
 British investigative journalist Duncan Campbell speaks at DeepSec Conference about the use of cryptography by terrorists and outlines the related threatscape.
British investigative journalist Duncan Campbell speaks at DeepSec Conference about the use of cryptography by terrorists and outlines the related threatscape.
Thanks very much and good morning. I’m gonna talk, or try and talk, about what real terrorists do with modern encryption tools in the 21st century, do they succeed in communicating securely, do they know how to, how they build their own effective methods. I’ll try to respond to these questions using evidence, including a strain of real terrorism cases in which specialists, including myself, have examined computers and Internet records. But first, throw out everything you’ve read in the press (that, by the way, is my other profession). In the real world the evidence is never going to be complete or perfect, we’ll look at some of that in a minute.

First, I’m going to look at the myths, the constant drum-beat of loud and fearful claims that we have endured for 2 decades about the risks of letting cryptography into the hands of Joe and Jane public. I’m going to review the terrorists’ teaching on cryptography and come up to a program invented recently by a group linked to al-Qaeda. That system code-named “Tadpole” is being used in the Indian subcontinent and was involved in an alleged plot to bring down transatlantic flights, so we’ll take the lid off Tadpole. According to the London Counter Terrorism Command, breaking Tadpole (see screenshot) was the most sophisticated decryption task of its kind ever undertaken (we’ll see).
Techno-fear rules – alongside techno-fear, the advocates of more Internet control have for 20 years invoked the spectres of Four Horsemen that would use the Internet and crypto to harm us: paedophiles, narcotics distributors, organized crime, and, of course, the big one, international terrorists.
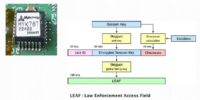
Those of us who are a little bit older will remember that 20 years ago Phil Zimmermann invented PGP and was threatened with jail for distributing it and making it available, and in 1993 President Clinton announced the counter-measure, the so-called Clipper and Capstone chips (see image) that included backdoor entry for the U.S. National Security Agency.
So the spectre of terrorism networks hiding behind unbreakable encryption has been a war cry for security agencies, supporting their claim for key registration for 20 years. If you were around then you’ll remember ‘key escrow’ that had required us to entrust governments with a database of registered backdoors to all crypto systems. What’s not to like about that? International campaigning groups challenged the Clipper plan as illegal and by 2001 they’d lost, the key escrow program proposals went right into the trash. Who now remembers the EES, the Escrowed Encryption Standard?
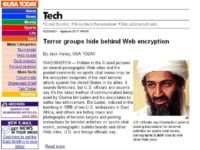
In the run up to 9/11 there was a new scare story out there in the media. On the 5th of February, 2001, ‘USA Today’ published an exclusive report “Terror groups hiding behind Web encryption” (see screenshot), and it says that “Hidden in X-rated pictures on pornographic websites and sports chats are the plans for the next terrorist attack on the United States”. Well, I only hope these chaps spent a lot of time looking at porn over the 9 months, but it didn’t do them a lot of good. “Computer software is allowing secret plans to go back and forth in the Internet undetected”. That’s the porn again. Farfetched they suggested it might have been, farfetched it was.
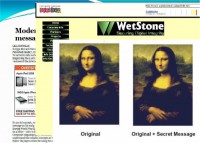
But it gained currency again, just after 9/11. The ABC programme ‘Primetime’ in the United Stated claimed there was new evidence of Bin Laden using Internet steganography that has absolutely astounded American law enforcement intelligence agencies. Wow! The ABC programme featured an interview with the president of WetStone Security Company, and it showed him entering a secret code on screen to unlock pictures and plans from a rather large familiar graphic (see image).
Was any of this true? These images were downloaded from WetStone’s website by a couple of researchers from the University of Michigan, they broke the steganography pretty quickly, about one minute, they found that the password to extract the secret content was “ABC” – the name of the network, and that was the so-called terrorist file, but the viewers of ABC television were never told.

