
Jayson E. Street, Information Systems security expert and CIO at Stratagem 1 Solutions, describes his real-world intrusion engagements during his Defcon talk to show the flaws of the current security model within enterprises.

Hi! This is my talk. I want you to understand I had to start with this slide (see image) because I’m gonna say things that might sound a little bad, mean, spiteful, hateful – you know, all those other adjectives. I’m adorable; I’m a wonderful fluffy person and stuff, who does not like doing bad things unless people pay me. I would never try to kill you unless you pay me to try it – I promise. So when I tell those really harmful terrible things I’m gonna be talking about, let’s just remember the kittens, okay?

The title of my talk is “Steal Everything, Kill Everyone, Cause Total Financial Ruin!”, or how I walked in & misbehaved. Quite simply, it’s because of the security fails. It’s like I’m gonna explain to you that physical security and stuff, you know, is one of our biggest weaknesses, because people can understand 2-dimensional versus 3-dimensional when they are walking up to the front door.
Let’s start off with who I am. I’ve got a day job and a night job. My day job is I’m the AVP of Information Security at financial institution. My boss is going to love this on Monday. What I do is I work in a cubicle with a lot of cool action figures around it. I monitor Firewalls, I watch IDS systems, I build our infrastructure, I find more creative ways to secure it and to go after people who are coming after us. And I do all the day-to-day blue team stuff. My main job is blue team, the defense.
My night job is the CIO of Stratagem 1 Solutions where I do pen testing maybe like 3 times a year, and basically I do speaking engagements like this around the world. I’ve written a book “Dissecting the Hack: The F0rb1dd3n Network” and I also do some other writing. That’s what I do at night. So I respond to incidents during the day, I create incidents for other people at night – so, best of both worlds.

I love these pictures because you see the first picture with the baseball cap – that was me standing outside for an hour in front of the industrial park building, secured facility, on a Sunday, with no traffic, and the security walked by twice and did not think to stop me and ask me “What the f… are you doing on the sidewalk just watching our building?” And he didn’t put it in his report either – so, bad on him. The second picture, you know, looking dapper in the glasses, is actually me going to apply for a job. Yes, I’m wearing a black hat colored shirt because I like to come with warning labels. I did not get the job – unfortunately I was way underqualified for that one. I did get their data, so win-win.

These are my 2 favorite pictures of engagements I’ve been on. The one where I’m wearing the “I’m a liability” shirt, I think, is the best one because I stole a car in that shirt. I was at a hotel off the coast, and the valet gave me the car, and I had to explain to him: “I can’t get in this car right now”, and he’s like “Why?” I said: “Well, because I’m stealing it, it’s like they paid me to do an assessment, I’m a liability” It took him a while to figure that out, so I finally had to say: “You might wanna take this back, I think the owner is gonna want it.” The next one is my favorite, it’s one of the most secured facilities I’ve ever seen in my life, right across the street from Ground Zero, SWAT teams, you know, with cannon units, with their machine guns walking through the concourse, 8 security guards in the main elevator lobby, not including the business lobby. That’s me in the upper floors, wearing an actual valid badge and a shirt that says “Your Company’s computer guy”. I like that picture a lot. I’ll get more into that story in a little bit.
I deal with CISSP, I think the Code of Ethics says that I have to put a Sun Tzu quote in my talks, there it is:
“… deception. Hence …” (Sun Tzu)

We’re done with the intro, half way through, so far so good. We’re gonna talk about the one fact that we have to face when we’re dealing with this subject. We’re gonna talk about the 2 rules that I go by when I’m doing an engagement, and the 3 outcomes from those 2 rules. And hopefully I’ll get to conclusions and discussions.
Why this talk? I gave a talk last year about the beginning of social engineering. I was talking about things that you could do to try to get into the buildings. That was the part 1, and quite frankly, I got some feedback afterwards, like: “Man, Jayson, that’s some basic concept stuff, you know. It’s like you weren’t showing any kind of NLP or anything.” Because I can’t. I am not a professional social engineering expert. I don’t know about NLP, I don’t know the psychology, facial recognition, mind ninja techniques. I still get in. I have 100% success rate of getting into facilities when I’m doing a social engineering engagement. So it’s not that I’m that great, trust me – anybody will tell you that. It’s because our security is that weak. So this is an educational, and hopefully in a funny way, kind of talk just to give you an onset of where to go look for more stuff, and then hopefully have a good chuckle while you’re doing it. You are not going to learn anything new, but hopefully you’ll remember something that will make you go look at something else.

