Investigative reporter Brian Krebs and cybersecurity expert Lance James taking the floor at Black Hat to dissect the infrastructure of DDoS-for-hire industry.
 Brian Krebs: Hey everyone! My name is Brian Krebs, I’m an independent investigative reporter at Krebsonsecurity.com. I think this is my fifth or sixth Black Hat – I can’t remember at this point – as a journalist. I’m kind of used to being where you guys are, in the audience and heckling the speakers, so it’s kind of a thrill to be up here. Hopefully you’ll be kind to me, and I guess, karmically, it’s okay if you’re not. I’ve got a lot of stuff to cover in a very short period of time, and my buddy Lance James here, who I’m sure is no stranger to a lot of you in the room, is going to be bringing up the second part of the talk, talking about some of the more technical aspects. So, if I blaze through this stuff real quickly I think we’re going to have hopefully a little time at the end for Q&A. But if you guys think I talk fast, wait till Lance gets up here – holy crap, he makes me look like I’m slow in the brain.
Brian Krebs: Hey everyone! My name is Brian Krebs, I’m an independent investigative reporter at Krebsonsecurity.com. I think this is my fifth or sixth Black Hat – I can’t remember at this point – as a journalist. I’m kind of used to being where you guys are, in the audience and heckling the speakers, so it’s kind of a thrill to be up here. Hopefully you’ll be kind to me, and I guess, karmically, it’s okay if you’re not. I’ve got a lot of stuff to cover in a very short period of time, and my buddy Lance James here, who I’m sure is no stranger to a lot of you in the room, is going to be bringing up the second part of the talk, talking about some of the more technical aspects. So, if I blaze through this stuff real quickly I think we’re going to have hopefully a little time at the end for Q&A. But if you guys think I talk fast, wait till Lance gets up here – holy crap, he makes me look like I’m slow in the brain.
This talk is about a pretty active area of the underground, or semi-underground, or whatever you want to call it – it’s about a proliferation of DDoS-for-hire sites that are basically springing up left and right. For the most part, they are run by teenagers or young men here in the United States who, frankly, aren’t doing a whole lot to hide their identities, or even trying that much, it seems. I want to state upfront what this talk is not about: it’s not about mysterious organized Russian cybercriminal hacker gangs or anything near that level of scariness; although the script kiddies that are running these sites do certain things to try to make themselves seem a little more leet, like, you know, their DDoS-for-hire sites could be .su or .ru domain names – that makes them a little more leet than they are.

What we’re dealing with here in this talk is, for the most part, admittedly a bunch of script kiddies, or what my friend and collaborator Allison Nixon likes to call the ‘noob persistent threat (NPT)’. Actually, most of these guys are so noobish that calling them script kiddies is probably an insult to the script kiddies of old. I mean, at least those guys could open up a command line and do their script from the command line.
That being said, I think that there’s a general tendency to dismiss the activities of script kiddies, because maybe they are not leet enough or scary enough to help companies sell security products. But I think it’s a mistake to discount these guys because some of the stuff they’re coming up with is pretty ingenious stuff. One of the hack forums I’m going to talk about today – a lot of these guys are selling their services on there, but they are selling things like remote access Trojans, they are selling things like botnet code, and this stuff is showing up in some really scary places, like the DarkComet RAT showing up in the Syrian government to target activists.
So, just a little bit of background on the DDoS-for-hire industry: this is not a new industry, I’m sure most of you understand that. Just about everyone you ask who monitors DDoS attacks these days are noticing they are not only becoming more prevalent and more damaging, but a lot more powerful. More importantly, while the targets of these DDoS attacks have traditionally been sort of the e-commerce sites, the banks, etc. – these days, if it has an IP address, somebody is going to packet it, they are going to get attacked at some point.

Some of the increase that we’re seeing on the DDoS attacks is, no doubt, automated build-your-own DDoS kits like BlackEnergy, Dirt Jumper, Darkness which make it stupid easy to build your own DDoS army. But even if you can’t be bothered to do this, to build your own DDoS, there have always been services that you can hire in the underground and go to in order to take somebody offline.

These commercial DDoS services typically have a few qualities that really limit their client base. #1 – a lot of them don’t have websites. Some guy who has put up an ad like this (see left-hand image) – you have to know where on the forum to find the guy, you have to chat him up in ICQ or Jabber, and if you don’t speak Russian it might not be the easiest thing to do. And at the end of the day, if you want to pay for one of these attacks, you’re not going to use your credit card, you’re going to use something like WebMoney. For the average Western guy who wants to take a website offline, he’s not going to have a WebMoney account or want to deal with that whole thing.