The next improbable allegation was published on another website by the Pentagon reporting that al-Qaeda was planning a major biological attack, with evidence from a former National Security Agency instructor. He claimed to have discovered plans of a much larger attack being arranged on the Internet and using coded instructions to direct sleeper agents. Scary stuff!
This novel was just published in Britain (see cover), it’s about a British Islamist terrorists cell who are about to mount a suicide attack on London. They gather secretly in a safe house. “Have you heard of steganography?”, says Salim. “There’s a kafir site (kafir that’s the rest of us, the unthinkables, the upper states, the infidels), called “babesdelight”, with naked girls. You choose lots of pictures and you need to type on one called ‘Olya’. Embedded in that, in a particularly intimate place, is your hourly last-minute instructions.” There it is, and just touching the intimate place for your instructions.

The hijackers who attacked New York and Washington did not use encryption at all. On the 18th of September 2001, FBI Assistant Director Ronald L. Dick, who was head of the U.S. National Infrastructure Protection Center, told reporters at an FBI briefing that records of the Internet messages between the 19 hijackers had not involved any encryption or concealment. He said it was simple e-mails back and forth. That was it: no encryption. A decade of fear, the biggest plot ever, the biggest loss of life – no encryption. And exactly the same conclusion was reached in the large official 9/11 report (see image). The hijackers had used regular e-mail services like Hotmail, they’d been taught to use simple codebook substitutions, such as calling the White House “The Faculty of Politics”, or the World Trade Center “The Faculty of Commerce”. They did not encrypt. No stag porn. Nothing, zilch.
After 9/11, U.S. legislators made a final attempt to bring in key escrow and to clamp down on Internet cryptography, but the new cryptography control bill collapsed in October 2001 when the U.S. Congress passed the very far-reaching Patriot Act, and Patriot Act did not include curbs on cryptography.

Just 6 weeks later, the world got the first insight into how terrorists encrypt or, at least, were taught to encrypt. This was because in December, they were desperate to get the Bill, the Patriot Bill, through the Senate; the U.S. Government published what they chose to call an “al-Qaeda Manual”. And this is it, that’s URL, it’s still live, right here, right now (see image), and it says it was found during a search of an al-Qaeda member’s home. It was found in a computer file described as the “military series” related to the “Declaration of Jihad”.
The manual contains 18 lessons in terror techniques. The original of the Manual is on John Young’s “Cryptome” site (see image). It’s originally in Arabic, and at the time it was written Osama bin Laden was helping run a guest-house for fighters attacking the Soviets, they were all supported by the West. The Manual was actually a war souvenir kept by a former fighter who’d been settled in Manchester. And you can tell it dates back 1999, because here, even in the American Government’s translation, it’s still referring in the last line to people in Russia, in the Army having to be in the Communist Party.

This is what the actual Manual (see image), you can see it’s a rather unusual sort of computer file. It isn’t a computer file at all in fact, it’s a hardbound paper document. Lesson 13 in this Manual is “Secret Writing and Codes, and Ciphers”. They set up various options for use with the 28-character Arabic alphabet. They are numerical, symbolic, and table encipherment documents, but nothing more complex than that. All of the ciphers in the “Jihad Manual” are actually simple monoalphabetic substitutions.
If you want to have a longer look at those instructions, they are not in the version put on the Department of Justice website; they are, however, in John Young’s “Cryptome” website which I put up earlier, you can go there and see it all translated into English. The full text is also in a special speaker folder for DeepSec participants, it’s been arranged timely by the organisers, that’s the address:
https://deepsec.net/docs/t/Keynote.zip
that’s the password: RPGogU4FNX3 .

During the 1990s that little manual evolved from a hundred-page document to a second edition of 11 photocopied volumes with over 5,000 pages (see image). A full set of the 2nd edition, “The Encyclopedia of the Afghan Jihad”, weighed 10 kilograms, and it was circulated amongst jihadist informed fighters who came to Afghanistan. In Arabic its title is “Muswada al Jihad al-Afghani” – “Encyclopedia of the Afghan Jihad”. Paper 2nd edition copies are rare, one was captured by police in Britain in 1998. Bizarrely, having captured it, they gave it back to its owner, this fine chap, Abu Hamza, and then they came back 7 years later, and arrested him for possessing it.

