
CEO of Tamoggemon Ltd. Tam Hanna covers the issues of mobile security at DeepSec 2011 conference, focusing on phone theft problems and mobile OS vulnerabilities.
 Well, today we are going to speak on attack vectors on mobile devices. Well, who am I? This is how I looked before I got into mobile security (see photo). You see I used to be a handsome man, now I look like a shaved monkey. I’m running a mobile computing consultancy, and we run websites, we do applications – basically, you name it and we do it.
Well, today we are going to speak on attack vectors on mobile devices. Well, who am I? This is how I looked before I got into mobile security (see photo). You see I used to be a handsome man, now I look like a shaved monkey. I’m running a mobile computing consultancy, and we run websites, we do applications – basically, you name it and we do it.
You might now wonder why you need mobile security. Who of you needs mobile security to keep his own phone safe? The reason is this thing here – today, smartphones are given not only to technical employees but everybody gets them: administrators, secretaries, programmers.
And for many less technical people, the user perception is that the phone is safe. And this has two reasons. First of all, there have been no large outbreaks so far. And secondarily, the phone is always in the pocket. And what’s in my pocket – it must be safe.
This issue is complicated because you cannot run antivirus software on a phone. Why can’t you run antivirus software on a phone? Because of the battery. So it is not possible to protect a phone using antivirus software. And the next problem is that users are stupid. There was a Symbian virus, it was called Cabir. It displayed a total of three warnings – not one, not two, but three warnings. But users clicked: ‘Next’, ‘Next’, ‘Next’…And there is a nice little sentence: ‘Users choose dancing pigs over security.’
As we already said, smartphones are soft targets because the programmers don’t know anything about mobile security. There was a guy today in the morning here who was speaking on the Windows Phone 7. If you look at what OEMs have been doing, it is just crazy. We have got the open operating systems, more and more smartphones, and finally smartphones become more attractive as attacking targets, for multiple reasons.
First of all, a smartphone today has a very fast processor. So it means you can really do some brute-force, you can do quite a bit of junk with those smartphone CPUs. Secondarily, smartphones connect seamlessly to the PC. And finally, not only can they call premium-rate numbers, but they can now deduct money right from my credit card. How can they do it? For example, in app purchases.
Now, you might say: “I bought the phone from a carrier, so the carrier should keep it safe”. And to some extent, I also agree that it’s logical thinking. But the problem is this: the carriers cannot protect everything because today smartphone not only has GSM or CDMA, but it also has a Bluetooth and wireless. And Bluetooth doesn’t go over the carrier. And the moment a carrier interferes with the Wi-Fi transmitter of the smartphone, people like me from the tech press start to wail: “This is an evil carrier!” So this essentially means the carriers cannot protect the smartphones.

Before we get into any of the more advanced technical attack schemes, what is the most common way phones disappear? Here is a picture (see image), these people are the Thuggee clan of India. When the Brits were still owning India, they essentially did what I am doing to you right not, but they didn’t give you things – they took things away. And in British English, still today a thug is somebody who you don’t want to meet for a drink.
And cell phones are stolen by two groups of people: one is the teenage thugs, basically people like me but five years younger. They steal them for personal usage and for resale. It’s a rampant issue in Western Europe. If you read the papers, in Austria there was a huge such scandal.
And now I am going to show you why carriers love theft. This guy here owns a beautiful Samsung smartphone. If I steal it from him, what does he do? He buys another one. And the carrier obviously charges outrageous prices for the phones.
And the manufactures also love theft, because let’s assume that a fourteen-year-old teenager who can’t afford an iPhone steals an iPhone. Then later he buys another iPhone, and the victim also buys a new iPhone, and now there are three iPhones on the market, so the market share of Apple raises. And so, why should Apple be unhappy with thefts? It’s true.
There is one way to stop these kinds of cell phone thefts, and this way is IMEI1 blacklisting. It works extraordinary well for example in the UK. But the problem is this – the governments don’t want to enforce it, because if you as a government admit that you have got a problem with petty theft, who would vote for a government which can’t control crime? Who of you would? Nobody, all of you are smart and honest.
