
 During his talk ‘OPSEC for Hackers by The Grugq: because Jail Is for wuftpd’ at HITB 2012 Conference, The Grugq, a well-known information security guru specializing in studying anti-forensic techniques, advises online freedom fighters out there on how to avoid getting busted.
During his talk ‘OPSEC for Hackers by The Grugq: because Jail Is for wuftpd’ at HITB 2012 Conference, The Grugq, a well-known information security guru specializing in studying anti-forensic techniques, advises online freedom fighters out there on how to avoid getting busted.
This is going to be a talk about OPSEC. It’s actually not very technical; most of the problems that people have with OPSEC are non-technical in nature – basically, they say too much. It’s intended for freedom fighters, so if you’re out freedom fighting on the Internet, this is useful for you.

Very briefly, we’re going to go over an introduction on what OPSEC actually is; a methodology for how to implement it. Then we’re going to spend quite a bit of time looking at the LulzSec indictments to see what they did wrong and the OPSEC fails that they had. Then we’re going to go over techniques to help your OPSEC, and then technology that you can use specifically to make OPSEC easier to do; and then a brief conclusion.
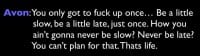
So, the problem that we’re facing is one that was expressed well on The Wire: it’s that you only need to fuck up once… (see right-hand image). One mistake is enough to be fatal. This one’s pretty awesome, right? So, you’ve only got to fuck up once, be a little late, be a little slow, just once, and you can never ever not be late or not be slow just once. Therefore you need to plan for that, you need to put methods in place to make it less likely that our mistakes will be fatal.
Intro to OPSEC

So, briefly: what the fuck is OPSEC? OPSEC, in a nutshell, is – keep your mouth shut, just don’t say it. The less you say, the harder it is for people to figure out what you’re doing. You need to guard your secrets; you need to, basically, operate on what we call a need-to-know basis – generally speaking, no one needs to know. The less you tell people, the better off you are. And you need to work hard so that you never get in a position where people can blackmail you.
This is reflected later on in another slide, where we say one law at a time. Basically, you do not want to give people an opportunity to take control of your actions or your life – it’s a terrible idea. So, in short – shut the fuck up, alright? If you don’t say it, then you don’t have to encrypt it or try to protect it.

This is an excellent guide to OPSEC (see left-hand image); it’s specifically for people who smoke weed – they’ve got a slightly different set of rules, but they’re aiming at basically the same thing. So, you need to be careful, you need to be conscious of what you’re doing, and you need to keep your fucking mouth shut. Again, the less you say it, the better off you are for it. As always, be paranoid, you need to be proactively paranoid; paranoia does not work retroactively. Mistakes you make will come back to haunt you.
You want to be tidy, so you want to make sure that you don’t leave contraband lying around. In the example of a freedom fighter this will mostly mean things like not leaving incriminating evidence on your laptop, making sure that your incriminating evidence is stored on your Jump Box, which will be the first hub that you reach before you start doing your freedom fighting activities on the Internet. You’d make sure that it’s always encrypted, that it’s not left lying around, that it’s not left in the state where other people can access it and copy it. You’d make sure that it’s not on your conference laptop, so that when you go to conferences and people break into your hotel room and copy your hard drive, they get nothing. Basically, you need to minimize the amount of stuff that’s left lying around that other people can find.
When you’re talking to people in an environment that might be monitored, which is whenever you’re talking to people, never be explicit, so don’t say: “Let’s go freedom-fight the hell out of Sony”, and also don’t use code. The clever codes that you come up to talk about stuff are terrible. They’re very easily, broken, so this example: “I would like 2 green sweaters and 1 mushroom pizza” – that is not a good code.
On the other hand, do use code words – cryptonyms are much better than being explicit, so if you’re going to be discussing a particular freedom fighting activity against a particular target, have a cryptonym set up for that target so you could say: “We are freedom-fighting the hell out of the Achilles”, and not “We are freedom-fighting the hell out of Sony”. That way it creates an additional layer of security so that if your conversation is monitored and logged, it is harder for people to understand what’s going on, and it is easier for your defense later on that you could say Achilles was not Sony, so that was actually not what we were talking about.
You need to provide less ammunition for people to try and go after you. You want to make sure that you are not breaking a large number of laws, that you get busted for one and then they find all your hacking kit; that would be bad. Similarly, it’s better off if you don’t do drugs, because, for example, with ‘weev’, who got busted in New York, they couldn’t get him on a hacking charge, they got him for drug possession. They will find a way to get you, so make it harder for them in that regard. And in general, camouflage is always good.

