
Installing some browser extensions might turn out a mixed blessing, because along with the benefits and increased web surfing convenience users may run into the problem of excessive intrusiveness. Ambiguous experience of this sort is exemplified by the Conduit Toolbar. Whereas, on the one hand, it is a custom tool that publishers can take advantage of in terms of product promotion campaigns, regular users who have it on their computers suffer from a severe frustration called forth by the abominable browser hijack this add-on leads to.
Some of the common symptoms of being affected by this adware include unannounced changes in one’s browser configuration. Whichever web browser you are using – be it Internet Explorer, Firefox, Chrome, etc. – the defaults such as homepage and preferred search engine will be altered to Search.conduit.com. It suffices to visit the latter just once to understand that it has been primarily tailored for advertising, the rest of the regular search system capacities such as keyword relevance and the like being to some extent disregarded.
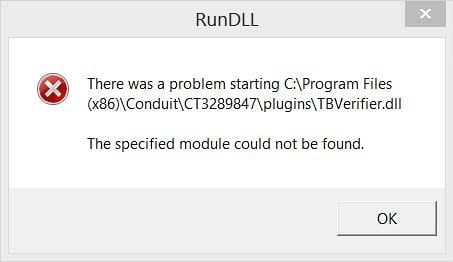
Another widely reported symptom is a RunDLL alert that pops up during Windows boot, saying that there is a problem starting TBVerifier.dll – a process related to the Conduit Toolbar. This scenario may testify to a misconfiguration in the browser extension’s functioning.
So, how come a legitimate business strategy causes inconveniences to individual users? The underlying reason for this has to do with the unsound aspiration for profit-making. The growth in the user base of Conduit’s products directly converts into greater online advertising revenues. By displaying ads above the fold within web pages people get redirected to, authors of this extension bring potential customers to advertisers but cause a great deal of trouble to those who happened to get this add-on integrated into their browsers.
Speaking of the way Conduit Search adware installs on PCs, it’s noteworthy that it gets on board either as a bundle to third-party software or affiliated apps (iWin Toolbar, SweetIM Bar Toolbar, Community Toolbar by Conduit, Search Protect, Conduit Apps Toolbar, BrotherSoft Extreme), or gets installed out of curiosity when a user thinks it’s a great thing. In any case, inability to freely surf the Internet quickly becomes a powerful stimulus for those affected to uninstall this annoying add-on. Unfortunately, Conduit Search removal is not easy, requiring a complex of steps to be followed. This guide will show you several clear methods to get rid of this adware.
Use reliable security software to detect and remove Conduit Search hijacker
CCleaner by Piriform is an efficient solution designed to automatically uninstall persistent malware such as the unwanted browser extensions related to Conduit hijacker and cease the browser redirect activity.
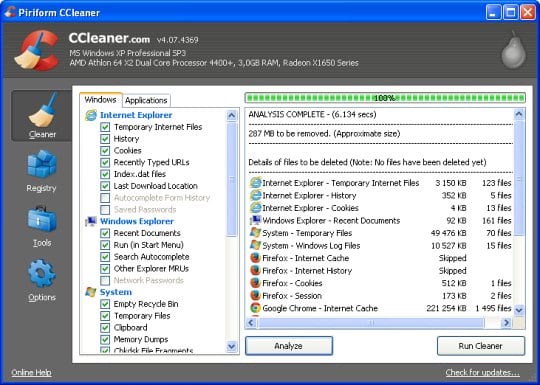
- Download free or paid version of CCleaner by Piriform and save it to your Desktop. Install and run the software.
- Click on the Cleaner button in the left-hand navigation menu, select Windows and Applications tabs in turn, and click Analyze option for each. Once the analysis has been completed, click Run Cleaner .
