
Taking the floor at Hack In Paris 2012 event, F-Secure’s CRO Mikko Hypponen depicts the global threatscape and speaks in detail about known groups of attackers.
 My name is Mikko Hypponen, and we will be speaking about the big picture, speaking about why we are still having all these problems, how come we can’t solve these issues, how come we can’t understand the enemy better, how come after 20 years, or, actually, now 21 years of working in this industry, I’m today busier than ever before.
My name is Mikko Hypponen, and we will be speaking about the big picture, speaking about why we are still having all these problems, how come we can’t solve these issues, how come we can’t understand the enemy better, how come after 20 years, or, actually, now 21 years of working in this industry, I’m today busier than ever before.
When I started analyzing viruses in 1991, it felt like it was gonna pass, it felt like, you know, we’re gonna get rid of these problems, we’re gonna fix our systems. At the time, the viruses that I was analyzing were viruses like Stoned and Jerusalem and so on, actually there was a Stoned version called Stoned Flame, which I just remembered, which is interesting because Flame, of course, is a name for another malware, which we are all excited about, I’m sure. And there was a virus called Stoned Flame in around 1992. And back then they were always infecting these 8-bit or 16-bit operating systems: Apple II’s, MS-DOS and so on. And these systems were very simple, very rudimentary, and it seemed obvious that we would be able to fix these systems and eventually we would have better systems, better secured, and this wouldn’t be a problem.
And then we got 32-bit operating systems, 64-bit operating systems, and we’re still here, we’re still finding malware today, we’re still finding vulnerabilities, we’re still finding exploits. And people keep asking me about how come we can’t fix this. Especially people who are financial people, managers, who don’t really understand why we have vulnerabilities. Like, why can’t we get rid of vulnerabilities? And the way I typically explain it to them is that, well, these vulnerabilities are just bugs; they’re just bugs, problems. People write these programs and people make mistakes. And of course these people remember that bugs used to mean that your system crashed or your program crashed, or your computer crashed. They remember using Microsoft Office, let’s say, Microsoft Word with Windows 3, and it would crash, and they would lose their document. That’s what bugs used to mean.
And then along came this Internet thingy and this web thingy, and today the very same bugs, very-very similar bugs don’t just mean that your application crashes and you lose your document or your computer crashes, and you have to reboot. Now, because we are online, those very same bugs mean that potentially the system could be taken over. And you can see sort of a light bulb going off on top of their head: oh, so it’s not just human problem, it’s the coders making mistakes, and we’ll never be able to fix the coders.
But we are seeing some improvement, and the one that I’d like to highlight is Apple. Now, we all know OS X has its issues; in fact it now has more malware than ever before. But let’s look at iOS: our iPhones, iPads, iPods.
iPhone will be 5 years old next week. 5 years, one of the most visible devices on the planet. 5 years, during which time it’s been one of the most popular smartphones on the planet. Right now Apple iPhones are #3 after Symbian-based devices and Android-based devices, or actually I should say Android-based devices and Symbian-based devices when you look at smartphones globally. So there’s no lack of these devices, and lots and lots of people have been looking at them trying to figure out ways to own them.
Yet, 5 years later the amount of real in-the-wild malware for iPhone is 0. Not a single one. Yes, we’ve seen proof of concepts; yes, we’ve seen Charlie Miller’s demos – that’s not a real in-the-wild malware; yes, we’ve seen FlexiSpy; yes, we’ve seen malware for jailbroken iPhones, but those are for jailbroken iPhones. For real, unmodified iPhones, 5 years have gone by – and nothing has happened, and that is a great achievement we really should give credit to Apple for a job well done.

And this, of course, has a lot to do with the App Store model, a lot to do with the restrictions they have built in place – golden handcuffs, you might say. But the fact remains: they are without malware. It’s not gonna last forever, but that’s the situation right now.
So who’s this guy (on the image)? Einstein, Albert Einstein. It’s a great photo, he’s having fun with his bicycle, and there’s something blowing up in the background. And I wanted to bring this image here to get some perspective of the long run: what’s really happening in our world. Because I claim nuclear physics lost its innocence in 1945. That’s when we, the mankind, used it as a weapon, that’s when we blew up bombs.

