
 Jordan Harbinger, expert in interpersonal dynamics and social engineering, gives a great keynote at DerbyCon event, highlighting the methods it takes to elicit confidential information from people with top secret level security clearance.
Jordan Harbinger, expert in interpersonal dynamics and social engineering, gives a great keynote at DerbyCon event, highlighting the methods it takes to elicit confidential information from people with top secret level security clearance.
Thank you guys for coming to DerbyCon, aka EarlyCon, aka HangoverCon right now. And I appreciate that you’ve all spread out to make the room look fuller: that helps my self-esteem a little bit. First, thanks to everybody who helped DerbyCon happen; I really appreciate you guys having me out here; I think it’s awesome to have an audience of people that really have no choice but to listen to me for an hour.
My name is Jordan Harbinger and I am all up in your business, literally, in this case. Top secret cleared staff, government employees and contractors have certain protocols for disseminating information, rules to follow regarding Internet use and social media, and plenty of you guys in here probably have direct experience with that.
But what happens when an employee is looking to jump ship or leave the company, and then they just don’t care about those policies anymore? What happens when they don’t know that they’re doing any harm? And so I put this question to the test and I mined a bunch of confidential information from dozens of contractors and personnel from law enforcement, and military, and high-profile defense contractors by using LinkedIn and other social media, all from home and nearly all of it using my iPhone.
So, if someone told you that you won a contest and all they needed to redeem your prize was some personal information, such as your mother’s maiden name and your Social Security Number, how many of you guys would fall for that scam? Few of you are a little bit less sharp than you appear. I would hope nobody would fall for that, it’s one of the oldest scams in the book.
Now, have a look at me for the next few minutes as I use basically the same scam, with a slight variation, on thousands of military and government contractors with top secret level security clearances. And today I’m gonna show you how I did this step by step and also share some thoughts on what might be done to stop it, or at least try to prevent it in the future.
So, one day I sat down in my living room and I got bored, and when that happens stuff goes down, I’ll just leave it at that. But within one hour I had a list of 7,700 government and military contractors, politicians, personnel, and all of them with a top secret level security clearance. And I did it all with my iPhone.

So, here we go: Hollywood Boulevard, this is right outside where I live, and this happens more often than you would think: Spiderman in cuffs. You haven’t lived until you’ve seen a Teletubby getting shoved into the backseat of a squad car after an altercation with Darth Vader.
Alright, so before the guys with badges get upset, I’m just gonna let you know right off the bat that I have not elicited any classified information; confidential and classified – totally different story. And I haven’t impersonated any federal employees or elicited anything that is worthy of protection of the law as far as you guys know.

So, a little bit of background on me, I’m a social engineer by trade and by nature, and I was wiretapping when I was 13 years old, which is like: “Mom, what were you doing? Where were you?” I think any statute of limitations is probably wrong by now; if not, just kidding.
I was listening to a married couple in my neighbourhood, they were getting divorced. So, I heard the guy talking to his Mom, to his wife, soon to be ex-wife, to his friends, and so I got a really unusual insight to social dynamics and social nature, really complicated social situations early on.
 And when I was in elementary school, I tried to develop a system for becoming cool and popular, and funny how that worked out, right? And that’s actually something I’m still working on; my company is called The Art of Charm. These days I run a company called The Art of Charm, based in LA, and the principal function of the said company is to teach men to be more charismatic, outgoing and meet and connect with women very strongly.
And when I was in elementary school, I tried to develop a system for becoming cool and popular, and funny how that worked out, right? And that’s actually something I’m still working on; my company is called The Art of Charm. These days I run a company called The Art of Charm, based in LA, and the principal function of the said company is to teach men to be more charismatic, outgoing and meet and connect with women very strongly.
So, what would happen if I mixed the dating science with the intelligence gathering stuff? What happens when you mix the art of charm with social engineering? So, I hunched this would go pretty well, given that the human element of security is always the weakest. And I had no idea just how much would come so quickly.
And by the way, I like interactive stuff, I’m a teacher usually, so if you guys have questions or something is totally confusing, raise a hand and I will more than happily engage questions from the audience, we’ll have plenty of time for that as well. Honestly, it took me 10 times more to prepare this presentation than it did to get all of the top secret level clearance people into one database in one place; at least 10 times as much. And I definitely rehearsed it way more. PowerPoint alone took me 10 times as much time as it did to get to the database.