Now I’m not talking about social engineering part so much, as this is all the damage I’m going to do after your security guy lets me through the front door. Because number 1 fact is I’m getting in. I took this picture, I kid you not, when I was going to meet the guy for the first part of our meeting, and as soon as I got into the concourse and I saw the employee door for the security area (I was like “Oh, you’ve got to be joking me”), I walked right over, pushed 135 – guess what, I got in! I would have tried 531 or 315. You should have seen the guy’s face when I showed up 10 minutes before our meeting and no one knew I was there. So, that was fun.

Here’s the other one. I went to apply for another “job”, and when I’m on these engagements I like to be bad, so when I signed in to the receptionist, I stole the pen. I’m a bad guy, that’s what we do. So as soon as I finished getting the pen and signing in, I asked the girl where the bathroom was. It’s not because I drink so much frickin diet Pepsi, it’s just because I get lost very easily, and I will wander buildings looking for that darn bathroom for hours. You can’t believe the things I can get into. Well, I’m going through and actually happen to stumble into the secured area, or part of the employee area. I was looking for the bathroom and I found the employee entrance… This is a facility actually equipped with a million-dollar security system. And I looked at the door and saw this little rod thing they were latching the door with. And then I remembered – oh, wait, I got a pen! So I took the pen that I stole, put the cap on the rod, the door shut perfectly, and it didn’t latch! So I leave, then come back in about 20 minutes or so – it’s still there, I’m now in a secured facility, and no one knows.
I’m not a master locksmith; I tell people I don’t have to be a master locksmith if your people will let me through the front door. I don’t have to be a massive ninja coder, which I’m not, if I could just steal your hard drive with all your data.

Here’s another key: I love forging emails and putting them on iPad (see image). The key is to put them on an iPad. If you forge an email and print it out, they’re gonna think it’s fake: “Oh, you just typed this up”. You put it on an iPad – the blue hyperlinks stay hyperlinked, and also it’s like: it’s on an iPad, it’s magical, you must be telling the truth. So I was up in that secured facility in New York, the network guy noticed an unusual amount of traffic coming from the computer of the CFO’s assistant going to their main server, and he was worried about what was going on. It was me. And so he comes over and asks: “What’s going on? What are you doing?” And I start telling him exactly why I’m there. I spent 2 hours on Google creating this email, making it sound like the new owner of this company was upset, and sent an email to the other company that he owns to send one of his guys out (me) to go look at the network. And I made it sound very political, and that was supposed to be a surprise so that no one knew I was supposed to be there.
So I showed this to the networking guy. Well, he sent me to his office, we went to his office and we talked to the CIO for about 10 minutes, and the employee then started to escort me around to all the other computer desks and stuff, you know, so I could plug in my malware… And I had an employee escort, so I had to be okay. So I actually could finish the rest of the engagement, having someone help me and make sure that people knew I was okay to be there, plugging in my USB devices and doing whatever else. I really loved that email.

I’ve got 2 rules, but guess what – looking for PCI is not one of them. I don’t really care, I just wanna eff you up, I just wanna mess you up in the worst possible way, I wanna be the worst thing to ever happen to you at the worst possible time (remember the kittens). So this is why I got my 2 rules, I got them from “Serenity” which was based off the series “Firefly”. And these 2 quotes are very simple: “I aim to misbehave” and “Let’s go be bad guys”. That’s it, I’m just trying to do bad. To team it up, it’s like “red team” – don’t act surprised when we try to kick you below the belt. It’s like bank managers are still being kidnapped today, taken to their home, their family held hostage overnight until they go open up the bank for bank robbers. That’s not funny, that’s real. This stuff still happens.