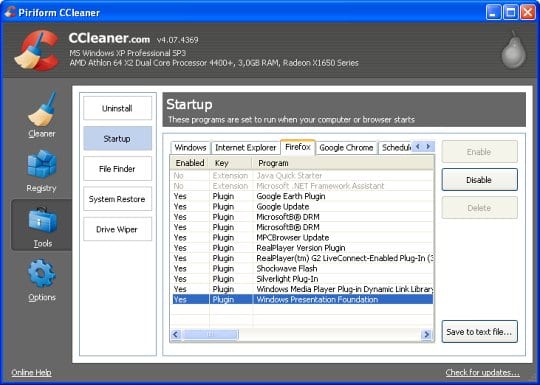
- Go to Tools in the navigation menu and select the Startup option. Search entries under all available tabs (‘Windows’ through ‘Context Menu’) for dubious items that might be related to Conduit adware (Conduit Community Toolbar, Search Protect, Conduit Apps Toolbar, BrotherSoft Extreme, etc.) and choose Disable and Delete for each one.
- You can also use the Uninstall functionality under Tools to completely get rid of browser add-ons / toolbars that cannot be deleted manually.
- Uninstall malicious extension(s) from Control Panel:

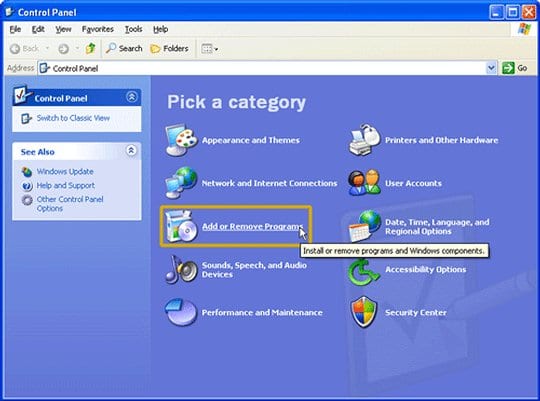
- On Windows XP: go to Start –> Control Panel –> Add/Remove Programs
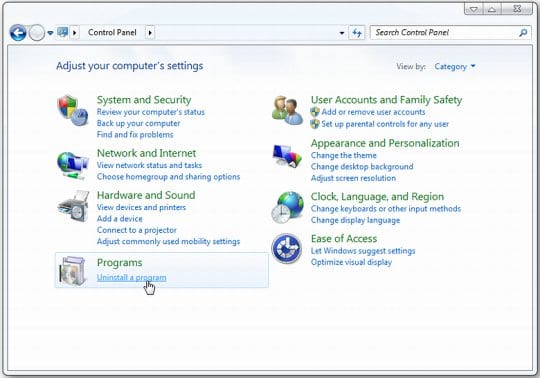
- On Windows Vista / 7: go to Start –> Control Panel –> Uninstall a Program
- On Windows 8: click on Search icon –> type in ‘add or remove‘ (this will suffice) –> select Add or remove programs
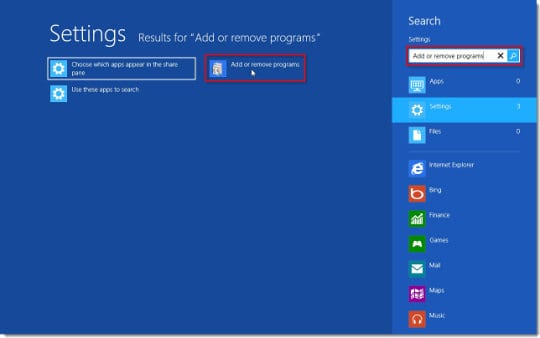
When the screen for program removal appears, look for the following items:
– Conduit Community Toolbar
– Search Protect by Conduit
– Conduit Apps Toolbar
– BrotherSoft Extreme
– iWin Toolbar
– SweetIM Bar Toolbar
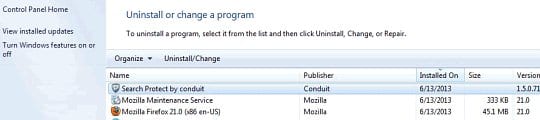
If located on the list, these should be uninstalled immediately as they are known to cause Search.conduit.com to show up in one’s web browser without user consent.
