
 Art Gilliland, Senior Vice President & General Manager of HP Software Enterprise Security Products, expresses his vision of corporate information security during RSA Conference 2013 keynote speech “Criminal Education”.
Art Gilliland, Senior Vice President & General Manager of HP Software Enterprise Security Products, expresses his vision of corporate information security during RSA Conference 2013 keynote speech “Criminal Education”.
Thank you very much and good afternoon! My name is Art Gilliland, and I’m going to share a little parenting story with you.
I am the father of twins; I have two young twins, a boy and a girl. And I’m also – some of you know that, fewer of you know – that I’m also a complete sci-fi geek. And when you marry those two facts together, as your kids start to approach the 7-year-old age, you really look forward to being able to sit down and watch Star Wars together.
So we sat down; we do a Friday movie night, probably like many of you do that are parents, because you’re wasted from the week and you come home and you want to sit down and you want to be with your kids, but doing anything active is going to be too much for you.
And so you sit down. We watch Star Wars, and I think about halfway through the first Star Wars marathon my kids got really interested, in particular my daughter, my son was not as interested, but my daughter got really interested in good guys and bad guys.
And like the true analytical geek coming out, I was really happy about it. She’s asking me to rate how good they are and how bad they are; Darth Vader – 10 bad, Jabba the Hutt – maybe 8 bad, Luke Skywalker – 7 good.
And so we go through this process, and then the question that was a little shocking to me: “Daddy, are you a good guy or a bad guy?” Deep breath: “Good guy.” Second question: “How good?” Well, she is 7, so: “10 good.” Nuances are probably lost at that age. So here we go, I’ve got 10 good, I’m a good guy, and so I ask the question back: “Do you want to be a good guy or a bad guy?” And I realize: do I really want to know the answer to this question? She’s 7, so, thank goodness: “Good guy.” Ok, excellent; and I said: “Why do you want to be a good guy?” She thinks about it, looks up in the air for a little bit; she says: “Daddy, because good guys win.” I better get back to work.
So, what I want to talk about today is a little bit about what I think we can learn by studying our adversaries. We’re clearly in a war; we’re in a war with the adversaries that we believe they are winning. And so what I want to take some time to do with you today is at least share some of the analysis we’ve done, and maybe offer some suggestions on ways that we can change the way we approach the problem that might help make us more effective.
So, as all good analysis should, let’s start with some data. 94 416 71 84 – interesting data; statistics from a lot of the recent reports. But why is it so significant? It’s significant because it helps to inform us about how effective our defenses are. It also helps to inform us about how much we’re actually listening to the data we’re producing. So let’s go into this intelligence, let’s go into the high level of this intelligence.

The first part of this: let’s start with the fact that 94% of the breaches that we report on, that our organization has been breached is told by a third party. So think about that: we’re spending so much of our resources to keep this adversary out, and they’re still getting in, and we’re not effective at finding them after they get in. That’s creating a challenge for us.
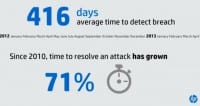
Second piece of data: we know that we’re struggling to find them, but they are inside our organizations for a very long time. 416 days on average from when they enter the organization to when we figure out that they’re inside, and that’s significant.
The second part of this, which I think is important, is even after we find them, over the last two years, the time it takes for us to remediate that breach, the time it takes for us, after we found them, to get rid of them has grown up to 71%, and that’s important because in a recent study that HP sponsored with the Ponemon Institute, we see that over the last year, from last year to this year, the cost that has assigned of with that increased, the cost of the breach has increased about 42% because of the increase in the length of time it takes us to remediate it.

And then the last piece of data: we’ve become very good, or much better, at least, at protecting our networks. We’ve become better at protecting the operating system. And that’s why we see about 84% of the breaches that occur are taking advantage of vulnerabilities that exist in the application layer.
What I take from this, or what we take from this, is that the adversary is innovating. If you combine this information – as we get better at the network, they move to the OS, we move to the application – if you take that and you combine it with the reality that they can go online now and rent botnet networks for $18 a day, or they can buy a Zeus kit for $7000 or so on average – there is something different going on in this adversary that we are competing against that we should be paying attention to. Something is different about the dynamic there.

And so if we’re going to win, we may need to think a little bit differently about this. I think there’s irony, obviously, that Sun Tzu is going to be our guide towards better security, but what he’s telling us is if you know your enemy and know yourself, you need not fear the result of a hundred battles (see image).
And so what that should inform us to do is maybe we should take a step back, we should look at our own capabilities and our own skill sets, and then put that in the context of how our adversary thinks about us, because they’re using what they know about us to attack us. Maybe we should learn more about them, understand how they see us, and maybe change our behavior a little bit to respond more effectively.