And I claim that computer science lost its innocence in 2009 – that’s Stuxnet. That’s when Operation Stuxnet started late 2008-early 2009, with U.S. President George W. Bush signing a cyber attack program against the nuclear program of Iran.
So there is some perspective for you. We have attacks like Stuxnet, like Duqu, like Flame – attacks launched by governments, militaries and intelligence agencies. And we sort of take this now for granted, cause we’ve been speaking about these problems for the last 3 years, and I’ll speak a little more about them as well, and we’ll have a presentation about Stuxnet later today, which is great.
But just imagine, if somebody would had told you 10 years ago that in 10 years we would for real see cases where governments are writing malware to attack other governments; governments are writing malware to attack their own citizens, and here I’m especially looking at the Germans using R2D2 to spy on their own people, as well as the totalitarian states in the Middle East; that governments would be moving most of their espionage operations from the real world to the online world with APTs and what have you; and that for real governments would be attacking the nuclear systems of another government with malware.
10 years ago if somebody would have told you this, would you have believed it? I wouldn’t. I would have told you that, you know, that’s not gonna happen, that’s a movie plot, that’s a Hollywood story, that’s “Die Hard 4”. And yet, that’s exactly what is happening right now for real. There’s a lot of talk about cyber wars, cyber warfare, cyber arms race. Of course we don’t have a cyber war, because wars are fought between people and nobody has announced a war between different countries, but definitely there is something big going on. But this is, of course, not the full picture. Not nearly all the problems are like this. In fact, the most likely, mundane problem you’re gonna run into is the attacks launched by the criminals, the ones who want to make money.

And I strongly believe that if we want to have any hope at all in defending against these attacks, we first have to understand the enemy, or the enemies. We have to understand who’s doing these attacks. We have to understand what they want, and we have to understand why they’re doing these attacks, because we have completely different attackers. So the way I like to group different attackers is based on their motives, like what makes them tick. And that brings us 3 main groups, and yes, there are some other fringe groups, but the big split is between criminals, hacktivists and governments.
I did a study on, for example, the level of skill of extremists, like terrorist groups, real terrorists like Al-Qaeda and guys like that. I researched this earlier this year, and as a result of that research I’m not including them here; they potentially could be the fourth group, but not yet. Their skills are in the hands of very few individuals with those groups, and they’re really of no danger at this very moment as far as I can see from cyber terrorism. But eventually it could become the fourth group, and of course we have some smaller groups as well. But the big split is, first of all, criminals, the biggest group, the most likely one to hit you; second of all, hacktivists; third of all, governments.
So what’s the motive? Well, for criminals it’s very easy – it’s money. And everybody understands that as a motive. Money makes the world go around; money makes people do whatever; and if you can’t become rich by writing viruses, well, somebody’s gonna do it, right? And many people are doing it. And this is what makes hacktivists different. Movements like Anonymous – they are not doing their attacks to become rich. They are not looking for money. That’s the difference. They want to do something else – they want to send a message, they want to protest, or they just do it for the lulz.
And we have cases where hacktivists were breaking into places trying to send a message or trying to protest, and then they stumble upon something valuable, and then they become greedy, and then they start stealing for their own benefit. In that case we simply move them from the group of hacktivists to the group of criminals: now they’ve just became criminals, they’re no longer hacktivists.
And companies get targeted because they do stupid stuff. Most of the cases where organizations and governments have been targeted with Low Orbit Ion Cannon attacks, or targeted with hacks by movements like Anonymous, they were basically asking for it. Let me give just one example. Let’s compare Sony to Apple. I already gave nice words about Apple and I’m not an Apple fanboy by any means, but let’s compare what happened when George Hotz hacked Sony and when Comex hacked Apple; and here I don’t mean hacked into, I mean hacked systems built by them. George Hotz wanted to run his own programs on his very own PlayStation 3, so he rooted his PS3 so he could run his own program. What did Sony do? Sony sued him. What happened? People got angry for a very good reason, and as an end result Sony was hacked, the last time I looked, 37 times, right? And then the very same thing: Comex wanted to run his own programs on his own iPhone, so he jailbroke his iPhone. What did Apple do? They didn’t sue him; instead, they hired him. Comex is now working for Apple. Good move, Apple has not been hacked 37 times – instead, Comex is now on their payroll, which means he’s no longer making new versions of his jailbreaks and he’s now inside Apple telling the Apple people how to fix these things, how to make it harder to break the security models of Apple. Good move!
And then we have the third group, the governments, which is completely different. Now you can see how it’s hopeless to even try to defend against these attacks with the same models, because we have completely different attackers, completely different motives. The things you do to try to secure your systems against a criminal attacker are completely different from the ones you try to do if you want to defend against the governmental attacker. Plus, criminals want to target pretty much anybody, they just want money. Governments are not gonna target you unless you’re interesting. The Flame virus is not gonna hit you if you are a normal private citizen, it’s not gonna hit your company if you’re a local pizza place. You don’t have to worry about Stuxnet or Flame ever, because you’re not interesting.
You do have to worry about them if you are a government employee for a Middle Eastern government or if you work for the nuclear program of Iran. That’s completely different.