What’s interesting about these booter services I’m going to talk about today is they don’t have any of those shortcomings. They call them ‘stressers’, they call them ‘stress testing sites’, because nobody uses it to take any other site offline except their own… And they are designed for use by U.S. citizens. I didn’t make this up (see right-hand image). These booter services cost pennies per attack, so some of the other DDoS-for-hire sites can cost 5-50 bucks a day. That may sound like not a lot of money, but for the guys who really want to pay for this stuff it tends to be.
You can go to these sites and create an account, and once you funded it you just put in the IP address or the hostname of the site you want to attack – and you’re off to the races. And the best part is there’s no need to deal with WebMoney and all these other virtual currencies, Bitcoin and crap like that. You can pay for it with PayPal. That means you can just launch DDoS attacks with your credit card.
So, how did I get interested in the ‘noob persistent threat’, these DDoS services? Well, it started with a story that I wrote last fall about one booter service called absoBoot (see left-hand image). absoBoot, like all of these booter services, is advertised and chiefly marketed in a ‘noobtacular’ forum called Hack Forums. The story that I wrote about absoBoot noted that the guy who was running it is also running a similar service called TWBooter. It was created by a guy on Hack Forums named Orgy, a very big time seller there.
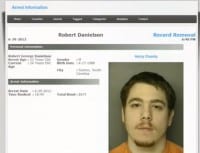
The story noted that Orgy hadn’t been super-careful with safeguarding the privacy of his Whois information (see right-hand image). He really hadn’t even tried that hard to obfuscate who he was. It was all run by a 23-year-old kid from North Carolina named Robert Danielson. He’d been busted a few times for different things, as you can see here. I think the latest one was robbing a local policeman’s house of his firearms – again, noobtacular… But anytime you write about these guys on Hack Forums, they get their dander up, they get a little pissed off because they are very proud of the forum, they’ve got a lot tied up into it, a lot of investing. And they start, you know, lashing out at you a little bit.

So, right after I wrote about this I started getting some anonymous threats, people sending me emails going: “Hey Krebs, watch your back – somebody is gonna swat your ass!” You guys know what swatting is? It’s when somebody calls in to your local police and pretends to be you and says there’s a hostage situation going on in your house and asks to send police right away. And usually, if you don’t answer the door they kick in your door, and all kinds of bad things can ensue after that. Well, I really didn’t want this to happen to me, so I reached out to my local police and I said: “Can you please send an officer out here, I want to file a police report?” And a guy came by, he was really nice; he had never heard of swatting before. But I said: “Look, if you get a call from somebody pretending to be me telling you about a hostage situation in my house – here’s my cell phone. Just freakin’ call me, okay? Don’t kick in my door.” They don’t reimburse you for that, by the way.

I didn’t get swatted, at least not then. Fast forward to March of this year, I wrote a story about a service in the underground that was being used to pull credit reports on celebrities and public figures. The guy that did this – this is his site (see right-hand image) called Exposed.su – basically, he started posting the name, address, Social Security Number, mother’s maiden name, previous addresses, all this stuff – pretty much anything you can find in a credit report. He started posting it all on the site. He did this for Arnold Schwarzenegger, Kanye West, and a whole bunch of other guys. When he got bored with that, he started doing public figures like the First Lady of the United States, the Director of the FBI, the Director of the CIA. And a lot of people were like: “Holy crap! If they can get this information on the Director of the FBI, they can get it on anybody.”
The story that I wrote said that now we’re talking about the right question here, because for every single one of you who lives in the United States, that information is for sale: for 5 or 10 bucks you can get it all. And I said: “This is one of the sites where you can get this information.” It was a site called ssndob.ru (see left-hand image). It’s no longer there, it’s at a different place. This is actually the account of the guy that set up Exposed.su. You can see he’s looking up Sarah Palin, Britney Spears and Tom Cruise; he actually looked up my information as well.

So I wrote about this and I said: “Look, this is out there. This is probably how he’s doing it.” I didn’t know at the time that it was. And the next day I get an interesting email from my hosting provider (see right-hand image), and they’re like: “Hey Krebs, FYI, we got a letter, looks like it came from the FBI but it’s kind of not really all that official-looking. But they said you’re hosting illegal content on your site, so we had to take down your site.” I also got the same email forwarded to me from Prolexic, which is a DDoS mitigation service that actually protects my site from attacks which are happening more often than not; my site has been under attack most of the day today.

So, they sent me this notice and said: “Just FYI.” I thought this was kind of interesting. And they said: “Oh, by the way, your site is under attack again, it’s down. We’re gonna fix that, no problem.” About an hour later, I’m vacuuming the foyer because I’m expecting my mom and my aunt to come over for dinner. It was about 5 o’clock. And I notice there’s a whole bunch of tape on the wall, on the door, around the door. I’d put some Christmas lights up and I decided – it’s March, I’m going to take this stuff down. So I’m taking the tape up and I notice it goes on the outside. So I open up the door and, sure enough, there’s this entire SWAT team out in front of my house.