And then of course, there are also the targeted attacks. If a person wants someone’s phone, he steals his phone, gets out the memory card; the data is usually unencrypted. And with that, it’s time for the first of the three platforms we look at.
Symbian was the first operating system to introduce some kind of security. It introduced the so-called Symbian signed code signing scheme. This meant that binaries had to be signed. And if the binary wasn’t signed, then the binary wasn’t allowed to do sensitive stuff, like for example call a premium-rate number. And the Symbian signed system was broken down on the process level.
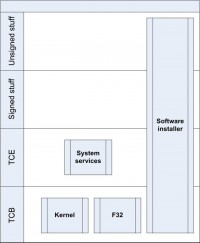
Why on the process level? The person who has a phone in his hand usually is the legal owner. Nobody of you hopefully shares a phone with somebody else nowadays. And so the point with this is that processes were divided into tiers (see image), and every tier required different types of signing and had different types of privileges. As I have already said, the capability is the token which must be presented to gain access to a privileged service. You might now be wondering why I am going over Symbian in such detail if the operating system is almost dead. I am going over it not out of boredom but because you meet these terms used in the concepts in every other mobile platform.
In regards to capabilities, there are three types of capabilities: TCB2 capabilities, then there are system capabilities, and then there are user capabilities which are essentially granted like they are granted on a J2ME3 application.
Another thing is data caging: Symbian protects some folders from access by other applications (see image). So it’s basically like a sandbox which we have today. But the difference between the sandbox we have today and the Symbian sandbox is that today you are allowed to access one folder. In the past, you were allowed to access all folders except for one.
And now, there is a problem. People like me develop applications. And if I have to send every application I have compiled to the signing house, have to pay 200 EUR and have to wait for a week – my productivity would be very, very low. Due to this, a developer certificate was introduced. A developer certificate allows me to say: “My company – Tamoggemon Ltd. – has these thousand phones. For these thousand phones, I – Tamoggemon Ltd. – act as a trusted provider”.
These developer certificates are easy to obtain. What I need is a capital company, like a UK Limited. It costs only about 200 USD to open UK Limited. These Limited’s are very easy to get. And with this site cer.opda.cn I can get these developers certificates. I open the Limited – the ‘Vakadukubananarama’ Phone Certification and Levitation Company. It is based in the Banana Street 64 in Timbuktu. The company’s house doesn’t care – they get the taxes. Cert department doesn’t care – they get the money. And I have a developer certificate.
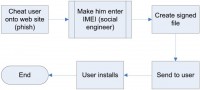
And this is the process used for a very dangerous trojan called SpitMo (see image). I am not going to explain in each detail how SpitMo works. SpitMo is a relatively simple trojan. The point is this: I am an attacker, I cheat you people to visit a bank website. On this website, I ask you to give me the IMEI number to send a security update to your phone. I collect these IMEIs. When I’ve got a thousand IMEIs, I request a developer certificate, it costs a few cents, so I waste a few cents. Then I send the signed files back to you, you install them, and then, when a Trojan comes in and an SMS comes in, I can read the SMS and send it to the server. These attacks are used to attack banks.
And of course I‘ve got some improvement ideas. The improvement idea is – why not in the future create a small unsigned application; make the unsigned application collect the IMEI; send the IMEI automatically to the server and automatically deploy the update? It would save you a bit of effort and make it even simpler.
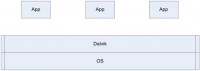
It’s time for Android which runs under slogan: ‘Android is open’, but it’s not only open for development – it’s also open for dangerous code. Android is essentially a huge Java virtual machine. As you can see here, there is the core operating system, the kernel running a virtualization system called Dalvik, and Dalvik runs a bunch of applications (see image).
And the problem is that the applications are written in Java, and Java is very easy to decompile. So if you look for some popular application, you find fifty versions of the same application by different vendors, which have been cloned by simply decompiling the Java code, adding some ad code to change the string of the ad, and re-uploading the application to the website. And even if the Google market bans me, I don’t really care because there are 50,000 other stores where I can give my applications away for free.

Android has a security model as well, but the Android security model is different from the Symbian security model in that there is no testing house of some kind which would be responsible for granting the certificate, but rather that each and every user himself decides if he wants to grant permission or not. So basically, every person decides for himself for his own phone. As you see here, if you download the application, it shows you a list of what the application wants to do (see image).