So let me give you a couple of examples of what’s happening in the criminal world. The mechanisms these guys use to make money – well, we started from the botnets which were used to send spam, then we got into credit card theft, most of these stolen with keyloggers from infected Windows computers, then we got into banking Trojans which will inject extra transactions from an infected Windows computer while you’re doing banking. And I keep repeating Windows because almost all of these are Windows computer issues.
That’s Mr. Ivan Maksakov in the white jacket (photo on the top) in the courthouse of a small city in Southeastern Russia with 2 of his partners in crime after running denial-of-service networks with botnets they’ve built to ask for ransom from companies whose websites they were taking down. Here is one of the guys behind the Koobface worm against Facebook platform (see image in the middle). This is the man named Igor (the bottom image), arrested a couple of months ago in Moscow for running the Carberp operation.

And this is Vladimir Tsastsin from the city of Tartu in Estonia. Tartu is the second largest city in Estonia. We first noticed Vladimir when he was running this company in around 2005-2006. He was running a domain registrar called “EstDomains” and a hosting company called “Esthost”, and an Internet operator. And this was a criminal Internet operator run by criminals for the criminals.
So he was, for example, providing bulletproof hosting and domain registration services where, if you were a criminal and you needed to have a website, for example, to have exploits to own people, or you wanted to have a website so that you could sell stolen credit cards and bank accounts – you know, criminal stuff, then you would register your domain and you would host with Vladimir.
And he would guarantee that you will stay online. If there were complaints about your website sent by CERTs, or sent by security companies, or even by authorities, he wouldn’t shut you down, he would only increase your billing, right? So the more stuff you did, the more you generated complaints, the more you had to pay. But if you kept paying, you stayed online. Very clever. He ended up selling around 265,000 domain names, which were basically all sold to online criminals. Actually, if you will look at Estonian newspapers of that time, this was one of the top 100 fastest growing IT companies in Estonia, and number 1 company on the list is the company called “Rove Digital OU” which is run by Vladimir. It’s really easy to grow really fast if your business is cybercrime.

But this did end when in December this bus parked outside of the street address Lau 6, Tartu, in Estonia, which was the headquarters for Rove company Vladimir was running. This bus is the forensics bus of the central criminal police of Estonia, and this is the Estonian police carrying out a router, which was the router for the operation we now know as “DNSChanger”, aka “Operation Ghost Click”. This is the reason why in 2 and a half weeks on the 9th of July about 100,000 computers around the world will go dark because the DNSChanger, the DNS infrastructure will be shut down because of the FBI court order which has kept them running the operation even after this operation was shut down. The court order will expire and the DNS network for these infected machines will shut down. It’s right now being run by Paul Vixie from ISC. He’s going to switch off the router, and these machines will go offline.
Another example I wanted to highlight is that there is quite a bit of these guys operating surprisingly out in the open. Yes, sure, some of them go to the deep web, to DOT Onion sites in the TOR network, or to IP2 Web, or to Free Net, but many of them are in completely open forums, in IRCs, in web chats and in YouTube. And here’s this one guy called Gwapo. Let me run a video that he has on his site: “Hello hackers, I am promoting Gwapo’s professional DDoS service. We are here to provide you a cheap professional DDoS service. We have been running this service on hack forums for months and serving a few huge companies outside of hack forums. We DDoS huge companies’ websites to small personal websites, to private game servers. Our prices are based on how huge and protected the website or server is. We are open through short to long-term jobs as we are capable of handling the jobs for days, weeks and months.”
So if you’re interested in the service of shutting down somebody else’s website, the URL is DDoSservice.com. And I found this channel had, like, 4 videos, a couple of these ads, and then there was this one video where Gwapo himself, as far as we can tell, is counting his proceeds from his criminal online operations. And those are hundred dollar bills. So it looks like a lot of money, but we have to remember that the value of the U.S. dollar has been going down, so, actually, it isn’t that much. It’s like 50 Euros, I think…