One methodology for doing OPSEC is, basically, you need to think about how to put the plumbing in first, so you need to set up your environment for OPSEC before you actually start doing things. You need to set up your cover identities before you start using them.
My recommendation will be that you create a cover; your cover is basically an alias, a fake identity. Then you need to work on the legend, which is history, the background and supporting documentation for that cover.
For example, one very famous cover is the case of the man who never was, which was a guy who died of pneumonia that was dumped overboard during World War II next to Spain with fake documents for the D-day invasion; and the idea was that when found, these fake documents will be taken as legitimate and would act as disinformation against the Nazis. It worked: he had 42 pieces of identifying documentation on him, from ticket stub for a movie to his driver’s license, to his officer ID. He had a huge amount of background documentation to act as bona fide, which, basically, made it appear that he was who he said he was.
 You need to do the same thing: having a simple Gmail account is not sufficient; you’re better off if you create an entire fake persona with a fake Twitter, fake Facebook, and so on. Even better if you can get fake photographs which appear to be of some other individual, and create this entire persona. And then you become that persona first, so you inhabit that before you create your online alias, your online usernames, and so on. And then when you do your freedom fighting activities from your online alias, when that gets compromised, the person that takes the heat is your cover, someone who doesn’t exist. And it’s very critical that you never contaminate. Contamination is when there is contact between 2 cover identities or 2 aliases, or in this case between your real identity and your cover persona. So be very conscious of contamination – avoid it like the plague.
You need to do the same thing: having a simple Gmail account is not sufficient; you’re better off if you create an entire fake persona with a fake Twitter, fake Facebook, and so on. Even better if you can get fake photographs which appear to be of some other individual, and create this entire persona. And then you become that persona first, so you inhabit that before you create your online alias, your online usernames, and so on. And then when you do your freedom fighting activities from your online alias, when that gets compromised, the person that takes the heat is your cover, someone who doesn’t exist. And it’s very critical that you never contaminate. Contamination is when there is contact between 2 cover identities or 2 aliases, or in this case between your real identity and your cover persona. So be very conscious of contamination – avoid it like the plague.

This is actually from the Ten Crack Commandments by Biggie Smalls – he has an excellent guide on how to conduct an illegal business, or illegal activities, without going to jail (see left-hand image). Never reveal your operational details; don’t tell people how you do, what you do, or what you are doing. Never reveal your plans: don’t let people know what you plan on doing or what you intend to do. Never trust anyone; this particularly goes for people you’re operating with, they are not your friends, they are criminal co-defendants. You want to make sure that they are not in the position that they can do harm to you if they get busted, and there’s a high likelihood that they will, because they are probably dumb, that’s why they’re doing what they’re doing.
You need to never confuse recreation activity hacking and freedom fighting activities. Recreation is shit that you do for fun; freedom fighting activities should be treated like a business, it’s an operation. You need to plan who you’re going after, you need to pick your targets, you need to select, you need to actually invest some time and effort into that, and then when you conduct your operations, you need to do that in a systematic and logical fashion, and you need to be careful about how you go about doing it. If you’re just going around popping boxes because it’s fun, you will go to jail.
 And never operate from your own house. For example, the Iceman who got popped a while ago, who was documented in the Kingpin book by Kevin The-hard-to-pronounce-last-name – he would rent hotel rooms and use those hotel rooms to operate from with a huge Wi-Fi antenna to hack into neighboring businesses and then steal their bandwidth to use that. So, that would keep his house contamination free, free of contraband. That’s a bit extreme; if you have the capability of doing that, you should do that, but at a bare minimum you have to make sure that you are using TOR before you go anywhere else. TOR provides a level of anonymity. However, you are better off just not using your own house.
And never operate from your own house. For example, the Iceman who got popped a while ago, who was documented in the Kingpin book by Kevin The-hard-to-pronounce-last-name – he would rent hotel rooms and use those hotel rooms to operate from with a huge Wi-Fi antenna to hack into neighboring businesses and then steal their bandwidth to use that. So, that would keep his house contamination free, free of contraband. That’s a bit extreme; if you have the capability of doing that, you should do that, but at a bare minimum you have to make sure that you are using TOR before you go anywhere else. TOR provides a level of anonymity. However, you are better off just not using your own house.

You need to be proactively paranoid, as I said before. Paranoia does not work retroactively – you need to plan in advance to be terrified of getting busted. And you need to work with that in mind all the time otherwise you’ll make mistakes and go to jail. You need to keep your personal life and your freedom fighting activities completely separated. You want to make sure that people who know about your freedom fighting activities do not know who you are, and the people who know you personally should not know that you are conducting freedom fighting activities. It’s dangerous for everyone: if you want friends, go to the pub; don’t hang out in IRC and hacker channels to meet people, it’s a terrible idea, you will go to jail.
You want to keep your personal environment contraband free – as I said earlier, you want to make sure that your own equipment is kept neat and tidy. You want to make sure that all of the evidence that you’re generating is not kept on your personal equipment, that it’s kept on your first Jump Box, on your hot box. It’s not a situation where if you get busted then it could be used against you. It’s a situation where if it gets busted, it can also not be used against you. It shouldn’t be on your person, ever.
Obviously, don’t talk to the police – it’s a dumb idea. And never give anyone power over you, which, again, is the one law at a time; or, similarly, don’t let people blackmail you, don’t get into a situation where there are other people who can control your actions. If someone else is in charge of your actions, then it’s going to end very badly – like you have no ability to control your own life at that point; that’s not where you want to be.
So, you might be thinking: “Wow, that sounds hard. Why do you need it?” Very simply: it hurts to get fucked. You’re better off going to the effort now and not going to the pain later, or with the army quote: “The more you sweat in peace, the less you bleed in war.” And it’s important to remember that no one is going to go to jail for you.