So, one day I was sitting around headquarters at The Art of Charm; we have live residential week-long programs in LA and New York where guys will fly in from wherever they are, and they will live with my coaches and myself, and we teach them all about rapport, and attraction, and running through drills, and things like that.
And I started talking about some of the clients and what they did, and it turns out that a few guys had government security clearances and they were going through the upgrade process. And it came out that I had a government security clearance from way back in the day for some work I did in college at an embassy overseas in South America. And some of the guys in the room perked up about their project and their clearances, and their top secret level stuff.
As it turns out, when you start discussing projects and use a little bit of elicitation, you can create that feeling of trust and that rapport. And when people start feeling like they’re in similar company, they lose that inhibition to keep things secret. You think: “We’re all computer guys, we’re all hackers, we can talk about our projects and exploits. We’re in good company, people will appreciate it more. We don’t have to be quite as careful, because we’re in good company.”
And so, I realized that with trust and comfort caused by rapport and that feeling of similarity, the information flows really freely, even when one of your principal jobs is to keep things secret. And so, some of the principles of trust value and rapport and other well-established psychological principles that we use for dating at The Art of Charm, can really be used for social engineering purposes. In fact, I would argue that social engineering and dating are pretty similar in a lot of ways; just that one hopefully involves a lot of authenticity, trust and honesty, and the other one involves hijacking your passwords and credit card information. That one is dating, nailed it!
One of the funniest parts about this, and one of the most sobering parts about this was that I was actually able to reproduce these types of chatter, these types of talk with these guys from MI6 and other organizations that you guys have heard of, who knew when they were talking that what they were talking about was probably not something they should be discussing openly, especially in a public place or wherever we happen to be at the time. You just can’t help yourself: when you’re on a roll, you’re on a roll, and if you mix alcohol in there, then you’ve got a recipe for a disaster, or in my case, for a PowerPoint presentation at DerbyCon, for a keynote.
The question is: was this just some face-to-face magic that social engineers, or myself, can work in person that was getting this type of result, or is this something that I can replicate over the Internet with people that I don’t even know, on a larger scale especially?
So, I decided to run a little experiment.
Step 1: Locate a target-rich environment

Where do you go when you’re trying to meet people? Guys, if you’re trying to meet girls, there’s one place that comes to mind pretty much instantaneously where you should go: a yoga class, or the bar, whatever. And when you’re looking for a bunch of people with top secret level security clearances, it’s a different story. I kind of figured that walking into the Pentagon in a Hawaiian shirt and announcing my request was not a good way to go.
So, I asked some government contractor friends which social networks they were on, and everybody was like: “I’m not on Facebook, I’m not on Twitter, it’s so trackable and hackable and all this stuff. But I’m on LinkedIn, you know, just to connect with colleagues.” So, how many of you guys are on LinkedIn? Pretty much everybody, practically, except for the guys in the back, who are like: “Social media is for kids,” which is maybe true.
 And honestly, while people were trying to hide themselves on Facebook and Twitter, they were all over LinkedIn with their updated resume and their headshots, where they’ve got a fist underneath with lasers in the background, like a yearbook photo.
And honestly, while people were trying to hide themselves on Facebook and Twitter, they were all over LinkedIn with their updated resume and their headshots, where they’ve got a fist underneath with lasers in the background, like a yearbook photo.
And I called LinkedIn, I called the connection at LinkedIn and I said: “Alright, how do I search for people? I don’t really use this, I’m on Facebook, because I don’t need a real job anytime soon, so I don’t really know how to use LinkedIn.” And they said: “Well, actually, if you’re going to hire someone or if you were looking for a specific qualifier, you can just give us a couple thousand dollars and you can search for any field that you want, you can search for all of the resumes, even if they’re on ‘private’; and you can contact them directly through this thing we’ve got, called InMail.”
This is a legal way for me to go; I want to search for everyone with the top secret level security clearance and I want them to be a ballistics engineer for maybe one of these 10 companies, and they go: “Ok”, and as soon as the check clears, I can search from my house, I don’t have to verify anything, as long as they’ve verified that their bank account swelled up a little bit. And I have access to all that data. Now, of course, they say: “Well, you don’t have access to my personal name and email”, but I can still reach out and touch you, and that’s the key.