Another thing is – what we’re doing is not a new concept. This is from 1992, the movie “Sneakers”:
– So, people hire you to break into their places…to make sure no one can break into their places?
– It’s a living.
– Not a very good one.

But this is indeed an old one. Better people than me talk about it a little bit more technically – like I said, I’m the comedy relief on this, but let’s keep going.
Another thing that we have to understand is management is not proactive, it’s reactive. Dan Erwin said in 2008: “The best way to get management excited about a disaster plan is to burn down the building across the street”. Hello everyone, let me introduce myself – I’m the fire… So what we’re gonna get to now is the fun part, and the fun part is talking about all the different ways that we can start those fires.

I love this one. This is what I call the trifecta bad, because, yes, I stole the phone or cloned it; yes, I’ve got the laptop – 30 laptops unsecured in this facility that had no laptop lock cables because they were “secure”. By the time I did the exit review I stated seeing laptop lock cables, which was good for them. They also had me an employee badge, I appreciated that.

Okay, I do feel bad about this one (see photo to the left) because I’m a CISSP, I have a Code of Ethics, so please don’t report me, let’s make this off the record, I’m sure no one’s watching. It’s not about the laptop because I had no problem stealing the laptop – I mean, the guy left the cable on it, he was just giving it to me. And I’m not talking about the screwdriver because I needed to steal something, you know, that was bolted down – I like to be thorough. I was a little hungry and I still wanted the cookies, I’m sorry. Okay, let’s go on.

I love this because people expect security not to be that thorough, so they get their laptop lock cable that’s supposed to be fastened to the desk, but that’s hard – you have to bend down. So let’s just loop that cable over the desk, and no one is going to pull it. And you know what – most security doesn’t pull the cable to see that’s actually secured. But I’m not security, I’m a thief. I’m gonna pull the cable, I’m gonna try to steal it.
Also, kudos for one guy who had it firmly attached to the desk, he also had it locked to his laptop. But I’m telling you, when it’s the code 0000 I’m gonna try that one. I’m gonna try 1111, I’m gonna try 9999. If you’re a geek, I’m gonna try 0007. So, sorry about that one. Also, they like to move the last number, or the top number, by 1 in either direction, and that’s it. So that would just go “tick” – unlocked.

Also, when I’m on engagements I’m going through all your drawers. I’m gonna go through all your desks and your cabinets. I’m gonna be looking for stuff because nice, honest coworkers are not gonna go look into your desk. I’m not a nice, honest coworker. This guy had his laptop locked totally correct, everything was right, and then he put the keys in his top drawer. So not only can I steal his laptop, but now I also have a nice really shiny laptop cable I can use to protect from someone stealing it. Because I hate when they steal my stuff that I stole…

This is another trifecta. I stole the purse, I stole the car keys, and yes, I stole the phone. Let the record state: I did not steal the lunch – I felt really proud about that. I took the car keys, took the driver’s license out of her purse. I then go down to the parking lot; I find out what car it is; I unlock the car; I go back and put her car keys back. She comes back after work, I’m in the back seat with a gun, telling her that I’ve got her driver’s license and I know where she lives; that I’ve got people there that will kill her family unless she goes back to that facility, steals all their data that I need, and then comes right back out; and that we’re tracing her, we’ve got her phone cloned, and we can monitor it. Employees need to know that their personal belongings are theirs, but the impact can be severe for them as well as the company. That’s why they need to secure their stuff. Now, let’s remember the kittens real quick…

Would you have these mini frowny faces on the slide – you’re just effed, it’s just game over. You literally gave me a blank check to steal your credit and your identity – and trust me, my credit sucks, so I’m taking it. Thanks for leaving the Social Security card, because it’s got your signature on it, so I know exactly how to forge it. It’s like – that was very helpful, not many people are that kind.

