 What is the present-day governmental and nation states espionage like and how should security companies treat it? How do emails with contagious attachments transform into critical privacy problems? How do you tell that you’re being spied on? The well-known malware adventurer and cybersecurity analyst Mikko Hypponen addresses these non-trivial relevant issues of today in his “Online Espionage” speech at SecTor IT security conference.
What is the present-day governmental and nation states espionage like and how should security companies treat it? How do emails with contagious attachments transform into critical privacy problems? How do you tell that you’re being spied on? The well-known malware adventurer and cybersecurity analyst Mikko Hypponen addresses these non-trivial relevant issues of today in his “Online Espionage” speech at SecTor IT security conference.
Let’s start off with the German governmental trojan – the trojan which we detect as R2D2 because the actual network transmissions from the infected laptop sent back to the government are initiated with this pass phrase, which is C3PO-R2D2-POE, which are all references to the ‘Star Wars’ the movie.
Should antivirus and security companies like us try to detect governmental trojans? These are being used by different governments, police forces and investigators to catch bad people. I guess it isn’t a bad thing if you get hit by a governmental trojan and you are a potential school shooter or a drug lord. But it is a bad thing if you get infected by a governmental trojan and you are innocent. And we are not the ones to make that call. We have to make the decision based on something else. Malware decisions are made by technical methods. If it’s a trojan, we will detect it regardless of the source – as easy as that. And I don’t see any other way.
 If we would bow to, let’s say, the government of Germany, or government of Canada, or government of the United States of America, then where do we draw the line? Next stop we have is the Italians asking us not to detect something, then the Spanish, then the Israelis, the Syrians…Where do you draw the line? So we don’t, we don’t draw the line at all. If it’s a trojan, we detect it – as simple as that.
If we would bow to, let’s say, the government of Germany, or government of Canada, or government of the United States of America, then where do we draw the line? Next stop we have is the Italians asking us not to detect something, then the Spanish, then the Israelis, the Syrians…Where do you draw the line? So we don’t, we don’t draw the line at all. If it’s a trojan, we detect it – as simple as that.
We actually did a public statement on this over 10 years ago which still stands today. And this is how we do it, we have it written out on our website and we follow that rule. But this was the very first time we had to actually use it in the real world. This was the first governmental trojan we received, which we knew was a governmental trojan.
It’s highly likely that in our collection of malware we have maybe several other trojans, which we just didn’t know were governmental trojans. Regarding this particular sample, we wouldn’t have thought twice that it was a governmental trojan – it’s a backdoor1, it’s just a keylogger2, it’s a screen grabber3. The only way we would think that was only because recording Skype was a bit weird. It wasn’t just intercepting ‘mic’ and recording everything – it was intercepting only Skype traffic, nothing else. And that was because of some legal requirement inside Germany, that you weren’t allowed to record anything else but the voice through VoIP4 traffic. I mean, we wouldn’t have thought for a second that this would be a governmental trojan, unless we would have known it. So it’s likely we have other governmental trojans which we already detected, which we actually don’t know are being used by police.
And what about espionage, spying, this ‘James Bond’ stuff? Well, spying is collecting information, that’s what it is. 20 years ago, that meant breaking into buildings and stealing paper or taking copies or photographs of them, making microfilms. If you wanted to reach the information, you had to physically go where the information was, because it was on paper, right?
Today, obviously, it’s data, it’s some computers and some computer networks, which means, at least in theory, that everything is reachable from anywhere in the world. There’s been a massive revolution on how espionage is being done: both industrial espionage and especially country-to-country, nation states espionage. Countries are spying each other with online attacks all the time. We saw first attacks like this in 2005. We know now that it had been going along for maybe 2 years before that already. So these have been going on for maybe 8 years now, or something like that.
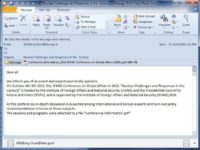
So let’s have a look at some of the emails we’ve seen in these attacks. And this email looks fairly normal: “To whom it may concern”, somebody sent a PDF file about competitor’s report 2011. That’s a real person, a real person’s name, a real email address, but it’s all spoofed and fake. It’s not actually coming from him, it’s not actually coming from the email address it seems to be coming from. And you all know how easy it is to spoof SMTP.
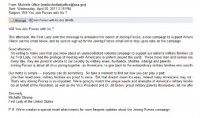
So, let’s have a closer look. You get an email like this. You believe the email to be real, why wouldn’t you? And you click on the attachment. So let’s open that file with Adobe Reader, and… bang, it’s gone away. And still, it continues loading, and eventually we get the file – everything looks great, except if you look closer you’ll see that the file name is now different from the one we were opening initially. And if we go and take a look closer at the system, suddenly you have a file called, for example, ‘A.exe’ at the root of drive C:. Windows XP does not have a file called ‘A.exe’ at the root of drive C: by default, it just appeared as a result of opening the attachment.