If you’re trusting people to keep their mouths shut, which you should never do, they won’t. This is why VPNs are not actually secure. VPNs would only be secure if you trusted that the operator of the VPN is going to go to jail for you. This is not going to happen, as these dudes (see left-hand image) found out. That would be Hammond and the other one, and then two other dudes. No one is going to go to jail for you. When Sabu fucked up and got busted, he flipped immediately, same day, and turned everyone else in. Your friends will betray you; you really cannot trust these people.
LulzSec: Lessons Learned

So, Hammond, who actually had reasonably good OPSEC activities, ended up being busted, because he revealed a large amount of personal profiling information during chats, which were then used to incriminate him later. So, here’s the LulzSec indictments (on right-hand image). Hammond at one point says to Sabu he’s been arrested for weed to 2 weeks in county jail, and then he says: “Don’t tell anyone, because it could compromise my identity, but I am on probation.” If you have to say “Don’t tell anyone”, you shouldn’t be telling that person. If you know it’s going to compromise your identity, why the fuck are you telling it to anyone? Never ever do this; never trust anyone, particularly your criminal co-defendants.
Violation: Never trust anyone
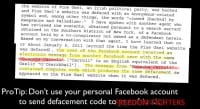
Ok, this is hilarious. This dude, Donncha Carroll, some Gaelic name, had been defacing political websites for Irish political parties in order to get the defacement code to put up. His friend used Facebook to send it to him (see right-hand image). They sent a copy of the defacement code via Facebook Messenger. Don’t do that; that’s a terrible fucking idea. So, his Facebook in his real name is now linked directly to this. There you go – ProTip: don’t use your personal Facebook account to send defacement code to freedom fighters; terrible fucking idea.
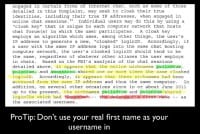
Again, when he was logged into IRC and talking with people, his username, the username that he used on his computer or on his IRC client before he logged in, was his real first name. And then, regardless of which nickname he used, which handle he had on IRC – his IP stayed the same, his username stayed the same, and he would do things like ‘/nick’ in the same channel to swap from one ID to the other (see image to the left). It turns out that that’s not very effective. That is not a good way to hide your identity. So, clearly, in this case you want to never provide personally identifiable information in your online name, and you want to avoid contamination. He did not avoid contamination in this case, so each of those usernames, each of those online IRC nicknames was contaminated by the others.

He directly contaminated in this case (see right-hand image), CW is Sabu, the covert witness. Sabu says to him: “Who is this?” And he is logged in as polonium and he responds: “This is palladium”. Again, don’t contaminate. You need to know which identity you are using.
Violation: Don’t contaminate

In this case Hammond was talking with Sabu and telling him about his lifestyle choices and how he operates. In particular he mentioned this very unique thing that he is a “freegan goddess” (see right-hand image). Freegans are people that dumpster dive for food. So, when he was under surveillance by the FBI when they thought they had the right guy and they observed him dumpster diving for food, that demonstrates that he’s a freegan and they could link it back to the statement that he’d made earlier. So, he had provided profiling information in his online chats, and that was used to bust him. A good example of keeping your personal life completely separated from your freedom fighting activity is to not talk about things that are personally identifiable to you.
Violation: Keep personal life and freedom fighting separate

This one is fucking genius (see right-hand image). We’re back to Donncha, the dude who used Facebook to send his defacement codes. He also used his home IP address; he used his actual home computer to log in to a compromised Gmail account to access one of the Irish police Gmail accounts. Don’t do that; definitely do not operate from your own home, that’s an incredibly fucking dumb idea. So, again, don’t connect to your target directly from your home IP address. You would think that this would be obvious, but never operate from your own home.

Hammond had also contaminated previously; he had used his own home IP address when he was hacking into some white supremacist sites. He hadn’t been busted for that, but he had been put on lists. That’s an important thing to do – to avoid being put on lists. They used lists of people who were known hackers from previous activity, and this was one of the lists that they used when they were narrowing down who the potential suspects were. Never operate from your own home.
Violation: Never operate from your home

They actually did some really impressive stuff: they used Wi-Fi triangulation to figure out which Wi-Fi signal coming from his house was actually his and figured out that it was coming from the rooms that he rented, tracked that down, and then from there, I’m assuming that he had some Wi-Fi encryption – it’s unlikely he was just using an open network, but they hopped onto his network, and then they used that to do a ping trace, and they also linked the MAC address of his computer against the statement that he’d made earlier about how he uses Apple products. They used the MAC address to show that he was using a Mac, and he had said earlier that he was using a Mac. So, again, this was used to compromise his identity and pop him, and that is because, again, he revealed operational details of what he was doing. So, don’t reveal your operational details, don’t tell people how you are doing things.

This is another example of how he revealed operational details: he complained frequently about how TOR was slow, how YouTube didn’t work and how annoying it was to use TOR (see left-hand image). When they were monitoring his traffic, they were able to show that all of the traffic leaving his house was going directly to TOR, so that was used as a piece of circumstantial evidence against him as well. By him revealing operational details of how he conducted his activities and how he operated, it was possible to then observe those particular operational details in action and link them to him.

This is an amazingly stupid activity. Here Sabu was supplied with an IP address from the Gmail logs. When they went to the Gmail logs of access to that compromised Irish police site, they found some that were anonymous and appeared to originate from Ireland. They said: “Can you find out who this is? We believe it’s palladium’s”. Sabu took that IP address and said to palladium: “Do you recognize this IP address?” And palladium, because he’s a fucking genius, said: “Yes, that looks like the one I connect from” (see image above).
Also, palladium had said that he was using a particular VPN network to connect to his targets. The IP addresses from the Gmail logs were from this particular VPN network, and again Sabu asked him: “Do you use the Perfect Privacy VPN?” And again, palladium answered: “Yes, I use that VPN”. Please send me to jail…

All of the access to the compromised Gmail accounts occurred from the guy’s home address or the one VPN that he’d stated that he uses. So, obviously, he’s going to jail. Once again – never reveal your operational details, do not tell people how you operate, don’t tell them what you’re doing.
Violation: Don’t reveal operational details

In this case palladium was insufficiently paranoid (see image). After he got busted, they took him to an interview and they showed him logs that they had collected from Sabu of the IRC channels where he was doing all of this stuff, and they said to him: “We know everything about you, we’ve got the logs, as you can see”. Then they released him on bail, he gets back on these compromised IRC channels and he says: “Hey everyone, I know for a fact that the feds are monitoring these channels”, and Sabu says: “No way, I don’t believe you, why would you think that? I’m certainly not a covert witness”, to which palladium says: “I was shown them during my interrogation.”
So, he’s now not only confirmed for a fact that he is polonium by verifying that he was busted and has been interrogated in this way, he’s now being in the same channels that are being logged as stating that he was just arrested and interrogated. It’s shockingly dumb.