Oh, when I stole the first car the guy sort of cheated and let some people know that I was going around and doing stuff like that. So I said: “Well, screw you!” At 2 a.m. I walked in, grabbed 3 Mercedes-Benz and a Beamer, and just took them with me. Less than 60 seconds, so Nicolas Cage – beat that! The look on the security manager’s face when I walked to him and I dropped him those 4 keys was priceless. I wish I could have included the picture but it’s on my desktop at home, so…

So, some countermeasures. Employees need to know that this stuff matters to them as well. Make sure they’re locking their desks, securing their property. They secure their property at home, they secure their property in their car – they need to secure their property at work. Also, no tailgating; you got to be sure that they understand that they shouldn’t tailgate. ‘Cause you know what I’m doing? I’m coming in a wheelchair and I’ve got, like, 4 books; and they’re like: “Oh man, chasing your douchebag?” And I’m like: “I’m a bad guy, I’m trying to steal from you! Do you really think I care that you’re gonna feel lesser about me because I’m not supposed to be in a wheelchair? No! I’m evil!” And trust me, when I go up to that door and I got these books, are you really gonna be the asshole who’s not gonna let me in the door? I mean, seriously. No, you’re gonna let me in, and I’ll thank you for that. Your employer is not going to, but I will.
Also, if you see something – say something. You don’t have to personally tackle the guy if you think he is suspicious. You do have to call security. You need to start empowering the employees to understand that they are part of your security team and they need to start acting like it.

Well, here’s the real warm and fuzzy side. We’re actually talking about how, you know, to kill everyone, because that always brings up a crowd on a Sunday night. This picture was taken at 2.30 in the morning, I’m in a hotel somewhere, different hotel than the car I mentioned earlier. And I’m inside a mechanical room, I’m wearing Pepsi pajama bottoms over some cargo pants with some really bad things, and a white T-shirt. And I’m barefoot because I took all my clothes off in the bathroom in the guest area of the hotel, and changed into that.

Then I started walking around to see what I could do. I could do a lot because – do you notice one important fact in this picture? There are no padlocks on any of the switches. If that switch is on, I’m turning it off. If that switch is off, I’m turning it on. And if, by golly, there’s a red button – I’m pushing it, twice! That’s just how I roll. Now, I want you to understand I’m not a total jerk. Yes, I’m going to start a fire in this room; and yes, it’s going to have some poisonous chemicals in it, so the smoke will go through the ventilation system that is right there.

But I’m not totally terrible because it’s 2.30 in the morning. Who wants to get woken up at 2.30 in the morning, listening to this alarm sound going off? So I’ll turn off the alarm system for you because I don’t want to be rude. The only thing worse than having that alarm going off in your ears and stuff is someone throwing cold water on your face when you’re trying to sleep. So I’ll turn the sprinkler system off for you too, okay. I don’t want to get everyone all wet and drenched and stuff – there’s a fire going on, that would be dangerous.

Another place that I think is great to kill people is the kitchen. This guy didn’t even ask who I was, but, you know, most people don’t. So, just to bring that home, here’s a nice little video. Is there any law enforcement from Malaysia in here? Okay. This is a video that I took in a Malaysian hotel. I was wearing my Defcon shirt and I’m in Malaysia, I don’t blend well. So, let’s see what happens (watch Jayson’s video below).
So I come up against this door here and I’m thinking: oh, this is awesome. The reason is because it’s secured, so it’s got stuff in there that you want protected, so you put a padlock on it. But then, you don’t padlock it…So, well, thank you for that! What could you be protecting? I don’t know, let’s see here. Oh… (says “WARNING! Hazardous chemicals”). I did not go in there with an Uzi or an AK-47, I did not bring C-4 with me – I just walked out of that closet with napalm, I just walked out with poison. So let’s see what I can do.
Well, first I got to find a place to do that; that’s gonna be a long search looking for the proper place to deploy this kind of stuff, let me turn around. Oh, I’m in the kitchen. That was quick. So, let’s walk through here. If I wanted I could destroy their food supply by poisoning the stuff that’s in the fridges. Here’s the mechanical area, this is where I start my mechanical fires using the napalm. You notice those 2 guys there? I have to use social engineering countermeasures, so I say: “Hey, how’s it going?” It was going okay, and I kept moving. Some more places where I could use napalm. One of the things I noticed was that they protect guest information very well in their computer systems. You know, you can’t go up to the front desk and ask where someone’s staying, but obviously you can walk into the kitchen because every person, their room number and their name is right there for room service. So, that’s pretty low-tech.
Now, I’m going through this and I’m thinking to myself: why just walk around the place? Let’s go try do some social engineering to see what happens if someone notices me. So I’m gonna go talk to the head chef and the manager of the hotel. I asked one of them if he was using Wi-Fi or cable. I got an iPad and I’ve got my hacker shirt on…He just says he’s using cable. And then I just left, that was it! That’s how easy it can be. In terms of social engineering, it’s just as easy as just saying: “How’s it going?” and stuff, and talking to someone. People don’t expect bad things to happen until they happen.