So what’s happened here? Well, the initial PDF file was infected. When you opened it, it crashed Adobe Reader, that’s why Adobe Reader came to screen and went away, that’s why it crashed. And it was crashed by an exploit targeting the vulnerability in Adobe Reader. In most of these cases, the vulnerabilities they are using are not zero-day. In most cases, it’s something you would actually block by just patching your systems: patching Word, patching Excel, patching PDF reader and so. And when it exploits PDF reader, it runs a piece of code which dumps 2 files from within the original file. So the file attached to the fake email has 2 files embedded inside of it: one of them is a new PDF file with a different name, and the other file is ‘A.exe’ which is a backdoor.
So it drops these on the hard drive and then it opens them both. The reason why this different PDF file is carried along at all is just for misdirection. The user clicks on the PDF file and expects to get a PDF file on his screen. The mistake they made here was that the file names didn’t match. If the file they dropped had been called just like the original one, everything would have looked fine. So they’ve been a bit sloppy here, but that happens.
And the ‘A.exe’ is a backdoor – in this case, it was ‘Poison Ivy’6, or some other typical backdoor that we see in various kinds of attacks, but also in these targeted attacks. It connects to an outside server and then gains access to the Firewalls, in many cases it connects to a server Port 80 or Port 443, opening them and can get to the Firewall, which it typically does. And whoever is sitting at the target address, now has full access to the computer which got infected, plus to all the network shares that this user can access in the local area network. And now we can all think for a moment what we can access in our organizations’ local area networks – quite a bit.

Another one was sent to EU parliament members, or people working at the EU parliament. It talks about EU topic, looks fairly real. It isn’t. Another one we got was called ‘Federal Tax Law Changes’, that’s a PDF file as well. Yet another spoofed PDF file – talking about World Bank things, looks pretty real to me. Some of the infected files are Word documents though. Most of these, about 60% are PDF files targeting Adobe Reader. If you open it with another reader – you are fine.
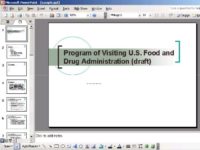
 Well, this was interesting (see image). This was an invitation to a conference, which ran last June, and we actually intercepted this in, I think, April, like 2 months before this. And it says: “Strategic and Tactical Missile Systems Conference”. And if you actually look closer at who is the target group for the conference, well, it’s actually classified secret. So who would be receiving an email with an attachment like this, and to him it would be perfectly normal and usual?
Well, this was interesting (see image). This was an invitation to a conference, which ran last June, and we actually intercepted this in, I think, April, like 2 months before this. And it says: “Strategic and Tactical Missile Systems Conference”. And if you actually look closer at who is the target group for the conference, well, it’s actually classified secret. So who would be receiving an email with an attachment like this, and to him it would be perfectly normal and usual?
Another one was an invitation to an ISSA3 meeting in North Alabama. When discussing that particular file, somebody pointed out to me that most of the members in this organization work with computer security inside NASA, which might have something to do with it, but I don’t know.
And of course we get these not just in English but in all the languages. And not all of them are business kind of content, like most of the stuff we’ve seen here. We also get all kinds of stuff, but what they all have in common is that by the time you have it on your screen, you already have a backdoor on your system. And of course, like I said, all these different languages, so we intercepted a Chinese PowerPoint file containing a backdoor. There was also a Russian PDF file bundled with a backdoor; a German Excel file containing a backdoor; a German PDF file with a backdoor. One sample was Arabic, I don’t read Arabic but guess it’s convincing as well.

We don’t know all the details of the story, but RSA made an announcement, they explained that they had been breached. And they were breached with a highly advanced and a targeted attack. They never made the actual backdoor available to the research community, and they never released the email that they were hit with.
But we have one guy in our labs who just wouldn’t let this go. He would go back every other week and search the virus sample collections, convinced that we have this sample somewhere in our system, we just don’t know which one it is. And then he eventually was going through the system, going through our sample collection of tens of millions of samples, went through all the infected files we have, exported all the Flash components and tried to find the exploit from the Flash components, because we knew what exploit was being targeted. And after basically half a year, he found the sample.
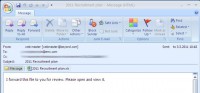
So the mistake made by the RSA was not about the patching, because they could not have patch for this. Why did they have Flash embedded and enabled inside Excel? Maybe it was enabled by default, maybe there was some internal system which required it. But as Outlook is trying to load the file, it just fails in actually getting it on the screen. When it finally then opens up the file, the Excel file has no content, it’s an empty file, but by this time there is already a backdoor on the hard drive, it’s already executed. So that’s the ‘highly advanced attack’ that hit RSA. Who was attacking them? We don’t know.




