Remove Conduit Search from your browser
Conduit Search removal from Mozilla Firefox
- Go to Tools and select Add-ons in the drop-down list
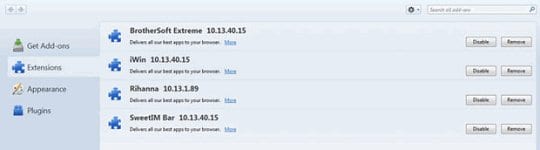
- Choose Extensions in the left-hand navigation panel and examine the list for entries associated with Conduit (BrotherSoft Extreme, Search Protect, iWin Toolbar, etc.). When found, click Remove next to the culprit
- Proceed to Options under Tools menu
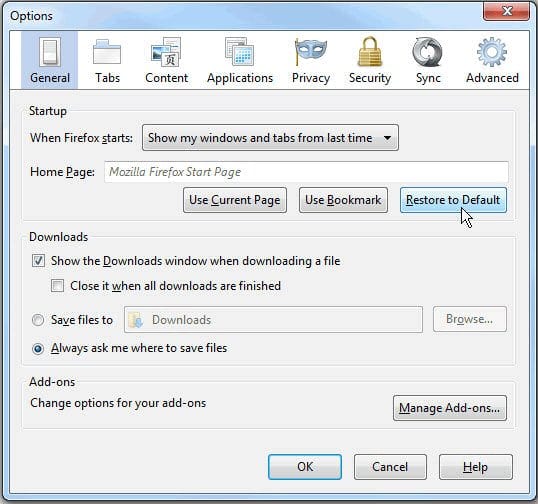
- Hit the General tab and select Restore to Default as shown on the image below
- In the search box to the right of the URL field, click on the arrow pointing downwards
- Click on the Manage Search Engines option in the drop-down menu that appears
- Click on the Conduit entry and select Remove
Remove Search.conduit.com hijacker from Google Chrome
- In the top right of your Chrome window, click on the Chrome menu icon
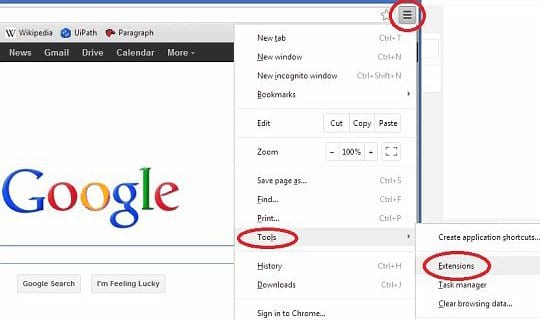
- Select Tools in the drop-down menu and choose Extensions
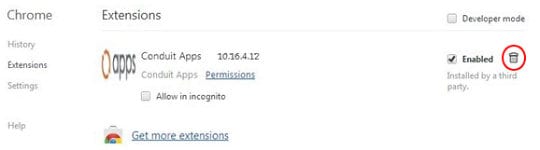
- Under Extensions, find the add-on related to Conduit and click on the trash bin next to it
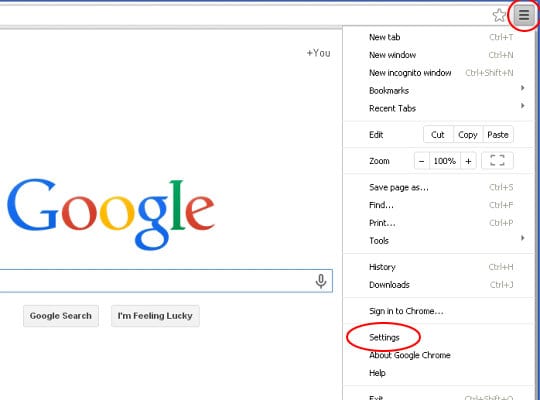
- Go to Settings under Chrome menu
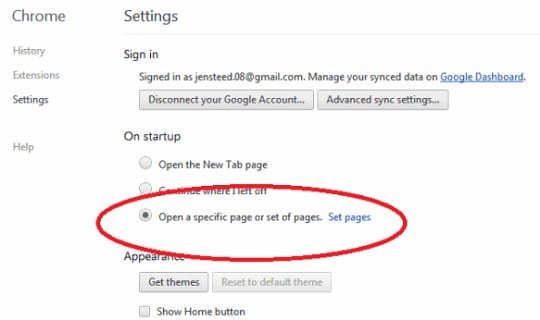
- Under Settings, Locate the On startup section and click Set pages
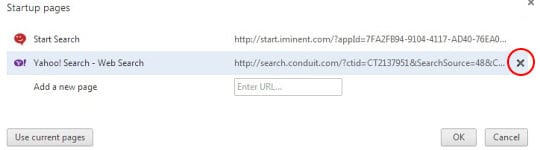
