

He is the founder of SocialMediaSecurity.com which is an open source community dedicated to exposing the insecurities of social media. Tom shares his research and opinions on his blog, Spylogic.net. He is one of the founders and co-hosts of the popular Social Media Security Podcast.
He also has written the popular “Facebook Privacy & Security Guide”, which is used for student security awareness training at several large universities and government organizations.
Tom heads up the OWASP Mobile Threat Model development as part of the OWASP Mobile Security Project.
Tom is a frequent speaker at security user groups and worldwide conferences including Black Hat, DEFCON, DerbyCon, InfoSec World, Notacon, SANS, OWASP AppSec and ShmooCon.
– Tom, your recent Black Hat talk was about security issues with accounting systems and Microsoft Dynamics in particular. You mentioned that in 2010 about 41k of companies used MS Dynamics GP. Do you have any current numbers to understand the scope of the problem?
– Microsoft doesn’t release much information about how many customers use MS Dynamics GP, however, based on data from the recent “Convergence 2013” conference this year (www.calszone.com/2013/04/how-many-companies-use-microsoft-dynamics-erp/) they put MS Dynamics GP as having 43,000 customers. This is an increase from 2010. We also found that at a recent MS there are many major companies using the Dynamics product (www.erpsoftwareblog.com/2013/03/famous-brands-using-microsoft-dynamics-name-dropping-at-convergence-2013/). I find this interesting as many of these companies could be targets since it’s most likely they are using GP as well.
– Your white paper states one can get into MS Dynamics GP through SQL server or through client system. In one paragraph, would you please explain the ways to perform an attack on MS Dynamics GP?
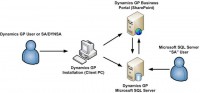
– Are there ways to immediately detect intruders?
– From a MS Dynamics GP perspective the only way we’ve found that an attacker could be detected would be through the logs on the SQL server or the GP application logs. However, if the attacker has hijacked a legitimate account all logs would appear to be from this user. If data is changed directly in the database then typical database forensics techniques would have to be used. By the time an investigation is launched the attacker will most likely have committed the fraud making these attacks harder to detect. MS Dynamics GP doesn’t have any alerting or monitoring capabilities that we’re aware of to prevent or detect the fraud attacks we describe in our whitepaper. The only good way to detect these types of fraud attacks are through the accounting controls a company should have in place such as reconciling bank accounts.
– That part of you talk where you are explaining how fraud can be committed is really sensitive and may help criminals. Why do you think it wasn’t enough just to show how to get in and let interested parties think of possible post-intrusion scenarios?
– We needed to go to this level of detail to show the specific attacks so that accounting as well as IT personnel are aware of the different types of fraud that could occur. This detail will help from an awareness perspective as well as to help determine what controls could be implemented to prevent these fraud attacks. Much like in penetration testing it is much more valuable to fully exploit a system to show real damage and data compromise.
– Often infosec researches face issues with corporations when they share anything about software security, did you have any issues with Microsoft? Have you contacted Microsoft and shared your findings?
– We’ve had no issues with Microsoft. We didn’t notify Microsoft because we didn’t find a vulnerability in the application or other type of exploit that can be patched. Our malware PoC doesn’t exploit the application; rather, it hijacks the database connections to the MS-SQL server.
– Do you have info about real life attacks/breaches on companies which use MS Dynamics GP?
– No, none that we’re aware of.
– What do you know about current version of MS Dynamics GP – are problems that you found addressed in it? Have they started encrypting at least banking info? Do you know of any exploits for MS Dynamics GP?
– You suggestions of preventing fraud require much additional resources, like logging any changes, periodic confirmation of vendor banking information, limiting number of people who can perform specific actions like entering new customers, and performing not only systematic account reconciliations but customers’ review etc, and really it is too hard for small businesses. Is there a way to automate prevention techniques? Do you have any advice on mechanisms built in the accounting system?
– We’ve suggested that accounting systems should have more automated fraud prevention controls built into the products, at least from an alerting perspective. However, fraud prevention for small/medium size business traditionally relies on standard accounting controls.
– What about other accounting systems like SAP, Oracle, what do you know about similar or different security problems in them?
