While presenting at Defcon, forensic examiners Eric Robi and Michael Perklin tell some hilarious stories about data destruction fails they’ve come across.
Eric Robi: Our talk is about forensic fails. I’m this guy over here (see right-hand image). I founded Elluma Discovery Company about 11 years ago, I’m a forensic examiner. I have done thousands and thousands of exams; I am also an expert witness in state, federal court, etc. And I like cats. And my name is Eric Robi.
Michael Perklin: Hi, I am Michael Perklin (see left-hand image). You may remember me from other Defcon talks such as ACL Steganography. I am a forensic examiner, cybercrime investigator, security professional. I have also done thousands of exams, and I like to break things a lot.
Eric: Don’t break my cat! So, our agenda today (see right-hand image), we have got seven amazing stories full of fail. We are going to learn something about forensic techniques, because that’s what we do. The fails today are brought to you by both the suspect and the examiner, and we’ll get into that in a little bit.
The names have been changed to protect the idiots on both sides. We have actually changed some of the facts to protect the idiots, and it seemed like a good thing to do basically. But because fail was not just one-dimensional – we found many dimensions of fail in our research – we’ve decided we need to create a fail matrix (see left-hand image). I am just going to explain how the fail matrix works. The first level of fail is the ‘user retard level’; oh my god, I spelled that wrong…
Michael: For the record, he was responsible for the keynote presentation, so this is definitely his fail.
Eric: This is my fail, I get 10 points. So, the ‘punishment level’ depends on what happens, so this particular guy lost the case. ‘Dollars distress caused’, let’s give this one five points, and bonus points are just whatever the fuck I feel like doing. His girlfriend left him in this case, so he gets 35 points.
Let’s get into the first one. This is the “Wasn’t Me” defense (see right-hand image), you may have heard this one before. Alright, so we do a lot of commercial litigation, and a really typical kind of case is a trade secrets case, and this is a typical example of that. So, this guy Bob was working in sales at Acme and he resigned his position and he decided to go work for a competitor. This happens all the time. And some allegations were made by his employer that he took some trade secrets. He took the customer list with him to his new company. It happens.
So, Bob says: “I’ve got nothing to hide. Come at me bros!” He didn’t exactly say that but it sounded good, I’m paraphrasing.
We started imaging the drive and we started planning the examination (see left-hand image). One thing we frequently do is we look for deleted files in unallocated space, and unallocated space is the part of the drive that can typically contain deleted files. You know, when you hit Shift + Delete and it doesn’t go away, it ends up in unallocated space. So we look for stuff there.
Something we also do is we look for recently used files by common programs like Word, Excel, Acrobat and so forth, and we might look for USB device insertion. We are basically looking to see how trade secrets got from Acme over to the new company.
Finally the drive finished imaging, and I’m actually going to share something really cool today. It is a Defcon exclusive, worldwide premier – we found a new wiping pattern (see leftmost image below).
This is actually real, I’m not making this up. Bob had apparently used some kind of data destruction program that can overwrite every bit of unallocated space (see middle image above). He used a pattern that, however, was not commonly used by Windows or any other utility I have seen, it might have been something custom. So, yeah, I thought: “Hmm… This might suggest something bad was happening here.” Let’s take another closer look at this. We are going to zoom in and we are going to look at this on a molecular level now. I think we need to zoom in a little bit more (see rightmost image above).
So, what have we learned? (see left-hand image) Data destruction can almost always be detected. Even if you don’t use a repeating pattern, it is still detectable. We see it all the time, there are artefacts left behind that could be part of the pattern or there are artefacts in the operating system itself. So we might not know what you have destroyed, but we will definitely know you destroyed something.
We have got to do the fail matrix (see right-hand image to check out Bob’s grand total for fail matrix): alright, 12 – pretty retarded, I think. Now, this guy lost the case, he got sued under a hundred thousand dollars, so not a huge amount of economic distress, and I didn’t really give him any bonus points here because it just wasn’t that good, so he gets 27.
