might sound surprising, but TeslaCrypt does not encrypt one’s actual files. It deletes them. What does get encrypted is the copies. This brings us to the point where a specific type of software can be used for dragging the original data out of memory, where it ended up after the erasure. Efficient recovery tools can work wonders in these ransomware scenarios.
Download and install Recuva by Piriform to give this restoration vector a shot. By running a computer scan with Recuva, you will get a list of all recoverable files and be able to reinstate them to their original location or another place of choice.

Bottom line
TeslaCrypt poses a critical risk to one’s personal information therefore the main focus security-wise should be made on prevention. In this context, some basic precautions can do the trick: refrain from opening email attachments from unknown senders and schedule regular antivirus software updates. Furthermore, performing data backups is a remarkable habit that will help evade the adverse aftermath of this attack.