I don’t know what it is but generally I always get the last law at the conferences I speak at, so hopefully I don’t tell everybody, you know, too much of a tiring lullaby. I mean, there is somebody after us, I feel really bad for him but, you know, what are you gonna do?
Okay, there we go. I’ve heard that all the presenters have been having really bad luck today, like no demos were working and, you know, stuff like that. So hopefully ours will go better.
So about me: in real life, I play a malware researcher at Kaspersky. I was also a malware analyst at Microsoft. And contrary to a popular opinion, or what you may find on Wikipedia, Conficker was not German and Dutch slang for ‘ass f..ker”, it was just a play on words that I managed to come up with. That was my, like, biggest achievement in life so far.
Underground I was a Gold farmer1, wrote some bots for some games that people might have heard of. I’ll let people guess as to what that is, because I know what ‘Blizzard’ does to people. I’ll let Mike talk about himself right now.
 Mike Donnelly (author of the Glider2): I’m Mike Donnelly, otherwise known as ‘Mercury’. I created the ‘Glider’ software for ‘World of Warcraft’, sold about 4 million dollars’ worth of the software, got sued badly, lost 6.5 million dollars in damages, personally liable, peeled it, got most of it flipped over, but overall the process was, I would say, less than fun. As far as my underground identity, I have none. Once you get sued, everything about you winds up in court record: all your deposition, all your addresses – everything.
Mike Donnelly (author of the Glider2): I’m Mike Donnelly, otherwise known as ‘Mercury’. I created the ‘Glider’ software for ‘World of Warcraft’, sold about 4 million dollars’ worth of the software, got sued badly, lost 6.5 million dollars in damages, personally liable, peeled it, got most of it flipped over, but overall the process was, I would say, less than fun. As far as my underground identity, I have none. Once you get sued, everything about you winds up in court record: all your deposition, all your addresses – everything.
But on the plus side, I did have a ‘Glider’ customer bring beer to my house. He had looked me up, dropped the beer off and then he posted a message on the ‘Glider’ forums that said “Hey Mercury, go check outside your front door, there’s a six pack of beer”. And there actually was the beer. Going through the garage I didn’t see it, and I went out, got it. That was only ‘Budweiser’, but free beer is free beer.
So if you’re gonna get smoked for 6.5 million dollars, at least I got some free beer.
Josh Phillips: Oh, and I guess all two of you ladies here, he’s single and he used to be rich. I’m married, so I’m not so lucky. So our goal of this talk is to not make anybody an expert at game hacking, so if you came here for that then we are going to disappoint you. You know, we planned on just giving you some overview. If you don’t have any technical skills – we assume you have some to get at least something out of this talk – but if you don’t have technical skills, we hope that some of our game hacking, war games will be entertaining for you guys.
Something I will say is we don’t really have any zero-days, so if you’re looking for zero-days then you’re also going to be disappointed. But we don’t really feel we need to give any zero-days because, you know, it’s really easy to find them. You know, every game that’s ever released is gonna have a buttload of stuff.
“He who knows when he can fight and when he cannot will be victorious” (Sun Tzu)
So here is a nice quote from Sun Tzu and I think Mike has some experience with this – he actually chose to fight, he’s actually the only person I know that actually did choose to fight, and I guess you can ask him about how that’s going. So here is a brief legal blurb that Mike has experience with, and he’s gonna talk about that.
Mike Donnelly: Yeah, one thing I wanted to say is of course everybody knows I’m not a lawyer, so I can’t give you any legal advice. But I’m a person and I can give you personal advice when it comes to lawyers: when you get sued, you’re f..ked. If it gets to that point, you are in a lot of trouble, chances are it’s gonna end badly. A lot of people, such as myself, might think “I’ve got a good legal theory for what to do: I’ve got section 117, I’ve got DMCA 1201(f) interoperability, you know. Let’s go man, you can’t take me down!”.
It’s incredibly painful and expensive to get that far, so even if you have winning arguments, the chances that you get there are slim. I’m not saying you should never do anything where you might get sued, I’m saying you need to understand the serious of getting sued. It’s bad, so you should take steps to avoid it. If you have to sell from Venus or Neptune or the 7th dimension, try to get away to avoid getting sued, because the game companies, if you piss them off, will show up at your door.
Josh Phillips: China is a good place to be though. So, my disclaimer is ‘We’re weasels’. I guess maybe I am a weasel, Mike chose to do everything in public. I think that might have been a poor choice, you guys can decide. So, you know, the names have been changed to protect the innocent.
So why do we hack? I think it’s mostly obvious: you know, we want some ‘womens’. Did I mention that Mike’s single?
Mike Donnelly: Oh, come on man!
Josh Phillips: So really there’s a lot of money in this. Mike made 4 million dollars, my first competitor was making half a million a month – that’s pretty real money. Sometimes people might want revenge or cheating, but that’s not really child play.