So, some of the countermeasures. One of the key ones is to make sure people understand that workplace violence happens. I mean, for gosh sakes, I got this information off of workplaceviolencenews.com. It happens so often that they put up a website for it, for gosh sakes – that’s depressing. So you got to understand that it happens. So, set up a code. I tell people, especially the receptionists, that the code “Oh my God, he’s got a gun – run, panic, or we’re all gonna die” – is not the best code. It is effective, it does raise the thing, but it may not be the best. I always tell them to suggest something like a code “perrywinkle”: “Mr. Perrywinkle to HR; Mr. Perrywinkle to HR”. And I’m hoping that someday someone institutes an actual code “perrywinkle” because I think that’s just funny saying “perrywinkle”.
Another one is conduct routine safety checks, not just safety checks of your equipment, but of your people as well. When I walked around for an hour I noticed one thing at that facility: there was just one door that I could easily jimmy, and it had a camera that was right over it but I couldn’t tell what the angle was. Because where the other 2 cameras were spaced, if I walked diagonally from the other parking area, they wouldn’t see me except for that one camera. And if that camera was angled at the wrong way, I could totally bypass it. So I talked to the former head of security there and told him about it. He’s like: “Whatever…Come with me.” He takes me into his office, the security office. It was empty. He showed me the computer screens – they were all turned off. He turns them on, and the one camera that was not working was that one…I did mention he was the former head of security at that facility.

Okay, so let’s talk about financial ruin, let’s talk about espionage. I hate to hurt some people’s feelings and say: “It’s not just the Chinese.” In the 70s, the 80s, the 90s French were doing awesome with it. Actually, the French did great counterespionage thing with the CIA and stuff back in the 90s with the Boeing incident, you can google that one (CIA wish you wouldn’t). So let’s talk about some of the things you can do there.

Once again, there’s many frowny faces, not good. But you know what – I’m an environmentalist, I am. Do you know how many poor senseless trees die every day due to those printouts that you leave beside the printer? But you know what – they will not die in vain when I visit. I’m taking all of them. I’m gonna liberate those trees. I am such an environmentalist, I will take the ones that are still printing out, just to make sure you don’t forget them. Those trees will not die in vain when I’m there. This is so sad, this is actually a Dilbert comic strip because they still use shred bins. You’re telling me all your confidential data, all the stuff that needs to be shredded – let’s put it in a big blue bucket. This is done in D.C., and this is done in financial institutions, this is done in DoD contractors’ offices. My favorite is the DoD contractor’s office, it’s a secured area, the actual office of the executives that is actually secured so that pretty much no one can go in because of all the top secret data. So what do they do? At night, they put the blue bucket outside their door. Yes, that’s awesome! I’m sorry, it’s awesome for the bad guys.

When I get to the point where I can just stick malware into your hard drive, it’s just gonna be a fun night for me, not for you. When you see that USB drive in your exchange server, it’s not gonna end well for you. I know where the USB drive has been – you don’t want it in your exchange server. You may think what kind of damage someone can do going after the exchange server (ask HBGary). Well, how about your accounting server? Me and the 25 other employees are not going to get any paychecks.