The volumes in the Manual are here (see image), but in fact, as for secret codes, cryptography, secret communication techniques there was nothing, nothing at all that we know about, that’s the paper 2nd edition then.
In the mid-1990s some American Islamists, the Amriki, arrived in the Pakistani jihad scene, they were people who were growing up in the United States, and they spoke English, they also spoke Nerd, and in February 1996 one of them who used the nom de guerre of Abdul Aziz, launched the project to enlarge the Encyclopedia as much as possible and to make it fully electronic for distribution. Here on the right is his checklist, this is the front of it, this is v.2, you can recognize the way the information is structured as being more intrinsically Western than Middle-Eastern, and it does have in 2.1, which is the 4th section down, “Computer Privacy”. You’ll find it’s nothing special, it’s something that any of you might have seen, if you’d been downloading from user lists during the 1990s, it’s just absolutely orthodox Western stuff, hacker stuff that doesn’t actually contain anything about cryptography. They put out “Computer Privacy” in ’96.

The next edition of the Encyclopedia came as a set of CD-ROMs (see image). They were sold in the bazaars and souks of South and East Asia from 1998 onwards. And they started out as not much more than scans of that huge paper previous edition. And at this stage “The Encyclopedia of Jihad”, “The Muswada”, was not an al-Qaeda project. These Amrikis did PDFs, of course, by 2000 there were over a hundred “Encyclopedia of Jihad” PDF files being circulated, and they ranged from military and sabotage manuals to ideological tracts and recipes for explosives.

Among the “Encyclopedia of Jihad” PDF files being circulated, there was also the “Mujahideen Poisons Handbook” which I really can’t recommend to you. You can probably find it, but you do not want to follow the recipe for making Botulinum toxin from fermented excrement.
The Amrikis also did PGP, now we’re getting somewhere. The organization for the preparation of Mujahideen – that’s the “Computer Privacy” document you can see online if you want (see image) – I think Mr. Goldsmith’s still around, if anyone knows him – he might not know they used his material.

So the organization for the preparation of Mujahideen now adopted and promulgated PGP, they included their public key, their e-mail address in every document, and supporters were invited to send in scanned and electronic material to build an electronic Jihad library (see image). They’ve been obviously doing this competently, but it was never used, or suggested to be used for operational communications, and what you actually find when you’re looking at the classes of people who do this kind of things is the people that collect documents and distribute documents and copy stuff and like to think that they’ve got the biggest library than the other person, and then the people who get out in the streets and do harm, and this kind of stuff, this use of PGP – was the kind of people who distribute and collect documents, that being their thing.
However, in 2002, after the Western invasion of Afghanistan destroyed the training camps, the 3rd edition of “Encyclopedia of Jihad” appeared on the Internet (see image), and it was published in the West, at GeoCities which was later taken over by Yahoo. And this is the full index of “Encyclopedia of Jihad” 3rd edition, down there, to the left, you’ll see the address at which it was originally published, it’s dead now, don’t try, it’s taken over by Yahoo as well.

And those of you who speak Arabic fluently will, of course, have spotted down at the bottom one of the files is “Emir Khattab’s course on cryptography and symbols”. This was now an al-Qaeda project, there was an endorsement to Osama bin Laden as now the head of the organisation, so it’s become integrated to al-Qaeda’s activities.
There was a chapter here on secret writing (see image), but when we read it in Arabic, “Secret writing” turns “Tasnya al-ahbar as-suriya” – which just turns out to be a set of recipes for chemicals to make secret inks.