One problem in particular, which has been growing just over the last months are ransom Trojans. And ransom Trojans are, from the point of view of the victim, a really shitty problem, because if you get hit by credit card theft, it’s fairly transient, you will notice that there were extra charges on your credit card bill, and then you just call the bank or you call the credit card company and you will complain, and they will refund you. Or if you get hit by a banking Trojan, especially for home users, the banks will refund you, because they don’t want people moving away from online banking back to real-world banking – that just won’t work anymore.
But ransom Trojans are a different thing. Rransom Trojans will directly, permanently hurt the end user. Ransom Trojans, like most of today’s Windows malware, are being distributed through exploit kits like “Blackhole”.
“Blackhole”, manufactured and sold by Russians, going by the range of $2000 right now, is a turnkey solution. You buy the kit, you hack a website – SQL injection, PHP holes, what have you; and then you drop Blackhole onto that website, and there you go. Now anybody who visits that website gets a perfectly normal website, it looks and operates normally, but they get series of exploits launched at them, and these exploits try to find a way in. They iterate through your operating systems, through your browsers, through your plug-ins, through you add-ons, and if you have anything which is unpatched or out of date, then they’ll launch an exploit against that.
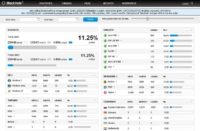
What you see here is the admin interface for Blackhole (see image); this is what the administrator, or the criminal sees: the statistics on who has been visiting the website, with what operating system and how many of them were infected. The one thing that I find especially interesting in this user interface for the criminals is that they have enough guys buying Blackhole and using it for criminal purposes that it’s actually worth their while to run ads on the interface which is only seen by the criminals.
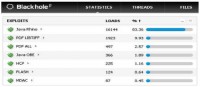
So they have an ad network built into Blackhole, where they can show ads for the guys who are running it for criminal purposes. So this is a typical interface, this was found from a server that was running in Denmark, and as you can see from the statistics here, most of the visitors on this Danish website were infected because they had an out-of-date version of Java. 83% of the infected users were running Java, then an out-of-date Adobe PDF Reader plug-in for Adobe Reader 8 or Adobe Reader 9. Adobe Reader 10 is actually much better here. Or an outdated version of Flash. But Java continues to be one of the main mechanisms people get infected on their Windows computers, and is now increasing also on Mac OS X computers, where Java exploits are already becoming a bigger problem.
So, what to do? I always say: “Friends don’t let friends run Java. Get rid of Java!” That’s what I recommend. I got rid of Java almost 3 years ago and I haven’t looked back. Now there are some caveats here. I know some of you have to run Java applications. That’s ok. I’m talking about Java applets; in fact, I’m talking about the Java plug-in in the browser. Drop the plug-in from the browser and you won’t miss it; or if you miss it (I know some online banks that run Java, or there are some internal applications that require Java) – alright, then have a separate browser just for that. Have, I don’t know, Firefox which has the Java plug-in, and you only use it for the sites which need Java, the 2 or 3 sites that do. And for everything else you use another browser.
So which browser to use? Depends.