Yeah, at LinkedIn they don’t care about any verification. Basically, I could walk into the office with a stack of cash and be like: “I need to use that search function we talked about.” They did not care; I asked if there was some sort of verification process, and they were like: “You mean for the credit card?”
So, to sum up: for a little bit of cash I can search for people with clearances and expertise that I want, and I can contact them directly using LinkedIn or InMail. And basically, that means I can go around their work email, I can go around their HR department, I can go around their security department. And the site is designed to function in that way, because the point is: sometimes, when you’re looking for a new job, you don’t want your employer to know, so LinkedIn goes: “Don’t worry, we’ll totally help you with that by making it really easy for other people to get in touch with you.” Sweet!
Step 2: Gain access to the targets
I thought about starting some sort of group on LinkedIn with all the top secret guys, but then I ran into two problems: first, how do I find people who are willing to join a group of people with top secret level clearances? That sounds like the dumbest thing ever. And who would be dumb enough to join that group? Who’d be dumb enough to be like: “Oh, I totally have one of those?”
Well, fortunately, that problem was solved, because I discovered that there was already a group of people on LinkedIn with top secret level security clearances. And I thought: alright, there’s probably a handful here, it’ll be great for this test, and I looked and there were 7,700 people in the group. And I checked later and there were even more, so every day people are like: “Oh, I have that, I want to be in this group.”
So, there were intelligence analysts in there; there were scientists in there; engineers of every foreseeable field: ballistics and aerospace and stuff I can’t even pronounce, and even a couple of congressmen. So, some of the people in the group were congressmen from Ohio, engineers from Lockheed Martin, Northrop Grumman, Raytheon, Homeland Security officials, federal business development and sales, Air Force guys and program directors, and even the commander of something called the 412th test flight squadron – I thought: “Ok, this is probably a guy who knows lots of cool stuff”, I didn’t mess with him though, I’m not stupid.
So, I had this entire list, as well as access to pretty much everyone in it from my iPhone – again, right from the phone and from any laptop from anywhere in the world. And I did most of this from Starbucks, just in case. You see the suits walk in and you’re like: “I’m not thirsty anymore, I’ve got to go.”
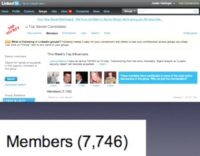
So, there’s the group (see image), and you can see Joshua Reese there, he’s got an active security clearance with some science stuff and blah-blah, and he’s leaving the Army, so he’s looking for a place to spill the beans on everything he worked on while he was there. Alright, so how many of you guys are in this group, or a group like it? You can just admit it, I recognize, like, half of you guys. Your secret is safe with me.
So, how the heck am I going to join this group though? I can’t join it; I don’t have a top secret level clearance. This is going to be verified, obviously, they’re going to look into this, right? Does anyone have a guess how I joined this group? I clicked ‘Join’!
And then of course they were like: “Well, you need to send an email to the moderator for verification purposes.” So I thought: it’s gonna ask for a photograph of some kind of certificate thing you probably get when you have this. So, I sent them an email and I was like: “Hey, I have a top secret level clearance and I want to join the group, and here’s the email. Tell me what else you need from me.” And 10 minutes later he was like: “You’ve been approved.” So, the verification process is clicking ‘Join’ and telling him: “Oh yeah, I meant to click Join”, so, sweet, awesome, I’m in. 24 hours is the usual verification process, probably, slightly less time than it takes to actually get a top secret level clearance.
Step 3: Associate and gain rapport with targets
So, now I was in and it was time to see what I could dig up. I want to make sure that I get something cool, because joining this group is funny, but it’s not going to impress anybody in this room. So I called Chris Hadnagy and I was like: “No one is going to like my talk, what do I do now?” He said: “Get some information.”
I’m like: “Ok, I can do that.” So, now I can see the LinkedIn profiles and their CVs and their contact information and their job descriptions, and I know exactly which company they work for, and they decided to supply that for just about 8,000 people.
And the problem was that obviously these guys go through some training, so they know that if someone hits them up on a network like LinkedIn, they probably shouldn’t say anything about what they do. I mean, surely they have some training to that effect.
