
 Kaspersky Lab’s Senior Malware Analyst Denis Maslennikov speaks at RSA Conference about the mobile side of the Russian cybercrime. Maslennikov outlines the prevalent techniques applied for scamming users, describing modifications of SMS Trojans and explaining how they work.
Kaspersky Lab’s Senior Malware Analyst Denis Maslennikov speaks at RSA Conference about the mobile side of the Russian cybercrime. Maslennikov outlines the prevalent techniques applied for scamming users, describing modifications of SMS Trojans and explaining how they work.
Hello, my name is Denis Maslennikov, I work for Kaspersky Lab as the Senior Malware Analyst, and today we are going to talk about Russian cybercrime and Russian mobile cybercriminals.
This research demonstrates one really interesting point: Russian mobile cybercriminals are probably the luckiest ones in the world. Why? Well, most people today are not aware of mobile malware, and legislation loopholes really help bad guys take advantage of the laws and profit from illegal activities.
This presentation will cover all aspects of mobile malware evolution and mobile malware industry in Russia. Also, we will estimate the losses caused by mobile malware and try to look into the future with and without various changes.
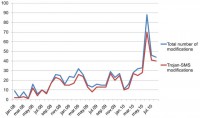
But first of all, let’s start with the evolution of the SMS Trojans and mobile malware industry. The following diagram (see image) represents the ratio between the total number of mobile malware modifications found by Kaspersky Lab and Trojan-SMS modifications.
What is a Trojan-SMS program? It’s a malicious application which was created for sending SMS messages to premium-rate numbers. For example, if the Trojan sends one SMS it can cost you 5 or 10 USD.
And you can see that this behavior of SMS Trojans has been dominating since January 2008 till the current moment.
Cybercriminals understood that the SMS Trojans are the easiest and the most profitable source of income due to direct access to the phone bill and unawareness of people.
Evolution of SMS Trojans
The evolution of SMS Trojans can be divided into three big parts. The first year of Trojan-SMS evolution was characterized by primitive Java 2 Micro Edition (J2ME)1 SMS Trojans. These are primitive applications without any kind of complication or social engineering tricks, or something else.
The second period was characterized not only by J2ME Trojans, they became more advanced, so they started to use some social engineering tricks, some kind of encryption in some cases. And also, we started to discover Symbian and Windows Mobile malicious applications.
And the last one, the third period which still continues can also be characterized by, again, advanced Java 2 Micro Edition Trojans and complex Symbian and Windows Mobile Trojans.
I will describe all these three steps now.
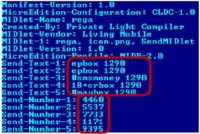
Let’s start with the primitive. Malware family named ‘Konov’ was one of the first widespread SMS Trojans. It can be characterized by very small size from 1 to 8 Kb. There was no encryption, no social engineering tricks. And all the information which is required for SMS sending was stored in the manifest file. So you can see there are 5 premium-rate numbers and there are 5 SMS texts.
This Trojan was mostly spread in the Russian social network named ‘Vkontakte’ (in contact). Sometimes, people receive different spam messages in social networks, and in this case there were spam messages which asked the users to click the link and go to a website telling them that if they clicked another link and downloaded special software for mobile phone, they would be granted 500 Rubles (15 USD) bonus. But in fact, this message won’t give you any kind of bonus but will only send expensive SMS messages.

This Trojan was really primitive. And the next one named ‘VScreener’ demonstrates how cybercriminals started to create more sophisticated malicious applications. This malware poses itself as a faulty video player. And this player must be ‘tuned’ by the user. The tuning can be done by pressing the left soft key.
There is one aspect in J2ME SMS Trojans – the majority of modern simple mobile phones do support J2ME technology, but this technology is a bit restricted. So for example, if the application is trying to connect to a URL or send an SMS message, or dial a number – the Java machine will notify the user by showing a message on the screen that for example: “This application wants to send an SMS message, would you allow it or not?” The user must then press ‘Yes’ or ‘No’.
This malicious application sends these expensive SMS messages during the ‘tuning’. So imagine the situation when the user is pressing the left soft key, he starts to see some kind of picture of a very cute lady, and at the same time this Trojan will try to send SMS messages, which the user will confirm by left soft key quick pressing. And besides, this premium rate number and the SMS text are stored in load.bin file and were encrypted with ADD and ‘0xA’ key.
So, we talked about J2ME Trojans, now let’s move on to smartphone malicious applications. I think some of you may remember the story of Symbian signed malware, the first example of which was a worm named ‘Yxe’. It became the first application of this kind which was signed by a valid certificate, and the Lopsoy Trojan was also signed by a valid certificate.