If we look at how big percentage of Chrome users get owned, just looking at the real statistics from an interface of Blackhole – you can see that Chrome in practice, in the real world is actually much more secure than Firefox or IE. And this is probably one of the reasons why Chrome is the most common browser on the planet. If it’s not yet, it’s gonna be very soon, which is great, because IE was the number 1 browser for almost 15 years.
The downside of course is that Chrome is done by Google, and by using Chrome you are selling your soul to Google, and that is a bad thing. Google is the Big Brother and there’s not much we can do about it, cause it’s really hard to try to avoid Google. I know, I’ve tried, it’s really hard to stay away, because the services are great.
Just stop and think about it for a moment. Think about Google. Think about their infrastructure. Think about their data centers. We run significant data centers ourselves for F-Secure; we have data centers around the world because we process somewhere in the range of 70,000-100,000 sample submissions every day, and processing here means we do cross-referencing, we run them, we throw them in the sandnets, we execute them, we scan them with all possible antivirus scanners on the planet – so, intensive stuff. We have sizeable infrastructure. But that’s nothing when you compare it to the infrastructure of Google. Just think about the search engine, think about Google Maps, think about YouTube. Just for a moment think about YouTube. I once took the time to start going through the DNS namespace of Youtube.com, and I found somewhere in the range of 80,000 hosts. Most of them cache servers in their namespace. That is just a ridiculous amount of hardware to run YouTube, and that’s just one of their services. So obviously it’s a very-very-very expensive operation to run the data centers for Google.
So how much do the Google services cost? How much do you pay? How much do you pay for google.com, or YouTube, or Google Maps? Nothing, it’s free. That’s an interesting combination of a very expensive service to run, which is completely free, and then you look at Google’s profits, and their profits are billions every quarter. And that’s a funny combination: a very expensive service to run, which is free and very profitable, which sort of explains to us just how valuable profiling us is.
And you could say exactly the same things about Facebook. And it’s sort of funny that 10 years ago we were worried about Microsoft. We were worried about Microsoft 10 years ago. Microsoft was the Big Brother and we couldn’t trust Microsoft, and Microsoft was the evil thing. I don’t think anybody is worried about Microsoft anymore, right? It’s Google and Facebook we should be worried about today.
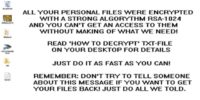
So you get hit by Blackhole, your Windows computer is owned, you boot up Windows, and the next time you boot it up, it boots up but your wallpaper has been changed.
Your wallpaper in Windows has been changed to a wallpaper which explains to you that all your personal files have been encrypted with RSA-1024 with a unique key, and this includes all of your documents, all of your files, all of your images. And if you want to get your files back, please read the “how to decrypt.txt”.
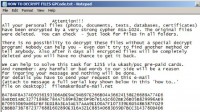
And when you open up “how to decrypt.txt” it explains in detail that they went through your local hard drives, they went through the shares, they went through the network and found all .doc, .xls, .ppt, .pdf, .jpg and .txt files and they’ve encrypted them. You can’t access your files anymore. And it’s all true, that’s exactly what they’ve done. And they’ve implemented RSA-1024 correctly, there are no crypto vulnerabilities we could find. And then they explain that if you want to get your files back, please pay $125 by contacting filemaker@safe-mail.net and sending this unique key generated from the encryption key on your computer. And when you contact them and you email them, they’re very responsive, you send them $125 over the Ukash mechanism; they will send you back a program which will decrypt your files for real. So at least these guys are honest criminals, right..?
And that’s the reason why we haven’t shut down the email address. Normally, we would shut down an address like this, addresses used by criminals. We haven’t. This address still works today. Why? Because we know there are victims out there who have to be able to reach out to these guys so that they can pay them to get their files back. And as much as I hate the idea of paying these clowns, it’s still the better option out of losing your files. We’ve had people contact us who lost their email history – no backups; they lost their holiday pictures – no backups, they’ve had their company infected, encrypting local area network, and the backups are from last month. And these guys would have been happy to pay much more than $125.
And of course the solution here is backups, and running something that would actually block this from infecting your system. But you can see how it’s different from banking Trojans or credit card theft, where you basically get the money back if you just complain about it. Here, you lost your files.
But this is an extreme case, this is called GPCode. This is very blatant, it actually tells you: “We are the bad guys, we took over your computer, you have to pay us”. There are other similar ransom Trojans that are much more clever on how they play with the user. For example, you boot up an infected Windows computer and it boots up, but then it stops just before explorer comes to the page, and instead of actually being able to access your computer, you get prompted by “Copyright violation alert”: “copyrighted content detected”.
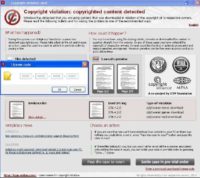
It says that Windows has detected that the content you’re using was downloaded in violation of copyright, so you’re now being sued by “Motion Picture Association of America” and RIAA, and the “Copyright Alliance”. And they have a lawsuit against you, there is a PDF file which has your information, evidence list – they list all the .mp3 files you have on your hard drive, all the movies, all the torrents, your IP history, your type of violation. And you can sort of see how people are feeling the steam in their heart: “Oh, shit, I do have some .mp3 files on my hard drive”. And you have only 2 actions: you can either pass the case to court, so you can fight this in court; or you can press this “Settle case in pre-trial order” button, which basically means you can pay and get a license for your .mp3s and movies with the credit card.
And no, this isn’t really the MPAA or the RIAA, or the “Copyright Alliance”. But you can see why people fall for this, because they know these copyright agencies are playing really hardball with their tactics, so it’s plausible, but it actually isn’t real.
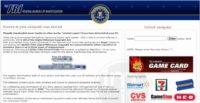
And the last example: you boot up your computer, it won’t start up, just like with the previous Trojan. It stops in the middle of the boot, and then you get prompted by the FBI that they have found porn, child porn, zoophile and child abuse images on your hard drive, and your computer has been used to send out spam with terrorist motives. To unlock the computer you have to pay a fine – $100 (read Reveton Trojan – FBI ransomware).