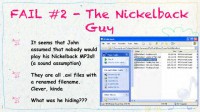
Michael: Alright, this case (see right-hand image) was a lot of fun. I didn’t expect it to be fun when I started out but it ended up being a lot of fun. I call it “The Nickelback Guy”, you will see why in a second. So, it was another allegation of stolen confidential documents. This guy, let’s call him John, left one company to go work for a direct competitor, and his old company hired us to go in and take a look at this.
The company where he left asked us to take a look at his work computer to look for signs of data exfiltration. He worked on a lot of confidential projects and they just wanted to make sure that he wasn’t taking these confidential projects to the competitor and letting them know what they were doing.
So, we open up the hard drive to start the analysis and we start finding the stuff that you typically find on a work computer. Yeah, there is some work stuff, sure some evidence of facebooking. He’s got an mp3 collection. He liked listening to music while he was at work. We found the confidential documents that we were asked to make sure he didn’t take. So, that was to be expected because he did the work on this computer.
And almost immediately something jumped out at me. And we will get into why it jumped out at me in a second. But his music collection became very interesting to me, not because I love Nickelback but because, well, again, we’ll get into this.
I’m Canadian too, and Nickelback is from Canada. If you take a closer look at this photo (see right-hand image) something may jump out at you as well. These are just mp3’s, just songs, but the size of these files is a little bit off.
Eric: What’s wrong here?
Michael: Yeah, the extended play Nickelback. This guy really loved his Nickelback. These were actually a bunch of .avi files that he had renamed. So it seems John assumed that nobody would listen to his Nickelback mp3’s, which is probably a good assumption because I don’t think anybody would listen to his Nickelback mp3’s. He was hiding something but what was he hiding?
Pregger porn! This guy had quite a big fetish for pregger porn. These were full length feature films of pregnant ladies banging, and there are just tons of them all over this guy’s hard drive.
We did have to analyze them to see what they were, but I will say that the specific techniques that we used to analyze – they are trade secrets, so I can’t tell you how much depth we went into when we were analyzing them.
It seems John did a lot more than just work on his confidential project on that computer. So we had to tell the company that over the last three years while he was working there on this confidential project, he was also doing other stuff. They were pretty happy that he left anyways.
Alright, so what have we learned? When we examiners take a look at files on a computer, we don’t typically look at it within the nested folder structure. We don’t have to go into every single subfolder, go back out, go into other sub-folders, back it out. We see it all on a big long list as it makes it a lot easier to analyze stuff.
Also, one of the very first things we always run is what’s called a file signature analysis. This is a special script that looks at the contents of every file and it compares what’s inside the file with the extension, and if there are any discrepancies those files are bumped up to the top of the list to get looked at because the system knows if these don’t match something may not be right here, a human should take a look at this.
And at the end of the day, John’s attempt at hiding his pregger porn actually made it bump up to the top of the list for me to take a look at. So, if you’re going to hide something, don’t just change the filename – that doesn’t hide something, that makes me want to look at it even more.
Alright, the fail matrix. The user retard level – I would say 12 because, again, renaming a file is not data hiding. If you want to do real data hiding you should have come to my ACL Steganography talk. Punishment level – 13. He lost his job, not only the previous company where he left but the new company where he landed – he lost his job there. Distress caused was zero, he didn’t really hurt anybody. I mean, what you choose to do on your own time is up to you, although he chose to do it on work time with work stuff.
Eric: You know what the bonus points are going to be for that, don’t you?
Michael: Yeah, there are going be some bonus points, I would say, about a nickel’s worth. That gives a grand total of 30 fail points.
Eric: By the way, do you like the font that we are using? Comic Sans! Can we get a hand for Comic Sans, nobody uses Comic Sans. It is the most underappreciated font in presentations.
Michael: I don’t know why we don’t see Comic Sans in more business settings, I mean, really.