They were pointing at me pistols, shotguns, and they’re like: “Put your hands up! Walk backwards!” So I had this tape ball in my hand, and he’s like: “What’s in your hand?! Drop it! Drop it!” I’m trying to get this freakin’ tape ball off my hand and I’m like: “Holy crap! Don’t shoot me!” Well, the first thing I said was: “You guys are being tricked; I told you this was gonna happen.” They put me in handcuffs, they brought me on the street, and eventually this guy who looks like he’s in charge shows up and he goes: “Are you the guy that filed a police report about swatting?” I go: “Yeah, that’s me, jackass!” He goes: “We did call you. We called your cell phone.” And they did, I checked it later – they called it. The phone was upstairs as I was vacuuming.

I decided this whole experience getting hit with a kinetic and a cyber attack at the same time is just too good not to write about. I started asking around about what might have been responsible for the DDoS, and it turns out that the booter site that was used in this attack – and Lance is going to talk a little more about this in a bit – Booter.tw, just had its SQL database hacked (see right-hand image). And whoever did it – I don’t really know, but I’m eternally grateful – basically put it on the booter’s own site for download from there; which I though was wonderful, so I included the link to that in my story.
But the database showed that the same account at this booter service that was used to attack my site actually was used to knock Ars Technica offline for about an hour. My buddy Dan Goodin at Ars Technica had called me after I tweeted about the SWAT. I’m like: “I just got swatted…” He goes: “Wtf?!” So I did some digging on who was responsible for calling the SWAT to my house, and that led to a 20-year-old kid in Milford, Connecticut (see left-hand image). He used a nickname ‘phobia’. This kid denied doing my SWAT, but strangely enough, he admitted to being the guy that hijacked the iCloud account of Mat Honan at Wired.com. I’ll come back to that in a few minutes at the end of my talk, but if you haven’t read this story it’s epic. I know this guy’s name, his dad gets on the phone and he goes: “Hey, my son didn’t say he hacked Mat Honan’s account. He said he knew Mat Honan.”
Anyway, after spotlighting what was going on with Booter.tw I started taking a harder look at the booters that were popping up on Hack Forums. And it wasn’t hard to learn, for example, that one booter that had thousands of paying customers was the AsylumStresser.com (see right-hand image). And somehow in the course of my reporting on this guy, the database for AsylumStresser got leaked as well. Not really sure how that happened.
It pointed to the owner as a 17-year-old kid Honor Roll student from Chicago. And the database (see left-hand image) showed that AsylumStresser had more than 30,000 paying customers, registered users; and that it brought in more than $34,000 in subscription payments via PayPal. This kid set up his business very much like legitimate cybercrime business. That doesn’t make any sense. He basically had paid a bunch of guys at bulletproof hosting providers in Romania to power most of his service. Asylum, like most of the booters, markets itself, as I said earlier, like a stress testing service – nobody’s going to attack anything but their own site, right? But all of these booter services include all kinds of ancillary add-on services that let you discover the IP address of people or websites that don’t want to be found. And they all have these disclaimers, like “Hey, this has all been vetted by our lawyers, and we’re not responsible for what you do with our service.”
The next booter that I looked at was Rage Booter. This is by far the most interesting and entertaining one I looked at. The guy who runs it is a young stoner kid from Memphis. His name is Justin Poland. Again, he’s a big time Hack Forums user. I think he’s kind of an idiot – he was not hard to find.
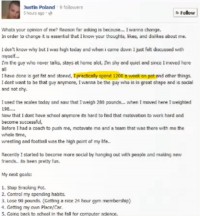
So, he’s on Facebook (see left-hand image), and I’m like: “This is kinda cool; I’m just gonna go ahead and chat this guy up and see if he’ll talk to me if I friend him.” And he did! So we’re chatting on Facebook and I’m reading his post that he’s putting up. He, by his own admission, smokes pretty much all of his income from the booter service, something like $1200 worth of weed a week. I don’t even know how it’s possible to smoke that much weed.
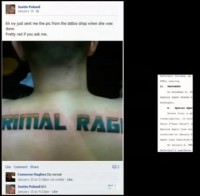
He’s seriously devoted to his site. As you can see from this Facebook picture (see right-hand image), he got it tattooed on the back of him. Tl;dr. Rage Booter’s database also gets popped – again, I’m not really sure how that happened.
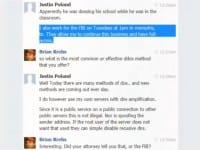
So I start chatting him up (see left-hand image) and I’m like: “Hey Justin, tell me more about your business.” And he’s like: “Oh, look, my service is vetted by lawyers, and everybody’s okay. And by the way, if you have any doubts about the legality of my service, I work at the FBI once a week; I go to the Memphis field office and work at the FBI once a week.” He also said they let him keep his site up as long as he gave them backdoor access to his site.
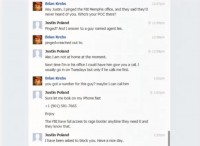
At first I was skeptical, so I came back to him and I said: “Hey Justin, I called the Memphis FBI office and they said they didn’t know anything about you, they don’t know Justin Poland and they have no idea what I’m talking about. Maybe you could give me the name and the number of your handler?” And he did, as you can see here. He said: “Oh, it’s Agent Lies.” And I thought, oh God, seriously – this guy is named Agent Lies? Bullshit.