And the interesting thing here is that if you take the very same computer out of the United States and you bring it, for example, to Germany, and you boot it up again with a German IP, then it’s “auf Deutsch”: “Bundespolizei, Achtung, Achtung…” And the price just went up from €100 to Ein Hundert Euro. In fact, you keep taking the very same computer to different countries and it always changes: there’s Spanish and Swedish, Luxemburg, Italian, Greek, German and French, right here.
And even the Finnish version, they have a version targeting us, Finns, there’s only 5 million of us, so we’re not a very big target. And yet they’ve localized it, and their Finnish is great, I mean there’s no typos or anything, they’ve had someone do it professionally. And I have to highlight the fact that as online criminal, if you really want to make 100% sure that the global law enforcement will go hunting after you – this is the way to do it, right? This is the way to make sure all the police will want to find you. And we, by the way, know at least 2 guys, Russians, who are involved in this case, so they will be going down.
Banking Trojans

A couple of words about Banking Trojans and the money mechanisms there. Most of these are being run by Zeus or SpyEye, which has become the leader in the field, and they are being sold online. There’s Gribodemon, or somebody using his nick, at least, who is the guy behind SpyEye, another Russian guy selling SpyEye. The prices are U.S. dollars, or actually Webmoney, but that’s U.S. dollars, so $2000 for the base kit, Firefox injects for another $2000, RBP functionality for $3000, Opera and Chrome formgrabbers for $1000. But all upgrades are free.
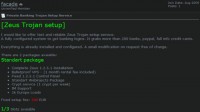
And the compatibility between the configuration file of these banking Trojans is great now. You can use the very same configuration file for Zeus and SpyEye, where you can just configure which bank is being targeted, which has created a market for guys like these. This is Facade selling Zeus Trojan setup. So he’s not selling the Trojan, he’s just selling the customization and tailoring of the Trojan against a specific Bank.
You tell them you have Zeus or you have SpyEye, and you want to target this bank. And they will look at the interface, they will look at the different versions, they will get an account in the bank, they will do online banking, they will tailor the scripts to work with that particular bank to do extra transactions or to change the account numbers on the fly when somebody’s doing banking there from an infected computer. This is 500 Euros, and it comes with full 24-hour support, they will update the scripts if the bank changes the interface and all that – great services, you don’t really have to do anything at all by yourself.

Let’s speak about governmental attacks. Now, like I said in the beginning, it’s quite surprising that it has come to this. Yes, Stuxnet, Flame and Duqu are clear examples of this, but even the cases that we’ve seen elsewhere are pretty remarkable, like the fact that Iran wanted to spy on their own citizens, and they did that in very large scale by their government-owned ISPs which were monitoring inbound and outbound traffic, which led to the situation that dissidents and revolutionary people inside Iran started using encrypted services and started using email providers outside of Iran so that they couldn’t be monitored: services like Hushmail or services like Gmail, because Gmail is always SSL-encrypted and it’s outside of Iran. And once that happens, Iran can’t monitor the traffic of these dissidents, because they can still intercept the traffic, but it’s SSL encrypted. And they can’t set up a fake copy of Gmail inside Iran or a proxy for Gmail inside Iran to trap the traffic because it’s encrypted and the SSL certificate would fail.
And Iran as a country can’t issue a fake certificate for Gmail. Why? Because Iran doesn’t have a CA. Why doesn’t Iran have a certificate authority? Because we, the rest of the world, haven’t trusted them enough to give them a CA. So what did they do? Well, they hacked a CA in the Netherlands – DigiNotar, generated 26 rogue certificates including SSL certificates for gmail.com, hotmail.com, live.com, facebook.com, skype.com, hushmail.com. And now they were able to set a local proxy or a local copy of these services inside Iran, install a fake certificate there, and now it would look perfect, because these were now trusted certificates issued by DigiNotar which were supported by all the browsers in the world. You really wouldn’t be able to tell that it wasn’t really Gmail. You really would have to go and inspect the certificate chain, which very few people do.
In fact, they were able to do this, we think, for at least 2 months, until one guy looked at the certificate chain and started wondering that it’s kind of weird that Google has gotten their certificate from a company in the Netherlands, and that’s how it started unraveling. And by the way, we actually believe that people died in Iran because of this hack. Think about that.