Then Sabu starts sort of quizzing him again to make sure he knows who this guy is. Sabu is acting proactively paranoid, like: “I don’t know who you are. Who are you? You’re saying shit’s being logged, I know shit’s being logged. You’ve just shown up out of nowhere.” He says: “Yes, I don’t want to tell you who I am, because I don’t want to be associated with a compromised handle”, and then he points out that he was raided, and again verifies that he is who he says he is (see image above).
The chat that I showed earlier where Sabu says to him: “Who is this?” – he responded with the username of the individual that was arrested. Again, you have to be proactively paranoid. Here is a huge warning sign: when he got raided and when they interrogated him, they asked him about a large number of other people involved in the chat, but not about Sabu, because obviously they don’t need to ask about Sabu – they’ve already got him and he’s acting as a covert witness. So, that should be a red warning sign: if out of your entire gang one guy gets arrested, and he’s asked about informational details of everyone else except for one person, there’s a very high likelihood that this one person has already been arrested and compromised. So you need to be proactively paranoid and make sure that no one involved with you is going to be able to compromise and reveal information about you.
Violation: Be paranoid
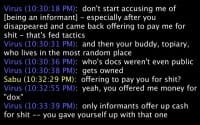
Here’s a guy that actually did good. This is Virus (see image). Virus was in a chat with Sabu, and basically Virus says: “Do not start accusing me of being an informant, especially after you fucking disappeared and came back offering to pay me for shit. That’s fed tactics. And then your friend, fucking Topiary, that no one knows where the fuck he is – he’s never been docked, no one knows who he is, he gets fucking busted,” and Sabu is like: “What? I never did that. Who offered to pay you for information?” And Virus points out: “Yes, you offered me money for docs. Only informants ever offer up cash for shit.”
So, again, here’s a warning sign: if someone disappears for a while, then they come back and start offering to buy information about things, cash is one of the things that feds are able to throw at a problem. They might not have the intellectual resources, but they have the financial resources, so once they compromise someone, they can then start using money to get other information. If someone starts offering up money for shit, he’s probably not a hacker, because hackers generally have no fucking money, otherwise they would be penetration testers, and penetration testers don’t do stupid shit. There is actually a happy ending: Virus, who is smart and proactively paranoid, has not been busted.
Happy Ending: Virus is still free

This slide (see right-hand image) is basically just for examination later on; it discusses various ways that you can contaminate an identity, so it lists different activities that the feds can do to correlate between online handles and use that to figure out that all of these handles are associated with one individual. Then they try and figure out who that one individual is. So, never contaminate.
Violation: Never contaminate

Here is just the information on how, once they believed that Hammond was the guy to go after (see right-hand image). They started conducting surveillance on his premises, on his domicile, where he lived. They used that surveillance to link his online activity of the sup_g handle to his presence in his home. When he was at home, they would call up Sabu and be like: “Is sup_g online?” And then when he would leave, they would call up and say: “Is sup_g online? Cause he just left now.” And they used that correlation between online activity and physical activity to further link Hammond to the sup_g persona.

Everyone recognize these? (See left-hand image) This was a JPEG that was put up on defaced sites by the fucking genius w0rmer, who is now in jail. He got busted, because when he uploaded this picture, which was sent to him by his girlfriend in Australia, he never removed the Exif metadata, which included the GPS tags for where it was taken, which was from her home, which was then linked to her Facebook account where her Facebook boyfriend was w0rmer. This is incredibly bad OPSEC.

Then, after he’d gotten busted, he went and posted a huge dump of his reasonings online on Pastebin and sent that out (see right-hand image), so he has made the job of his public defender incredibly difficult: “This is my name, this is my online handle. I was taken to the office, I turned over all the evidence I had, I’m not going to jail. I hate myself, I’m a dumbass.” He fell for one of the oldest tricks in the book; the FBI agent basically said: “You have no skills, you’re no good”, so it’s kind of like nagging – basically, the guy doing the interrogation will belittle the abilities of the person they’re interrogating, and the large ego of the person they’re interrogating will cause them to then correct the mistakes and demonstrate that they actually have the skills that are being demeaned, and in that process they confess to everything.

Here he points out in particular that neither the DPS administration nor the FBI understand the complexity of SQL injections (see image). I would guess that the FBI might understand the complexity of SQL injections, particularly if they’re interrogating someone who does not understand the complexity of Exif data.
Those are some examples of dumbass fucking things that you can do and how they will end you in jail. It turns out that it’s pretty low-hanging fruit that you need to go after. It’s very difficult to be sufficiently paranoid, but being more paranoid than these dudes isn’t that hard.