 So raise the hands who would like to go to ‘Game Hacking 101’ school. I mean, I really wish that this was, you know, offered in my college but it really wasn’t. We are gonna get through some tools of the trade: IDA, Ollydbg, Your favorite memory editor/searcher, 010 Editor, Wireshark, Custom tools – you make them. If you don’t know any of these, maybe you should start looking at them. So I think most reverse engineers can’t live without it. It should be pretty obvious what you do with that – you disassemble some code (‘Ollydbg’ – Olly Debugger). If you don’t know what a debugger is, then you probably shouldn’t be here really either. You need the memory, something to search memory – most people use something like ‘ArtMoney’ or ‘TSearch’, something like that; they’re pretty popular. ‘010 Editor’ – if you are doing anything with file formats, this is like ‘god mode’. I think that anybody doing it without ‘010 Editor’ is, you know, failing. It also helps with packet captures if you want to see what the structure of a packet is. And something that’s very important is your custom tools. Once you get serious about game hacking, if you don’t have your own scripts for IDA to do all these sorts of magical things, then you are wasting your time.
So raise the hands who would like to go to ‘Game Hacking 101’ school. I mean, I really wish that this was, you know, offered in my college but it really wasn’t. We are gonna get through some tools of the trade: IDA, Ollydbg, Your favorite memory editor/searcher, 010 Editor, Wireshark, Custom tools – you make them. If you don’t know any of these, maybe you should start looking at them. So I think most reverse engineers can’t live without it. It should be pretty obvious what you do with that – you disassemble some code (‘Ollydbg’ – Olly Debugger). If you don’t know what a debugger is, then you probably shouldn’t be here really either. You need the memory, something to search memory – most people use something like ‘ArtMoney’ or ‘TSearch’, something like that; they’re pretty popular. ‘010 Editor’ – if you are doing anything with file formats, this is like ‘god mode’. I think that anybody doing it without ‘010 Editor’ is, you know, failing. It also helps with packet captures if you want to see what the structure of a packet is. And something that’s very important is your custom tools. Once you get serious about game hacking, if you don’t have your own scripts for IDA to do all these sorts of magical things, then you are wasting your time.
Mike Donnelly: One thing I wanted to add is these are the tools that you are looking at if you’re doing something professional, if you’re gonna build a big piece of software and sell it or run it, or, you know, take this on as a business. You can do a lot with nothing: you can duplicate items, you can find bugs in games just by being clever and tinkering, so this is like a pro-grade or what you would use to make money. Part of the Panel is hacking for fun, so I’m not gonna completely focus profit.
Josh Phillips: Yeah, there’s nothing worse than coding up a bot with a bunch of hard-coded offsets, and then, you know, the game releases an update and your stuff doesn’t work again, and then you have to start from pretty much ground zero.
So I’m gonna give you a bit of classification – basically, there’s like cheats, bots. I’m not gonna get into real deep details about this stuff. I’ll talk in more detail when the stuff comes up later on. There’s some really, I guess, motivated individuals who have written custom clients. One of my competitors in China wrote a custom client for ‘World of Warcraft” and pretty much destroyed us. They could run hundreds of clients per computer, and it’s really hard to compete with that when you can write, like, three or four.
 Mike Donnelly: What about this one custom client in particular? It’s funny – just raise the hands how many people here have played the game ‘Hellgate: London”? Okay, how many people that have played it were playing it six months later? One? Okay. Well, the reason I mentioned it is I know a guy that works with ‘World of Warcraft’ – German guy – and he got the ‘Hellgate: London’ paid and he thought it was awesome. So he wrote a clientless bot, he reverse-engineered the entire protocol – everything (their keyshake or their handshake), all the encryption. He had it ready for game at launch time, and then… thousands of hours, you know. This is gonna be the next while. So, you know, if you’re writing something for profit, think of it like a business, don’t be stupid.
Mike Donnelly: What about this one custom client in particular? It’s funny – just raise the hands how many people here have played the game ‘Hellgate: London”? Okay, how many people that have played it were playing it six months later? One? Okay. Well, the reason I mentioned it is I know a guy that works with ‘World of Warcraft’ – German guy – and he got the ‘Hellgate: London’ paid and he thought it was awesome. So he wrote a clientless bot, he reverse-engineered the entire protocol – everything (their keyshake or their handshake), all the encryption. He had it ready for game at launch time, and then… thousands of hours, you know. This is gonna be the next while. So, you know, if you’re writing something for profit, think of it like a business, don’t be stupid.
Josh Phillips: Yeah, that’s a lot of waste of time.
Then, there’s things like exploits. They can either be malicious or really get you a giant paycheck: dupes or, you know, ‘god mode’.
Asset hacks aren’t really worth it for the most part. You know, you can do some pathfinding if you can reverse-engineer the map formats and other assets. But pathfinding is super-hard, unless you’re going to do something like use recast navigation which is easy mode for solving a really-really tough problem.
So this is where we separate the ‘haves’ from the ‘have-nots’. People might not be able to follow. Hopefully they can follow.
So the skills that you need, you are probably gonna want to at least know ‘X86 Assembly’. If you don’t know that, then you’ve got a lot to learn, that’s gonna be a pretty big steep road ahead for you. The stuff isn’t really necessary, you can write some, like, lame pixel reading things – I think somebody presented that a couple of years ago here, it was pretty well attended and I wanted to punch the dudes because they were very cool. Yeah, noobs need not apply.

