
 F-Secure’s Chief Research Officer Mikko Hypponen speaks on telephone fraud schemes leading to money theft.
F-Secure’s Chief Research Officer Mikko Hypponen speaks on telephone fraud schemes leading to money theft.
Hi everybody, my name is Mikko Hypponen, and we’ll be spending the next 30 minutes in this turbo talk, talking about ‘You will be billed 90,000 dollars for this call’
So, let me just outline real quick about the company I represent. F-Secure has 850 people in 22 countries. We’ve been around for 22 years, researching viruses. The last 10 of those, one of our focus areas has been focusing on, on mobile malware, mobile attacks of various kinds. So we’ve analyzed viruses on Symbian, on Iphone, on Blackberries, on Android and so on. So that’s one of the things we do, although most of our revenues come from working with ISPs (Internet service providers) to protect traditional Windows computers.
 But I really want to start by asking you a question: how many of you had one of these? (See image) Yes, they were great devices, U.S. Robotics. Funny thing, when I tried to find its image, I found it from U.S. Robotics website. U.S. Robotics is still around. They’re still around today. They have 120 employees, which was a bit of a surprise to me, sort of disappeared but…
But I really want to start by asking you a question: how many of you had one of these? (See image) Yes, they were great devices, U.S. Robotics. Funny thing, when I tried to find its image, I found it from U.S. Robotics website. U.S. Robotics is still around. They’re still around today. They have 120 employees, which was a bit of a surprise to me, sort of disappeared but…
So, that’s the modem, that’s how we used to get online. In fact, we all used their modems. In fact, some of our computers still do. Fact is my thin pad, which is like 3 years old, still has a modem slot for a telephone line. Of course it’s never connected to a telephone line anymore, there is a modem.
And back then, when everybody used to have a modem and it used to be connected to a telephone line, we had a problem. Particularly a problem what used to be known as Dialers, or more specifically Porn Dialers1. So, Windows Trojans that would infect your computer and then start making phone calls with your modem. And then charge money back to you.
Quite a bit of these were obvious to the user, tailored to the user with the EULA2, that you know, we will show you porn images or porn movies and as we show them to you, we’ll be at the same time making phone calls to a 1-900 number.
And people, of course, ignored that completely because they never read EULAs, especially if they’ve just downloaded an application to look at porn, they’re just gonna ignore that.
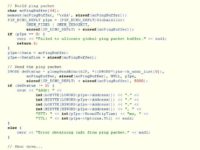
So, in a nutshell, the point of talk is here (Code snippet 1). That’s a code snippet to make a ping, to send one ping packet. Basically this code snippet right here, which is some Linux source code somewhere, creates a connection between two devices, that’s what it does. Right? Very simple.

So, basically, these two things make the same thing: they create a connection between two devices.
However, there’s one crucial difference. When the code from snippet 1 of sending ping packet is executed, no money is being moved. When the code from snippet 2 is executed, this is actually a money transaction. It actually moves money around, because when you make a phone call, you pay for the call.
Now, imagine if traditional virus writers who write Windows viruses today would have such an easy mechanism today to extract money from infected computers. That would be like their red dream. Of course, they don’t have that. So they have to go through these, frankly, very complex mechanisms of extracting money from infected computers. Like dropping a spambot to the infected computer, then sending spam through the infected machine, try to advertise Viagra, then sell Viagra. You know, it’s pretty complicated. Or to drop a keylogger on an infected Windows box. Then wait for the user to go online to make online purchases, get his credit card number, then use his credit card number to make purchases, get yourself laptops, resell them. Again, very complicated. Yet, this is what they are doing. Although this is complicated, they still do this. If they would have a direct mechanism of just extracting money straight off from infected computers, it would be their dream. But they don’t have that. They used to have it 10 years ago when we had modems, they don’t anymore.
So, there’s another problem with these premium rate numbers. Well, there is quite a bit of difference, worldwide, when we look at these premium rate numbers that we can dial, and which actually cost you extra money. Here in USA, these are the 1-900. You go to other countries, you pretty much have this in every single country around the world. In Finland, where I am based, these are the 0-700 numbers and they can charge you anything from 10 cents a minute to 9 dollars a minute or something like that.
Now, 1-900 numbers have several problems from the point of view of the attackers. First of all, you have to have initial investment to get started, you have to actually pay money to subscribe to one of these services that outsource 1-900 phone lines. Typically around 900, maybe 1000 dollars to get started, which is a barrier.