So, techniques – basically, you need to put in the plumbing. Plumbing is all of the stuff that you’re going to use to maintain your cover identities and to keep them separate from your actual identity to create an environment where your personas appear to be legitimate and real and are not actually in contact with who you are.
The problem is: plumbing is fucking boring. It’s not exciting to go and create a fake Facebook account and generate fake activity and make it appear legitimate and make sure that every time you do this, you do it from the correct IPs and all this other stuff, and that you never make mistakes on that, and on and on. It’s tiring, it’s boring, and it’s really not fun. And my advice, by the way, is use Gmail, because it’s a pain in the ass to set up Hotmail or Yahoo – that shit sucks, and then they ask for money if you want something like more than 10 MB of space. Gmail is actually fairly good for that. Obviously, it’s all monitored.
The awesome thing about plumbing is if you’ve done it correctly, then nothing happens. The important thing is, of course, you have to put it in place first, because paranoia does not work retroactively. Really, you have to be proactively paranoid; you have to worry about all of this shit before it happens.

So, if we talk briefly about personas, you need to have legitimate personas, ones that are vaguely believable. Again, an awesome quote from The Wire: “He knows my name, but my name is not my name. And to them you’re only The Greek. And of course, I’m not even Greek”. So, in this case they have set up very legitimate personas which provide a strong level of protection so that even if the other criminal co-defendants are compromised, they will not be able to reveal information that is actually useful against these 2 individuals.

That’s why your handle should be something like Jose, rather than your name. The problem is, basically, you are you. You are a unique butterfly, you stick out in the crowd. Really, what you want to do is you want to be someone else. If you’re someone else, people will be distracted from wanting to know who you are. So, as you all notice, he’s wearing a mask (see right-hand image).

The primary danger that you will face when you are using an online persona is contamination. Contamination is when there is contact between any cover identities or your real identity. That contamination will occur when they interact, and it can then be used to trace from one compromised identity through to the other, so it’s always important to keep them completely separated and never interact. They need to be in isolation from each other.
You also need to do layers, so simply having an initial cover identity is not sufficient. Once you have one cover identity, you then start creating sub-aliases from that. It’s better to have multiple cover identities so that when you get paranoid and you believe one has been compromised, you can phase it out rapidly and move another one into place.
An important thing to realize with the cover identity is that the time when it is most compromised is when it appears to be most effective. So, once it’s generated a sufficient, large history and legend and it’s got enough background, enough interaction with a whole bunch of other people, it’s at this point that you need to kill it and roll in a new one, because it’s at this point that it has generated enough interactions to be dangerous, that it is going to be the most compromised and the most interesting to other people. And it’s at that point that you want to get rid of it and then move on to a new one.

You need to use technologies that fail closed; you need to make sure that you do, for example, TOR before you do anything else. TOR will provide a level of anonymity so that if your other techniques get compromised or broken, then at least you have TOR to fall back on as a final layer of defense. TOR is not foolproof, but that’s why it’s part of a layer defense, and it’s part of your last layer, so that there is a level of anonymity around you before it gets to anything else.
You should have your back stop persona, which is your sort of primary cover identity, and then you have your sub-aliases underneath that. For instance, you can have your primary cover identity, set up a secondary cover identity and use that secondary cover identity to create your online handles and have layers of defense in that regard. So, you would basically become your primary cover, your primary cover will become your secondary cover, your secondary cover will become your online handle, who would then go and do freedom fighting activities. When they’re compromised, there’re layers that need to be unwrapped. And if you’ve been diligent in avoiding contamination, it’ll be hard to link back through those multiple layers.

One way you can avoid that is to avoid profiling information (see right-hand image). The problem with profiling information is when you provide information about yourself or about where you are, and this can reveal your location geographically, it can reveal information about you that can be used to unmask and figure out who you are.
I’ve been having a discussion with some people about exactly how many weather events with time stamps you would need to correlate before you can figure out where someone is geographically. If someone gets on IRC and goes: “I fucking hate how hot it is today”, if you’ve got a time stamp you can start eliminating places that are not hot at that point in time. Then, later on he starts complaining about the rain – you could then use that time stamp to correlate for all of the areas that were previously hot that are now also raining, and so on. And from that you can probably track down someone’s geographic location. It’s likely not going to be easy, but again, it’s better off – when it’s raining – bitch about the heat, when it’s hot – bitch about the cold, and so on. Do some disinformation there, or just don’t talk about it.

The other important thing that you need to realize is that it appears very easy to create a cover identity and assume that cover identity and do it without contamination; it’s actually something that requires practice (see left-hand image). So, what you need to do is you need to do it several times in situations that are not likely to end up with you going to jail. You need to practice being someone else. You need to practice going through the steps of creating a new cover identity. As it says: “Amateurs practice until they get it right, professionals practice until they can’t get it wrong.” You need to get really deeply engrained that when you are your cover identity, you are your cover identity. You are not pretending to be your cover identity, you actually are that person, so don’t fall out of character.
Briefly on logging – again, The Wire has got massive amounts of respect for having some excellent OPSEC rules: “What are you doing?” – “Robert’s Rules of Order says we need to have minutes of the meeting. These the minutes” – “Nigga, is you taking the notes on a criminal fucking conspiracy?” Avoid logging useless information, so no logs – no crime. In particular, the logs that you want to have are things like your scan logs or information that you’ve pulled down, such as your password lists and so on. Those are useful pieces of information that can be used to conduct operations in future.
Pieces of information that are not useful are things like syslog. Your Jump Box does not need to know at which times you have logged in. That’s not information that is actually useful to you, and it could be used as evidence against you, so kill syslog. If you’d look at the script that was released with the Stuxnet CNC servers, that’s very good in how to strip down and eliminate information about what sort of activities you’re doing, and mitigating against the risks of unnecessarily logged information. Other interesting things that they do are, for example, they don’t call their botnet a botnet, they have a very primitive interface which appears to be juvenile, except that it’s simply making it uninteresting to the casual observer. There’s a huge amount that can be learned from the operational activities of these Stuxnet CNC administrators.

