
Content:
What is CryptoLocker?
September 2013 turned out fruitful and lucrative for one of the cybercrime syndicates out there, but really alarming for private users and organizations on the other side of the IT security battlefield. The reason is the launch of a vicious computer infection known as CryptoLocker which in terms of severity and consequences for the infected PCs outstripped the typical “Police” ransomware dominating the extortion landscape at that time.
Whereas regular screen lockers yield to removal and complete remediation of the contaminated system via a special procedure, CryptoLocker encrypts users’ files and won’t allow for restoring those unless a certain amount of money is paid. Furthermore, unlike ransomware which attempts to disguise itself as something legitimate, this type of malware goes straightforward on the victim and in no way conceals its true extortion nature. It encrypts your personal files using asymmetric encryption, which means that the decryption process involves a public and private key, the latter being stored on the criminals’ remote server.
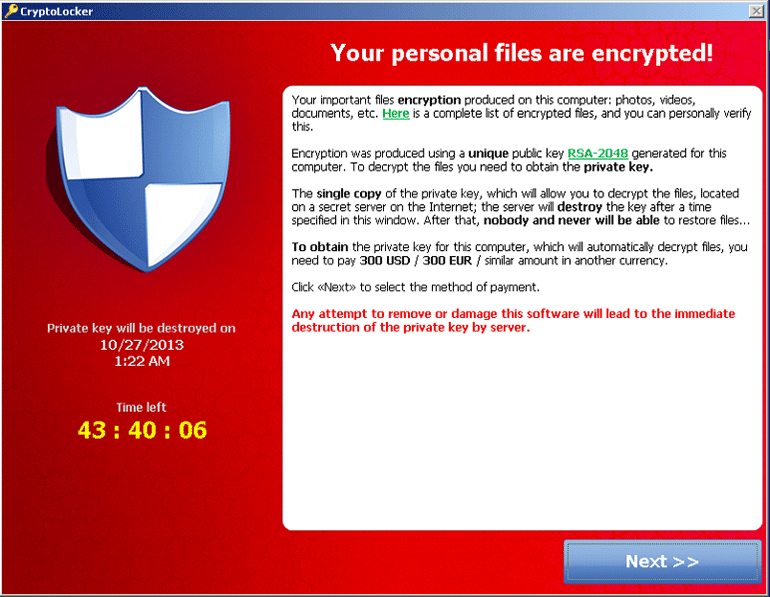
For the users to have their files decrypted, they needed to pay a fee of $100-300 via Bitcoins (the cheapest option according to the fraudsters’ notice). Newer versions can demand up to $1,000 worth of cryptocurrency. The payment is to be made within 96 hours otherwise all of the encrypted files will be lost. Note that the original version of the ransomware additionally accepted payments made via Green Dot MoneyPak (USA only), Ukash or cashU – this was some lame OPSEC, obviously, and the crooks ended up excluding these easily traceable channels from their modus operandi.
At its dawn, CryptoLocker was known to spread by means of sending emails masqueraded as ones concerning customer issues related to FedEx, DHS, UPS, etc. The contamination proper would take place when an unsuspecting user opened up an attached ZIP file that contained a malicious executable made to look like it’s a PDF item. Six years afterwards, this predatory program has considerably extended its reach by utilizing many more phishing email templates and also employing exploit kits for propagation.