So I call him up and ‘Agent Lies’ doesn’t want to say who he is, he doesn’t want to confirm or anything like that, but he says: “You need to talk to the guy in charge of the media relations at the Memphis field office. It’s this guy, here’s his number,” and then he hangs up. And two minutes later Justin goes: “I have been asked to block you. Have a nice day.” That’s it. Anyway, I did a little research afterwards because I thought this ‘Agent Lies’ was too much. But it turns out there is a special agent Lies in the Memphis field office (see left-hand image) and he does a lot of cyber cases, so maybe the guy was telling the truth, I really don’t know.
Rage Booter, pretty much like every single one of these booters out there, was hidden behind CloudFlare, and as I’m sure most of you know, this content distribution network, ironically, is used probably most often to keep sites online in face of lots of traffic, particularly DDoS attacks. Apparently, running a DDoS-for-hire service kind of makes you a target for competing DDoS-for-hire services. So, if they’re not behind CloudFlare the whole thing falls apart.
That got me to thinking – if CloudFlare said they wouldn’t be dealing with these guys anymore and they would kick all those booter services off their network, it would be a very good chance that this problem would kind of take care of itself. So I asked CloudFlare about this, and Matthew Prince, the CEO, referred me to a blog post that he’d put up last summer, in which he basically said: “Look, we don’t want to go there. We don’t want to be the arbiter of what kind of content we want to allow on our networks, because this is a slippery slope.”

Allow me to quote from that post (see right-hand image). He basically says: “CloudFlare is firm in our belief that our role is not that of Internet censor. There are tens of thousands of websites currently using CloudFlare’s network. Some of them contain information I find troubling. Such is the nature of a free and open network and, as an organization that aims to make the whole Internet faster and safer, such inherently will be our ongoing struggle. While we will respect the laws of the jurisdictions in which we operate, we do not believe it is our decision to determine what content may and may not be published. That is a slippery slope down which we will not tread.”
Okay, I get this. As a journalist, I’m a big backer and proponent of the First Amendment. I think people should be able to put whatever the hell they want on the Internet, and if it offends you – too bad. But in this case, I think there are two – I don’t know if you could call it conflict of interest – but for me, first of all, the purpose of these booter sites is to take sites offline, basically to stifle speech. And number two, CloudFlare – they’re basically a big DDoS protection, and the fact that they are harboring all these booter services and not really making an effort to get them off their network – it seems like a conflict of interest.

I reached out to PayPal as well, because I sort of thought this was the other way that this booter industry would just fall apart, if these guys weren’t able to take PayPal. And PayPal responded (see right-hand image). They basically said: “Hey, we take security very seriously at PayPal and do not condone the use of our site in the sale or dissemination of tools, which have the sole purpose to attack customers and illegally take down websites.” Oddly enough, I think Rage Booter is still online, it’s still able to accept PayPal payments, as is Booter.tw – the booter services that got me interested in this whole thing in the first place.
Given that a lot of these script kiddies on Hack Forums who are running these booter services are here in the U.S., it might not be unreasonable to expect that at some point – and they have no OPSEC – they’re going to get a visit from the feds or from the local cops. But maybe not, if the Hack Forums that has become the breeding ground for these businesses is actually working with the feds itself.

I discovered something really interesting about the administrator of Hack Forums. He’s a 40-something guy named Jesse Labrocca, he lives right here in Las Vegas actually. In mid-2010, Jesse seemed to be taking steps to clean up Hack Forums (see left-hand image). There were a lot of guys on there that were going: “We’re selling banking Trojans, Zeus botnet stuff, carding, all kinds of things.” And then Jesse said: “You know what? If you guys want to talk about all that stuff, do it somewhere else, you need to get off my site. And by the way, if you really want to do that, we’re creating a new forum for you guys, and if you want to get on just message me for an invite code – and you’ll be good to go.” And he also said: “For all of you Hack Forums members who have VIP status,” which is basically a paid status there, – “Your VIP status will transfer over to this new site.”
Well, that new carding site turned out to be Carderprofit.cc (see right-hand image), which was a fake carding forum set up by the FBI. And here’s where this comes full circle. I’d been kind of sitting on this information up to this talk, but I recently discovered that the kid who swatted me and used Booter.tw to DDoS my site was the same kid who was primarily responsible for building Exposed.su site that was doxing all the celebrities and the public officials.
I mentioned the story of Mat Honan’s epic hack – he did a follow-up not only after that, where he wrote a piece called “Cosmo, the Hacker ‘God’ Who Fell to Earth” (see left-hand image). It was about a 16-year-old kid from Long Beach, CA, who was responsible for a lot of the UG Nazi attacks, the kind of the LulzSec and Anonymous stuff. And he was one of the guys that Phobia I mentioned earlier was very tight with; Phobia – the same guy who acknowledged hacking into Mat Honan’s iCloud account. This 16-year-old kid from Long Beach was among two dozen members of Carderprofit.cc that were arrested last fall for allegedly trading stolen credit card accounts and other data.