Eric: We are bringing it back, it’s a new movement. Alright, let’s look at the “Just Bill Me Later” case (see right-hand image). Our client, the ABC firm, outsourced a key part of their business. They’ve been doing it for many years. And the part of their business that they are outsourcing is on a time and materials basis.
So, there are a lot of invoices with hours and rates, and that’s basically it. It was several million dollars a year on average that was being billed. And our client started a review project because they thought they were being overbilled. They thought there might be a little inflation and they wanted to figure out why things were looking inflated. They looked at some of the individual bills and they thought things were taking a little bit too long. So we came in and decided to help.
They had thousands and thousands of PDF format invoices. And that is not going to do us a lot of good even if we OCR it, even if we apply optical character recognition to it we still got a lot of unstructured data. I can search one or two PDF’s but when I’ve got tens of thousands of them it’s really difficult to do anything with that. So where do we start? We didn’t have a lot of clues in this one.
So, through the magic of court order, we were able to go to this customer’s database, their network and get an image of everything in their network including a billing database, which turned out to be very handy.
We made a forensic copy of this database, and it was in a proprietary format. In order for us to do forensic analysis in a database, we need to be able to get it into something like SQL where we could do kind of standard query. So we migrated over, we do standard queries and we’re looking at it, and there is still no easy way to compare the PDF to the database. So we decided to reverse engineer the tables in the database. Sometimes it’s easy but sometimes there are thousands and thousands of tables, and when we don’t have tech support or the developers you just have to figure it out. So it’s a really slow laborious process but we did figure it out. We noticed that the audit logs were turned on in this, which happened to be particularly useful.
So, we ran a lot of queries – time billed versus the audit logs, and we found there was sort of a pattern of inflation going on; because basically when you’re billing on time and materials, all you’re doing is you’ve got either hours or you’ve got a rate, and those are the two things that got overinflated.
Basically, there are two things that you can change there. You can change time or you can change the rate. But we found the audit logs were turned off by default and the IT folks, bless the IT folks, they turned the audit logs on, which was really, really helpful because we do a lot of database forensics cases and this is the only one we’ve seen where the audit logs were turned on.
So we were able to compare, basically, the amount that was billed at the end of the day versus how many hours were put up to that point, we were able to see a chronology. So maybe at the end of the day the bill was for a thousand dollars but we saw that there was only eight hundred dollars that was actually billed.
The billing person, the database person who basically was working with this – this person would change the hours and the rates sometimes and bump it up. So it went from, like, eight hundred to a thousand dollars on a typical invoice. They did this thousands and thousands and thousands of times.
So, let’s look at the fail matrix. I didn’t give the ‘user retard level’ too many points here because it was a billing administrator. Most of the average people don’t really know what’s going on inside a database. However, they had to refund the money, so they get 18 points for that.
Michael: …Over the last 4 or 5 years’ worth of money. So it was a lot of money.
Eric: It was about 12 million dollars actually. So they get 15 points. And bonus points – systematic culture of overbilling. They get 45 total.
Michael: I call the next one “Smoking Gun.txt” (see right-hand image). If you work in the forensic arena, you’ve probably heard the term ‘the smoking gun.txt’. It is the gag name of what you are always looking for in a case. It could be that record in the database; it could be that Internet history record that shows that the guy really did something bad. It comes from the cheesy western movies where, you know, the murderer’s gun is still smoking after he shot it. It proves that he was the one who fired the shot.
So in forensics you always say: “Did you find the smoking gun?” – “Yeah, found the smoking gun.txt.” Sometimes I wish it were as easy as finding a file named ‘smoking gun.txt’, but you can only wish.
This is another intellectual property case. Again, you got a guy leaving one company to go work for another company. And the first company says: “Can you make sure he didn’t do stupid shit?” And we were called in to make sure that he didn’t do stupid shit.