So we’ve got to 1993, we’ve got on to Yahoo, we’re doing GeoCities, we’ve passed through PGP, but when we’re putting it out there and we’ve got the endorsement of Sheikh Osama, but its chemical secret inks, and the other one which was “Emir Khattab’s course on cryptography and symbols” (which sounds pretty exciting, as it’s coming from a real Emir) – that turns out to just be a series of diagrams on military manoeuvres. Up there there’s an index list and another Hotmail and Yahoo address, all very standard, all very similar stuff.
There were also “Encyclopedia of Jihad” manuals in Arabic on hacking and cracking, and the English one that you’ve seen already on computer privacy.
This is the 4th edition of “Encyclopedia of Jihad” (see image), now it’s published at Yahoo in California, it’s December 2004, and it’s got new sections, it’s got “Nuclear Weapons”, it’s got “Bio-war”, it’s got plans from Hamas, the Palestinian group, for home-made missiles which are sadly and unusually lethally effective, and how-to videos on suicide vests, but there was still nothing on electronic cryptography.

Same year al-Qaeda launched a couple of new magazines – they also ran a discussion group right there on Yahoo – this is the magazine, or the journal, of the camp al-Batar, or “The Sword”, for several years it published the usual fare of explosives and booby trap guidance mixed in with religious fatwas, but it did not cover crypto. And the same is true even of newer CDs (see image). This is in the last few years picked up in the Middle East, quite extensive and new materials – bombs, bazookas – but not cryptography. So that’s the literature review.
What about the tools? During most of the early 2000s, most sensitive communications used by jihadists went by unencrypted e-mail. The use of code names, code word substitutions was extremely common and standard practice. The collaborators often used the now very well known method of a Web mail dead drop on Hotmail, Yahoo, or the like; that is to say that messages would be written and left in Web mail “Draft” folders to be accessed by multiple users from different locations all of whom have shared the username and password. By doing that, although they were not using encryption, the communications obviously went over the Net as Web traffic, and not as e-mail. Now, more recently they’ve been doing this again, but they do it using sites using the Cloud.

Now, finally, we have cryptography from jihadis. This is “Asrar al-Mujahideen” (see image) – “The Secrets of Mujahideen” in Arabic, and it embodies a series of executables and various other files promoted as “the first Islamic programme for secure network communication”. It was originally published on the website aclass.org. Now that aclass has been closed, Asrar still can be found on the Net, if you know where to look for it; “Asrar” is Arabic for “secrets”.
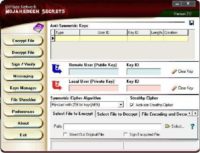
The main screen here offers encryption, decryption, file wiping and key management (see screenshot). And I’d ask you to especially note this feature, right over there, under “Mujahideen Secrets”, you see they’ve come up with something clearly devastating to world of cryptography, it’s “Anti-Symmetric Keys”, in order to carry out their communications.

Asrar offers a choice of 5 candidate AES ciphers, you can see Rijndael as a symmetric algorithm written down there, they also include Mars, Serpent, RC 6, and Twofish. The key management structure is based on so-called AKF files, or Asrar Key Files, and this is the content of an AKF file (see image), for all the world it looks like a clone of PGP. Now, I’m not a reverse engineer, and I hope that many of you are, a quick look at Asrar showed that it was using the PGP for Win executable Cleopatra, and with the key management looking like PGP, it is possibly nothing more than an Islamic GUI for open source PGP and AES software.
But is it? Are the AES engines intact, or have they’ve been tampered with? Could they’ve been stealthed to send out keys? Both Islamist sources that I’ve seen and people like Bruce Schneier and his blog have expressed doubts about whether this is the genuine thing, or whether it’s a plant by NSA or somebody else.
I don’t know. I haven’t heard of anyone doing any proper tests. It’s an interesting question since it’s the only modern mujahideen crypto that’s out there. So if any of you would like to have a go at it, please, do. It’s in the speaker area, Asrar is there, I can provide anything additional that any of you might need, or any collateral material, but it would be lovely to get an answer to the question as when they put out Asrar, was it spiked, and if so, by whom? Or is it a trustworthy project? You’ll see how this has confounded the jihadists in a minute. So, that’s the tool set.