So memory searching is an arcane art, but that’s the skill that you definitely need. If you cannot master memory searching, it’s gonna be really difficult to do some static analysis and find these things. So I mentioned some games here – I’m sure everybody is familiar with ‘World of Warcraft’. Anybody not? Okay, I think everybody is. So they were one of the first games to actually use a commodity script engine (most games make the mistake of rolling their own). But they chose Lua1, and one of the side effects of Lua is you have this string embedded in your binary that tells you the name of the function. So if you have a reverse-engineering code and you want to know “Hey, how do I cast a spell in ‘World of Warcraft’”, well you open up IDA2 and you look for the string like ‘CastSpell’, and it will pretty much instantly take you to where the code is.
Mike Donnelly: I was gonna add one more thing on the Lua thing that it makes reverse-engineering a game incredibly easy. What you can do is you can create a Lua script to do what you want like show the spell ID, make sure it works and then you can just load up the game, drop your break point right where the Lua is, hit your test code and step right though it – just right there on the platter.
Josh Phillips: Yeah, script engines can make things definitely easy in reverse-engineering, there’s no technical challenge there.
 So brief history…I’m gonna go through some of these things pretty quick. ‘Ultima Online’ was probably the first major MMO3. I think it had around 225,000 users at peak, which is, I guess, pretty big compared to ‘World of Warcraft’ and, I guess, even some of the Facebook apps that have like 30 million people. Anybody play ‘Farmville’? No? Okay. I don’t believe you guys. So ‘Ultima Online’ was hackers’ heyday – I mean dupes, the cheats, people seeing invisible people, walk through walls etc. ‘World of Warcraft’, I think, definitely deserves a mention here as it was the first super-big one that had millions of people. It’s not so big compared to some other ones anymore, but it’s still pretty big. Chinese games are massive compared to ‘WoW’, if anybody knows.
So brief history…I’m gonna go through some of these things pretty quick. ‘Ultima Online’ was probably the first major MMO3. I think it had around 225,000 users at peak, which is, I guess, pretty big compared to ‘World of Warcraft’ and, I guess, even some of the Facebook apps that have like 30 million people. Anybody play ‘Farmville’? No? Okay. I don’t believe you guys. So ‘Ultima Online’ was hackers’ heyday – I mean dupes, the cheats, people seeing invisible people, walk through walls etc. ‘World of Warcraft’, I think, definitely deserves a mention here as it was the first super-big one that had millions of people. It’s not so big compared to some other ones anymore, but it’s still pretty big. Chinese games are massive compared to ‘WoW’, if anybody knows.
The thing about ‘Blizzard’ though is they do more than saying just ‘cease and desist’ – Mike can attest to that.
Mike Donnelly: Right, actually ‘Blizzard’ sometimes doesn’t send a CMD at all, they just show up like “Knock-knock…I’m a lawyer, here’s a draft complaint. Sign this paper and cut off your thumb, or we’re filing this”. That’s how they work. But ‘World of Warcraft’ is a big game, there’s so much money there that even if you’re only getting 1% market penetration, it’s worth the risk, ‘cause it is a risk. But if you’re gonna take a risk, it’s gotta be for a big enough game where you have some kind of profit base.
Josh Phillips: I’d like to add, sometimes ‘Blizzard’ will show up on your doorstep, and if you don’t happen to have connections with Polish mafia to chase them out with the baseball bat, then you’re gonna end up like Mike. That did really happen.
Even if your game is really small, you can still make a couple of grand a month, which for a lot of people is worth it, especially in Eastern Europe, South America – a couple of grand a month is still living like a king.
Mike Donnelly: Oh yeah, absolutely. If you just make, you know, a thousand bucks a month – that’s where I started – and I thought this was a mortgage, or car payment (depends on a car).
 Josh Phillips: So I mentioned ‘Eve’ and ‘Darkfall’. ‘Eve’ was, I think, the first game to actually use a commodity script engine – I think they were out before ‘World of Warcraft’. You know, the decompiled source of ‘Eve’ was released. I mentioned ‘Darkfall’, it was pretty massive – half a million lines of code. ‘Age of Conan’ – I think that was a big flop, I think a lot of people were excited about it. But the interesting thing here is they left a lot of debug strings. So I wrote a script that would search ‘IDA’ for something like ‘ClassName::MethodName’, and then I would have my ‘IDA’ script rename all of the functions in my IDB with this string. So that made it also a pretty easy mode. Then you have something like ‘Aion’ who tries to step up the barrier for game hacking, but they failed pretty miserably. So ‘GameGuard’ is actually a pretty formidable foe, and so is Themida, but if you don’t use any of the advanced features of either of these things, then it’s actually still pretty easy to bypass them. With ‘Aion’, you could just patch out a call and make it return ‘1’, and then you defeated their ‘GameGuard’.