So we imaged the drive, kicked off our standard analysis scripts like the file signature analysis script I told you guys about before, and opened up his desktop folder. I like to open the desktop folder of every suspect that I am examining because you can tell a lot about the person when you are looking at the desktop. Do they cram a lot of files in there in an unorganized fashion, or maybe everything is neatly packed away in the My Documents folder? Things like that… Are they arranged nicely, or is it just all smattered? It tells you a little bit about the person so you can get a little bit into the mind of who they are, and immediately I solved the case.
Eric: How did you do that?
Michael: Well, this is the ‘smoking gun.txt’. It was almost as easy as this (see right-hand image).
Eric: With a barbecue?
Michael: So I opened up the desktop folder and I saw this (see left-hand image). I will read it out for you: you’ve got a folder on the desktop, and you can see at the bottom left there that the folder is called “Competitive Intelligence”. And inside that folder we’ve got a PowerPoint presentation titled “Project Bluebook”. We’ve got some PDFs, we’ve got a whole bunch of stuff about this “Project Bluebook” that this guy was working on from his old company. He was getting ready to deliver this presentation to the executive leadership team of the new company, telling them everything about this confidential project from his old company.
He didn’t even make it difficult for me. It was not only that all this stuff was there, but he made a PowerPoint presentation describing it to deliver all the knowledge for this.
Eric: Michael, what have we learned in this case?
Michael: Well, we learned that sometimes people don’t even try. Fail matrix: alright, the user retard level has got to be 18. Sorry, we are saving the higher scores for some of the later stories.
Eric: The numbers are going up as you may have noticed.
Michael: Yeah, so far the numbers have been going up. He got 18 for user retard level because if you are going to be doing this, don’t leave tracks all over your computer. I mean, sure, if you are going to say they are going to be launching this new thing in August next year – that’s one thing to say it to a person but if you put together a whole presentation about the thing – that’s fail. Punishment level is 10 because he had to settle, he’s obviously in breach of his NDA from the old company. And it cost him 1.5 million dollars in damages. So the distress caused is a six-pointer, and bonus points of 12 for zero effort. This all adds up to the fail matrix score of 46.
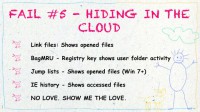
Eric: Alright, the next one I call “Hiding In The Cloud” (see right-hand image). So, once again, a top sales guy leaves the company, and the sales just take a nose dive actually, and they think he took the customer list but they can’t prove it. They know that there are old customers over at the new company but they can’t prove that he has taken the customer list. So we image his computer and we start looking for the usual kind of clues.
For example, link files, a Windows artifact that shows what files have been recently opened; they are simple text files and they are pretty easily parsed and they have got a lot of information about the location of the file, the date and the time, all that kind of good stuff. We look at a registry key, and I just love the name of this. It makes absolutely no sense to me at all but somebody at Microsoft maybe had a couple of beers when they were working, it’s called BagMRU for some unknown reason.
So it is a registry key that can show user activity and it can show what files are inside a folder. That’s one of the things that we typically look at in a data exfiltration case. Jump lists, which are from Vista – I just don’t love Vista enough to put it in there. Anyways, the jump lists are the thing on your taskbar if you’ve got, like, five Word documents open, and you click on it and you’ve got the five – those are jump lists, basically.
And IE history – Internet Explorer is so much more than just exploring the Internet. It actually records things that you do without your knowledge, like opening files. But we’re getting no love, I’m not finding anything. Show me the love baby.
Alright, so we searched the IE history, and we found an .htm file that had some JavaScript in it pointing to filesanywhere.com. Who is familiar with that site? It is very much like Dropbox, the same kind of concept but it is more for business users. It’s got a lot of really great auditing and logging and stuff like that. So if you’re uploading and downloading files you can, basically, monitor and track them and so forth. That turned out to be a very nice thing because typically that’s only in the User Control Panel, but we found this little .htm file, and bingo – we solved the case!
So, what we got was the account ID, the upload times, the filenames, everything. We got some sweet loving, we got ourselves some stolen files. Let’s look at this little actual bit of JavaScript here (see left-hand image).