How have real terrorists communicated in the last decade? Since 2002 I’ve been asked to be an expert in several dozen terrorism cases, and in most of the big ones in Britain. And this is a sample of the cases from evidence in open court and from public sources. Going to look at about a dozen of them.
On 22nd of December 2001 Richard Reid attempted to detonate high explosive hidden in his boots while on a flight inbound to Miami (see image). Reid did use the method of Web mail dead drops to send messages to another jihadi in the days running up to his attempt at martyrdom, but no encryption.

In 2003 in January in the run up to the attack on Iraq, British police arrested 5 men who were alleged to be manufacturing the poison ricin from castor oil beans as a weapon of mass destruction. In fact, you can make about enough to off a medium sized sheep from a jar of castor beans, but no worry. The arrest of the so-called “Ricin Ring” was used to support the case for war on Iraq, and in February of 2003 the U.S. Secretary of State Colin Powell relied on it with much else in the way of notorious and, now debunked, evidence to make the case for war to the United Nations. Powell said that Iraq and bin Laden were at the center of a European wide terror ring (see image), securely and secretly communicating details of poisons and explosives chemistry.
This was found to be fiction, 2 years later, after the war, at trial. There was no ricin actually found, that had been an undisclosed scientific error, right at the start. The lists of chemicals which were claimed directly to link the plotters in Europe to Iraq and al-Qaeda turned out to be Internet copies of an identical document, in fact, one of the explosives manuals that had been kicking around, that we’ve seen, for 6 years, from the “Encyclopaedia Jihad”. So, this plot that was used to help make the case for the attack on Iraq, with its poisons, its plotters, and its secret communications, simply didn’t exist – no ricin, no encrypted communications, no plot.
Operation CREVICE (2004)

However, after the attack on Iraq, the situation did change. In Britain, earlier in 2004, March 2004, operation CREVICE. The police and security services arrested 6 Muslim men who’d been acquiring and storing very large quantities of fertilizer (see image). That’s one of them, on the left there, shipping it around in a storage site. The principal organizer, Omar Khyam, had created a shared e-mail dead drop account which he used to link to Canadian and American conspirators, and he handed it out to them, according to reports out of a training camp in Pakistan.

His collaborator Canadian Momin Khawaja was brought in and came over to Britain to supply the vitally needed detonators for their major explosives plans, and he claimed to have brought with him a specially invented detonator system which he called the “HiFi Digimonster”. Pretty good! When it was taken apart it turned out to be a garage remote door opening system.
7th of July 2005, operation THESEUS. This was the investigation of the 4 coordinated suicide attacks that killed 52 people in London’s transport system. No secret codes were reported to have been used. The official enquiry later found little evidence that 3 of the 4 bombers were big Internet users. However, they were Britain’s worst ever terrorist killers.
Operation MAZHAR (2005)

An international search tracked down an Islamic Internet activist who for 3 years had been tauntingly calling himself on the Internet “Irhabi 007”. “Irhabi” is Arabic for “terrorist”, so “Terrorist 007”. He was certainly putting it in their face and, from the appearance of Mr. Tsouli after his arrest, it looks like they may also have been putting it in his face.
Younis Tsouli was arrested in London and quickly found to be the long-sought-after “Irhabi 007”. When his computers were seized, it was found that he had managed and set up a series of Islamic websites on behalf of al-Qaeda using money stolen by carding. Tsouli and others in his circle were active members of the Russian-based carding sites “Carders Army” and “ShadowCrew”.
He was alleged to have raised over 2 million Euro from carding and he had become al-Qaeda’s principal video distribution outlet at the time. He hacked websites to place and then distribute new al-Qaeda videos. Now, Tsouli did use PGP, and used it properly. He communicated over Hotmail, MSN, and the usual networks, but only with a small PGP key directly, there weren’t many people in his network, and it appeared that they mainly used GAIM – that’s an instant messaging system which supports encryption over normal instant messaging.