Not exactly; as it turns out, people who think they’re in similar companies, as I said before, actually don’t seem to have a problem discussing anything that they’re working on, even if it’s over the freakin’ Internet. Because, well, I’m in that group, so I must be TS cleared and probably I’m a good guy, and also, we’ll get into it as well, what do you think people are doing in that group in the first place? Does anyone want to guess what people are doing in that group? They’re looking for jobs, right. So, what do you offer people looking for jobs if you want them to talk? You offer them a job, nailed it!
So, I needed to think about what I could offer these people job-wise that would make sense and wouldn’t arouse any suspicion. That wasn’t too hard, actually. The group exists, as you guys guessed, to help people with top secret level clearances find jobs. It seems to be a field in which a lot of guys bounce from one project to another, they come from the military and then they’re like: “How do I get a job in civilian life? I’m in freakin’ Kuwait right now, I can’t interview. How do I even start?” And this group is a good place for that. It’s very useful, which is why I’m destroying it in this talk right now.
So, I started a LinkedIn profile showing that I was a headhunter, so I can offer people jobs. And I made this credible simply by modeling it after other headhunters that were also in the group, or other people that were on LinkedIn, or people that I knew were headhunters, who I could call and say: “Hey, how do I make a fake LinkedIn profile that looks like a headhunter?” And they’re like: “Use mine, use this, just don’t use my pictures.”

So, that was really easy, and, in fact, you’d be surprised how many people want to help you when they think you’re going to mess with other people. And I’m really exploiting the principle that people trust their senses implicitly; they think that what they see is what is actually there, which is interesting. If you look at something like this, for example, the chameleon is a classic example of this, right? It sheds predators all the time by tricking them using their own senses, and it’s brilliant, because we don’t question those things.
Not being a real headhunter, I had to practice a little bit, so I even practiced with headhunter buddies and said: “Ok, what kind of questioning line do I do?” Because I assume that if you’re looking for a job, you’ve talked to maybe half a dozen headhunters already; you’ve already gone through this. So, if I call and I’m just like: “So, tell me what you’re working on right now,” that might not fit in line with what everybody else has done so far. So, I tried to get it and it was relatively simple, I mean, it was really, really simple actually.
I then found a few people looking for employment to see how easily I could get them to send over a copy of their resume with personal information on it and any other details on their projects and activities. I was especially looking to grab any information that I shouldn’t have ready access to, but that wasn’t classified of course, especially their specialties, or former jobs, or any projects they might have worked on in the past.
So, I indicated a preference for military in a very non-shady way by including a line that says: “We prefer supporting veterans wherever possible,” and that, basically, gets them all out of the woodwork. And it’s great because I like supporting veterans, but also somebody’s got to know that, again, if you’re looking to exploit that niche, the best thing you can do is flatter somebody or offer them something of value. And so I got more responses from active duty military than I thought I would.
And eventually I’d hit a digital wall, in which the targets have probably had enough contact from somebody that they didn’t know very well and I asked just a few too many questions. That’s when we get here:
Step 4: Lay groundwork for the attack
 I calibrated my approach a little bit and I requested certain information, and then I used the service called Jigsaw or something similar to grab their office number. And so, even if all I had was their name, I could call the company switchboard and get connected, which is really easy and very convenient if someone is legitimately trying to reach you.
I calibrated my approach a little bit and I requested certain information, and then I used the service called Jigsaw or something similar to grab their office number. And so, even if all I had was their name, I could call the company switchboard and get connected, which is really easy and very convenient if someone is legitimately trying to reach you.
Once connected, I would just feign a bad connection and have them call me back on their office phone to my burner, burner being a phone that I’m not going to use, or that I don’t use to call my parents and friends. And so I’d have their number on my caller ID; sometimes it worked, sometimes it didn’t.
I did this because in the future I wanted to have the option of calling those people back, spoofing their actual internal office phone numbers. So, in other words, I could call them from a colleague or an office across the country, or from IT support, or anything like that right from their own work phones, which actually worked a treat. Even on digital systems people just think: “Oh, there’s something weird going on,” because the whole number is showing up, not just the extension. They don’t go: “Hmm, somebody must be spoofing my number, because a week ago I got a call from a headhunter and I wasn’t even looking for a job.”
Once I had a few telephone conversations with the target or even beforehand, I would ask them for their private email address, because I don’t want to send them the information about the job to their work email. And you guys probably all know what can be done with a private email address, using programs like Maltego, and looking on Facebook, just a simple Facebook search can bring up a lot.