Incidentally, those who read the Wired story about this kid Cosmo are going to know that this is the same guy who took credit for hacking into the Gmail accounts of CloudFlare CEO Matthew Prince. And the crazy thing about the CloudFlare hack – I don’t know how many of you remember this – but, basically, Cosmo and his pals mainly used it to redirect 4chan’s DNS to UG Nazi Twitter feed. But they could have done a heck of a lot more damage with that hack.
Now I’m going to ask Lance to come up and bring up the rest of it. Thank you!
Lance James: How is everybody so far? I’m Lance James, some of you know me. I work at Deloitte. Don’t ask, it’s cool. I get to do some fun stuff.

We’re going to kind of go through this story here where I got involved. Krebs and I have been friends for years and have done some crazy cool stuff together. He’s taught me a lot of cool stuff, and I’ve taught him a lot of cool stuff, and we just kind of do cool stuff. So, basically, I’m going to go from the investigatorial perspective from a technical sense. I did this over pretty much, I think, my lunch break in some way although it was a lot of work. But it was fun stuff to me, so I was excited, in a bad way.
So I started looking at things from a psychological profile perspective first and then got into the computer stuff. We, obviously, know he was the target of attack; he provided probable links when I talked to him, related to SSNDOB.ru we saw in that fake FBI letter. Then we started to get it linked together. He had some information that the TWBooter service was being used in this attack.
I started looking at who does this type of stuff – we had swatting, we had DDoS. I’m used to profiling groups, and I have organized crime groups, I have Middle Eastern groups, I’ve got Anonymous and LulzSec chaotic organizations. So I was trying to figure out which group I might be thinking about here, what kind of adversary we’re dealing with. So I broke this down from a simple behavioral profile. The intent is obvious: disrupt Brian all day, make him have a shitty day. Basically, swatting and DDoS are usually fear tactics, really hostile. You know, the guys are sending a clear message how they feel about Brian, basically. They’re clever, tactical, capable. But we saw in the behavior that it’s short-sighted because they forget that Brian is friends with a good amount of information security professionals, and we like him. So one of the things I did was get coordination with some people, and people were ready to go – he’s a big voice for us.
We saw that this kid is short-sighted, like: “What were you thinking? You’re going to get exposed.” I also looked at the history of the arrest records of swatting and DDoS, and you’d see there from 12 to 20 years old. So I know what kind of adversary I’m dealing with, a typical kid hacker with anti-social behavior type mentality.

Let me go into the actual looking at the terms of service (see right-hand image), because I look at things from a legal perspective as well. So, the terms of service are, literally: don’t use this to attack unless it’s your own site, things like that. They have all their plausible deniability, and in my opinion, working in cryptography for years, plausible deniability doesn’t really exist. And these terms of service are on almost every site.
When you look at breaking down the infrastructure, you have three big tiers. Now, even if CloudFlare is in front of it or just the ISP that they’re really hosted at, you don’t see that DDoS traffic going out of there. So the ISPs that are hosting the web service part are not aware of it because it’s not having any traffic going out, it’s just the web. And then they have these backend ISPs that are handling the actual weaponry, they have the proxies and all the stuff that’s actually hitting the servers. So, in a way, there’s no proof; it’s hard to take these things down and it gets a little difficult because you have to bring together an entire case.

Obviously, HackForums.net is a very interesting site. There’re a lot of things that are going on over there. I kind of looked up about these booter services because, honestly, my focus wasn’t in this and I had to catch up. So I started trailing back and I found the TWBooter code leaked in the forums. We seem to see that all these kiddies – just like I’ve seen back in the early days of swatting – they swatted each other first. They weren’t hitting celebrities first, they were hitting each other. It was very much like a gang war.
So I joined the forum with not my real name obviously, grabbed a copy of the code. I did some code research; I’ve gotten pretty good at WebAppSec over years. I perused through the code and found some basic understanding of the web application and file structure. I even set up my own TWBooter locally, because it lets me understand how the system works, what’s available. This comes into some legal exploitation, because that’s important to me; it’s basically what I call ‘inferred access’ – I know there’s a file sitting on there, it may not be advertised that it’s there but it’s readable to me. So I study this code, and unknown files may be known. Incorrect Directory/File Permissions – that’s one thing a kiddie doesn’t know anything about; and publicly accessible files, including maybe Database Export scripts. That’s been kind of a fun thing.

