 The prominent malware researcher Mikko Hypponen and Security Advisor Sean Sullivan talk about evolution of Ransom Trojans, describe the recent GPcode variants and advise on ways to treat those if infected.
The prominent malware researcher Mikko Hypponen and Security Advisor Sean Sullivan talk about evolution of Ransom Trojans, describe the recent GPcode variants and advise on ways to treat those if infected.
25 years ago, when we started analyzing viruses, what was the worse type of damage user could suffer? Back then we saw lots of destructive viruses. They would just completely wipe everything on your hard drive. We even saw viruses like CIH which would try to reflash your BIOS, so you would even lose the computer itself.
And it’s probably still people’s public perception of what viruses do, they still fear destructive viruses. That’s right, but most of the damage you get when you become a victim of, and you get infected by a piece of malware today – it’s pretty transient. Let’s say you get infected by a spambot, and it sends lots of email spam from your computer. That’s not gonna hurt you. It’s gonna hurt other people, not directly you. Or, let’s say, there’s a keylogger which steals your credit card number. Well, there’s gonna be extra charges on your credit card bill, but you don’t really have to pay those, you can just complaint to your credit card company and get the money back.
So most of these problems are kind of temporary problems. But then we have Ransom Trojans. And Ransom Trojans are a special category of Trojans which directly hurt the user. These are cases where the computer is taken over by a Trojan which takes your files and holds them as a hostage.
We’ve seen a recent rush of some particularly advanced attacks. And this is actually interesting, because in fact one of the very first moneymaking Trojans in history, was Trojan called AIDS Information Trojan from, I think, 1988. And that actually was a Ransom Trojan already. So it did this, it encrypted your files, and you had to register the product to get your files back, in a sort of like antipiracy method at the time, but it was basically the same idea as we see today: Trojan takes over your computer, encrypts your files, and then you have to buy a key to recover the files.
We’ve seen some which were badly implemented, so that it was easy for researches to reverse engineer what the key was, and distribute that to their customers. But recently we’ve seen some that are hardcore and practically impossible to decrypt.
First GPcode variants, and the GPcode is the biggest family of Ransom Trojans for Windows today, were found in 2008, and they had problems in their implementation from the point of view of the attacker. It was actually possible to decrypt the files without paying.
But now for example, the latest versions of GPcode use strong encryption, public key encryption, they use AES with an RSA key. And we aren’t aware of any mechanism of breaking that if you don’t have backups. If you have backups, there is no problem, you just restore the files – and you are off, and of course that’s why we recommend people to use backup tools like the one we sell. So backups are the easiest solution. The next solution to get your files back is to pay, and of course you don’t want to pay this.

I was trying to follow up with one of these guys, I emailed the email address, pretending to be a victim myself. So I set up a temporary account, I emailed the guy and said I got this message, asked him what do I do, trying to trace back where he wanted me to send the money. And that was to a private person in Bosnia and Herzegovina, in Eastern Europe, and he probably was a money mule. But that’s where the money actually ends up going to.
Now, with the latest versions of GPcode, the way of sending money is no longer wiring it. Now they are actually asking you to buy these UK cards, prepaid credit cards, and transfer the money in that way. Again, it’s fairly anonymous.
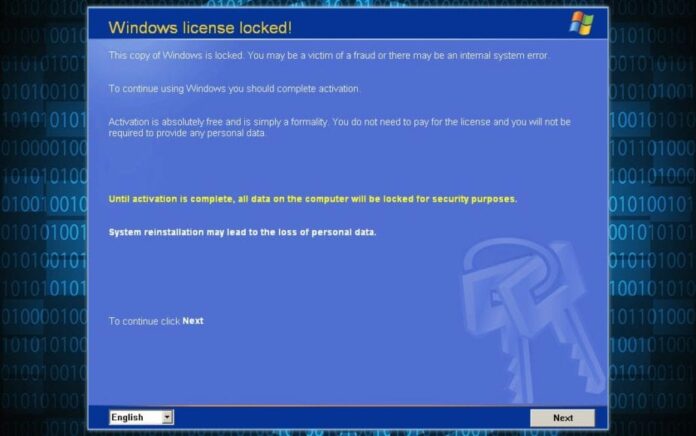
The colors and the fonts here look kind of like Windows installation screen. They pretend to be Microsoft, and it basically explains to you that you have to reactivate Windows, and it says: “Activation is absolutely free and is simply a formality”, and you can activate over the Internet or by dialing a service number; to continue click ‘Next’, and when we click ‘Next’, it shows us an error message: “Activation via Internet is not available”, which means the only way to activate this is to dial one of these numbers.
And it gives you different call centers you can dial for ‘Microsoft support’ that will give you the activation code. And these numbers are nice, like 002 612 2100, they look like some sort of service numbers, they start with 00, it’s an international number. And for example 239 00 239 – that’s Dominican Republic, so you’re calling far away.
I’ve come across numbers like these before, from another Windows mobile case: a mobile phone Trojan which was dialing international numbers in South Pole, in Somalia. So these are numbers operated by rogue operators. When these numbers are called, the call actually doesn’t go to Somalia, it doesn’t go to South Pole. It ends up in some much cheaper country, but they charge you the full price, and that’s how they make money.
It’s a billing system of a sort, so if I call Indonesia and I don’t have a paypal account, I call a special phone number, I get charged 5 EUR worth for the call, but really the slice that the person who owns the number gets is something like 4.50 EUR, and that pays for the software license or whatever it is you’re trying to buy. This mechanism is known as ‘short stopping’, so they stop the calls short.
Let’s call one of these numbers and check out what actually happens when you dial the number. (Voice on the phone) “Hello, welcome to the activation system, please wait for the reply and then enter your code, the system will provide you with an activation key”; and later (voice on the phone): “Line is busy, please hold the line, call waiting time is 3 minutes”.
So it is trying to keep us on the line for as long as possible; (voice on the phone): “Warning, please enter the code after the signal”. Alright, let’s put in the code 7*108#; (voice on the phone): “Thank you, your activation key is 1351236”.
The call duration was 3 minutes and 40 seconds. And as an end result, we did get the code, and that code indeed does unlock Windows, and you can use it again. In fact, the code is always the same, so if you get hit by this Trojan, don’t dial these numbers, don’t do what we did, just put in 1351236 – and you’re home free.




