 So, I plugged it into Maltego. Does anybody know what Maltego is? Does everybody not have a clue what I’m talking about right now? I’ll just give a brief overview: Maltego is a program that can take little bits of information, such as an email address, and search the five corners of the interwebs and find everything that has that, so if you’re fishing and you use that email address on some forum where you talk about fishing and you post pictures of how many fish you catch and about your boat and the suspension on your car, I can find all that. And if someone’s dumb enough to post an email you sent them about something unrelated and post it in the forum or anywhere, Maltego will find it and I can take a look, and now I know what kind of brake issues you’re having on your Z3, Miata or whatever, I don’t care.
So, I plugged it into Maltego. Does anybody know what Maltego is? Does everybody not have a clue what I’m talking about right now? I’ll just give a brief overview: Maltego is a program that can take little bits of information, such as an email address, and search the five corners of the interwebs and find everything that has that, so if you’re fishing and you use that email address on some forum where you talk about fishing and you post pictures of how many fish you catch and about your boat and the suspension on your car, I can find all that. And if someone’s dumb enough to post an email you sent them about something unrelated and post it in the forum or anywhere, Maltego will find it and I can take a look, and now I know what kind of brake issues you’re having on your Z3, Miata or whatever, I don’t care.
But I can find out lots of stuff that you weren’t going to tell me, and I can use that to create rapport: I can also use that to find your blog, I can use it to find your Facebook profile, and that’s where I really struck gold. So, it’s kind of the digital equivalent of fixing a GPS to your car and then downloading all that data later on; only I get it in, like, 10 minutes.
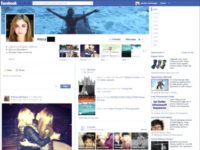
So, I created a fake Facebook account, a female, obviously; and I molded it after a big mixture of my female friends and someone who’s appealing, especially to an engineer type, but seems real enough and accessible enough that the guy thinks he stands a reasonable chance of maybe getting a date with that girl, or gets the idea in his head that that’s a good one.
So, here’s my assistant (see image), she looks ok from there; this isn’t the actual profile that I used, but it was very similar and her photos were up there. And her being an engineer, of course, that got a lot of attention from a lot of the guys that I was looking to talk to. And so, there she is, of course, because I knew you guys were going to look for that anyway, so I’ll save you the trouble.
Step 5: Execute the attack
So, I added a bunch of my targets on Facebook and I was able to get the privacy settings down so that if I added a few people from one company, they wouldn’t necessarily see each other and be like: “Well, that’s weird, Chris is on there and Tim’s on there. Is my whole department quitting?”

One of the things I thought for sure was going to happen is people were going to go: “How do you know me?” But they didn’t; most of the time the guys were like: “Sweet, accept!” And 30% of the time at most guys would be like: “How do you know me?” And I go: “Oh, Facebook suggested we’d become friends,” and they were like: “Ok, fine, whatever.” There’s that little suggestion box, nobody thinks that’s weird for some reason. When it’s a guy, they’re like: ‘Delete’, but when it’s a girl that looks like that, they’re like: “Ok! Thanks Facebook, good looking out!”
Besides, our minds always want to believe what we want; we always want to think: “That type of girl totally would want to be friends with me.” And if this principle weren’t true, there would be a lot fewer people who would think they could walk around wearing spandex: you guys know who you are.
So, the female Facebook friend, of course, is also an engineer and she’s got a clickable resume on her Facebook profile, and that’s to another website. So, when you want to look at her resume, you can click on that, and, of course, when it goes to that website, I get the IP address, which leads to the location, and I get the browser and the OS and the language and stuff, and by that I can sort of figure out which person that might have been, which office that person might have been from; especially if I know that somebody with a really Chinese-sounding name who works in California and has their browser in Mandarin is looking at this at this time after I just friended him, like, 5 hours ago.
So, I can guess that’s who that is and now I know where they are, what browser they’re using, etc. And all you tech guys know what you can do with some of that, given a few other facts.

Now, of course, there’s also another link with her most recent vacation photos (see image), and that, not surprisingly, got a lot more clicks than her resume.
So, you guys could think: “Oh, great, so what? Your friend is some defense contractor on Facebook, who the hell cares?” And that’s fair. But the ‘damsel in distress’ type of ploy tends to be ripe proving grounds for eliciting information, and a pretty girl asking an engineer for confidential information or classified information theoretically, hypothetically, etc., is a lot easier than you might think.