Tsouli and his colleagues were cyber criminals as much as they were jihadis. From the evidence presented, Tsouli was a competent enough hacker and data manager. He did encrypt using PGP, but only with what seems to have been a rather small core of international and iKey-competent correspondence. And just as they were moving in, he had a plan for a new website which was going to look a bit like the YouTube for Jihadi videos, but it’d have a different name, “YouBombit”. As far as I can recall, “YouBombit” never went live.
Operation NICHE (2006)

This was in Scotland, my country. Mohammed Siddique was a young Scottish Muslim who was arrested on his way back from Pakistan. He’d been targeted because of the e-mails exchanged with 2 Internet contacts who appeared to be grooming him for jihad missions, or Shahid missions – suicide missions. One of them called himself “Oceanblue”, the other “Khalid the Shahid” – “Khalid the Martyr”.
Oceanblue at the time lived in the North of England, and he was already the subject of a very closed surveillance operation by the United Kingdom Security Service. Siddique was claimed also by a fellow university student to have announced that he wanted to be a suicide bomber, and he’d said so in a university cafe. After Siddique was arrested, Scottish police used an international warrant to subpoena all of the Internet records from AOL for the second alleged groomer, and this was Khalid the Shahid.

Khalid turned out to be an American living in a town he said was Centreville, Maryland, which doesn’t exist. However, Khalid’s real identity was established by the U.S. Department of Justice, and then they went through all of his records and screen names on AOL to see what he’d been doing as a groomer. So this is his list of screen names: “Khalid the Shahid”, “RyanRobinAnne”, “Miss Em 2301”, “Florida JW Gal”, and “Intel Cutie 2006”. It seems that Mr. Khalid was perhaps indeed a groomer, but you have to wonder who he was trying to groom and for what.
Mohammed Siddique was convicted, not of associating with that lot, but he was convicted, astonishingly, of assisting terrorism by just hyperlinking on a website he’d set up as a student. He’d hyperlink indirectly to al-Qaeda material which had been published elsewhere in the Internet, and he was sentenced to 6 years imprisonment for that. However, that sentence was fully quashed in January of 2010.
Operation PRALINE (2006)

Four Muslim men were arrested in the South of England for conspiracy to murder. At the center of the plot was this man, Aabid Khan, who was an active social networker who’d been under surveillance for months in a major operation. He was alleged to have groomed international contacts to join Jihad. There were large pinwheel diagrams of his associates, and this is one of the diaries they seized from him, talking about plans for assail to acquire equipment, mount an attack, and then the surveillance log outside an airport terminal. All of their activities operated in the way you’re now familiar with: normal Webmail, Hotmail, Yahoo, and some open codes, nothing more.
Operation OVERT (2006)

This you’ve got to remember, because it was the transatlantic airline bombing plot that triggered the overnight ban on passengers carrying liquids. This was a real terror plan, which the prosecutors in the later trial claimed could have caused more casualties than 9/11, and that could have been true if the bombs had gone off. They had their suicide videos lined up, they adapted 10 aircrafts targeted, they had arranged bombs that were made of 2 components disguised as fruit juices using copious quantities of hydrogen peroxide hidden in woods outside London. They’d acquired one special house for use for bomb assembly.

And the operation was run from Pakistan by a guy called Rashid Rauf and his British friend Mohammed Gulzar, both of them had come from Birmingham. They communicated with each other by open-coded e-mails. So, for example, when Gulzar was reporting to Rauf how much hydrogen peroxide he’d acquired, he referred not to H2O2, but to aftershave. So, again, in this major plot, the e-mail command linking back to al-Qaeda, there was no encryption, just open code and the use of varying Webmail addresses, in the hope of staying under the surveillance radar.
The suspected manager of this operation in Britain, Mohammed Gulzar, had come in to Britain and re-entered on a contrived identity with a new bride who disappeared as soon as he landed. He came with a laptop that had been reformatted, reloaded with Windows, and made to look really clean and sweet – wedding pictures, family chat, nothing more. Suspicious of itself, actually. But there was no attempt on this computer at hidden partitions, complex tricks, information hiding.