In terms of staying anonymous, briefly, if we go over some guidelines, you want to avoid revealing personal information about yourself. Any personal information that you reveal can be used to create a profile. That profile could then be linked to a subset of people on lists, so if you are at this conference, you are already on lists, I can guarantee it.

Anti-profiling guidelines: these are all you would think amazingly fucking obvious, but again, as you’ve seen, you will be surprised. So don’t discuss any personal information, don’t discuss where you’re from, what’s happening, what’s going on, or who you are. Don’t include personal information in your online identities – so don’t call yourself 5.6ft 180lbs White Guy 1988. That’s a horrible fucking name, unless you’re actually not a 5.6ft 180lbs White Guy.
Avoid creating handles which are obviously linked to you in some way. When you’re discussing with people in chats that will be monitored, which is, again, all chats, don’t reveal things which are personally identifying, such as physical traits: your gender, your tattoos, your piercings, or whether you only have one leg, for example. This is why I never talk about my big penis, because that’s something that can be used to identify me.
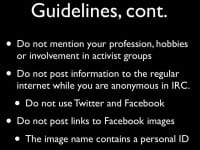
Don’t mention your profession, your hobbies, or your political activities – these are things that can be used to profile and identify you. For example, these are things that Hammond did when he said he’d been arrested in an action recently, which was the Republican National Convention, and he was one of the protesters who got arrested out of 120 people. It’s like: “Oh look, here’s one that’s been busted for hacking and one who says he was arrested during this event. Maybe it’s this dude?” So, avoid mentioning things you’ve done that can be identified.
When you are conducting anonymous operations, don’t post things to Cleartext – this was used heavily by that HBGary guy, what’s his name? Yeah, that dude who liked to correlate information between online activities from different accounts and used that as a contamination source to figure out who was who. We don’t know how actually effective that was, but again, it is a source of contamination when you are using an anonymous activity with a non-anonymous activity. Never ever post Facebook pictures, even if they are gorgeous tits – you will go to jail. For example, your Facebook link will contain your personal ID, and that will be linked to your Facebook account, and then they’ll know who the fuck you are.
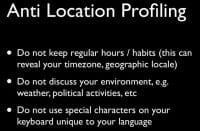
Another one – there’s a large amount to be said for keeping very irregular hours. This will prevent locating you in a particular time zone, which will, again, mitigate against some geographic profiling. Don’t discuss your environment, such as: “The elections are coming up and I really hope some political party wins.” And if you are using a keyboard which is unique in any way, for example, anything that is not a pure US 102-character keyboard – don’t use special characters. Again, that will be used to geographically profile you.

And if you think you’re awesome – you’re not. Basically, the NSA was doing buffer overflows in the 1980s; there’s a high chance that some of you weren’t even born yet. There is no way that you’re more advanced than them. However, for a long time the NSA didn’t really give a fuck about being the #1 dog on the Internet – it didn’t actually matter. So, for quite a long time, as hackers, we thought that we were the apex predator, and it’s just basically that the nation states didn’t give a fuck. We have ceded the position of apex predator to LEO. LEO is Law Enforcement Officials. It’s actually more generally meant in this case to mean nation states who now give a fuck. We now simply don’t have the resource to compete with nation states: they’ve got massive amounts of money, huge amounts of people, and they don’t face going to jail if they fuck up. So, again – shut the fuck up.
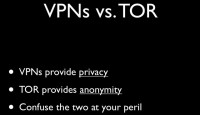
In terms of technologies that you can use to help ensure that you maintain good OPSEC, on the subject of VPN vs. TOR, a lot of people seem to have thought that VPNs provide anonymity; that’s not the case. VPNs provide privacy, TOR provides anonymity, so the difference is: privacy protects your data, anonymity protects you. Therefore if you are using a VPN service, you have to make sure that you’ve gone through TOR first, otherwise that VPN is simply a link from the end point to yourself. So, TOR to VPN – ok; VPN to TOR – go to jail.
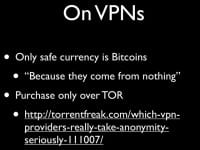
When you’re purchasing a VPN, the only safe currency you can use is Bitcoins. Liberty Reserve is monitored by the FSB, WebMoney is monitored by the FSB, if not administrated by the FSB. You might not care whether the FSB knows who you are, but you probably will be better off without them having that information. Again, when you purchase Bitcoins, do that only over TOR. If you’re looking for VPNs which do not keep logs, check out this link from Torrentfreak (see left-hand image). Again, I wouldn’t actually trust any of those VPNs who say that they don’t keep logs. PRQ and Mullvad are the ones that I would recommend. Ipredator is ok, except that it’s slow as hell.
A bit more on Bitcoins: you need to remember Bitcoins are anonymous, but they are not private, so all of the Bitcoin activity can be traced and can be used to connect back between different individuals, so make sure that when you’re using your Bitcoins, you do that in a way that is not going to contaminate between cover identities. At a bare minimum use unique wallets. Use mixers to do anything, apparently. I don’t actually have a good list of mixers that you can use to make sure that your Bitcoins have been mixed thoroughly. It’s something I need to address in future, but I don’t use VPNs, so it’s not a huge problem for me.
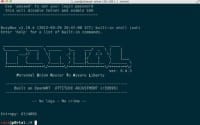
The other thing is you need to make sure that you fail closed, so in the Infosec cartoon where he forgets to enable TOR, he gets fucked. And the reason is, if you use TORbutton or TOR Browser, these are technologies that can fail open. You don’t actually have a good backstop. That’s why I have developed PORTAL. PORTAL is the Personal Onion Router To Assure Liberty (see right-hand image).
So, we’ve got 2 examples. TP-Link VR703N would be one of them; it’s tiny, it’s awesome. The other one is an MR11U, and it has been chipped to have more RAM and more disc space, and it also has an onboard battery that can run 4 to 5 hours. When you log in, you get a really awesome display of my ASCII skills and some NC colors, which is pretty fucking cool. No logs – no crime.