Second problem is that FTC3, who regulates this in USA, makes a measure that there has to be an audio warning or preamble at the beginning of the call, telling you where you’re calling and who runs it, who owns it, and how much you’re gonna pay.
Even more importantly, if you run fraud, for example if you would have a Dialer today that would automatically issue calls to 1-900 number, and would do it completely illegally, without the user knowing. Users would realize, they would see this, they would complain and this would be shut down before any money is moved to the criminal. This has been designed just to prevent fraud like this. You don’t get the money immediately. There’s a 30 day delay before the number owner gets the money out of the calls, which is pretty neat in the preventing fraud like this.
One thing which was a bit of a surprise to me, and I realize this, is that here in USA you can’t call premium rate numbers from a cell phone. You can’t. They only work from land lines. Of cause land lines are going away. Everywhere else, as far as I know, they do work, like local premium rate numbers anywhere in Europe, anywhere in Asia, do work from cell phones. Of course they do. I don’t actually know why you can’t call a 1-900 number here in USA, but you can’t. Which means, if somebody wants to write a smartphone trojan to call premium rate numbers, they can’t use 1-900 number.
And the last barrier is that these numbers are not international. From USA you can’t call a 0-700 premium rate number, in Finland, it will not work. From Finland if I try to call 1-900 number it won’t work. I actually play you an audio clip, what happens when I try to use my phone in Finland to dial one of your numbers: “The call you are attempting to place is not allowed from this line, please dial 611”. It basically says that you just can’t reach this number. The call is not allowed from your area code, basically you can’t do this international.
Alright, so let’s think from the bad part point of view. This doesn’t work if they wanna have premium rate numbers, wanna extract money automatically with malware. They have to do it with some other mechanism than 1-900 numbers.
There is one guy, wrote this posting explaining that he was woken up on Sunday morning at 2:40 AM. He woke up because he was sleeping right next to his phone and the lights on his phone turned on. And he looked at his phone and his phone was making a phone call. Alright? So, he looked at the log and realized that his phone has actually made a number of calls.
So he, he was baffled about this, he made his posting. He listed the numbers that he found from his phone call logs and asked does anybody have any idea what’s going on.
Well, nobody had an idea, no replies. Nothing happened for 5 days. Then 5 days later, suddenly new users started registering on this forum, and started posting replies to this forum. And basically all the replies were along the lines that, you know what, same thing happened on my phone, I’m from Denmark, and same thing happened for my phone, I am from Tokyo.
So people from all over the world, started posting replies on this forum posting. Because what happened is that they had the same thing happening on their phone. They saw from their call logs, the number where the phone had dialed in, of course what they lose if they google for the number. What else do you do? And when you googled for any of these numbers, one hit, one hit only, which was this forum posting. So obviously, all the people who were trying to figure out what’s going on with their phone ended up replying on the same thread.
So then somebody pointed this out to us. And we went to the same forum. We posted there basically, you know, explaining we are F-Secure antivirus company, we work with mobile antivirus for a long time. We’re pretty confident this is a virus or worm or Trojan doing this. And we asked people who were affected by this, to post a list of applications they have installed on their devices.
And all the users who were complaining were running Windows Mobile. Windows mobile 6 or Windows Mobile 6.5 And people posted whatever applications they had installed. And they had different e-mail clients, different calendar applications, different games.
 One thing they all had, one thing what was common in all these devices all over the world, which was doing this, was that they all had this game: ‘3D Anti-terrorist Action’, which is a 3D shooting game, it’s actually a Counter Strike clone.
One thing they all had, one thing what was common in all these devices all over the world, which was doing this, was that they all had this game: ‘3D Anti-terrorist Action’, which is a 3D shooting game, it’s actually a Counter Strike clone.
It’s actually a very good game, very fast, no, very nice game. And it’s made by this Chinese company called ‘Huike’. And ‘Huike’ is a fairly large, OEM game manufacturer writing 3D games. And they’ve done nothing wrong. This is a commercial game, written a year and a half ago, being sold by ‘Huike’ typically for 5 dollars or so.
What happened was that an unknown Russian hacker got this commercial game, cracked it, removed copy protection. Then created a copycat website of ‘Huike’, registering a new domain name that sounded similar, copied the content over and then post himself, that I am the developer of this game. And submitted the cracked version of the game as a free demo to several Windows Mobile download sites around the world. Sites where people can download games for their phones. And it is a good game, and now it was free. And of course these download sites believed that it’s the real deal, it all looked real, right, how would they know that this guy who was coming from this website, isn’t actually the real company.