I have changed the names of the files in this case, but, you know, we got “Stolen_File”, “Recipe_for_Coke” for example – you know, minor trade secrets. The user is the user account name, so we were able to subpoena that from filesanywhere.com and figure out who actually registered the account. There is the folder that it was in (see right-hand image), and this is really handy here – the date that it was uploaded, and we got a whole bunch of these. In fact, this is the first page of an about 80-page Excel report that I prepared, and these are all the filenames that this guy uploaded.
The second part of the case: the opposing attorney, the guy representing the thief, handed us a CD with Outlook.PST on it, and this is part of the discovery process. Discovery is a legal term in litigation where both sides are able to exchange evidence; in fact, they’re compelled to exchange evidence through the rules of the court.
So he gives us a CD and it’s got an Outlook.PST on it (see left-hand image above). The first thing we do is we want to recover the deleted emails in the PST, because we are forensic analysts and that’s what we like doing, we like looking at people’s emails.
I am going to show you the old school way of recovering deleted emails (see image above). You can use a hex editor, you crack open the PST and you change bytes 7 through 12 or 7 through 13; change them to 0s, save the file. Then you use the Outlook Repair Tool which is built-in with Microsoft, and you basically repair the PST, and what happens is you get a lot of emails back (see image above). Now, these are not the actual emails but you get tons and tons of emails back.
And in fact, in this case we got tens of thousands of deleted emails, and what was in these mails? Everything that completely turned this case around.
So, not only did we have this guy with all the uploads on the spreadsheets, we also had all the emails about who was involved, what lists he took, who were all the people that were involved. We were winning, we went to Charlie Sheen mode all of a sudden. And the funny thing is we were able to take all this information at a deposition, and if you don’t know what a deposition is – we get to ask questions of the opposing party.
We were asking them: “What happened? Did you guys steal anything, did you take anything?” – “No!” We started pulling out these emails one by one by one, and the guy turns white as a sheet, and he spills the beans, and basically, you know, we do pretty well. So, who do you think deleted the mails in this case?
Michael: Call it out if you think you know who.
Eric: They hired Saul Goodman unfortunately, and yeah, he deleted the mails, not a good thing, not a good thing… So, what have we learned?
IE history is actually really difficult to wipe – that’s what we’ve learned. It seems to leave stuff behind. We found a new artifact which is actually pretty cool, filesanywhere.com, this JavaScript artifact; I haven’t heard this being discussed anywhere before, so I think it’s kind of cool. JavaScript files can give us love too, we like them. And uploading files still leaves traces. And attorneys shouldn’t mess with evidence; it’s against the ethical rules in every state and in probably every Canadian province, and it can get you disbarred actually.
Let’s look at the fail matrix (see left-hand image). The user retard level is pretty damn high on this one. We got fails on the attorney’s part and also on the ex-sales guy. Huge lawsuit, 3.5 million dollars in fees and damages, which our client all got back basically; and 15 bonus points, the attorney might lose his license on this one. He hasn’t yet, we don’t know, we don’t track that kind of stuff. 51, we’re moving up.
Michael: This next case (see right-hand image) was probably one of the most fun cases that I have worked on. Right from the start I could tell that it was going to be a fun one. I call it “The RDP Bounce”, you’ll see why. I was called in to investigate a network breach. The company told us and they shared some information with us that there was evidence that at least one computer had been breached. They didn’t know why, didn’t know what, and they asked us to investigate and to tell them why and to tell them what.
It was a large company, they had a lot of computers, all of them were Windows-based, thousands of computers in offices all across the world. In one of their offices they noticed that this computer had been breached. So let’s figure out what happened.
We move in and analyze the one computer that they knew was breached. It showed that RDP, Remote Desktop Protocol – this is the tool that’s built into Windows that allows you to remotely control another computer – some logs showed us that RDP was used to connect using the local administrator password to another machine. It showed that RDP was used to connect in and it also showed that RDP was used to connect out. So, in this little diagram here (see image above) we are also looking at the middle computer, I didn’t know at the time that there were other computers. I was just looking at the middle one, and it seemed that there were a bunch used in here. So it was probably the tip of the iceberg.