- On the list of startup pages, find the one related to Conduit Search and click on the X button to the right of it
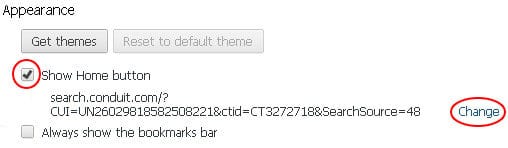
- Go to Appearance section under Settings. Select Show Home button option and click Change
- Activate the Use the New Tab page radio button and click OK
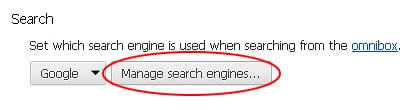
- Proceed to the Search section under Settings and select Manage search engines

- Pick your default search engine other than Conduit Search. Also, be sure to click on the X button next to Conduit in order to remove it from the list
Remove Conduit Search virus from Internet Explorer
- Go to Tools -> Manage add-ons and choose Enable or Disable Add-ons
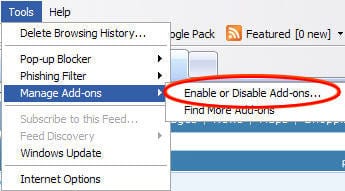
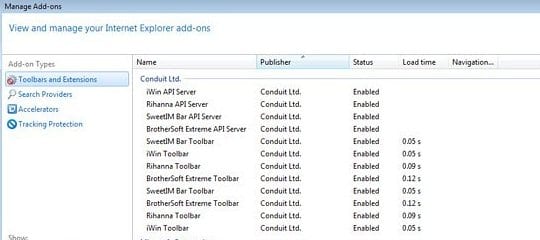
- Select Toolbars and Extensions and locate all entries by Conduit
- Highlight each one and click the Disable button for all these entries
- Click on Search Providers in the left-hand section of the Manage add-ons window. Choose your preferred search provider from the list and click Set as default
- Highlight Conduit Search on the list of search providers and click Remove at the bottom of the interface
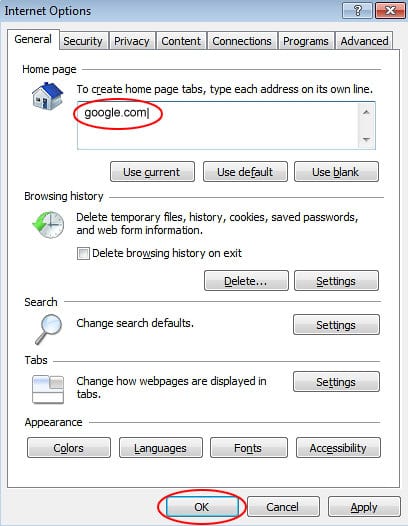
- Now proceed to Tools –> Internet Options, and select General tab
- Set a preferred value of your homepage and OK to save the changes.