I can also do wire sniff on your traffic. Sniffing passwords is hard, you got to configure a lot of stuff. Like I said, I’m not that technical, I’m not that bright. Why don’t I just get them off your monitor? (see image to the left) I love this one, I actually tried “<leave blank>” first, I gave them the benefit of the doubt.

This one is my favorite of all time (image to the right). You know why? Because this was at a research lab; you know, I was supposed to be dealing with rocket scientists. The password – first of all, they shouldn’t have written it down at all. But the password that’s scratched out was actually an alphanumeric special character password. It was very complex, and it was hard. So they scratched it out and put it to “welcome”. And it was all lower case, I tried the capital first because, you know, they are rocket scientists…

The one thing worse than seeing me in Pepsi pajamas is actually seeing me in a suit, because if I’m in a suit, I am out to screw you over terribly. Because I’m wearing my vest of doom. You can learn more about the vest of doom and all these little toys in my talk that I did last year. But now I want you to know I’ve got a vest of doom 2.0. Let’s see some of those things. I’ve got some video recorder USB pens – now that I’m keeping one in my pocket, I’m going to actually be going in and leaving them in your little cup holders that you leave, so I can record you logging in with your passwords, carrying on your conversations, things like that. So, that’s awesome! If I’m the tech guy, I got my nice little handy 8 GB USB flashlight (video recorder). When I walk into your facility, I’m a walking talking Google street car – I’m capturing everything I can.
Now, I got another device in my 2.0 vest. This was something that was given to me by a 3-letter agency in D.C. The only reason why he gave me this device (which cost billions of dollars of research – he said) was that I was to never talk about it in public. So this device he gave me is actually a USB keystroke logger. It’s undetected by any antivirus, you can plug it in, it’s very streamlined. It is very hard to spot when you actually plug it into a device, and it records all the keystrokes. You’re right, I’m lying – I got it off of ThinkGeek. I’d like you to tell the QSAs and your executives about that. Let’s put this in a different way so that they understand it a little bit better – the risk matrix.
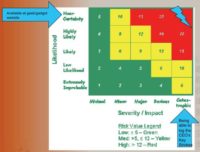
“Available at a geek and gadget website” – well, we discover it’s a “Near Certainty”. Being able to log the CEO’s keystrokes – yeah, I’m gonna go with “Catastrophic” on that one. Now, you see all these other devices, you see all these pens and stuff – to acquire those and be able to get access to that kind of technology, you’ve got to be a “select” group of people. I think everybody is familiar with that kind of access; I think everybody here has that access, it’s called “frequent flyers”. I mean, you talk about hackers getting this kind of data? Okay, I’m an accountant, I really hate my boss, I really hate my job, I wanna go somewhere, I wanna steal a whole bunch of stuff from the Company first. How could I do that? Oh, I’m on this flight; oh, look, SkyMall; oh, I can put keylogger and spyware on my boss’ computer; oh, I can have a USB recorder and stuff, so I can take video of my Company’ secrets; and yes, I can actually have a voice recorder so I can record our top secret confidential conference meetings.
People are so busy protecting their stuff from these very high-level attacks that they are forgetting SQLI (oops, sorry Sony). Sometimes it’s a low-hanging fruit, and it really is the low-hanging fruit they are going to go after. So you got to be protecting that as well, you got to be protecting from these kind of threats as well.

I love this one. This is the “Pwn Plug” from Pwnie Express. I took these pictures at a bank branch on the West Coast. I did 4 branches: 4 attempts, 4 successes. After the 4th one they told me to stop. The reason why is because I walked in, I was wearing a blue Defcon work shirt with warning labels, and I told them: “We have been having brownouts at the corporate office, and we need to check to make sure that the power fluctuations aren’t affecting your operations here. So what I’m gonna do is plug this device into your network so that I can take the readings and report back to the home office. And by the way, I need to go in and make sure all the computers have proper power surges and the UPS system is working.”
I used a false name that I had no ID, or identification, for. I used a fake company and a fake phone number. I signed in to their vendor log. If I would have come in there with a ski mask and a shotgun, every single person would have reacted exactly the right way – they have been trained to handle that. They did not expect the geek factor and they walked me through the teller area, the drive-through area, and through the backrooms where the actual money is, not the shiny little volt thing but the big safe with the actual money in it. What kind of damage could I have done? What I did do was I plugged in my Pwnie device. This one with the power unit on the right – I liked that one the best because I had to get the bank manager to get out of her seat so I could plug it in behind her desk. What I do right after that – it’s like…I don’t have to go to my car, I don’t have to phone home; I go to the bank lobby and I’ve got BackTrack 5 on a Xoom tablet, and I’ve got it already connected to the Pwnie Express. I’m pwning you before I even get out your door.