Josh Phillips: So I mentioned ‘Eve’ and ‘Darkfall’. ‘Eve’ was, I think, the first game to actually use a commodity script engine – I think they were out before ‘World of Warcraft’. You know, the decompiled source of ‘Eve’ was released. I mentioned ‘Darkfall’, it was pretty massive – half a million lines of code. ‘Age of Conan’ – I think that was a big flop, I think a lot of people were excited about it. But the interesting thing here is they left a lot of debug strings. So I wrote a script that would search ‘IDA’ for something like ‘ClassName::MethodName’, and then I would have my ‘IDA’ script rename all of the functions in my IDB with this string. So that made it also a pretty easy mode. Then you have something like ‘Aion’ who tries to step up the barrier for game hacking, but they failed pretty miserably. So ‘GameGuard’ is actually a pretty formidable foe, and so is Themida, but if you don’t use any of the advanced features of either of these things, then it’s actually still pretty easy to bypass them. With ‘Aion’, you could just patch out a call and make it return ‘1’, and then you defeated their ‘GameGuard’.
So this is some brief overview of the types of hacks or exploits that have been in games that have been released. ‘Vanguard’ pretty much sucked, I think Microsoft wasted 50 million dollars on that pile of crap, and I guess that’s why they’ve cancelled, like, 3 more MMOs – they were probably afraid. So it’s like super powers.
Speedhacks have been around in every game imaginable. They are still available if you know how to do them in ‘World of Warcraft’ for example. With 2D games like ‘UO’ (‘Ultima Online’) it’s simpler, but with 3D games it’s really CPU intensive to track the movement of 20 – 30 thousand people, so they still really haven’t done that great of a job.
Mike Donnelly: Yeah, they just trust the client – we all know how ‘smart’ that is.
Josh Phillips: Yeah, if anybody here trusts the client, then you should probably leave…
So dupes are like what the Federal Reserve does when they go to the Treasury. They’re like “Hey, can you print me a million billion dollars? We promise we’ll have the American people pay it back”. Yeah, that’s really how you get rich. I’ve got a friend who did some hacks and was making, you know, close to a million a month. He at one point had two ‘Lambos’ (‘Twin Turbo Gallardo’ and a ‘Murcielago’), and now he is stuck with just online dream. I feel sorry for him.
Mike Donnelly: One thing on dupes before you go is this is a good display of just some of the tinkering. Figuring out how to duplicate an object is very much a non-technical thing. It really comes down to finding, like, an edge condition that the game developers didn’t think of. So it’s not some guy writing a clever piece of code – it’s somebody doing something weird, like, you know, maybe on ‘World of Warcraft’ you’re crafting an item, and while you’re casting the craft you trade one of the gradients and another player summons you. You know, all these weird conditions that the developer may not have thought of – that’s typically how you wind up with the dupe. You do something that they didn’t think of, or you can crash, like, a world server. So I could give Josh my sword of epic ass pounding, and then I crash the game server, and then when I log back in I still have it. But the point is that this is really just tinkering, which all of you guys know how to do, whether you’re pro reversers or not. It’s really just tinkering, and thinking outside the box. When you see the game, you see its zone, you see a pause – and you think, what if I’m in the middle of doing something at that time? The more mature games, they’re harder to find. But it really just does come down to tinkering.
Josh Phillips: I’d like to add, this isn’t like real-world security research where you find some bug in, like, ‘Adobe’, and then you spend three weeks figuring out how to exploit it and, you know, bypass ASLR (Address Space Layout Randomization). This isn’t like that. I wonder if they check whether or not I can substitute an ID with some other random player’s ID, or whether I can tell them that I just bought a million billion things for free. Yeah, so just a bunch of tinkering.
So I wanna talk about some, I guess, more detailed methods of hacking, like what you would try to do to, say, write a teleport etc. So basically, for teleport hack you look for the player’s position in memory and then you use your memory editor and change that value. And if you’re lucky, then you teleport – that’s really complex (not really).
Mike Donnelly: …Or you get banned.
Josh Phillips: Yeah, or you get banned or disconnected – that’s in an old game when they realized that people were gonna do that. It’s actually really surprising how naive a lot of game developers are. They generally don’t have any clue about how to write a game that’s hard to hack.
So you can go into more difficult ways. You know, if your game is more mature, like ‘World of Warcraft’, that’s how to deal with this stuff for, I guess, 7 years and they still haven’t done it correctly. You have to modify movement packets and, you know, forge the timing – stuff like that. It gets more complex but it’s still doable.
Speedhacks – again, you can get these off the shelf, they will work with every game. And if you’re lucky, then it still works with your game. And I don’t know what ‘squeezing network code’ means, I didn’t write that.
Mike Donnelly: Sorry. That’s actually just what I was talking about with lag hacks. And this still works on ‘World of Warcraft’, this works in every game today where you can literally unplug your Ethernet cable, move around in the game a little bit, and if you plug it back in before the TCP connection’s dead, then the game client will simply tell the server “Oh, here’s where I am”. It’s, you know, dealing with their congestion code, they have to accept some latency. So in a lot of situations you can pull out your Ethernet cable, walk past the monster, and all the logic to have the monster hit you is on the server side; of course the server doesn’t see you’re near the monster. Then you plug your Ethernet cable back in – good to go, you passed the monster without triggering anything. Don’t try it on wireless, ‘cause when you disable it you actually close the TCP connection. But if you can physically interrupt it just by pulling out the cable, it actually works, it works great.