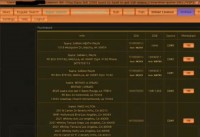
As Brian said, the SQL files keep getting hacked. It was a publicly accessible file when I found it, so I grabbed it. It was sitting on the backup directory of the booter site. I quickly did something so that we could confirm we’re on the right track. We searched for KrebsOnSecurity inside the booter file (see right-hand image); of course we’ve got a hit here, so it’s good for us.

The dates are in Unix format, so this is something where we need to go technical (see left-hand image). I wrote quick conversion code and we started looking at the first date of the DDoS attack based on the story that occurred. And we see it’s Thursday, March 14, 13:13 EDT 2013. I worked with Brian to also work with Prolexic, and we all started looking at the correlation that was matching the time for the attacks that were occurring.

Then I started looking at the SQL database itself and looked at the user IDs and stuff – there’s a table here (see right-hand image) where you can kind of get to learn this stuff. User ID 126 is where we started tracking from.

Then we see this article on Ars Technica the next day, it made big news. And Brian is like: “Oh, shoot! They’re DDoS’ing the site.” Basically, we suspected the same motive – attack all things “Brian Krebs”. This also very much goes back into the psychological profile of “It’s likely a kid” because, again, that’s a very impulsive behavior.

So, one problem is, my booter.sql file does not have historical logs, so we had to make an effort to change that.
So, we got to fear the foo but pity the foobar. I had these logs and did targeted analysis, basically I looked at Arstechnica.com, their IP address. And we have to do a couple of things. Date conversion – guess what? Friday, March 15, 11:54 EDT 2013. Epic fail for the bad guy, or win for us, obviously.
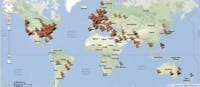
Moving on, I started doing database analysis to get a birds-eye view, diverse activity and stuff. We wanted to look at how many people are on this thing and in what areas they are (see right-hand image). This just gives us an idea of the diversity and the involvement of this service.

I also have general goodies that are actually important. You have server IP addresses, you have CPU that’s being used, attack capabilities, and we have the passwords. I’m going to warn you that the next part with passwords (see image below) could be offensive to some.
I like to learn what’s going on from behind the scenes here. And then we get into following the money. To me, from the forensic view, the closer I get to the adversary is actually where the money is. As much as we bring up PayPal, they do a pretty good job at validating who is on these accounts and stuff. I actually happen to work a lot with the PayPal investigations teams in the background; they won’t necessarily share details with me, but if you notify them they will take action.
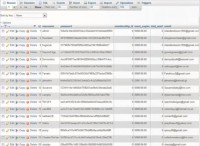
But what’s kind of neat about these booters is, because they use PayPal, we actually see little things like their email address that you’re paying the money to (see left-hand image). In most cases, you’re going to assume that that’s not a stolen email.

But this one is even better, because the actual domain name is the last name of the actual person involved here, so I’m putting it in a higher probability that it’s probably not a hacked Gmail account or anything like that. And the domain name belongs to a guy that looks like this (see right-hand image).
And then we looked into this guy because we did the Whois and we got the information. He’s actually doing a great job of separating himself from the booter service. But what I did find, really coincidentally, is the only thing he’s got on his Google+ site is CloudFlare promotional type of stuff (see right-hand image). Also, what was interesting is that the real person works in InfoSec at a major financial institution, so there is an internal investigation being in progress. And also, when I went through the code, some of the payment process code was in French.

As I was looking into this, I realized that some of the big targets that have been on the news (see right-hand image) were Whitehouse.gov, CIA.gov, Barackobama.com DDoS’es, the FBI.gov; I’m sure I’ve seen a couple of the NSA IPs in there. I saw a lot of big financial institutions in there. There were actually 631 distinct targets in there, some of the personnel obviously. But you get to really map their activity, so I’ve been working on putting together the timeline of this.
I also wanted to get into the actual DDoS TTP’s. There was some leaked source code on Hack Forums as well. When Brian started giving me information on other booter services out there, I started looking at AsylumStresser and a few others. They had funny little vulnerabilities laying around, and I’m not surprised that they’re getting hacked. They also use the same backend code for the weaponization, and I can guarantee that kiddies didn’t write this stuff, it’s probably been around for a while. What’s great about that for us is when you think about it from a holistic perspective you can sit there and write remediation capabilities off the analysis and cover the entire gamut based on the tool.