And of course none of this is done in real time, so if I get a message with a question back, I have like 5, 10, 24, 72 hours to craft a pretty perfect response, and I can call people and ask what they would do, and if they would ask a career-specific question I can get a real answer from somebody who actually knows what they’re talking about. And that actually turned out to be shockingly easy, and you can do tons of research and prep on the fly.
There is also the fact that she’s sharing plenty of information about herself too, right? I’ve got a whole persona for her. I’ve got a matchmaker that works with us at The Art of Charm, so she’s helping me craft the perfect girl for each target. Like, this guy’s into this, he probably really loves this, this and this. Then our female engineer of course becomes that girl overnight immediately, within an hour phone call to the matchmaker.
So, even her resume is tailor-made to impress the target, and she makes him feel important by having him take a look at her resume as well. I created multiple profiles, just in case. I did have, like, a basic cookie cutter girl with a lot more blanks than information filled out so that I could fill it in with just whatever I needed to in the email. So, if the guy seemed like he wasn’t sporty, I didn’t have her be like “yoga, running, dancing,” because that would be a little intimidating. I’d have her be like: “movies, video games,” so you don’t want to write all these things in. Just saying, you know it’s true, no hate.
Robert Cialdini, a psychologist, has a principle called Reciprocity: the more she shares about herself, the more the target feels secure in sharing about himself. And in one case a more careful target was like: “I’m not going to tell you where I work, I’m not going to tell you my location, I’m not going to share project data with a recruiter online.” However, once she asked him to meet for coffee to talk about jobs, he could not wait to disclose his location, and his email address, and what he was doing, and that he was free for the next 18 days. And that was much faster than LinkedIn, because she would write back something like: “Listen, I don’t use this that much, but if you just send me an email, it’s a lot easier.”
So, I was then able to use his personal email to find his Yelp account, everyone probably knows what Yelp is, but if not – it’s a site where you do business reviews online, and judging from the approximate area by looking at what he’s reviewed, I can find out, basically, where he lives. So, if he’s reviewed 20 Thai restaurants and coffee shops in Albuquerque, I know he probably lives very close, or works very close, or lives there.
Now, of course, the girl was thinking of applying to his company and, possibly, moving closer to home, closer to her parents, in that case, and conveniently located in the area where she was working, so that was a great coincidence for him that this pretty girl in his field was thinking about maybe moving there, and he was going to do everything he could to sell that idea.
Let’s recap:

I know facility locations, department names, project names, target names, target resumes, spoofed internal phone numbers, and target social media profiles. And I’ve got that all without any real technical skill at all. The most technical thing I’ve done so far is look at a server log for their IP address, which everybody, my Mom probably knows how to do that. So there’s no real technical exploit here; there’s no systems that have been compromised; the only system that has been compromised is common sense and rationality, or due diligence on part of the target.
Step 6: [Hypothetically] Elicit classified info

Now that I have tons of information about the company, the facilities and how things work from the inside, from the types of computers they use and even their phone systems, I know that I can call target number 2, maybe a supervisor, but not the target’s actual supervisor. And I can call from an internal number or an employee’s cell phone, and since I have plenty of knowledge about the company itself, I can ask about: if I was meeting with a headhunter for a job, what information should I not discuss?
So, now I’m getting: “Make sure you don’t talk about this, this and this,” all these things that I didn’t know existed before. And I cannot take that innocuous information and repeat this process over and over: “Hey, I was wondering if I could discuss this, but I’m wondering what aspects of this are really under the table, and what else I can talk about.” Well, let’s break this down into 5 parts.
Now I can start mapping some of the things they were talking about in detail, and you’ll be surprised: once somebody knows a little bit, it’s like a keyhole, you can really go in there, you can open that door and people are like: “Well, if you know that much, you obviously know all this other stuff, so let’s just recap that right now.”
 I discussed vaguely what I was working on, and I asked which topics I should avoid, and I’d love to share this cool list of stuff that I got with you, but of course our lawyer at the EFF put a kibosh on that really fast. So, my original goal with the experiment was just to do that. But that was so easy I thought I would take things up a notch.