 Josh Phillips: That’s pretty hi-tech.
Josh Phillips: That’s pretty hi-tech.
Mike Donnelly: Seriously…
Josh Phillips: Dude, that’s kinda lame…
Mike Donnelly: I think you’re gonna mention this, but that’s where you see a lot of chests and various dungeons. You know, in ‘World of Warcraft’ there’s a lot of dungeons, and you could kinda eek your way along, deep into a dungeon just by lag-hacking past the monsters and get to a chest, exist instance and get the money. That’s why there are no more chests in instances anymore.
Josh Phillips: I know who is responsible for that.
So, dupes…Anybody who doesn’t know what a dupe is? Basically you duplicate something, and you get a million billion of it or something like that. This is the key to making a lot of money, and this is how my ‘poor’ friend with the Lamborghinis got them. With the game he was targeting, it took almost a year before they figured out how to deal with this stuff. They were like “I think we have a problem in that, you know, gold is really available to everybody now, nobody has to work for it. I wonder what happened”. Like I said, these game developers are pretty naïve. They think “Wow, these guys are good at playing my game”.
A lot of games have multiple servers and things like that, so you just try to do things back and forth and hope that if you do it fast enough, maybe sometimes the server will lose track of your items and they’ll magically start filling up in your backpack. Or, like in a game where if you can die and your items go on your corpse, you have your friend go loot your corpse before his character is saved. And then, you know, magically when you guys both log in the server you each have your items. These are pretty basic, like we said – tinkering. Sometimes there’s no skill involved or maybe just really a lot of creativity, you don’t necessarily have to be a god in reverse-engineering, but it definitely helps.
Integer overflow/underflow things are also really awesome. You can get from zero to max pretty easily, that’s a pretty big number.
Mike Donnelly: Yeah, and that just comes down to tinkering too, where you take your armour on and off and notice that one of your stats isn’t going back the way it should. And these things happened in ‘World of Warcraft’, we’d have a guy sitting in Orgrimmar taking his helmet on and off a hundred times, and then all of a sudden he’s got, you know, thirty second minus one strength. And it really did happen.
Josh Phillips: Or maybe he just used a memory editor and took a screenshot.
Alright, my favourites like GM mode – company will ship the game out with, you know, the ability to reverse-engineer and flip a bit, and now you are like a GM and you can teleport people, you can kill things, you got the commands, which is pretty interesting.
Or stealing from NPCs…‘Age of Conan’ was one that was really rife with vulnerabilities. You could for example kill a GM. I don’t think they were very happy…
Mike Donnelly: That was the source player ID thing, right?
Josh Phillips: Yeah, you just, you know, tell the game that I’m this GM and I just died.
Mike Donnelly: With each packet coming up, you would say “I’m gonna sell this item”, and your player ID was in there. And somehow, this game server would believe you if you said you were someone else. You’re like “No, I’m so and so, and I’m selling this”. Okay…
Josh Phillips: Did I say that game developers are naive? I mean they work hard but…
So, UI hacks are pretty much worthless unless you want to zoom out really far – that’s pretty much what you’re gonna get from UI hacks. Maybe you can get, like, ghost mode where you can fly around the world and you stay still, but it’s not very beneficial.
Mike Donnelly: You can also do the language translation, ‘cause they had the thing where Alliance players couldn’t understand what Horde players were saying. That was all client side, so the actual text from the opposing player was sent to the client – it would just choose not to display it. So it’s actually a pretty easy hack to see it, but it’s not really marketable, I don’t know who’s gonna pay for that.
Josh Phillips: Yeah, good luck selling that. But it’s not very powerful – wow, you can talk to humans if you’re an orc… “I’m in your base killing your mans”…
I guess I’m gonna tell you exactly how to write a teleport hack. So the easy way to do a teleport hack is you’re gonna have to, like, find the player position in memory, use WriteProcessMemory to overwrite that, and then you’ll teleport. And you can also – if you know where the code is that’s responsible for updating player’s location – call that directly with some functions. Is there a teleport spell? You know, maybe there’s a ‘Lua’ function called, you know, ‘CastSpell’ and it takes the parameters like the location you want to teleport to, and the server doesn’t verify that…
Mike Donnelly: That’s basic tinkering. It’s not gonna work today but that kinda stuff is out there, and poking and prodding it is actually fun to find.
Josh Phillips: It definitely worked in some games. The hard way is when you actually have to get down to forging movement packets. You have to do some math, you have to reverse-engineer the structures for the movement packets and maybe adjust the timestamp so that you can teleport or run faster.
Logic attack – this is what we were talking about with ‘Age of Conan’. You could give fall damage to anything in the game, and that’s how you kill the GM. You told them that you had a million fall damage and he would die.
Mike Donnelly: That was funny.