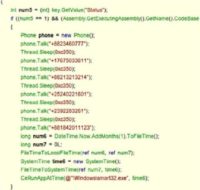
Phone calls to these 8 numbers listed right here. And it waited for 0xc350, that’s 50,000 timer ticks, waited for the call to go on and then it shut down the call and issued another call.
And once it had called all of these numbers, these 8 numbers, then it sleeped for 31 days. After 31 day, it repeated the calls and sleeped for 31 days. That’s what it does.
And when you call these numbers, this will create you around 12 dollars in costs. And the logic in doing this only every 31 days is that most of us have a monthly bill. If you don’t have a prepaid number, then you typically get a monthly bill. If you get an extra 12 dollars international calls in your bill, well some of us will notice, some of us won’t, I wouldn’t notice for example.
I have, you know, so, so much international calls anyway that 12 dollars would easily go through.
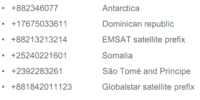 So, what are these numbers? Where was the phone actually calling? Well, it was calling the South God Damn Pole! Yes, it was calling Antarctica, it was calling Dominican Republic, it was calling different satellite providers, it was calling Somalia in Africa, San Tome and Principe, which is a very small island name somewhere outside of Africa on the West cost.
So, what are these numbers? Where was the phone actually calling? Well, it was calling the South God Damn Pole! Yes, it was calling Antarctica, it was calling Dominican Republic, it was calling different satellite providers, it was calling Somalia in Africa, San Tome and Principe, which is a very small island name somewhere outside of Africa on the West cost.
And it’s pretty obvious, that you know, if you call faraway places like these, it’s going to be an expensive call. Everybody understands that. If you’re gonna call the South Pole, it’s gonna cost you money, right?
So, how does the guy get money out of this? That’s the crucial part. How does this actually work, so that the guy running this operation, is able to get money out of it and is able to do it without getting caught, and is able to continue it, although there might be attempts to take down.
And this all done by the fact that these numbers are so called international premium rate numbers, which means they are not premium rate numbers, theу are perfectly, in perfectly normal number space but they are very expensive.
 These fraud phone numbers are built so that they actually fund money back to the person who’s operating the number. And this means, that these numbers will work from anywhere in the world and they will work for cell phones. So if you compare these numbers to the 1-900 numbers here in USA, well, you can call this from USA, you can call from cell phones and they would generate money to the person operating it. They do all the things that you cannot do with 1-900 numbers, and they will work from any country in the world, any phone, anywhere in the world will be able to call these numbers and they will fund money back to the operator.
These fraud phone numbers are built so that they actually fund money back to the person who’s operating the number. And this means, that these numbers will work from anywhere in the world and they will work for cell phones. So if you compare these numbers to the 1-900 numbers here in USA, well, you can call this from USA, you can call from cell phones and they would generate money to the person operating it. They do all the things that you cannot do with 1-900 numbers, and they will work from any country in the world, any phone, anywhere in the world will be able to call these numbers and they will fund money back to the operator.
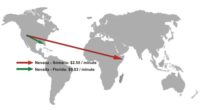
Now, the trick is, when you call one of the fraud numbers, for example the number going to Somalia, it actually won’t go to Somalia. The call gets disconnected, for example in Florida or Canada or Australia or the Netherlands. And they keep the rest of the money. And calling Florida from Nevada costs you a couple of cents, which means they get to keep over 2 dollars a minute of extra.
And this is what’s known as Short Stopping or Long Lining, illegal call terminations, they are terminating the call before it actually reaches the place. So, when your phone was infected by 3D Anti-Terrorist Trojan, when your phone was calling the South Pole, it actually didn’t call the South Pole. But you paid for the call to South Pole, and someone else, the virus writer got the money instead.
 So, how do you actually create a number like this? How do you create a number that uses these call terminations or shortstopping? Well, you just go online and you search for this, and you’ll find several operators that are selling numbers exactly like these: international premium rate numbers in Zaire, in Madagascar, in Cameroon, in Niger and elsewhere.
So, how do you actually create a number like this? How do you create a number that uses these call terminations or shortstopping? Well, you just go online and you search for this, and you’ll find several operators that are selling numbers exactly like these: international premium rate numbers in Zaire, in Madagascar, in Cameroon, in Niger and elsewhere.