During the research, I found the website of the probable author, and his article which fully describes the logic of how this Trojan works. You know, a few days after adding the detection of this Trojan, I found the Twitter account of this probable Trojan author, where he wrote: “Because of this article they’re saying I’m a virus writer. Even though anyone could see that my goal was only to warn people.” But I don’t think that it is a good idea to warn people by creating malicious applications.
Lopsoy became the first SMS Trojan which connects to the author’s URL in order to download the information. In this case, this Trojan was trying to download an SMS text and premium-rate number from the website. So for example, if cell mobile operators noticed that this SMS text and this premium rate number were used illegally – they could block it, but in this case the author can rent another premium-rate number and another SMS text, update the information on the website and the Trojan will continue its work.
Another example of how this Trojan was spreading – we found a lot of smartphone games websites which were able to define the User Agent of the browser the user was surfing from. And for example, if the user was surfing the Internet with his mobile phone, they would display on the screen of the mobile phone the optimized page of the website.
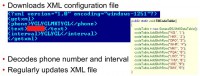
Another example of a Windows Mobile Trojan was also able to connect to the URL and download information for SMS sending. But in our case it was trying to download an XML2 file, and some parts of this XML file were encrypted. You can see some strange letters between the tags ‘phone’ and ‘interval’. Well, inside the body of the Trojan we found the following table (see image), and this table was used by the Trojan in order to decrypt and retrieve the information about the premium-rate number and the interval between each message.
This Trojan was also spread through different fake websites, but in this case these were PDA application websites. So for instance, the user was searching for some kind of free software for his Windows Mobile smartphone, and somehow he visited the following website. In this case, he will download a KB archive with the application inside, maybe legal, but at the same time there will be an executable file with the Trojan body in the KB archive.
The root of all evil
So, I’ve tried to briefly describe the evolution with specific examples, and now let’s go to the root of all this evil and see how Russian mobile cybercriminals actually work.
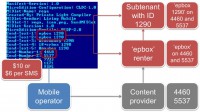
The main question of the presentation is still unanswered: why are Russian mobile cybercriminals the happiest ones in the world? Let’s go back to the Konov manifest file (see image). You can see premium-rate numbers and SMS texts there. 10 or 6 dollars per SMS is a normal situation. And, you know, in Russia mobile operators usually act as owners of the premium-rate number. Well, there are such organizations like content providers. They were created to provide rental services for as many people and as many companies as possible.
So, what about ‘epbox 1290’? We can divide this, let’s say, prefix, or SMS text into 2 parts: Renter and Subtenant. The main renter leases ‘epbox’ prefix on the premium-rate numbers 4460 or 5537 from content provider and offers subtenancy services for ‘epbox 1290’ renter.
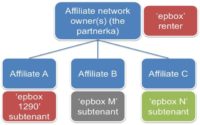
But who are ‘epbox’ and ‘epbox 1290’ renters? Our ‘epbox’ renter is an affiliate network owner, and ‘epbox 1290’ Renter is one of the many affiliates. Beside ‘epbox 1290’ renter, we can also find ‘epbox M’ subtenant or ‘epbox N’ subtenant – they can also participate in this affiliate network.
And for example, ‘epbox N’ subtenant can offer legal services. For example, the user sends an SMS with the text ‘epbox N’ to the premium-rate number 4460 – and he will receive, for example, a link to download a legal game. ‘epbox M’ subtenant acts like this: if the user sends an SMS with the following text he will receive, say, a link to a .JPEG file. And ‘epbox 1290’ is our mobile cybercriminal.

So the root of all evil is here – it’s the affiliate network registration form (see image). For example, if I have very nice photos of San Francisco or New York, or Moscow, I can sell them. I can register with the affiliate network and try to sell my photos with the help of premium-rate SMS messages.
If I want to register there I must provide the following information: my name, my email, my website URL where I will post my pictures, website name, and Webmoney account. Webmoney is a Russian electronic money payment system; for instance, if I sell 10 pictures at 10 dollars each, the money will go to my Webmoney account.
In other words, after the registration I will receive my affiliate ID like ‘epbox 1290’ or ‘epbox M’, or something else. And I think you have already noticed that I provide no sensitive data at all. I don’t need to send them the scan of my passport or confirm my identity, or something else. It means that I can act absolutely anonymously. So, that’s the root of all the evil. In Russia it is possible to rent special text or prefix on premium-rate number absolutely anonymously.
The biggest part of the affiliate websites are porn sites. Porn was always very close to malware in general. This is an example of a typical affiliate website (see image). You can see several porn thumbnails which offer users to download 3gp or mp4 porn videos.