So, basically, we did some analysis, and here are 8 types of DDoS (see left-hand image). We have the ‘amp.c’, which is a UDP Amplification attack using chargen, basically Port 19. We have ‘arme.c’, which is an Apache Remote Memory Exhaustion; that’s a pretty popular one that has been around for a while. You also have what’s called ‘essyn.c’, which is a standard SYN flooder. We have ‘lag.c’, which is basically same as ‘amp’ but with slight timing differences. We have ‘scloud.c’, which is Skype DDoS based on ‘amp’, so it’s the same code as ‘amp’, only it has a Skype IP resolver using SpeedResolve.com. There’s also ‘slow.c’, the Slowloris attack which ‘RSnake’ invented; that’s one of the popular attacks as well. And then we have the ‘rudy.c’, which is basically ‘R-U-Dead-Yet’ – it’s a long form field submission type of attack. And also we have ‘ghp.c’, which is GET/HEAD/POST Flooder; you saw a few of those when Brian was showing his stuff.

So, we were going through the code and we categorized it (see right-hand image). The ‘amp’, lag and the scloud – you can basically use standard UDP volumetric countermeasures to take care of those. If you have a Prolexic or even standard firewalls, you can handle that in most cases. The ‘arme’ – the Apache Killer Snort Signature will work for that, but you can also do some stuff with range and the bytes. To handle ‘essyn’, you can employ standard countermeasures for SYN. The Slowloris – there are some regex rules on this specific one, where it’s like ‘x’- and then there are 7 random lowercase letters, and then ‘: 1’. ‘rudy’ – on this tool that’s a regex on the default settings which these kids aren’t changing, there’s this thing sitting on these European ISPs just ready to go. Pretty much this whole thing, these booter kits – you can just unzip, install, go. The username equals ‘ZZZZ…’. For the GET/HEAD/POST one, the rule would be to use HTTP authentication or look for missing ‘Accept*’ headers.

We have a new set of lists here (see left-hand image). I checked all of these that are protected behind CloudFlare, so they go with the whole competitive space here. So we have the iDDoS Stresser, Onion Stresser, Quantum Stresser – this Star Wars list could keep going, I think, right from the beginning.
Then I was looking at what’s going on next, and I saw this today (see right-hand image), it was kind of awesome. You’re getting mobile devices fully compatible, HTML5 stuff basically. You don’t really have to go get an app for that, you can be compatible.
I did want to give some thanks out, obviously, to law enforcement, some FBI involvement. Daniel Clemens over there from PacketNinjas has provided a lot of assistance in this. Allison Nixon – she’s been awesome. I want to thank Arbor Networks because they also were involved in some of the analysis stuff I did. Jamie@CloudFlare – she’s actually been cool, so as much as we might seem like we’re coming off CloudFlare for this or that, I’ve had some good luck with CloudFlare in some of the areas, and it’s just going to take coordinative initiative to take all of this stuff down, but they were definitely helpful when I’ve asked. Thanks to my Company for allowing me to do this crazy stuff that they are going “Wow!” Thanks to Mr. Krebs over here just taking the heat for all of this, and you guys here, Prolexic as well, and Black Hat, and anybody I missed.
Question from Matthew Prince: So, Brian, you reached out to me and I actually wrote back to you trying to schedule some time to call, and you never called me. So, where would you draw the line? If someone, let’s say The New York Times put an article up and said: “Here’s how you launch a DDoS attack,” – I know you wouldn’t take that down; if there were merely an advertising site that said: “We offer great DDoS, call this phone number,” – would you knock that offline?
Brian Krebs: I don’t know…
Matthew Prince: So, again, what I’m going to say is these aren’t simple questions, and I’m totally happy to have this discussion. You know, we have 1.5 million customers, among them the Turkish government, the Muslim Brotherhood – organizations that do suppress freedom of speech and cause me great consternation – use us like crazy. And so, I’d love to have this discussion with you and I proposed some times that you could call me, and you never called. That was very sad. And if you’d like to talk, I’d be happy to do this. But it’s not an easy position that we sit at. So, I appreciate this, and this is great work.
Brian Krebs: So, is there any interest in taking down the booter sites?