– Based on research we’ve conducted as well as in discussions with SAP/Oracle professionals these types of fraud attacks could be replicated on more complex systems like these. All that is needed is a deep and intricate knowledge of where these accounting systems store financial data and the workflow to manipulate it.
– You say that accounting systems are frequently overlooked by penetration testers. Why?
– Accounting systems are overlooked by penetration testers because the tester doesn’t know where they are located on a network or they don’t understand where sensitive financial information is stored in a database. Penetration testers typically attempt to gain access to personal information (SSN, date of birth), credit card numbers and proprietary data to the company.
– Have you ever found any evidences of real accounting frauds during your pen tests?
– Not during penetration tests but we’ve worked with organizations that have been breached through financial fraud.
– From your pen testing experience, what type of organizations are less protected now, big ones or small? In what industries? Can you draw a hypothetical portrait of a less protected organization?
– All organizations big and small and across all industries have security problems and breaches. From my experience if a company becomes a target they will eventually get hacked. Attackers have the luxury of unlimited time and in some cases unlimited resources. An example of an organization that would be less protected would be a company who chooses to ignore the fact that they could be a target. Defense in depth, basic security controls, and how a company responds to an incident are more important than ever.
– From your experience as a government contractor – how often do security problems with accounting systems occur among government organizations?
– When it comes to security within the Federal Government it is a general rule of thumb to assume they are 3-5 years behind the commercial sector. So if this is a problem in the commercial sector, it is a problem within the Federal Government. There are a variety of reasons the government is behind commercial from a sheer monetary/investment standpoint, bureaucracy and change management as well as slow adoption. The other issue is what are the ramifications for the Federal Government if they suffer a breach? Typically no one gets fired, there are no fines… there is really no incentive for increasing security. In fact in most cases if a Federal Entity has been breached, they typically get an influx of budget/money.
– As we know most often people are the weakest part. Doing pen testing, how rare or often do you see that people do not click on stuff, use good passwords, encryption and keep their social life private and mouth shut? Have you come across organizations where all employees were perfectly trained not to fall pen testers’ tricks?
– No, I haven’t encountered an organization where users were perfectly trained from a security awareness perspective. I have however seen improvements with a solid security awareness program in place. Typically, good penetration testers have the same “tricks” that the real attackers do. To develop these tricks it requires creativity and the ability to think like a real hacker.
– Aside from human factor, from your experience, please list top 3 high-risk technologies companies overlook or implement incorrectly?
– My top three include mobile devices and applications, web applications to include the associated network infrastructure and social media risks.
– Seems like pen testing is a quickly growing niche. Many former white-black-grey hats are launching their companies and start providing pen test services, what do you think of such tendency? From your experience how often PTES compliance is met?
– There is a lot of demand for pentesting services, hence the reason some pentesters decide to start their own businesses. I don’t have statistics on how many pentest firms follow a methodology like PTES, however, SecureState follows PTES as well as other industry accepted methodologies depending on the assessment being conducted.
– If a company has a small budget and is mostly under the security poverty line, in your opinion, what is the single most important step they should take not to get breached?
– There isn’t one thing that a company can do to be secure. It requires a lot of little things to meet a certain comfort level of security posture. Even if you do everything right you can still get hacked. I would have to say basic security awareness with a focus on passwords and phishing, change defaults, limit exposed services and/or baseline all systems is a good start. Unfortunately, nothing is 100% secure.
– Have you tried Social-Engineer Toolkit? What can you say about it or any other such kits?
– Yes, we’ve used it. Open source tools like SET are very valuable from a penetration testing perspective.
– We found that SecureState does some subcontracting for government. Is it hard to get such contracts and what interesting work do you for NASA, Department of the Army or other government entities?
– It is not easy to get subcontracting work for the government. This is due to the procurement process within the government, the sales cycles are extremely long and strenuous. The type of work that SecureState performs for federal entities is very similar to the work we perform for commercial organizations. Our work is specifically focused on helping organizations work from their Current State to their Desired State of security through the implementation of tactical and strategic processes that increase their security while decreasing the amount of risk they accept. This is done through a variety of services from penetration testing and vulnerability management to compliance program development and incident response.



