CryptoLocker variants
Although now in 2019 the above highlights seem like an echo from a distant past, CryptoLocker is still alive and kicking, having evolved into a modern threat accommodating a top-notch deleterious toolkit. It exists in quite a few different incarnations, some of which are copycats of the famous progenitor, while others could be spinoffs distributed on a RaaS (Ransomware-as-a-Service) basis. Here is a list of widespread CryptoLocker variants discovered to date:
- Crypt0L0cker – appends the .encrypted or .enc extension to encrypted data, drops a ransom note named HOW_TO_RESTORE_FILES.txt
- CryptoLocker-v3 – uses the .crypted extension to label hostage files
- Cryptographic Locker – concatenates the .clf string to filenames
- PCLock – doesn’t rename files, creates a ransom note named last_chance.txt or Your files are locked!!!.txt
- CryptoTorLocker2015 – added the .CryptoTorLocker2015 suffix to affected files, dropped HOW TO DECRYPT FILES.txt rescue note on desktop
- Crypt0 – uses the ._crypt0 file extension and HELP_DECRYPT.txt ransom manual
- Cryptolocker3 – leverages XOR cryptographic algorithm, stains filenames with .cryptolocker extension
- CryptoLocker 5.1 – appends the .locked tail to filenames, demands €250 worth of Bitcoin for recovery within a 48-hour deadline
- MNS Cryptolocker – replaces desktop wallpaper with a ransom note demanding 0.2 BTC and instructing the victim to contact the extortionists at alex@dr.com
- CryptoLocker EU – has Russian roots, uses the self-explanatory .send 0.3 BTC crypt file extension
- CryptON – targets Portuguese-speaking users, drops a ransom note named COMO_ABRIR_ARQUIVOS.txt
Most of these CryptoLocker personas feature a similar or identical warning window style, which is a way for the attackers to pay tribute to the notorious prototype of all modern file-encrypting ransomware. Some spinoffs have a different look and feel while indicating the progenitor’s name on their alerts, as is the case with the above-mentioned PCLock version illustrated below.
All in all, CryptoLocker became a real game-changer in the cyber extortion ecosystem. Although its first distribution wave is now history, it demonstrated that cryptography could be weaponized for moneymaking purposes and thereby encouraged numerous hacker gangs to get on the hype train.
CryptoLocker 2019 virus: contamination workflow
Now let’s have a look at what actually happens to the infected machine from more of a technical viewpoint. Once CryptoLocker 2019 infiltrates a targeted computer, it creates a random-named file in the root of AppData or LocalAppData path and spawns several registry entries to ensure it gets launched on system startup as well as in Safe Mode. This being done, the culprit establishes a background connection with its Command & Control server in order to get a public key for file encryption, the private key being stored outside of the affected PC.
Then, the malware scans all computer drives to locate files with a variety of extensions, some of which are most common ones such as *.doc, *.docx, *.docm, *.xls, *.xlsx, *.xlsm, *.xlsb, *.ppt, *.pptx, *.rtf, *.psd, *.pdf, *.jpg, *.png, etc. Having found all of these, CryptoLocker 2019 encrypts them and then displays an alert screen.
The ransomware window contains a ticking countdown clock for enhancing the intimidation and urgency aspects, as well as details on what should be done for decryption to commence. It has been reported that entering a wrong code will cause the remaining time to be reduced. Also, in case the payment is made the files will not be decrypted immediately as it apparently takes the villains some time for processing the payment and request proper. However, according to user feedback, the scammers behind CryptoLocker have been ‘honest’ so far in terms of decrypting files after payment – an honor code of a kind, if you will.
In the following section, we will show you how to get rid of CryptoLocker 2019 and try to restore your encrypted files without paying the ransom.
CryptoLocker 2019 virus removal
As counterintuitive as it is, removal of this particular threat is not too complicated unlike the cleanup scenarios for screen lockers, which represent another group of ransomware infections on the loose. This being said, the main challenge in regards to CryptoLocker 2019 ransomware boils down to getting personal files back without having to do what the extortionists want.
Basically, this means you can get rid of the malady using efficient security software without much of a hindrance. Make sure your antivirus is up to date if not check here. However, the options for recovering encrypted data are a matter of a separate discussion, which we will cover further down.