Josh Phillips: So this could also be used maliciously in the ‘Age of Conan’ in that you could force somebody else to trade with you and they wouldn’t really know that they just traded with you. But you could also force an NPC1 to trade with you, so still useful and not mean. So I don’t feel bad stealing from computer characters. I don’t think any of you guys should either.
 Alright, so item dupes – that’s basically exploiting, I’ve talked about this before. I’ll say that server line issues in the ‘Age of Conan’ had some zoning a request, had zoning in ‘Final Fantasy XI’ and had zoning in ‘Ultima Online’ – just had these server lines where if you cast a spell on one side across the server line and you were fighting somebody, then you are f..ked.
Alright, so item dupes – that’s basically exploiting, I’ve talked about this before. I’ll say that server line issues in the ‘Age of Conan’ had some zoning a request, had zoning in ‘Final Fantasy XI’ and had zoning in ‘Ultima Online’ – just had these server lines where if you cast a spell on one side across the server line and you were fighting somebody, then you are f..ked.
Repetition attacks – you just basically move things back and forth from, say, a trade window to your backpack a thousand times a second. I mean, most people should do that by hand, right? The server eventually loses track of stuff and they start filling up in your backpack. Or maybe everybody knows ‘Diablo 1’ where you just drop an item on the ground, you run up to it and pick the item up really quickly on your cursor, and it appears in your backpack and on your cursor, so that’s pretty fun.
Asset hacking – I mentioned it – is definitely not worth it unless somebody else has published their work for you and you can borrow it. So basically what you do here, maybe some people have played ‘World of Warcraft’ and somebody has magically appeared on your side. I never actually played ‘World of Warcraft’, it’s too boring. I’d much rather have bought it. Year, I should have bought a Glider. So those people who either use teleports to go from one side of the battleground to the enemy’s base – you know, “he’s in your base killing your mans” (pretty confident it’s ‘mans’) – or maybe they modify the map to have this tunnel so they could run under ground and nobody would know or see them (maybe you could see his name on the screen or this little dot on the screen and you go like “Wow, where is he?”) – otherwise it’s not worth it, they’re really complex.
Real profit is definitely dangerous, like Niccolo Machiavelli said. You can get sued, I think.
So you can have a game bot, I think somebody talked about one a couple of years ago and I wanted to punch him as it wasn’t very interesting. Basically, you do pixel reading and there’s really no reverse-engineering required. You just see that your hit points are red when they’re full, and they’re not red when you’re dying. It’s very limited scope, but most likely you’re not gonna get detected, and detection is something that is not your friend.
Mike Donnelly: Actually, real quick, just by show of hands – does anybody know why detection is so bad? I mean, you all understand this, right? I don’t wanna glass over client-side detection. Everybody appears very wise in regards to detection.
I’ll go over it just real quick. Obviously game manufacturers don’t like everything we’re talking about, hence the lawsuits. So what they do is they try to detect your software, and again, if they do then they ban you. If you’re just doing this for fun, just, you know, hacking around, tinkering, and you lose your game account – it’s not a big deal. If you have 100,000 customers, that is a big deal because when all your customers are banned, then you’re f..ked. So avoiding detection is really important. We are gonna get into that a lot more later, but client-side detection of your software is very important.
 Josh Phillips: Also, I’ll say does anybody ever wonder why it takes, like, 3 months for the ban to happen? That’s because when you ban, like, 50,000 accounts every week, then those people who are re-buying those 50,000 accounts never actually re-buy them again because it gets expensive. But if you do it every 3 months or every 4 months, they will actually go buy the accounts back, so it’s actually, you know, profitable for the game company to say “Oh, hey, we’ve detected these guys ever since they turned on the lighter, but we’re not gonna detect them yet because we know that if we ban them too soon, they won’t give us 50 more dollars”.
Josh Phillips: Also, I’ll say does anybody ever wonder why it takes, like, 3 months for the ban to happen? That’s because when you ban, like, 50,000 accounts every week, then those people who are re-buying those 50,000 accounts never actually re-buy them again because it gets expensive. But if you do it every 3 months or every 4 months, they will actually go buy the accounts back, so it’s actually, you know, profitable for the game company to say “Oh, hey, we’ve detected these guys ever since they turned on the lighter, but we’re not gonna detect them yet because we know that if we ban them too soon, they won’t give us 50 more dollars”.
So we got some code injection where basically you inject some assembly code to do some small thing like maybe some crappy RPC2 thing. Your attack surface is a little bit higher, I mean you couldn’t really easily detect that. And then you have something like dll injection where you’ve got some pretty big bulk of code written in a high-level language like C or C++, and it’s really easy to detect that. And so you get into this game where you write this dll loader that fixes all your imports and stuff like that, and it gets really complex and you’re still pretty easy to detect.
Or you can go into the network or packet level and do some really good work like reverse-engineering the network protocol, which is very time-consuming. I think there are very few games (or maybe there’s a lot of games) that have complete analysis on this, but it’s still not easy to do.
Or you can go write your custom client if you think that you’re really good. Not many people think that they’re that good. It takes a lot of time, but if you write a custom client and if you’re at that level, then you’re probably gonna make a lot of money, like the guys that destroyed me I think were probably making at least a couple of hundred grand a month.