So let’s start by understanding a little bit more about us. Let’s discuss a little bit about how we are seen by the adversary. We are incredibly predictable to our adversary. We’ve defined our capabilities with a standard, whether it’s ISO 27001 or our PCI standards, or many of the other kinds of standards that we use, we’ve defined our capabilities along these standards, and we’re proud of it when we meet compliance.
And to be fair, we’ve done a phenomenal job as an industry of raising the low bar. These regulatory requirements, or these frameworks, have helped us raise the low bar. However, we should not be aspiring to the low bar, not when you’re competing with this type of adversary. And so we need to be thinking about that as we go through, this is something they count on. We’ve given them, through committing, a roadmap to our defenses.
The second thing they know about us is for us to fulfill our roadmap, for us to go along this roadmap we must behave within budgetary cycles. And so, building our capabilities slowly towards this end goal of compliance to these regulatory requirements or industry frameworks, we follow a pattern.
They know that, they can use it, they can be very disruptive to this pattern. As they innovate, they attack us in some new way that the standard is not capable of defending against. And so we rush to fix that, leaving some of the other projects behind because we can’t get to these things that we probably are still needing to do, but we rush because they’ve got this new technology attacking us in a new way, and our budgets don’t let us do both.

And because we’ve added all these different technologies and all these different categories, we are left to stitch those things together, partly because the technologies are different, and partly because the ways we implement those technologies are in different functional departments in our organization, whether it’s data center operations, or network operations, or others. Being able to respond quickly to see what’s going on and to remediate fast requires a much bigger audience within our organizations. And they count on that; they know it’s going to take us a long time, they know we can’t see everything. And that’s how they exploit us.
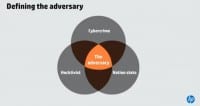
So let’s take a look at them and what we know, and talk about them. In our industry, and definitely in the recent past, we talk a lot about the individual actors. We talk about cyber criminals, we talk about nation state attackers, we talk about the hacktivists.
And while interesting and definitely press worthy, I think it’s a bit of a red herring for us in terms of trying to figure out how we should defend ourselves. In fact, it’s the intersection of those adversary actors that is the challenge for us. This adversary that we face is actually a market. It’s a market with a distinct process, and I’ll talk about that process in a second. But that market has a distinct process around it, and that’s the process of breaching our environments and stealing our data, for the most part.
This market does what a lot of markets do, which is, it organizes the actors, it organizes the participants. And now you have nation states and hacktivists, which hate each other, working together in a marketplace to share information.
And in just like all markets, you make more money if you specialize. If you’re excellent at one of the steps, you can differentiate in that market, and you can make more money. And so we see massive specialization around each of the stages of this process. And what is this process really good at? And this is the killer, I think, for us; this process is really good at monetizing the sharing of information. This ecosystem is incredibly efficient at creating, sharing and acting on its security intelligence. And that’s creating a huge burden for us, because they’re way faster than we are.
What should we do about that? We’ve talked a little bit about the standard that we use and the way in which we define our capabilities. But I think the way to get more clarity around that is to look more deeply at the process they give.
So what is the process that they use to define their attack? I use a very simple one, this isn’t super sophisticated or complex; it was actually created by Lockheed Martin, I believe, about 6 years ago. Maybe I’ve paraphrased it a little bit, so forgive me if there’s Lockheed Martin people in the audience and it’s not exact.