I discussed vaguely what I was working on, and I asked which topics I should avoid, and I’d love to share this cool list of stuff that I got with you, but of course our lawyer at the EFF put a kibosh on that really fast. So, my original goal with the experiment was just to do that. But that was so easy I thought I would take things up a notch.
So, once I found somebody willing to jump ship, I decided to contact them privately through email and I enticed them enough to want this information about this new job.
In order to get this new job I needed them to sign an NDA, because it’s a pretty sensitive career, so I made sure they get sent over an NDA to get signed and then sent back to me. So, now I had their signature. And despite having not yet applied for the job, I needed to do more to protect myself, so I made sure that NDA was comprehensive, as comprehensive as possible, and had address information and name and everything that I could just verify that I knew. And I had it all in one place, and of course I had their signature right below that. That was so that I could kick off a preliminary background check on the target, which is great, because people with security clearances are really used to people looking into their business and they are willing to give out all kinds of information that they shouldn’t so that people can do that, if they think you’re legit.

So, now I’ve got Social Security Number, mother’s maiden name, address, last few addresses, employment history, signature, resume – everything. There’s not a lot that I cannot do with that information, and I could maybe reset their password for online banking, I could reset their PayPal password, which shows which banks they use. If I got into their banks or their credit cards, I could find out which financial transactions they were doing, where they were spending most of their money, whether they had a lot of debt.
I could also figure out whether or not they were using a cell phone – of course, everyone was; which carrier they were using, and then of course I would go into their cell phone call records and go: “Ok, cool, this is probably their Mom, this is where they grew up, because that’s where the area codes were concentrated; here’s their best friend, here’s their office; here’s all the people they text all the time.” So, think about that: the call history shows me who your closest friends and family are, and I already have all this information.
I also have your direct deposit in your bank account, so I know how much you get paid, which is good, because as a recruiter I want to make you a juicy job offer that pays you quite a bit more money than you’re making now, but not a ridiculous amount that’s off par with market or something that makes you go: “Wait a minute, what? I don’t understand this,” and raises any red flags.
So, more importantly, I can see if somebody has debt and how much, because that’s really the key: you can make a million dollars a year, but if you owe people 10 million, you’re broke. And I can also now call tech support for this guy’s company, prove that I’m him and have them help me install a VPN on my computer so that I can log in to the machines at that intranet while I’m away on business, which is great, because I already know when he’s working remotely or out of town anyway, because I have his Facebook and everything else, so I’m monitoring all that.
And even more devious: if I was a real bastard, I could use TripIt or just his Facebook status updates and I could see when he’s travelling for work or he’s not home, and I could probably go house sit for a few hours and clone any hard drives I wanted or take a look at anything I really wanted in his personal office.
Imagine the consequences with that. I’m an honest dude for the most part, with an iPhone, a laptop and Internet connection, and way too much time on my hands, and if I can do this in just a few hours, imagine what could be done with a budget, or a team, or people who don’t care about U.S. law, for example.
And instead of waiting for a business trip of unknown duration, if I had a budget for this, I could just fly the target out along with his whole family to ensure an empty house, to nice recruiting retreats, which I’m sure plenty of you guys have seen, you know, they’re: “Oh, come work for us, look, we’re going to have this thing in these resorts, you can go there with your family, most of it is free time and you just have to attend a few presentations about our company so we can entice you to work here.” Meanwhile, their house is empty and the rest of my team is in their garage looking under the hood of their car, etc.

There are some call records, just in case you don’t know what your call records look like – looks pretty much like that (see left-hand image), and I can see your texts too, but I can’t see the actual messages, of course, without a court order, not that I would need to if I know who you’re talking to anyway.
This is actually corporate bank statements (see right-hand image above) which are surprisingly disorganized. This check I freakin’ found online; somebody scanned this and put it online – unreal. So, here is what I’m doing while you’re away – I’m breaking into your place.
Solutions
So, the solutions are obvious, right? Training: sure, you got policies with respect to social media in your company, and you’ve got this classified info, and you know you’re not supposed to divulge all this stuff. But if someone’s ready to jump ship, if you don’t care about the company anymore, you don’t give a crap, right? You don’t care. You think: “Well, I’m not doing any harm, I’m just looking for another gig. I’m not really hurting anyone by talking about this stuff. This is a recruiter, what is he going to do? He just wants to know. No big deal.”