The attack scheme for attacking an Android phone is always the same. Every Android virus follows this scheme: it gets onto a phone by social engineering usually, or by masquerading as a legitimate application; and then it either sends data to the master or calls a premium-rate number.
 There is one pretty funny example called DroidKungFu. DroidKungFu abuses the Android security model. How does it do it? It takes place when an update comes, it’s typical for Microsoft. Who of you recently received the Skype update for Android from Microsoft? The thing is this: after you got the update, you suddenly got ads. Microsoft slipped the ads onto your phone during the update, because most people just see the arrow: ’12 updates are available’, and they click: ‘Get all’. And this is what is used by DroidKungFu: you intentionally get an outdated application which then updates itself, and during the update process you don’t get to see the update capabilities.
There is one pretty funny example called DroidKungFu. DroidKungFu abuses the Android security model. How does it do it? It takes place when an update comes, it’s typical for Microsoft. Who of you recently received the Skype update for Android from Microsoft? The thing is this: after you got the update, you suddenly got ads. Microsoft slipped the ads onto your phone during the update, because most people just see the arrow: ’12 updates are available’, and they click: ‘Get all’. And this is what is used by DroidKungFu: you intentionally get an outdated application which then updates itself, and during the update process you don’t get to see the update capabilities.
When DroidKungFu is on the phone, it basically starts sending home data, and now there is a funny thing. DroidKungFu contains an exploit which on some phones gets its root rights, but it does nothing with these root rights. So this is probably an unfinished feature which we will see very soon.
Next stop is Carrier IO. Let’s assume Christo is living in the beautiful United States of America. In the United States of America, the government wants to keep an eye on Christo. And someday, poor Christo runs after me, and I hit him over the head with a beer bottle. And he calls the emergency services: “A shaved monkey just hit me with a beer bottle, help!” And then, a service is activated which is called E9111. The government, the police who takes the call can interact with Christo’s phone to see where he is. Carrier IO was originally intended as a service for the government to track Christo. It was created by a company which was elected as one of the top 15 mobile companies in 2008. The company is also called Carrier IO. It lives on Android, on Blackberry, on Nokia, on iOS, on every phone you have those bastards right from the carrier as a free gift to you.
And the problem is this: their software reports quite a lot. It reports whenever you open an application, when you receive an SMS, if the screen is turned on or off, if the call is received, where you are, and what media you play. For example, in my case they could know that Mr. Hanna often turns on his phone at night, so this means his marriage is not so good, and it means he has insomnia. He listens a lot to DJ Shadow, so this means that his ears are already very damaged. He often receives calls from females who are working in his company, which means that there are too many females in his company and he must be sued for unequal distribution of the jobs, it’s mandatory in Austrian law. And this now sounds crazy.
This is not crazy at all. The data which my phone collects on me is sent via HTTPS to a central portal. And every carrier who has access to this portal can see data on every individual person. So really, he can see that I am using my phone at 2 o’clock at night often. And the point is I cannot opt out of this thing. And just in case anybody of you wonders why the carriers deploy it, they say they need the program to better analyze and understand myself so that they can offer me better products. I’ve got one question: “This stuff has been around for years; why am I less and less happy with every phone I get?”

Next stop, we’ve got the only religious sect in mobile – the ‘The Church of Apple’. You know their prophet recently died, so they are really on their way to becoming a church. Most churches, only when their founder dies, become really crazy. So now that Steve Jobs is dead, the situation can become really funny.
Well, the simplest way to get a donation from the church is to spam them. If I tell a member of the Apple church that I know something about Apple, they would willingly do anything just to know it first. So I just opened a website with some silly picture of an iPhone (see image), and all the believers click, click, click – ‘Steve Jobs, I pray to you.’ And they click, they click often – and they get a virus. They download a virus, ignoring the security warnings, because it’s Steve Jobs the great God.