So when Stuxnet was found in 2010, and then when we later learned that it was already started as an operation called “Operation Olympic” in 2008, it was a real game changer. I just finished reading the book “Confront and Conceal”, which is the book by David E. Sanger, editor for “New York Times”, which is the book that breaks the story where U.S. government takes the responsibility for Stuxnet, which is interesting indeed.
U.S. government is now investigating who leaked this information; they are not denying; they’re not saying that it’s not true; they just want to find out who leaked it. And, of course, it wasn’t leaked by accident, it was leaked on purpose. Why? Well, I don’t know; something probably to do with the fact that it’s election year in United States. Call me cynical, but that’s what I believe.

But before we had this for a fact, we already knew that Stuxnet was targeting the Natanz nuclear enrichment lab in Iran. We knew it for a fact. How did we know that? Well, it’s an interesting story. This was uncovered mostly by Ralph Lander who did the analysis of the cascade structure code inside Stuxnet, because Stuxnet only operates if it finds a very specific cascade configuration of high-frequency power converters, and the configuration has to look exactly like this. There has to be 4 high-speed configurators by each other in this very specific structure, sort of like Fibonacci sequence, but not exactly. And if it doesn’t find the sequence, it does nothing.
And this is very unique. I don’t know much about nuclear enrichment centrifuges, but the experts tell me that this is highly unique. There is probably one place in the world that has a setup like this, and that’s what it was looking for. But the question becomes: does Natanz have a cascade of high-frequency power converters spinning centrifuges, or does it not?

So how do we find out? How could we possibly find out if Natanz has a configuration of centrifuges which would look like this? Well, one solution is to go to this website (see image). I don’t know if you visit the website of the Iranian President very often, but if you would, you would find out that President Mahmoud Ahmadinejad has a collection of photos on his page, photos of when he goes and visits places. And in 2008 he visited Natanz. There’s a photo from inside Natanz on the President’s website, a photo where he’s walking by the centrifuges – the centrifuges which were targeted by Stuxnet. And if you look closely, you can notice that indeed they are 4 by each other. That’s interesting, but it doesn’t tell us much yet, because there’s no way to calculate how many there are, and you won’t be able to see the actual cascade structure, because that’s just logical structure, there’s nothing physical to see.

So close, but not exactly what we need. But if you keep looking, you will find this photo (image to the left). And these photos were taken with a Canon EOS-DSLR, which means that they posted the original images, full-resolution images on the website, which means you can actually zoom in. And if you change the coloring values here, that’s actually what’s on the screen, and when you compare this sequence, you’ll see that it’s an exact match to what’s inside Stuxnet. Can you believe that? We know it was Natanz-based, on the photos leaked by the official website of the President of Iran. Quite remarkable. And by the way, the picture is still there, I checked it last week – it’s still there, 4 years later.
I actually went and tried finding out how long it would take me to find a copy of Stuxnet from open sources. It took me 3 minutes to find a copy of Stuxnet, just like that. So the risk of somebody going and actually modifying Stuxnet exists as well. It’s not a very easy thing to modify, it’s not trivial, it’s far from trivial, but obviously it would be easier to modify it than to recreate it from scratch, which brings us to Flame.

I wanted to find some image about flame or fire, or something that would nicely fit into all the talk, and the best image I could find was this. That’s solid advice, keep that in mind. If there’s a fire here, first go to the outside, then tweet, not the other way around.
So I was contacted 3 weeks ago by Iran, I got an email from the Iranian CERT explaining that they had this weird problem and now they’re reaching out to Western security companies. And this is not normal, we don’t normally get emails from Iran, we don’t have much of a customer base there at all. And as we now know, most of the infectious were in Iran or in Sudan, or Syria, or Libya, or other Middle-Eastern countries, and even there the amounts of infections were very small – we’re talking about a few hundred computers in the whole world, very-very targeted. That’s the actual main files we initially found (see image to the top left), we found more since then; it’s sort of like a puzzle where we’re missing some of the pieces.
But what do we know about it? Well, we know it’s highly unique, we know it’s using weird certificates, we know they connect to a series of websites – these are the control servers, and many of these have been named so that if the admin is looking at firewall logs and he sees a machine connecting to nvidiadrivers.info or something like that, they would think it’s just some updates server. It’s not. These are the servers used for traffic by Flame.