PORTAL acts as a router between your operational console and your online targets. It ensures that all of your traffic is always going over TOR. Your operational machine is unable to actually access the router itself, it cannot conduct any administration activities, it cannot log in or access it at all, and any traffic it sends will always be routed over TOR. As a result, if your laptop gets compromised, it cannot be used to connect back to someone else’s shell and reveal your IP address.
Similarly, when you use an operational laptop, it should be one that has no radios – no Wi-Fi, no Bluetooth, it should have no webcam, and it should also not have an online battery, so that if the police do come down and lock down the door, you can pull the power plug out and it shuts down, and now they have to deal with your encryption rather than with trying to break your online passwords.
In this case I use a mobile uplink – in Thailand it’s very easy to get 3G connections, like, I can just walk into a 7-Eleven and buy any number of SIM cards – obviously, I don’t actually do that, I send my maid to go and get them for me, or have her get motorcycle guys to go and buy them and bring them to me. It’s a lot easier and means that I don’t end up on CCTV purchasing a particular SIM card.
By using mobile Uplink it’s safer than going to coffee shops. At a coffee shop your Wi-Fi can be monitored by people in the environment, and you also have the problem that if you’ve got your phone with you and it’s on and you haven’t pulled the battery out, when you’re at a coffee shop, if they are able to backtrack the attacks to that specific IP during that timeframe, they will also be able to correlate that with logs of your phone being at that specific location during that timeframe. So your mobile phone can be used to uncover your geographic location, and if your IP address can be used to also geolocate, then those 2 can be correlated and you can go to jail.
With PORTAL we had to use some additional tricks on the earlier versions to get enough disc space to install. The unmodified routers have only 4 MB of Flash, and it is not possible to install TOR on 4 MB, because TOR takes 1.2 MB by itself and the operating system takes 2.7, and you lose because you have no space. So it’s not actually possible to get TOR onto a non-modified router without using a microSD in a mobile and a 3G modem. We have the SD card configured to act as an overlay device which gets union mounted and you can have between 2 and 32 GB of disc space, which is excessive on a router, but maybe you want to run BitTorrent as well…

This is the hardware that’s going to be supported (see image): the MR-11U, and the MR-3040; I would recommend these, they are fairly small, they have an onboard battery, they come in a neat carrying case, they’re pretty awesome. The MR-3020 sucks; it’s basically the 703 but bigger with nothing else, and the 703 is tiny, which is awesome. They both have USB; you can hit up my Github, where I’ve put up some more information about it, it’s not actually complete yet, but it will be soon.
So, that would be the technology to use. It provides an initial layer. I’m now working on another project on developing an operational console that you would then use when you’re doing your actual online operations. I’m probably going to use Raspberry Pi for that, because it’s fairly easy to get.
So, in conclusion: you can be a criminal, you can be famous, but you cannot be a famous criminal; shut the fuck up.
The Grugq: So, are there any questions?
Question: What’s, in your estimation, the average cost per persona?
Answer: In terms of time, you probably want to invest something like 6 months to bring it up. There has been some discussion of creating a marketplace for personas, because it’s just really a massive pain in the ass.