Mike Donnelly: Right. And writing a custom client isn’t something you’re gonna sell. This is, you know, goldfarming, real money transactions. So you’re writing a custom client so that you can have your partner run 10 million instances of game on a server farm. If you don’t have a custom client, that’s way too much 3D rendering, but if you can just take the game out of the equation – just don’t render anything. So it’s all a matter of scale for goldfarming at this point.
Josh Phillips: You go from, like, 2 or 3 clients per computer to 200 or 300, so it’s pretty big scaling.
Here is where we get into some anti-cheat stuff. This stuff gets difficult sometimes. I can’t emphasize enough that it’s very important to not be detected ‘cause then you lose.
Mike Donnelly: Alright, what I wanna talk about on this is not so much the technical aspects of detection but how you approach it strategically. This isn’t in the book on MMO hacking – I think there’s a book.
Josh Phillips: Yeah, one of my friends wrote it.
Mike Donnelly: I think it was written by the guy who was eliminated by Warden3 first. So this isn’t in the book, but strategically what you’re looking at is you have 2 main things to worry about. You have the attack surface, which is how hard your software is to detect, and that’s gonna work in a couple of ways because it’s gonna make detection code bigger. Secondarily, you have what I’m just calling intelligence, which is how much of what they’re doing that you know, how good is your understanding of their detection code – because it’s very important. If you don’t know what they’re doing, if you don’t know how any of it works, then how are you gonna keep from being detected? And they work together, such that if your attack surface is very big, it’s gonna be really hard to tell what they’re doing because the effort they have to take is so minimal. If they can write one line of code to detect your bot, you’re never gonna find it when they do.
The only other thing with attack surface is that of course that’s a constraint on your features, so when you think of something really cool (like “I’m gonna have my bot react within 2 milliseconds every time a monster does something”), you might be setting yourself off some detection. So that’s a decision you have to make when you’re choosing your features and handling with your customers. You should ask yourself whether you want to risk increasing your attack surface by adding this. So before the next slide, I want to talk about something that happened with me and another software developer with ‘World of Warcraft’. We’ll call the software ‘Interspace’ ‘cause that’s what it was – it worked by injecting a dll into the game, which is pretty big. But the guy that wrote it is a very competent reverse-engineer, so he had taken all of Blizzard’s detection code, he had it wired up and as soon as they sent it down he’d laid down a million breakpoints – it was pretty neat stuff. But he still had the dll memory which he tried to obfuscate, and more importantly, he had to patch one of Blizzard’s functions. So, you know, he’d go to the beginning of the function and just stick a ‘far jump’ in there. He’d think “Well, I got Warden covered, so they’re not gonna find it”.
Josh Phillips: Are you ready for the code yet?
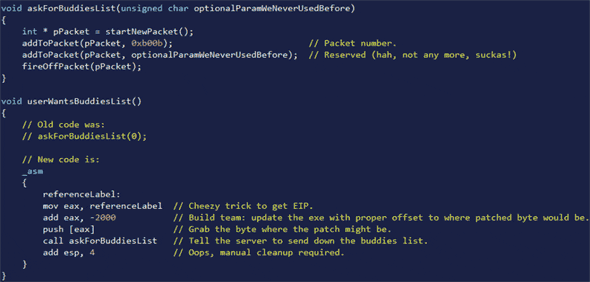
Mike Donnelly: Okay, I’m ready for the code. Alright, so this is an example of a piece of code that would be inside the game.
This is not actually from the ‘World of Warcraft’. So we’re looking at a piece of code here that the game uses to request, say, your buddies list. As you can see, it has an optional parameter we never used before, and it takes a packet number (command number) b00b, sticks that optional parameter in there and sends it up to the server – pretty simple stuff. So the way that code used to get called – you can see where it says ‘Old code’ askForBiddiesList, just passing (0) for the optional parameter we never used before.
So what Blizzard said was “You know what, we’re gonna get this guy, we’re gonna find his patch function”. And they changed that call to the little sample code there – well, this is again slightly paraphrased. They load up a register and they do some math on it so that IDA won’t see another reference to that function. Then they reach into the function that’s being patched, pull the first byte of their own code and send that as the optional parameter we never used before. So what this is doing is just sending up one byte of their own code every time they make their request. And of course on the server side, they comb come through it, find the ‘E9’ – gone. What’s interesting is in the software here you don’t see anything like “If this guy is a bot, then tell the server”. You just see how they grab this byte and send it up, and it’s a tiny piece of code, it doesn’t even change the underlying network code. There’s no new parameters, no new nothing else. The only way you would find it is if you are somehow watching that data going out and see it used to always be ‘0’ and now it’s ‘E9’ – that can’t be good, that’s a far jump.
So when they did this, he lost all those customers. You know, they waited a few weeks and banned ‘em all. I don’t know how he did business, hopefully he did okay. But they just hammered him again and again with this, and I found this way after the fact and as far as I can tell, he never found it. But it’s a good explanation of how much the attack surface matters. I mean, patching one function turned into this. Alright, that’s it for the code.