Matthew Prince: Again, my Ops team would love me if I took all the booter sites off CloudFlare. We hate this. They don’t pay us. If they do pay, they pay with stolen credit cards, so that’s just a disaster. So, you know, what I would love is due process to work its way through. I think it’s really tricky when private organizations act as law enforcement, and so we try to follow what is due process.
Brian Krebs: Have you gotten any requests from law enforcement to take down any booter sites?
Matthew Prince: We’ve gotten two different types of requests. This is something that I would have loved to talk to you about if you’d ever called me. I looked the emails up and I was like: “Did I drop the ball somewhere?” But three emails with specific times, I’m available at any of these times – but who needs to actually ask questions as a journalist? So, we have two issues. Sometimes we have law enforcement issues that ask us to take things down, and we have court orders, too. Strangely – and again, this is the “rock and a hard place” – we sometimes have court orders that order us to not take sites down. For example, the Carderprofit site, the FBI’s site – that was a CloudFlare customer.
Brian Krebs: I understand. So, the answer to the question is No?
Matthew Prince: No, we’ve had court orders and we comply with every court order that we receive unless we feel that it’s truly abusive, and this case is related.
Brian Krebs: Booter-related?
Matthew Prince: Again, what’s a booter and what’s not a booter? There have been some hacking-related sites that we have been asked to take down.
Brian Krebs: Any other hecklers out there? There must be more hecklers, come on!
Question: How long do you estimate it’s going to take those script kiddies to smarten up? Maybe law enforcement should be asked to investigate who’s been doing those things on the Internet?
Brian Krebs: Are you asking about OpSec?
Question follow-up: No, it’s not me and not you. There’s obviously no problem with OpSec there. What I’m trying to say is that they might take it further than just swatting people. You know, we all started as script kiddies.
Brian Krebs: …Like send heroin to your house, something like that?
Question follow-up: I mean, if you’re not law enforcement, you shouldn’t maybe act like them, because they are acting within a certain legal framework, and the rules are supposed to be the same for everyone. And the kiddies abusing the rules is probably not a good idea. And I believe in leading by example.
Lance James: It’s funny because it’s sort of a dichotomy. There’s really bad OpSec where they hide behind the legal. So you are getting this trade-off, like: “Yes, you know who I am but what are you gonna do about it?” Which is kind of a teenage mentality in some sense, right? I think here’s the problem – I was discussing this with a law enforcement guy who was pretty innovative – and I was like: “Look, we could actually make a simple anti-swatting thing, a website that basically he (Brian) can sign up to and says this happens.”
And if you look at swatting, TTY terminals or what’s been used – there’s no voice in the phone; the only voice you have is an operator on the other end. And you can sit there and say: “I don’t want to be swatted, I’m going to put my name on this, I’m likely a target.” And you can start building a cognitive awareness as to the 911, saying: “Hey, send a SWAT,” or “Here’s an authentication method of calling back”. And the problem is they said: “Now you’re asking the 911 dispatching to slow down something.” Now, the only time we’re going to actually really stop this problem or start solving this problem is when someone gets shot.
So, when I looked at what happened to Brian, I’m like: “This is bordering on terrorism.” It may look like a bullying thing to those kids because all they see is their computers and this tool, and it sounds cool. So, yes, I expect that we have to find this balance, and all of us – law enforcement, the InfoSec community, journalists, etc. – are trying to come together. That’s why these conferences exist so we can sit there and have discussions with Matthew over here and maybe figure out how we can find this balance that will still protect people, especially as you’re seeing more kinetic incidents happening with cyber. I think, as we go along, that’s the idea – we’re trying to preemptively do this. And that’s why these arguments come up.
Question: Where do you guys draw the line between DDoS attacks and adequate, perhaps similar, response in return: like if they DDoS’ed me – I’m gonna DDoS them?
Lance James: I think that’s a terrible idea because you continue the retaliation. There are a lot of lines. The work I do is behind a lot of legal things; there are a lot of permissions gotten, steps to take, and things like that. A lot of it is very passive forensics. And, really, when I worked with Brian we handed all of this to the law enforcement. I don’t know whether CloudFlare is with this, but I do work a lot with their abuse team and I happily report issues there. And I expect them to do what they’re supposed to do on their end. But that also comes down to their business, and it’s like different pieces. If things start getting hard, you want to push harder and figure it out; or you get creative and figure out how we get movement on stuff. It’s not a right-away process, it is law enforcement; and it is a due process, it’s not always where we want to be. So, I don’t know where there are certain lines, but it really is down to an individual situation in most cases as long as you know where you’re supposed to stop and what your duties are.
Question: Lance, you made your investigation look really easy, which to me means that you showed real-time access to data, passwords in the clear. So either this kid was really dumb and he didn’t configure anything – you could just grab the files, or you have some kickass tools and know the right people. Which one was it?
Brian Krebs: A lot of these booter services are based on the same source code, which is now open source. So, what you tend to find is the same vulnerabilities across multiple services.
Comment: I was just going to respond to one of the questions out here. We have responded to a lot of different incidents where there was kinetic option given to our clients. There is not an answer for every single incident. But the problem we’re dealing with in different scenarios is – this is either going to be the state department issue with your government or a law enforcement issue with your government. Either way, you’re not going to be getting justice for a minimum two years most of the time. And if your intellectual property is walking out the door, what’s that doing to, you know, the 10-year turnaround time on your return on an investment for your intellectual property?
You have different options in different countries, just by the nature of how those different countries operate when you’re dealing with international incidents. So there is a place, in my opinion, for the free market to maybe show up to some sad bad guy, buy him a beer and say: “We know what you’re doing – please stop!” It doesn’t mean we totally turn around on the other side, but I think you guys can get creative on some of these problems.
Brian Krebs: Thank you guys for your attention!




