Let’s now outline a rather easy and perfectly effective way of ransomware removal from a contaminated computer. Please follow the directions below step by step:
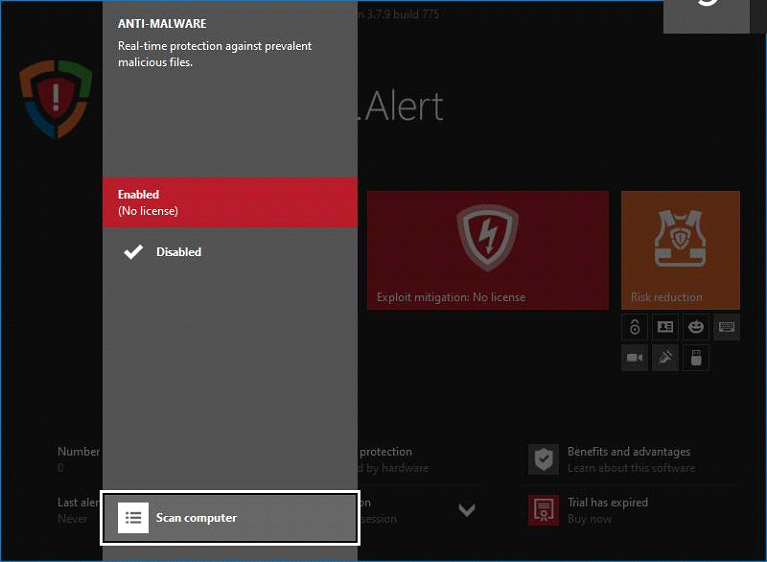
- Download and install HitmanPro.Alert
-
Open the program, go to its Anti-Malware module

- HitmanPro.Alert comes up with the scan report

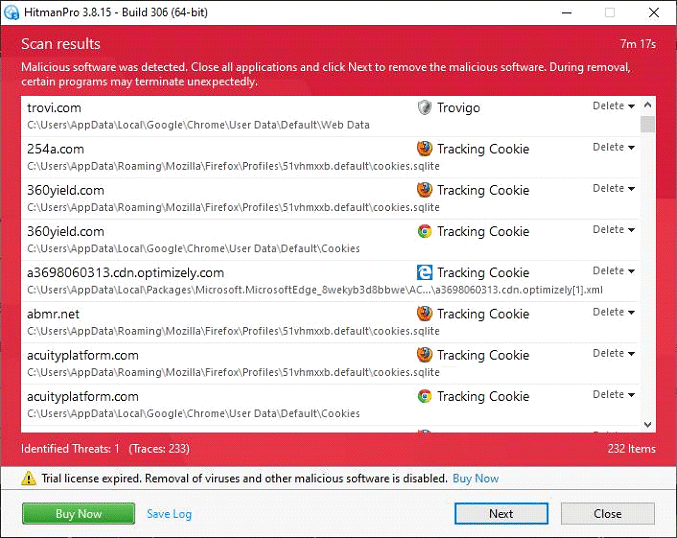
Now you’ve got both some good and bad news. On the one hand, the CryptoLocker 2019 ransomware is gone from your computer and won’t do any further damage. On the other, your files are still encrypted, since elimination of the malware proper does not undo its previous misdemeanors. In the next section of this guide we will highlight methods that may help you restore your data.
Restore encrypted files using Shadow Copies
As it has been mentioned above, despite successful removal of the CryptoLocker 2019 virus, the compromised files remain encrypted with a strong cipher. While it does not appear possible to obtain the key for decryption in this case even with brute-forcing, you can try to restore previous versions of these files either using the native Windows functionality or the application called Shadow Explorer.
Please note that this method is only applicable in case you have System Restore enabled on your PC, and the versions of the files that you can recover this way may not be the most recent. It’s definitely worth a try, though.
Getting your files back using Previous Versions functionality
Windows provides a feature where you can right-click on an arbitrary file, select Properties and choose the tab called Previous Versions. Having done that for a particular file, you will view all versions of it that were previously backed up and stored by the so-called Volume Shadow Copy Service (VSS). The tab also provides the history of these backups by date.