However, experience shows that in both sides of the business – the terrorists and the anti-terrorists – they make mistakes, and in this case both of them made inconceivably bad mistakes. For the terrorists, although they’d reformatted the computer, they had not wiped the unallocated clusters to null, as a consequence traces were left, clear traces, of previous research on hydrogen peroxide, which is completely damning evidence. They should, therefore, have been a conviction achieved in the view of the prosecutors. But this vital evidence was missed at trial. It was fished out of the unallocated clusters apparently too late to be used. As a result, although the co-conspirators who’d recorded their suicide videos were jailed for life, Mr. Gulzar was acquitted and walked free. These are the 8 who were accused of making bomb plots.
Operation PATHWAY (2009)

This investigation was blown to the entire world by mistake, when Commander Bob Quick, who was then head of British anti-terror operations was photographed by the press going into the Prime Minister’s office in Downing Street openly carrying operational orders. You can read them, right there on the image below to the left.
So they had to move very quickly and arrested 10 students in the North of England just hours later. The student group, many of whom have roots in Waziristan, in Pakistan, close to Afghanistan, had been under surveillance for weeks and they were suspected of being a bombing cell. But once arrested, the police found nothing to support that theory, there were no explosives, there were no chemicals.

One of the accused had been watched, however, going to Internet cafes, and e-mailing a Yahoo contact in Pakistan. The message talked about a Nikkah, or Islamic wedding. The messages were somewhat veiled, “Hi Buddy… my affair with Nadia is soon turning in to family life … I met with Nadia family …we .. have agreed to conduct the Nikkah after 15th and before 20th of this month”. However, there was no Nadia, and historically and culturally jihadis have often used the word ‘Nikkah’ to talk about suicide operations or attacks. There’s a cultural reason for this, because what they’re thinking of, bless them, is 72 virgins in Paradise whom they’re going to marry when they move on from the plane of this world to Jannah.

And the reference to dates got the police very scared, because they read this message as: “We’re going to attack our targets between the 15th and 20th of this month”, which was days away. The messages were being sent to ‘Sohaib’ at a Yahoo address in Pakistan, you’ll find that that address was actually used for contacts with other alleged jihadis in North America. Whether these messages refer to a genuine bomb plot or simply to a fantasy by the Islamists who were in Britain trying to kid on the people in Pakistan that they were going to do something – we don’t know, but throughout the communications there was no attempt to suggest encryption or use encryption or PGP. Once again, code terms, regular open e-mail.
Operation CLUTCH (2010)

The man named Anwar Al-Awlaki, was the head of al-Qaeda in the Arabian Peninsula until his demise. Based in Yemen, he was at the beginning of this year the effective leader of al-Qaeda, given Osama bin Laden’s silence. Rajib Karim was an IT engineer living and working in Newcastle, he worked for British Airways, his family came from Bangladesh, and he and his family members supported the resistance organization “Jamaat-ul-Mujahideen Bangladesh”, or JMB.
He was an avowed Islamist who sought to overthrow the despotic current rulers of Bangladesh, and he was prepared to do hijra, or to die, in context for that cause. The senior members of JMP communicated using something they called “Tadpole”, they’d invented it themselves. And through his brother, Karim (the IT worker) was put in direct contact with the al-Qaeda leader he revered, Sheikh Al-Awlaki, and they communicated using Tadpole.
Karim wanted to be sent to fight in Bangladesh, and Al-Awlaki personally urged him to stay patient and aim higher. This, by the way, is the Tadpole encryption system opening page (see image). Al-Awlaki went back to him and said: “Our highest priority is the U.S., it’s much more important. Is it possible to get a package, or a person with a package on board a flight?”
So, you have here, effectively the boss of al-Qaeda talking to somebody who might help him arrange a new transatlantic bombing plot. Al-Awlaki also urged the British air engineer to use the “Mujahideen Secrets” programme we’ve seen – “Asrar;” he said, “Please, use Asrar”. But Karim (the IT worker) was reluctant to reply, and he said this: “I have a slight concern regarding Asrar. It was released in the jihadi forums, and the kuffs” – us – “have access to it as well. I don’t think it would be too difficult for IT experts to crack the software. And I don’t think it’s wise to leave encrypted texts in email, it just draws more attention. I feel our process” – that’s Tadpole – “is a lot better, where we paste encrypted text into a .doc file…”