So we know it’s huge, but that by itself means nothing, right? It is big, and almost all of it is code, 10 Megabytes or so. It has a keylogger, so it collects your passwords, takes screenshots of your screen – that’s not really unusual; than it has 80 libraries for SSH, SSL and LUA, and SQLite. It has an SQLite database built in, which we have never seen before in any malware, and it uses that to collect documents. It goes through your local hard drive, through your Dropbox shares and through the local area network; and in a typical organization, from the local area network it would find tens of thousands of documents like .doc, .xls, .ppt and AutoCAD files – it also searches for AutoCAD. So it couldn’t possibly steal them all, there’s way too much in a typical network. So instead, it has this system called iFilter, which goes through the files and takes excerpts, like a couple of sentences for each, one sheet from each Excel file, and puts them into a local SQLite database and then sends it out through this nvidiadrivers.info and other services.
And then the attackers can look at the data which was collected, and pinpoint: that is interesting, take this file and that file; collect more files like this. It’s sort of a back and forth service, very interesting.
It also looks through your .jpeg files and gets the GPS coordinates form every single .jpeg file on your hard drive and in the network, so it knows where the people are moving and where they are taking photos. Then it sees if there are any phones paired or bluetoothed to the infected Windows computer. If there is a phone, it will connect to the phone over Bluetooth (it supports iPhone, Android and Nokia), and then it collects the address book from the phone over Bluetooth, puts it into the local SQLite database and sends it out.
And it’s able to send out information even if it’s a highly secured environment and there is no Internet connectivity. It does this by infecting USB sticks that are used in the computers, and copying the SQLite database on those USB sticks. So when that USB stick is taken out from the computer and somebody brings it home or takes it to a customer and puts it into a computer which does have Internet connectivity, then it’s going to send out the information, and even better – it gets back the instructions from the operators and puts them back on the USB sticks which are then brought back to the network, so they can still pinpoint the data collection even if there’s still no Internet connectivity, even if it’s a high-security, let’s say, military network.
Now, we know it’s connected to Stuxnet, because one sample of Stuxnet from 2009 has one module which is from Flame, so we know it’s the same guys, which means we know it’s the Americans, maybe with the Israelis. And then we learned that it replicated within the local area network by spoofing Microsoft Updates. It does this by repurposing a Microsoft Terminal Server License certificate, which would be enough to get it working under XP, but not enough to get it working under Vista and Windows 7.
So they actually took the certificate, dropped some critical extensions from this certificate, which means the certificate was now invalid, it didn’t match the certificate linked back to Microsoft root, so they forged it by giving it the same MD5 hash as the original certificate, which is impossible, except it isn’t if you do the MD5 hash collision, and MD5 hash collisions are a known attack, except they didn’t use the known attack, they came up with a completely new novel way of doing it, which had never been seen before.
And if you look at the mailing list of cryptographic experts, they’re also excited: “Oh my God, somebody found this really cool way, this is going to advance our science by years, it’s excellent!” And you’re sort of wondering who in the world has expertise like this. And even if they came up with a novel way of doing this MD5 hash collision, they still would require a supercomputer to actually do it, and they would still have to do it with a time window of 1 millisecond.

So I’ll just summarize that by pinpointing this press release from June, 11th, that’s 2 weeks ago. This is Northrop Grumman, one of the largest defense contractors in the world; I think the second largest in the United States.
These guys: Northrop Grumman, Booz Allen Hamilton, Boeing, SAIC – they all work heavily with the U.S. government, with the U.S. military, with the U.S. intelligence. And this press release from June, 11th mentions that they’ve just been awarded a multimillion dollar contract for cyber security services with an organization called Maryland Procurement Office.
Well, I’ve never heard of this organization before. Maryland Procurement Office, they procure stuff in Maryland. I wonder who these guys are for real. Googling them gives us their address. If you take a closer look where exactly that is, you’ll see that Maryland Procurement Office shares the office with NSA.
So I’ll repeat: nuclear physics lost its innocence in 1945, computer science lost its innocence 3 years ago.
Thank you very much!




