This is World Premium Telecom, they are selling numbers in Latvia, Belarus, Sierra Leone, Lithuania, Kosovo, Myanmar, Georgia, and that’s Georgia the country, not the state. Another one of these operators is selling numbers in, yes, Afghanistan, Albania, again Antarctica.
And these are all based on the same idea that the calls are terminated before they reach their actual destination and the money is funded back. And these provide daily payments or weekly payments. You don’t have to wait for 30 days. Fraud checking that’s being done by these guys, well I don’t really know, but I am guessing it’s not nearly as string as that would be by a real phone operator. And there is no legislation, there is no FTC governance. It’s really hard to actually figure out where these guys operate themselves.
 And if you just think about this, here is the list of one of these operators, they are selling, look at this, they are selling numbers in North, God damn, Korea, right there. You can buy a North Korean number, +358 goes to North Korea, which of course never goes to Korea, but can be used for exactly this. And now, I’m sure there is some logical perfectly fine explanation why somebody would like to buy a number like this, which would make sense, which wouldn’t be illegal phishing in anyway. I am sure there is some explanation, but I can’t figure it out. I can’t imagine a non-shady reason why somebody would like to have a phone number in North Korea and get extra money out whenever somebody calls that number.
And if you just think about this, here is the list of one of these operators, they are selling, look at this, they are selling numbers in North, God damn, Korea, right there. You can buy a North Korean number, +358 goes to North Korea, which of course never goes to Korea, but can be used for exactly this. And now, I’m sure there is some logical perfectly fine explanation why somebody would like to buy a number like this, which would make sense, which wouldn’t be illegal phishing in anyway. I am sure there is some explanation, but I can’t figure it out. I can’t imagine a non-shady reason why somebody would like to have a phone number in North Korea and get extra money out whenever somebody calls that number.
If you can figure it out you tell me. And these operators, like I said, these are fairly easy to find, again, I am sure there are logical reasons why they keep doing this and why this is not really being regulated.
Some of them seem to be very touchy about this subject. I’ve made a short blog post about this when I was researching background for this talk, mentioning a couple of these operators and I immediately started getting threats from one of these operators. So, they seem to be a bit touchy about the fact that if somebody starts looking at their operations. What I got were just nasty emails, nobody was trying to beat me up.
 And there are a lot of problems if you have an international phone number like these, like, for example, numbers used by 3D Anti-Terrorist Trojan, I wasn’t able to figure out who operated those numbers, like which of these companies was running those numbers. There is no way to do that. No way that I am aware of. Which means, there is no way you can actually complain. How do you get such a number shut down if you can’t figure out who is the operator behind?
And there are a lot of problems if you have an international phone number like these, like, for example, numbers used by 3D Anti-Terrorist Trojan, I wasn’t able to figure out who operated those numbers, like which of these companies was running those numbers. There is no way to do that. No way that I am aware of. Which means, there is no way you can actually complain. How do you get such a number shut down if you can’t figure out who is the operator behind?
These are pretty nasty problems. Those numbers, those 8 numbers used by 3D Anti-Terrorist Trojan are now shut down, they don’t work anymore. I don’t know how and who did it, because we sure didn’t do it. We tried, tried to get them down but couldn’t find any party where to report them.
 And of course, eventually, virus writers will realize, that it is easier to make money by infecting phones than it is by infecting computers. Because you have this built-in billing mechanism on phones that you do not have in computers. And also, let’s remember that there are more phones on this planet than computers. But of course, this hasn’t happened yet. And my numbers, of what the difference of the amount of malware on Windows side, and what the amount of malware on phone side is nicely illustrated by these figures, showing the difference between the size of Sun and size of Earth.
And of course, eventually, virus writers will realize, that it is easier to make money by infecting phones than it is by infecting computers. Because you have this built-in billing mechanism on phones that you do not have in computers. And also, let’s remember that there are more phones on this planet than computers. But of course, this hasn’t happened yet. And my numbers, of what the difference of the amount of malware on Windows side, and what the amount of malware on phone side is nicely illustrated by these figures, showing the difference between the size of Sun and size of Earth.
So, there really is a world of difference right now. Really, not very likely today to get infected by mobile phone attack, not even the kind of stuff that the 3D Anti-Terrorist Trojan has done. Yes, there were global infections but even then the number were polling hundreds more than, or not, maybe in thousands, but not more than that. So, the problem really isn’t there. It could be but it isn’t.