There is another beautiful thing, because the Gods of Apple have decided their millions are too silly: if you buy an iPhone – you rent it. You can’t run every app on it. And so there are jailbreaks, where you visit a website and it unlocks your phone. And if any website can get root access, then an evil website can also do so. And now, my idea was – I open the website freelouboutins.com. For the non-females in the room, louboutins are expensive shoes, every female dreams of them. And on freelouboutins.com, you click there and you get the exploit. It would also work with me. But with me it’s much easier – freeredbull.com.
The next thing we have is a few exploits that are typical to Germany. Germany is a strong area for the church of iPhone, and so many attackers focus on the land where the believers are. And there is a thing called RenRen. Very little is known about RenRen except that it has popped up on users’ accounts, charged them 80 EUR – and that was it. And they said: “We didn’t even download anything”, many didn’t even have an iPhone. So this is relatively strange. Nobody knows anything about RenRen.
As I have already said, there are two ways: either it can be social engineering to get the password or it can be an exploit in iOS. But me not being paid, I decided to do some research on my own. And the first thing I did was I figured out this thing – an article in ‘Spiegel’ (see screenshot). The ‘Spiegel’ is a German newspaper. It is not particularly reliable, but on tech they are one magnitude better than the New York Times, and so one can believe them to some extent. And they gave us some good information. First of all, non-iOS owners get attacked also. So the article in ‘Spiegel’ tells us it could be phishing, and secondarily they gave us this string in Chinese. It’s the name of the app. And the name of the app is: ‘The world has difficult times ahead of itself.’

I googled it, and I saw this – a company called ‘RenRen’ is peddling the application. And the manufacturer string was only given partly by the ‘Spiegel’: ‘Beijing Quianxiang Wangji.’ When I googled this, it brings me to this poor fellow (see image). I sent him an email asking him: “My dear friend, could you tell me more?” And he thought: “This guy is Sha Gua”, which means as much as ‘f..king idiot’, the only word I learned in Chinese. So he has probably nothing to do with it. It is similar to another malware some time ago, which contained the string: ‘Mikko cut your hair.’ They meant a security expert from F-Secure who has got long hair, and he should cut his hair.
But the next thing was much more interesting. RenRen is a huge Chinese company. They are said to be the Chinese Facebook. And the really funny string was this: “The company believes it will be increasingly shifting toward third-party licensed games in order to leverage the platform effect of renren.com.”
And so, what do we know? RenRen operates an Internet website. And stock announcement about RenRen is that they are sitting on over one billion USD in cash and no debt. This is not like some American company which is worth ten billion but has fifteen billion of debt. These people actually have money.
And so I decided I am going to get in touch with them. I sent an email to their press department – I have a press ID so I thought I should send an email to them. I asked them just friendlily: “Please forgive me for getting in touch, bla, bla, bla…I would like to ask if the iPhone game (Chinese name) was in-house developed, or is it a third-party product?” The response came very, very fast, and it CC’d the chief of investor relations, for a normal peaceful question. And now comes the unusual thing: there was no actual info, and instead she wanted to know more from me.
People who have basic understanding of PR know that usually if a journalist is asking something short – you just answer this question because it costs you nothing. If somebody asked my company: “Mr. Hanna, how often do you shave?”, I send him back: “Every day in the morning”. Because if I send him back: “Where are you working?” – he might get angry, he might say: “He doesn’t know me, what an asshole, I will dig something out and write bad about his company”. So this was really, really strange.
But me be me, I sent them another friendly email, telling them I am working for a magazine where I really do work, and I want to tell them that this made quite a splash in Germany recently due to creative use of app purchases. I didn’t mention anywhere that criminal stuff or anything. And the effect was I never heard from them again. I am not a lawyer, so I can’t say what this means, but I can tell if something smells like phish, and I really smell the phish.
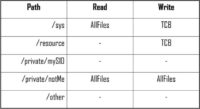
That brings us to another thing – the WAP scams. Today, especially with Nokia, people don’t buy apps, they want everything for free. And these apps are monetized via ad banners. If I click on such an ad on the cell phone, the web browser opens a WAP URL. And when a WAP URL is opened, you get the so-called MSISDN1 number. This number is worth gold because if I have your MSISDN number, I can charge you money by your carrier, and I get the money deducted off your phone bill.