So, what are some of the countermeasures? There is only one major countermeasure, and that, frankly, is just going to be – stop printing! What happens to those papers in an office, for gosh sakes? Make sure you’re doing proper DLP (data loss prevention), make sure you’re talking about it. There’s a recent report about how some of these data leakages are mostly coming from inside, from the actual employees themselves. So make sure that not everything is being shared open.

So now, what can we do? Like I said, I’m the blue team. I like it when we win. I kid you not, I’m rooting so hard for the good guys when I go on an engagement. I look at some of those employees sometimes, thinking: “Do you believe what I just said? Seriously?” And when they let me in, I’m like: “Oh, dude! Obviously, I was a bad guy!” So what do we need to do though? We need to educate, empower and enforce our workforce, our employees. And the best way to educate them is to stop this one simple phrase: “stupid users”. Stupid users clicked on an email; stupid users went to a website they weren’t supposed to go. You know what? If I’m in the security department, stupid me for not educating my employees properly on how to handle those kind of threats.
And another thing is, if I hire an employee and they don’t even have a driver’s license; if on their first day of work I’m telling them: “Here’s the keys to my Bentley, go do some deliveries”, and they crash that car – who’s the idiot? The one that started driving, or the one that gave them the keys? If we’re giving them technology they don’t know how to use, they need to start being educated properly on how to use it. Then, when they screw up we can say it, but not until then. We need to educate our employees and let them understand what they are going to do. We also need to empower our employees. We need to let them know one simple fact: they are part of the security team. From the CEO to the mailroom, you are part of the security team. It is part of your job and your duties to make sure you’re protecting the Company data. They need to know that and they need to enjoy that. They need to understand: you as information security have access to the biggest intrusion detection systems known to man. All those employees on the frontline are saying: “Oh, that looked weird. That shouldn’t have happened. Let me call somebody.” That’s what you need to start doing. You need to start empowering them and letting them know that it’s required.
I’ve got a guy who sends me 15 frickin emails a week on a phishing scam or some kind of other thing he thought was weird, and he wanted to make sure I knew about it. You know what I say every single time? “Awesome! Thank you very much, I appreciate it!” Because that 16th one is not going to be a false positive, it’s going to be something we need to respond to. I’d rather get 1000 false positives from people that are actually thinking about it, because to me that means they’re thinking about security. We do walkthroughs in our facility during our day job, and we look under keyboards for passwords. And we actually started finding them, that was bad. But then we started not finding them, but we still do it. You know why? Because every time you do that, everybody in that area is going: “Oh, they’re checking for something, we got to make sure everything’s okay.”
Creating that security awareness without shoving it down the throat – that’s how you do it and you enforce it. Not with a baseball bat (oh gosh, that would be fun), but with positive enforcement. When someone stops me when I don’t have a visible badge, I report them to their supervisor, and I say: “Awesome job!” That person did what they were supposed to do, that person is protecting our data. We’ve put a list on our bulletin saying: “People who got kudos for security”. They did the right thing, they did it the right way. And you know what that breeds? Competition. ‘Cause that frickin Suzie in accounting – she’s always getting the credit for doing that stuff. Well, I can do it too! You know, I can stop someone if I don’t think they have a proper badge. That’s how you enforce it. It doesn’t have to be negative. You’ve got a workforce, you’ve got a human intrusion detection system out there just waiting to be used – start using them. So, as soon as you stop saying “stupid user” and start saying “my coworkers in the information security department”, we’re gonna start winning.
Thank you!




