The point is that if you think you know where all the detection code is, there’s always a chance it’s not where you think it is. In the case with Blizzard, they had never put detection code outside of Warden – they’d kept everything in this nice bucket, hide from me and Warden. So it’s incredibly important to stay hard to detect, ‘cause if they had to make a new kernel call or something to detect him, maybe he was running a private API monitor (not that I ever did that) and he would see a new kernel call. But because they can just get him with one move – poof…So it’s really important to stay small and it’s really important to keep an eye on what they’re doing: you know, building tools to monitor their systems, building tools to monitor what the data stream is supposed to look like, and then if it smells funny, maybe you have a problem. With ‘Glider’, we actually had tools that would page us, so if Warden was updated and that didn’t look good, they would actually page me. Well, I can always just turn off ‘Glider’, I’m too drunk to fix it – so there’s always a way out, but it does come down to “You can’t be lazy”. Again, I’m talking from the profit angle, not the fun angle. It’s a lot of work but it pays off.
At one point, Blizzard got data Warden and they added a new scan. And the way the scan worked is it would take an encrypted string inside the Warden, get a key from the server, it would decrypt this string, and they would call ‘GetProg’ address (kernel 32). They would take whatever that string was, and if it resolved to a function, they would just call it with no parameters. So I was looking at this code and, you know, the game was down for a patch, so I don’t have the key to see what it’s gonna decrypt to. And I’m like “What are they gonna do? Are they just gonna call something at kernel 32 with no parameters? What’s the point?” Of course, if the ‘GetProg’ fails, it just does nothing. So I sat there looking at this for hours, and I was talking to the ‘Hellgate: London’ smart guy, and we couldn’t figure it out. So we just decided to bring it up. So we’d bring it up, stick some breakpoints in and they’d send the key down right away. Oh, there’s the key, let’s see what the string is! So you see, it decrypts it, and it’s a URL, it’s a YouTube URL. So I pasted it in the browser, and it’s a f..king rickroll. They rickrolled me, and I don’t know how many people they got (not many). Anyway, that was epic, you know, and it was really well done. That’s all I got to say, that’s the most epic rickroll ever.
Josh Phillips: So there are some client-side things that can be pretty powerful. They can use packers for obfuscation. The biggest thing that you have to worry about if you’re really professional in this is server-side data mining. Some analyst at Blizzard gave us a really big bone and was like “Hey man, this is how I detect people. I just write some sequel queries and I walk in the next morning and I ban people”. And we’re like “Well, thanks for telling us that. Now we can modify your stuff”. But I don’t think he realized that, I think he was just trying to be cool.
So you have things that are both client and server side, and basically what these things are is like command and control things that botnets use. You send your game client – in this case, 10 million ‘World of Warcraft’ customers – this bulk of code that they’re gonna execute on their machines.
Mike Donnelly: This is like a botnet malware to detect a bot.
Josh Phillips: Yeah, it’s pretty funny.
 So, ‘PunkBuster’ – I’ll go through this story. ‘PunkBuster’ basically looked for strings to ban people. I mean, they could be strings or they could just be some binary data. A lot of the times, they would be strings like a window name. And this group discovered that, and they were like “Hey, I don’t like this. And so what I’m gonna to is I’m gonna go into their IRC channel and I’m gonna send some strings to all of their members, and then I’m gonna go back in game and watch them all get banned for cheating”. Of course ‘PunkBuster’ was like “No, that’s not how it works”. But it really worked that way.
So, ‘PunkBuster’ – I’ll go through this story. ‘PunkBuster’ basically looked for strings to ban people. I mean, they could be strings or they could just be some binary data. A lot of the times, they would be strings like a window name. And this group discovered that, and they were like “Hey, I don’t like this. And so what I’m gonna to is I’m gonna go into their IRC channel and I’m gonna send some strings to all of their members, and then I’m gonna go back in game and watch them all get banned for cheating”. Of course ‘PunkBuster’ was like “No, that’s not how it works”. But it really worked that way.
This is where you get into money. If you’re not an expert by now – I hope you guys are all experts.
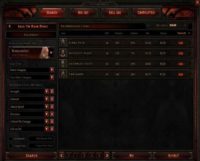 Mike Donnelly: There’s one thing that came under development before. In ‘Diablo 3 Auction House’, Blizzard started endorsing you selling items for money. So you can wire up a third-party payment system to your Blizzard battlenet account and you can sell that sort of epic ass pounding that you made for real money, or you can buy gold, you can sell gold. You’re not gonna have to compete with me ‘cause I’m done with Blizzard, but this is very interesting.
Mike Donnelly: There’s one thing that came under development before. In ‘Diablo 3 Auction House’, Blizzard started endorsing you selling items for money. So you can wire up a third-party payment system to your Blizzard battlenet account and you can sell that sort of epic ass pounding that you made for real money, or you can buy gold, you can sell gold. You’re not gonna have to compete with me ‘cause I’m done with Blizzard, but this is very interesting.
Josh Phillips: Yes, very interesting.
So we’d like to thank all of our friends in Poland, Germany, New Zealand and Australia. They couldn’t be here, it’s really expensive for them to fly over.