(Source: How to remove Conduit Search (search.conduit.com) virus)
Double-check
Scan your system with Bitdefender, the Privacy PC Gold Award winner in Internet security suites category, to make sure all registry entries and junk files added by Conduit Search hijacker have been cleaned up. This step will help you ascertain that no remainders of the infection are still there in case you missed something or if the adware has restored some of its components after manual removal.






























This download ia handled by cnet which will infect you with the conduit virus – you can keep it – i’ll stick with Malwarebytes
When you download from CNET it gives you the option to use their downloader, OR, download it directly. ALWAYS download it directly to get JUST the program you are asking for.
Watch for a program in your “Add/Remove Programs” Control Panel, called “Search Protect”. I had this one. My PC had a fresh OS install and a fresh FIREFOX install, and no software that came form an unofficial source. I still got CONDUIT in under 3 days.
Also, do not trust the official DIVX player and codex fully anymore. Use caution. Many “free” projects that are strapped for money, use items like CONDUIT and ASK as a way to get cash. They will include CONDUIT in their product (often with an “opt out”). Never fully trust any product install that includes ASK or CONDUIT in their install wizard choices. There is a large chance that you will wind up with ASK or CONDUIT even after saying *NO* to it.
You will often find CONDUIT installed in :
“Program Files\Conduit”
“Program Files\Search Protect”
“Search Protect”
“Program Files\Search Protect\Main\bin\CltMngSvc.exe
is the application used by Conduit to continuously update your browser, so that you can’t get rid of the search setting and new tab setting (the come back as soon as you get rid of them).
However it is also often bundled into browser addons. There are many browser addons that are used as trojans for CONDUIT and ASK (and other annoying malware).
JRT.EXE found references to CONDUIT on one of our PCs in these FIREFOX addon files :
**** Successfully deleted: [File] C:\Documents and Settings\[MYUSERNAME]\Application Data\mozilla\firefox\profiles\fulw3yrc.default\extensions\firefox1@myibay.com.xpi
This is an auction snipe ADDON for FIREFOX, associated with “https://www.myibidder.com/”
**** Successfully deleted: [Folder] C:\Documents and Settings\[MYUSERNAME]\Application Data\mozilla\firefox\profiles\fulw3yrc.default\smartbar
This is supposed ot be a smart searching tool for comparing answers from various search engines. Nobody in the house ever installed it, and it has conduit in it (yet there it was on the machine). It was probably a part of a different ADDON install, and we will never know which one.
JRT.EXE also found these things to delete:
Successfully deleted: [Folder] “C:\Documents and Settings\[MYUSERNAME]\Local Settings\Application Data\searchprotect”
Successfully deleted: [Folder] “C:\Program Files\searchprotect”
Successfully deleted: [File] C:\Documents and Settings\[MYUSERNAME]\Application Data\mozilla\firefox\profiles\fulw3yrc.default\extensions\firefox1@myibay.com.xpi
Successfully deleted: [Folder] C:\Documents and Settings\[MYUSERNAME]\Application Data\mozilla\firefox\profiles\fulw3yrc.default\smartbar
Successfully deleted the following from C:\Documents and Settings\\[MYUSERNAME]\Application Data\mozilla\firefox\profiles\fulw3yrc.default\prefs.js
The really interesting thing about this entry ( “C:\Program Files\searchprotect”), is that I LOOKED for all variations of this directory name. I could not see it in explorer even after telling it to show me all hidden files. That never bodes well. I will now need to run all my antivirus software (AVG, MALWAREBYTES, etc), and watch the “CBL” for any entries for a week or so (to make sure I do not have a rootkit too).
and then run “scf /scannow” and reinstall my service packs, in case anything ELSE was compromised.
Ken,
Thanks a lot for these well-grounded observations! Pretty sure some users can benefit from this info in terms of preventing the infection from getting through.