Yes there is tons of like traditional hacking going on, which uses premium rate numbers to get money out of it, including hacking VoIP1 systems and Asterisk2 systems and others. What I am talking right here is the difference between PC and mobile malware, using mobile malware to issue calls straight from the smartphone, and that difference is that big. Five hundred mobile malware, of which only a handful tries to do premium rate text messages or premium rate calls.
So, this problem doesn’t exist yet. We only have a handful of examples.
 My theory on why the bad guys are doing more of these already is in the operating system market shares. Low hanging fruit is Windows, and it is Windows XP. Most of the malware today have been written for Windows, specifically written for the Windows XP.
My theory on why the bad guys are doing more of these already is in the operating system market shares. Low hanging fruit is Windows, and it is Windows XP. Most of the malware today have been written for Windows, specifically written for the Windows XP.
Because Windows XP is 9 years old, almost everybody is running it as ‘Administrator’. It has by far the biggest market share, 62% of the computers on this planet are running Windows XP, 15% – Vista, 12% – Windows 7 (See image). That’s the latest figures I could find.
Which means, why on Earth would the attackers even consider any other platform right now than Windows XP, where they already have existing attacks, existing malware frameworks that work and bring great results? They are getting great money out of current attacks. They do not have to move anywhere. And they won’t. Of course, eventually, this will change. In two years, Windows XP will no longer be the most common operating system. It will be replaced by Windows 7. And of course Windows 7, sure, can get infected but it is harder. You know, there’s a bigger barrier again, and it’s perfectly possible when the current virus writer gangs realize that they have to start putting in more efforts, they have to start pointing their software from Windows XP to somewhere else, to Windows 7, or maybe, maybe some of them look around and realize that actually targeting phones might be a better idea.
We’ll see, but right now, I am not really expecting huge amount of rush from the current virus writers, from their current platforms to mobile, because it works so well for them already right now. Why would they move? Such an easy target.
 So, what should you do to protect against attacks like these? A scenario where your customers or your users are hit by piece of malware, and which uses their smart phones to issue calls to faraway places.
So, what should you do to protect against attacks like these? A scenario where your customers or your users are hit by piece of malware, and which uses their smart phones to issue calls to faraway places.
Well, the usual, look down the devices, prevent the installation of 3rd party applications, setup policies, tell your users not to install games, especially not the ‘3D Anti-terrorist game’. And of course you can buy expensive security products on your device. For example we have a solution for this which we’d be happy to sell to you – it’s called F-Secure Mobile Security. But, frankly, right now most of our customers who buy security products for their smartphones, aren’t actually buying it to prevent mobile from viruses. They are more looking into other features that security products provide like: antitheft, online backup, remote lock, remote write – that kind of features. Because that’s something you need already today, while antivirus and mobile firewall is something you would need more in the future.
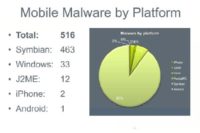 If you look at mobile malware by platform (See image), it looks like this: 516 mobile phone attacks have been seen so far. Majority, by far, targeting Symbian, Symbian like for example my Nokia phone right here. Why Symbian? Because Symbian is the king of the hill. Symbian is the guerilla. They by far, have the biggest market share of smartphone operating systems. They are three times ahead of Blackberry or Iphone or Android or Windows Mobile. Of course, here in USA nobody runs Symbian, but you go anywhere and it is by far the most common platform. So, most of the attackers are writing for the biggest operating system. Yes, there are some attacks for others but frankly very little, so that’s the distribution of malware today.
If you look at mobile malware by platform (See image), it looks like this: 516 mobile phone attacks have been seen so far. Majority, by far, targeting Symbian, Symbian like for example my Nokia phone right here. Why Symbian? Because Symbian is the king of the hill. Symbian is the guerilla. They by far, have the biggest market share of smartphone operating systems. They are three times ahead of Blackberry or Iphone or Android or Windows Mobile. Of course, here in USA nobody runs Symbian, but you go anywhere and it is by far the most common platform. So, most of the attackers are writing for the biggest operating system. Yes, there are some attacks for others but frankly very little, so that’s the distribution of malware today.
We have seen, for example a remote spy program is available for Blackberry. So, it’s not a virus or worm, but it’s a spying tool that can be installed on a Blackberry and then to be used remotely: listen all the phone calls, see the location of the phone, turn on the microphone remotely and listen what’s being discussed. That would be a typical example of Blackberry malware but outside of that, there are very few examples.
So, that’s what I wanted to share with you today. Thank you very much.




