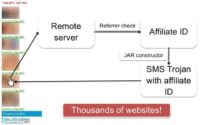
But what is going to happen in reality if the user clicks on one of these links? The user will be redirected to a remote server which checks the referrer and correlates it with the affiliate ID. After that, a JAR1 constructor which works on the web server will generate an SMS Trojan with the affiliate ID, and the web server will return this SMS Trojan as a porn video to the user. Unfortunately there are thousands of such websites on the web, and almost all of them do spread SMS Trojans that way.
How much do they make?
And now, let’s answer the second main question: how much do they make? But first of all we must see how the revenue is shared between persons and organizations in the following scheme.
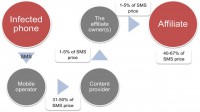
So, let’s say we have an infected phone, and the phone is infected by SMS Trojan, and this SMS Trojan sends an SMS. Mobile operator will take from 31% to 50% of the cost of the SMS. Content provider will take from 1% to 5% of the cost of the SMS. And finally, the affiliate network owner will take from 1% to 5% of the cost of the SMS. And in the end, the affiliate who actually created this SMS Trojan and spread it will earn from 40% to 67% of the cost of the SMS. So it means if an SMS costs, say, 10 dollars, the affiliate will earn from 4 to 7 dollars from each SMS message.

Some time ago, I found a very interesting screenshot which opened very interesting secret information from one of the largest mobile affiliate networks. I don’t know how but the information was available in public sources. And the screenshot shows us that this affiliate network was fined by content provider (see image). And the fine was equal to 25% of the weekly revenue of the affiliate network: 1.6 million rubles, or 53,000 dollars. We can estimate the weekly income: it equals to approximately 212,000 dollars, and the monthly income equals to 850,000 dollars. I told you earlier that affiliates will earn at least 40% of the cost of the SMS. What does it mean? It means that Perlag affiliates cause serious financial damage, which is equal to at least 1.2 million dollars per month.
This turned out to be a ‘death penalty’ for Perlag – some time after this screenshot became available, this affiliate network was closed and gone.
And now, I would like to summarize everything we talked about, and let’s see today’s situation in general. Today we have a lot of SMS Trojans for Java 2 Micro Edition platform, for Symbian platform, for Windows Mobile platform, for Android platform, and some of them became really complicated. Cybercriminals are organized now, and such organizations as affiliate networks help them in their so called ‘e-business’. And unfortunately all of them are still unpunished, so that is probably why they feel safe and continue their activities.
I think that you would also agree that all antivirus vendors have problems with detecting Java 2 Micro Edition Trojans on simple mobile phones. In fact, we cannot detect them because it is impossible to create an mobile antivirus for Java 2 Micro Edition platform and simple cell phones.
Today and tomorrow
And today, only Russia and some CIS2 countries are targeted by these activities and by SMS Trojans. The only reason of that is legislation loopholes, which allows cybercriminals to rent premium-rate numbers absolutely anonymously. If the situation is not changed, we will be seeing absolutely the same thing.
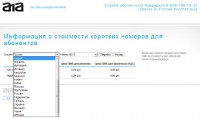
The potential targets of mobile cybercrime are a questionable issue. Why? Not so long ago, on one of the affiliate websites I found the following information about the premium-rate numbers and the cost of each SMS to premium-rate numbers (see screenshot). We can find there some Russian premium-rate numbers, Ukrainian, Kazakhstani, and even Latvian, Lithuanian, Estonian, and maybe even German premium-rate numbers.
And one more content provider allows us to rent U.S. premium-rate numbers from Russia absolutely anonymously. So, we have already seen other types of malware which uses U.S. premium-rate numbers, and this malware was created by Russian cybercriminals and was spread in the U.S. Fortunately, we have not seen mobile malware, but in some cases it is only a matter of time.
So, what should we do in this situation? I think, except detecting mobile malware and providing antivirus database updates, we must surely force some legislation changes in certain countries. In my opinion, mobile cybercriminals are the same cybercriminals – and they must also be punished. And surely, we must educate users and provide more user awareness of this problem.
And again, as a summary: SMS Trojans target mostly single users, not enterprises surely. Social engineering is exploited to a large extent by cybercriminals. In most cases, threats are really easy to remove – sometimes you can go to the phone menu and simply press ‘Delete’ button. And one very positive note is that mobile operators always refund the money if malicious SMS messages were sent. So for example, if you were infected by an SMS Trojan and you somehow noticed that, and the SMS messages were sent, you should write a complaint letter to the mobile operator, and you will get your money back.




