What happens in this criminal market is there are experts who understand how to build profiles, profiles of the attacked. And so I’ll give you an example of how this could work: I want to attack into company X, I’m really good at building profiles, I figure out who the top executives of that organization are, I start looking at their Facebook posts, I go on to LinkedIn profiles, I create these profiles. I know who Art’s friends are, I know what kinds of things he likes to do, I can see the pictures from where he’s been, Art may even check in at restaurants when he travels around the world – I get a ton of information about Art that makes him really easy to attack, because no one else should know that data. Only people that really know me should know, so they spoof a friend and they have that.
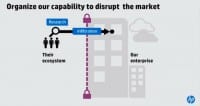
They put their hand upon the Internet and they say: “I’ve got the profiles of the top 50 people of X Company; who would like to buy that?” And the next person in line who’s really good at breaking in says: “I’ll buy those profiles; they’re better and it’s way less time for me just to buy them than to actually build them myself.”
And they either build their own toolkits to attack you, or they use a toolkit that they buy off or rent, or they rent one of the botnets that are out there to bang away on your websites. And they break in. And then after they get enough of these locations, they may own this, and this may be why the time it takes for us to find them is 416 days – they just enter, and they sit, and then they put their hand upon the Internet and they say: “I’ve got 50 access points; who would like to buy that?”
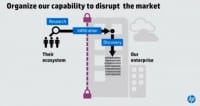
And then the person who’s really good at using those access points, figuring out where your sensitive data is, being able to map your environment, figure out your configurations – they create this map, they stick their hand upon the Internet,
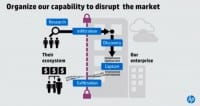
sell it to the next person, and so forth to get your data out, which then gets monetized and feeds this entire ecosystem (see images).
And so, that process, and I’ve named it as very specialized: are they vertically integrated bad guys? Absolutely, there are people who do all of this, nation states may do all of this. But if someone is more efficient and more effective at doing one of those stages, why wouldn’t you just buy it?
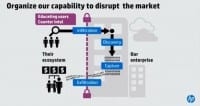
I think we need to define a new defense in depth for us. And part of that is building our capabilities at each stage of their value change (see right-hand image). And so, obviously, we do some of these things. We help to try to teach our users how to be less vulnerable. How can you interact with the Internet without hitting on the links that’s going to download the virus to your laptop? We spend money building capabilities to block the adversary, keep them out, whether it’s identity, whether it’s anti-virus, figure out your control.
But we spend a good amount of our resources to try to keep the adversary out of the organization.
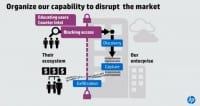
We need to be building technologies to help us find the adversary after they’re inside and before they’ve stolen data. And why is that? If we put all our money and all our chips in one category, in the blocking technology, they are the best in the world and they only need to be right one time. And so finding them after they’ve gotten inside before they’ve stolen data is important.
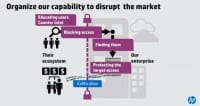
The second part is they are still going to get past that; they are extraordinarily good at evading us, and we see that in the data: 94% of the time someone else tells us they’re inside. And so – building more capabilities to protect the sensitive data we have (see left-hand image). And yes, there are physical attacks that are occurring, but I think for the vast majority of the folks in this room the real challenge for us is information theft. Customer information, our sensitive IP that helps us be more productive – that is the risk we face.
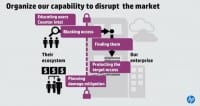
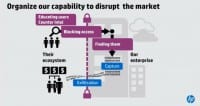
And then the last part of this is capabilities for responding after they have won (see right-hand image). The amount of money we spend in breach response can be massively mitigated if we can remediate faster and if we have a plan for how we’re going to talk to our customers, how we are going to sort of save our reputation as we go. Our job as security professionals is to mitigate the damage created by these breaches.
So that’s how we build this new defense in depth. I was very curious when we went through this process as we’re starting to evolve the thinking as we work with our customers, and granted this is a simple model, simplification of the model, I was interested: “How much do we spend as an industry today in these categories?”
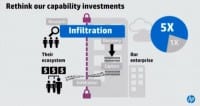
And we found out something very shocking in the research. We spend five times as much money in the infiltrate to block the adversary as we do in the entire rest of the chain. 86% or so of our expenditures go into blocking the adversary. And so we’ve built our defenses as a big shield around us, hoping that they won’t get in, but we’ve already defined that they are the best in the world and they only have to be right one time.
And this is where I think the big data benefit comes to us: understanding what’s happening, seeing what’s going on allows us to find the adversary after they’re inside and before they’ve stolen data. And that’s going to be a critical capability for us as we move forward with this type of adversary, this market-based adversary.
As you think about how we spend, even in this case; and I’ll give you one quick diversion, I apologize for this, one quick diversion about it: if you think about how we’re spending, even in our place, are we using the intelligence we have?
We already know, as we talked about earlier, that 84% of the breaches attack the application layer. If that’s true, then application security should be fundamental. But how much of that 5 times of the blocking are mitigations to protect that application layer still?
Focusing on the data, what the data tells us, and then trying to figure out what we need to do about it is part of the question, but we’ve got to act on it. And if we can act, if we do act with that data, then the promise of these big data platforms that we’re talking about is extraordinary.

The ability to pull data in from all different sources to really consolidate the intelligence, whether it’s from inside the organization or outside the organization, bringing that context together, so that we can understand what’s happening and really make a more informed decision because of that idea, is going to change the way we think about that.
And we’re currently working with customers to watch sentiment of their employees and of the outside, combine that with the access, abnormal access patterns that you might see in your environment, and with sentiment and access you can try to find those malicious insiders.
Other organizations are pulling data from cyber criminal networks to try and look for and scan for their sensitive information that might be sitting out there on the Internet to better identify if there has been a breach.
And we also have recently talked about the ability now to collect information, not only from your internal systems, and pulling all your intelligence from your internal systems, but also from the cloud environments you might be adopting, whether those are salesforce.com, or Box, or pick your cloud service provider, to be able to get a much better picture of the context that exists within your environment.
So, as a veteran of this industry, I am actually pretty excited about the promise that big data has for us. I think if we can figure out a way to make it actionable, that is going to be something that really changes the game for us. But I think we can make it matter more than that. I think we can make big data matter more for security. And to do that we need to make sure that our ecosystem is as efficient at finding, creating and sharing intelligence as our adversary’s ecosystem.
And so what I would pose to this audience and to our industry is a challenge. If you think about the capabilities we have today, with cloud computing and the power that that allows us to harness for building collective processing power, and you combine that infrastructure that we have out there, this cloud infrastructure, with the power of big data to analyze information.
My challenge is this: I think we can get a lot better if we share our information, analyze it in a central location. Big data as the basis can give us the power to build a platform for jointly analyzing security data, for sharing that information. And if we do that, I think we can make my daughter right, and we can fight and win together. Thank you very much!




