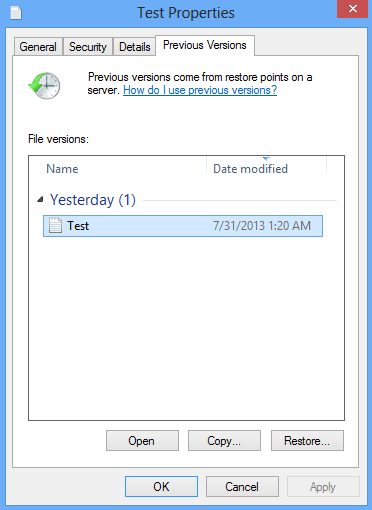
In order to restore the needed version of the file, click the Copy button and then select the location to which this file is to be restored. In case you would like to replace the existing file with its restored version, click the Restore button instead. Conveniently enough, you can have whole folders restored the same way.
Restoring encrypted data with Shadow Explorer utility
Besides the built-in Windows functionality highlighted above, you can use an application that will restore previous version of entire folders for you. It’s called ShadowExplorer.
Once you download and launch this program, it will display all of your drives as well as a list of dates when Shadow Copies were generated. Simply pick the desired drive and date for restoration, as shown on the following screenshot:
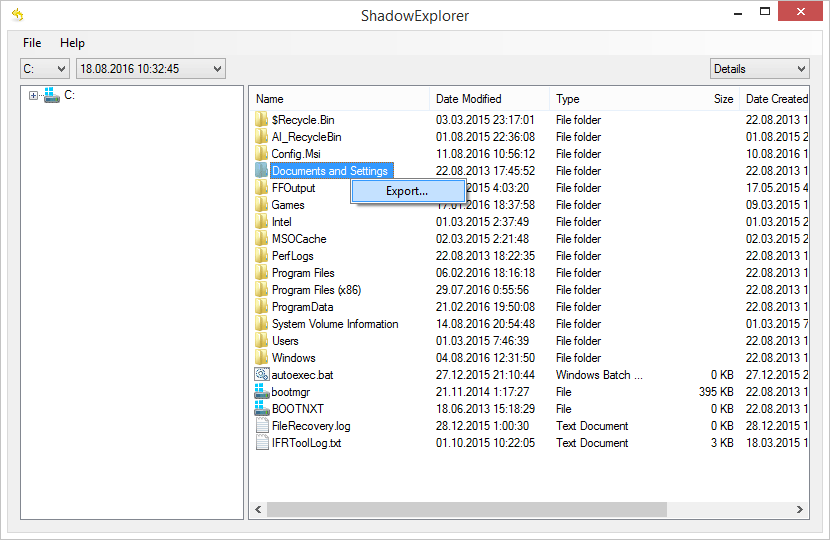
Right-click the directory you wish to restore and choose Export in the context menu. This will be followed by a request to indicate where you would like to restore the information to.
Use automatic recovery software
It might sound surprising, but some ransomware strains do not encrypt one’s actual files. They delete them. What does get encrypted is the copies. This brings us to the point where a specific type of software can be used for dragging the original data out of memory, where it ended up after the erasure. Efficient recovery tools can work wonders in these ransomware scenarios.