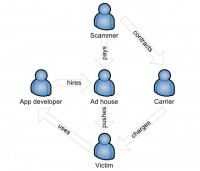
And this brings us a pretty complex economy of crime (see scheme). On the top, we have the scammer. The scammer pays the ad house to run an ad and in addition contracts the carrier to get the right to bill from MSISDN. The ad house then gets in contact with the developer who shows the ads of the ad house in his app. The user uses the app of the app developer who gets the ad from the ad house, clicks on the ad, the carrier charges the money, and the scammer gets paid. So we’ve got a total of five parties involved, and only one of them is acting criminally. Only the scammer is acting criminally. The developer doesn’t know anything, he is powerless. The ad house doesn’t really know much either. The victim gets owned due to stupidity and unawareness, and the carrier charges the money.
So again, the user clicks the ad, the WAP request is sent, the MSISDN is transmitted, and the carrier charges. And this is where the point gets hairy because the carrier has to pay the MSISDN charge within less then 24 hours. So by the time you get the bill and you complain, if I am the scammer I am already sitting in Panama with six girls, so I am long disappeared.
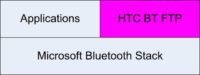
It’s time now to look at the staff who are working in mobile industry. First of all, most mobile programmers still are completely unaware of security. There is no secure chain, and this means there is a huge amount of unfound and exploitable errors in the operating systems currently. An example for this was the HTC Bluetooth FTP. It is a ‘bonus gift’ to smartphone users, which is given out from HTC. It allows you to access files in an outbox folder of the phone. And a well-mannered client sees he is in the outbox folder, so he is not allowed to go up anymore. An evil client sends the dot-dot command in the root folder, and then he can access /Windows. And the moment he can access /Windows on a classic Windows Mobile device, the device is down.
But why HTC Bluetooth FTP didn’t become too much of the problem was because Bluetooth FTP requires pairing. And if I would today pair with anyone of you, would you accept the pairing process? No. The average user wouldn’t even understand what it means ‘to pair’. So the practical risk was relatively low.
And we’ve got another benefit. The attackers currently are not particularly smart. Every mobile computing programmer can create a cutting edge mobile virus today. I develop mobile applications to make money with them, for sale, and I could replicate any of the Android viruses currently on the market with ease. Even my pupil who is in training could replicate most of them with ease. So we are not seeing any kind of really advanced malware just yet. But the attackers are socially smart because they need to get the people to accept installation request.
And secondarily, the attackers are greedy. There are no viruses like the infamous ‘Den Zuk’ which brought you the nice pictures, the beautifully rendered graphics. And there are no viruses like ‘I Love You’ which is basically a worm, and which only causes havoc.
The attackers today are greedy, and they do no technical development unless it is needed to make money. And as they can currently make good money with social engineering, why should they take more effort?
And finally, I have got a spring of new ideas for all those of you who are looking for new ways to create a better mobile virus. The last time I had such a set of slides, it was at Confidence 2010, and I told the people how to bypass the quality assurance for iPhone, Android, and Ovi Store. Two months later, the first attacks were surfacing using my vector. Manufactures were not always as reactive.
The first idea which I suggest is mobile ransomware. Already today, there are products like FlexiSPY: I install FlexiSPY on my wife’s phone, and then I can read her SMS and see her phone calls. And I suggest in the future data theft that attacks the credit card numbers and similar sensitive data on the phone to do identity theft and other ‘funny’ things.
The next thing is there are tons of exploits still open, the question is who finds one first. And then there is something which I personally expect to see after talking about this definitely. It’s an attack which bridges from the phone to the PC. In the past, the PC and the phone were synced, hot synced, active synced and so on. Today, it is easier because this phone can act as a USB drive. And if I connect it to my PC, the autostart mechanism of Windows starts the application. So all I would have to do as a virus is I would have to place an autostart application in the right folder – and profit.
And finally, another very funny thing I want to suggest is the mobile scam (see image). Essentially, you send the person one or another kind of email, and he then responds, and you either scam him off or you send him an SMS, and he responds to a premium-rate number. I predict a lot of new things like this will come up soon.




