So, Tadpole is better. They had a communication protocol for using Tadpole which was an extended cloud version of what had been going on. Take the cleartext, use some code book substitutions, apply punctuation editing, and then encrypt using Tadpole, rename the TXT file deceptively (not really convincingly) as DLL, PDF or something like that, and then upload it to a cloud sharing site, they used SpeedyShare, they used 2shared, they used others. Once you’ve got the path to the cloud sharing site, they created a short URL using Notlong in particular, and other services, and then you’re left with the very short alphanumeric string on the particular site, so there’s a shared secret that when you send a message which is in fact a short alphanumeric string, it is the name of a short URL on the Notlong site. So they used that and then they used also, or tried to use, I think, Torpark with the Firefox browser to anonymize some of their activities. So, a number of things going on there.
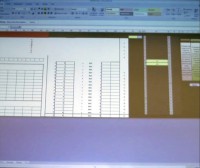
Now we should look at Tadpole as we come to the end here. So Tadpole, the JMBs-invented encryption system, is an Excel spreadsheet, although it takes a mighty long time to load; it’s an XLSM sheet, and it has plenty of macros loaded into it, so they are going to be the engine of this system. The front page (Sheet 1, A1) is a deceptive one, but if you jump right over, you’ll notice I’ve taken out most of the columns, so we’re over to column GZ where you have macro buttons marked “Encrypt” and “Decrypt”, and then some code structures just over to the right there. All of this was hidden on the top-level pictures and so on, and if I just unhide between these two cells here (see image to the left) we will find the directory and instructions for encrypting and decrypting, you just simply drop onto these spaces, to encrypt dropper or pull off the decryption from this one using a specific directory, so they have specific communication keys assigned to each pair of communicating parties.
So what are they actually using? What is Tadpole? A little look at the code in some of the boxes reveals what Tadpole is, you can see it just appear there: it’s simply the HLookup function of Excel, that is to say a simple one column lookup vector.
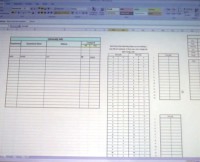
Another column in this thing points to tables of values which are located on Sheet 2 (see screenshot). If you go to Sheet 2 there, you can actually find the lookup tables, here they are, encryption and decryption – single-column, fixed monoalphabetic substitutions. Okay, one alphabet per communicating pair. Well done, guys! You have re-invented the ciphers from about 4 centuries before Christ, as first used by Julius Caesar in the alphabetic shift cipher – 55 years before Christ, “De Bello Gallico”. Furthermore, an Arabic mathematician is credited with the first break of monoalphabetic substitution ciphers about 1200 years ago.
So you see the comic genius of this situation, which an IT worker, who’s competent, says: “Let’s not use the Asrar, that’s kuffar stuff; let’s start and re-invent the wheel by going back to millennia”.
Tadpole was so secure (read ‘insecure’), that you can assure the message traffic was being read almost immediately. So when on the 10th of February, 2010 a message came from Sheikh Al-Awlaki specifically talking about targeting, and Karim replied saying: “We would like to choose some better targets, we should choose better targets, I agree the blood and wealth is halal, and we should think about targeting planes and passengers there”. So they moved in and arrested him. Now, Karim also used PGP Desk, his computers were found to hold several PGP Desk encrypted volumes disguised as RAR compressed files, and inside them he had the Tadpole program that you’ve seen and other Tadpole encryption.
That’s actually all from me today, thanks, and draw your conclusions.




