Of course, you don’t know that there’s a malicious angle to it, because you’re not thinking about that, you’re just looking out for yourself. So, a company like White Hat Defense, or a shortlist of other highly qualified trainers can work miracles. And if you’ve had training already, a lot of you would be like: “Oh, I’ve already had training, I’m good.”
When is the last time you took the class yourself? And when is the last time you gave it to your staff? And also, do you remember what you learned in that class? Because I took a course a few months ago, and you don’t remember 80% of what you learned, even if you were there for 4 straight days. So, if you don’t remember what’s taught, you know damn well that nobody else on your team does.
And if you think that your staff would never fall for this, I’d like to just recount a brief story that happened to us at The Art of Charm. We were moving from New York to LA, and we decided: “Ok, cool, we’re going to do the work for, like, 6 weeks in between these two things, these two locations.” And so we’re going to pack all our earthly belongings and we’re going to send them through the shipping company with a big crate and put them in the storage unit, and then we’ll come back and have them ship all that stuff to LA, and that was a great idea. Except when we got to LA and we called that company, their number didn’t work anymore. And then, when we googled and investigated it and found different locations on the map and the warehouse that they used, I called the warehouse, and the kid who worked there was like: “Yeah, they went out of business, like, 3 months ago,” which is funny, because I hired them a month and a half ago.
All of our stuff was gone, and he looked and looked, and we called him every day and we offered him $1000 if he could find our stuff. And finally some good news came back and he had some of our stuff, so he packed it all into a box and he mailed it over, and out of the 26 boxes of crap that we sent to this storage unit in Pennsylvania, we got 13 boxes back; all of the valuable stuff was gone and all of our clothes were soaked in all of our toiletries, that was ‘great’. So, all this stuff was ruined; not only have we been ransacked, but everything was ripped open; and what was really missing besides the electronics was all our luggage, which I assumed had been used to carry away our electronics.
Basically, if you’re thinking: “I would never fall for this” – realize that everybody can fall for this; it doesn’t matter how sharp you are. My assistant who found that company, and we do not want to put the blame on her, obviously did her homework as much as she could have, and just found a place where price matched, called, the guy was nice on the phone – fine, you’re hired, right?
So, I would propose an independent HR department or a security department, where people don’t feel isolated, because the thing is people make stupid decisions and they don’t think critically when they’re isolated. And if you’re looking for a new job, you can’t tell your boss, you can’t tell your colleagues, you can’t tell HR, because you don’t want to get fired. The problem there is a lot of the information that I elicited would never have come out if people were like: “Hey, I’m talking to this recruiter and he just needs to know a few things about what we’re doing here. Do you think it’s a good idea?” – “You probably should just tell him you can’t tell that and he’ll have to understand.” – “Oh yeah, maybe I should do that.”
But if you can’t bounce that off of anyone else, you’re just going to do what I ask you to, because you don’t know any better and you want that job so bad. And this is why con men and salesmen operate best in the vacuum: if you are thinking critically, if you have a moment to think – a lot of times you’re going to choose the right decision, which is: “Keep your freakin’ trap shut, someone’s going to poke holes in that.”
In conclusion, obviously, the human element of security is the weakest, always, and it always will be. The sophistication of our systems improves all the time, but the software that’s in your brain really doesn’t. In fact, it degrades over time as we become complacent.
And I’m going to skip the ending story that I had for you all, because I think you guys are pretty sharp and obviously understand this. But essentially, when I was in college our computer lab kept getting robbed over and over again, and finally they installed the keycard thing, where you had to insert your student card to go in and get to use the computers. And they still got their stuff stolen, and they finally installed all these other locks and these verification things, and you had to sign in and everything. And then they finally installed a really expensive video surveillance system, and they still got robbed, but when they reviewed the tape they finally realized how these guys were getting in, and the way they were getting in was they were knocking on the door and telling whoever was there that they forgot their card; and they would wait until everyone left, and then they would steal all of the stuff.
So, no matter how expensive your locks are, no matter how awesome your security system is, it’s not worth a crap if someone’s going to open the door from the inside. So, I’ll leave you with a quote from Paul Wilson from BBC’s “The real hustle”. He says: “If you’re the type of person that thinks they can’t be conned, then you’re exactly the type of person that I would like to meet.” Thank you!





























Great things read about. Thanks :)