Question: In terms of money?
Answer: In terms of money, I wouldn’t know. In terms of time investment that I put into it to create a bare bones persona, it took me 3 days. Yahoo! fucking sucks. Hotmail is a pain in the ass, you cannot believe. I think that could probably be cut down by at least 1 day, because I had to do a fair amount of learning on-the-go, but if you calculate my time based on what I would charge for doing that, you’re looking at thousands of dollars per persona. The hassle of doing it is pretty epic.
I don’t know if the sweatshops in India that are good at clicking on CAPTCHAs and stuff like that could be trained to create online personas – basically, more filled-out spam accounts. They already have a lot of the infrastructure for that, and if they can be trained to do that, then they might be such a volume of stuff that the price goes down and the anonymity goes up, because it’s an online marketplace. That’s possible. I mean, if you’re doing this yourself, you’re looking at several days of work, and depending on how you would value them, that’s quite a lot of money. I mean, for you that must be tens of thousands of dollars.
Question: Prepaid credit cards?
Answer: I don’t really like them. So, the question was what is my opinion on prepaid credit cards? The issue I have with a prepaid credit card is the acquisition is inherently unsafe, like, even if you just walk into a local 7-Eleven to purchase one over the counter, you’re going to be tied to that particular card via CCTV. So, if they do trackback, they have your picture, which is not great, and they have your geographic location, which is, again, not great. So you have to travel to make sure that it’s not from your hometown, you have to wear a hat and a hoodie and look like you’re going to mug someone, which is going to draw attention, which is going to make it even more annoying.
 You also have the problem that when you use it, it is tracked and monitored online. I actually do prefer Liberty Reserve for those sorts of things. Liberty Reserve is monitored by the FSB, but the FSB basically doesn’t give a fuck as long as you don’t fuck with Russia. And if you’re Russian, as long as you fuck with other people, they, again, don’t give a fuck. So they have a very myopic view of things, and you can take advantage of that. It might not be completely foolproof, but it does provide this level of, like, it’s being administered the FSB, FSB is not going to cooperate with external entities because that’s just not what they do. And as long as you don’t piss in their tent, they’re not going to care about you, so you can kind of fly under the radar on that one. I would not be very comfortable with prepaid cards.
You also have the problem that when you use it, it is tracked and monitored online. I actually do prefer Liberty Reserve for those sorts of things. Liberty Reserve is monitored by the FSB, but the FSB basically doesn’t give a fuck as long as you don’t fuck with Russia. And if you’re Russian, as long as you fuck with other people, they, again, don’t give a fuck. So they have a very myopic view of things, and you can take advantage of that. It might not be completely foolproof, but it does provide this level of, like, it’s being administered the FSB, FSB is not going to cooperate with external entities because that’s just not what they do. And as long as you don’t piss in their tent, they’re not going to care about you, so you can kind of fly under the radar on that one. I would not be very comfortable with prepaid cards.
That could work. The idea would be to have a mixer or an online exchange for prepaid credit cards. If you actually do want to purchase prepaid credit cards that are anonymous, you can buy them with Liberty Reserve from Russian websites. It costs 20% more than the actual cost, but it is purchased through a layer of indirection, and it comes from criminals, so it’s probably not being monitored. And shut the fuck up about your prepaid credit card use.
Question: I wanted to ask a question about children. I work a lot with children, and when I do, I like to use a prepaid credit card. What are your thoughts on proxying resources through other countries, for example, paying a small child to get a credit card on your behalf in another country?
Answer: Basically, there is a lot of value to having an understanding of geopolitics. I had a friend who got busted for a different hack, but what he used to do was hack the shit out of Iran, all the time. He loved it, and his reasoning was: there is no way in hell that the US is going to extradite someone to Iran for hacking, it’s just never going to happen. So he could hack as much as he fucking liked, and no one would care. If you do similar things like that, for example, if you’re Malaysian, I’m pretty sure you can hack the shit out of Singapore with impunity. I don’t think that you’re going to have to worry too much about that. I wouldn’t recommend doing it, but again, that is the sort of understanding of the geopolitical environment that you can use to your benefit.
In terms of proxying through multiple places, again, I would recommend using TOR – it is sufficiently anonymous to keep you safe at that level. If you want a lot of proxies, you can purchase them from the LD4 botnet. The LD4 botnet has been set up from millions of bots across the world. You can buy – again, using Liberty Reserve – SOCKS proxies from the LD4 botnet, from AWMproxy.net; they have an online site that actually has a Firefox plug-in that will use their proxies for you automatically, so you can just click Refresh and get a new proxy sent to you from the botnet pool.
If you use that as a final hub, you’re probably going to be safe, because the bots are developed in such a way that no connections are ever logged. So you will be able to choose your geographic location, where you’re going to exit, your terminal point; you can probably choose down to a particular state or a city in the US. Similarly, you can probably choose a particular country in Europe. You can purchase from criminals – again, they will happily give up their logs once they get busted, but you should be doing it in such a manner that the logs that they can provide do not incriminate your actual identity, that they don’t allow you to go to jail. They have no monitoring of the end points, the actual traffic that goes back and forth. They can show that someone purchased stuff, but you’re basically safe.
Question: What is your assessment of the security of TOR as an anonymizer? If you’re into bad shit, how good is TOR going to be?
 Answer: So, the question is, basically, how secure is TOR against a motivated nation state. What happens with TOR is it’s completely effective against a motivated police agent; against LEO it’s fine. Against a nation state, the TOR network has insufficient resources and has sufficient bad actors that it is not actually secure. So, if you’re going to hack the shit out of the NSA, if you do really bad planning and you do not actually evaluate the targets that you’re going after, and you pick on a state actor that is going to come down on you like a ton of bricks, you will go to jail.
Answer: So, the question is, basically, how secure is TOR against a motivated nation state. What happens with TOR is it’s completely effective against a motivated police agent; against LEO it’s fine. Against a nation state, the TOR network has insufficient resources and has sufficient bad actors that it is not actually secure. So, if you’re going to hack the shit out of the NSA, if you do really bad planning and you do not actually evaluate the targets that you’re going after, and you pick on a state actor that is going to come down on you like a ton of bricks, you will go to jail.
There are problems with TOR in that if someone controls a sufficient percentage of the network, they will be able to monitor exit nodes and entry points, and that percentage is really low. I think there’s only something like 3000 nodes in the network at any one time. I’ve heard that you only need to control 1% of them to statistically have a guarantee that you will be both an entrance node and an exit node at some point in time, and you can use that to damask. So, if you can purchase 300 VPS accounts at $5 each, then you can set up 1% of the TOR network, and statistically, over a month you’ll be able to uncover a large number of users. So, TOR is actually not super effective for that, but what else are you going to do? You’re better off selecting your targets so that they will not be state actors.




