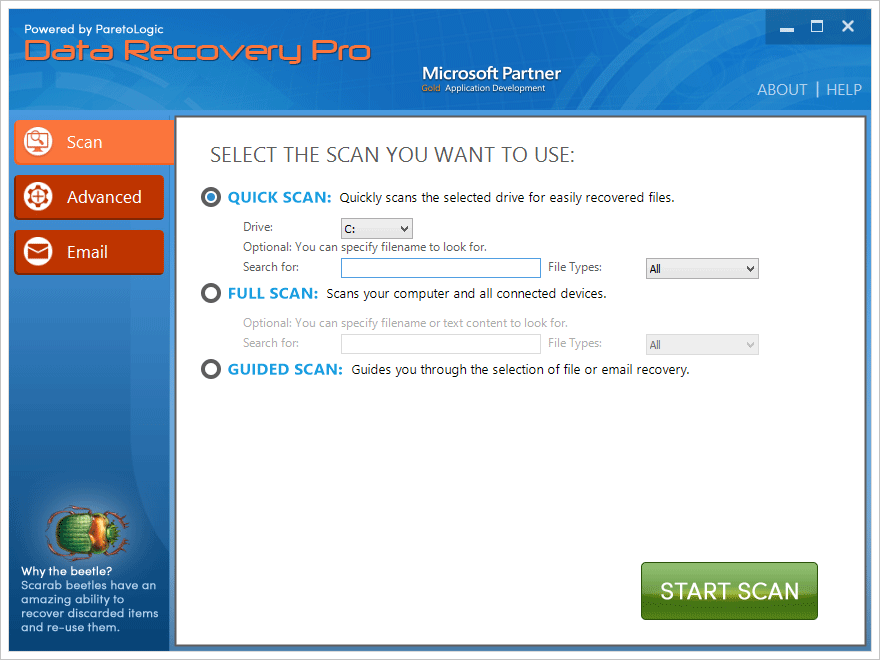
Download and install Paretologic Data Recovery Pro to give this restoration vector a shot.
By running a computer scan with Data Recovery Pro, you will get a list of all recoverable files and be able to reinstate them to their original location or another place of choice.
Summary
CryptoLocker 2019 is a really nasty computer threat designed to act in a very cunning way. There’s no particular focus made on preventing users from removal of this infection, the underlying reason being that most people will want their encrypted files back.
Again, no method has so far been found for obtaining the private key which is necessary for decrypting the affected user’s personal data – of course, other than surrendering to the criminals by paying the ransom via a monetary system which guarantees them anonymity and guards from prosecution in a way. The file restore workflows outlined in this article may help partially, but only in case System Restore was activated earlier; moreover, there’s no confidence that the file version you recover will be the most recent one.
In order to protect yourself from being infected with viruses like CryptoLocker 2019, be sure to use up-to-date versions of reliable security software that won’t allow malicious code to be executed on your computer. Also, a rule of thumb is to maintain backups of the most valuable data – this is an amazingly effective proactive measure in ransomware scenarios.






























cool article!!
my computer didn’t back up, could i still choose the Previous Versions functionality?
thanks,
Janee,
By your phrase “my computer didn’t back up” did you mean you didn’t have System Restore enabled? If so, unfortunately you won’t be able to recover previous versions of the encrypted files using the mentioned native Windows functionality.
If you meant something else, please specify.
Thanks
I downloaded the shadow explorer but there do not apear to be any available versions before the virus was downlaoded
Sorry to hear that. There is no solution yet to decrypt your files back.
The cryptolocker virus attack may come from different sources. These kind of virus is observed by the Dell Secureworks in 2013 September. The points which are mentioned here is really impressive and helpful for me. Keep sharing more in the upcoming posts.
I had the virus, but I was about to do this, but I knew that I could go to Safe Mode, regedit and delte from Microsoft -> Windows -> suheugheugehuguejrgig.inf, then I go to AppData on Roaming and I saw Cryptolocker! I delete that, then I go to my normal Windows. Next I checked Windows Task Manager, and no cryptolocker was running on my PC, then I did a quick scan to be sure that everything is gone! Then, I restored my files/ backup them!
Mihai, thanks for your comment!
Glad you got rid of the bug. Just a quick notice – backing up one’s files is essential here. CryptoLocker isn’t that hard to remove, but getting the files back is the key problem.
Thank you so much. The shadow explorer worked perfectly!
So the crooks and thieves are smarter than the smartest IT people on the planet? Why hasn’t someone come up with a way to counter act what the bad guys are doing and charge just a little less then what the crooks want.