Eric: Where do you find these logs, Michael?
Michael: Specifically I was looking at the Windows event log, the Event Viewer. If you go into the Control Panel and the administrator tools, there is the Event Viewer tool. By default it logs a lot of stuff in there including when RDP is used to connect in and when you are connecting out. So I analyzed the machine that came before it – same thing. There were logs that showed that someone was connecting into that. It was basically an entire bounce.
Now, these computers were located in different offices all around the world. This guy was bouncing all around the world to do something. So, obviously, this is a pattern. I still didn’t know what he was doing. I just knew that he was, clearly, going through a lot of trouble to obfuscate his trail, bouncing all around, probably so that when he does hit his final target there’s no direct evidence to where he was coming from.
Audience: Were these sessions within sessions?
Michael: Yes, they were all sessions within sessions. He opens up a remote desktop, and then within that remote desktop window he opens up another remote desktop to another machine. He just did this over and over. It must have taken him hours because remote desktop is not the fastest protocol at all. I don’t even want to speculate how long it took him to do this.
Eric: Can you imagine how long the screen redraw was by the time you get to, like, machine ten?
Michael: Jesus Christ! You probably have to double-click with, like, a minute in-between clicks or something. So, what was the target? I think you can all figure out what I am going to do next. Rather than following the trail back I started to follow the trail forward. What was he getting? Step after step, computer after computer, site after site after site all around the world, I finally reached the high-profile machine. I wish I could tell you which specific machine it was; I can’t because it would give away too much about this company.
Once I reached this machine, I knew exactly what he was going after. He wanted highly confidential documents that were only on this one machine in the entire company. He obviously knew this and he wanted to get into this machine to get these documents.
So I focused my analysis on this target machine, on this special confidential machine, and I wanted to see specifically which files they took. It took me only about two minutes as I was analyzing this machine, I identified the attacker immediately. He went through all around the world, and finally when I was taking a look at his target, within two minutes I found out who he was.
Audience: Did he use his own credentials on the machine?
Michael: No, he did not use his own credentials on the machine. Any other guesses?
Audience: He emailed it to himself?
Michael: Nope.
Audience: He stole his own file?
Michael: Nope.
Audience: Shared drive?
Michael: No shared drives. Why don’t I tell you what he did?
Eric: Michael, what did he do?
Michael: Printers! So, one thing a lot of people don’t know about remote desktop is by default it maps the printer connected to your machine to the machine that you’re connecting out to. It does this so that when you hit Print inside your remote desktop window, your printer next to you is available so you can print a document beside you. Now, this guy didn’t print any documents. Just by connecting, his machine automatically mapped his local printer to the target machine which identified his machine name. He forgot to turn this off. There’s a checkbox in Remote Desktop Protocol; when you open up the RDP window you hit Options and then uncheck Map Printers to Target Machine. It’s just a checkbox, he did not uncheck it.
Audience: Wow!
Eric: What have we learned, Michael?
Michael: Well, log entries that are created by innocuous system events can give insight into user actions. Now, he didn’t map his printer, the system did it automatically. So sometimes just looking at what the system is doing can tell you what the user was doing.
For the fail matrix (see left-hand image), user retard level would be about 20 because he went through a lot of trouble to cover his tracks and he did not cover his tracks. Punishment level would be 15: he lost his job and he also lost his references, he can’t use that company as a reference anymore. Distress caused would be 8. Bonus points would be 20: do some research! If you’re going to use RDP to pull off some kind of a scam, know how RDP works. Adding it all up, we get a fail score of 63.
Eric: Alright, the last story is a little bit different than the others. This is the “Epic Porno Fail”. The difference in this one is all the other cases we’ve talked about have either been commercial litigation, civil litigation, something on that side. This one happens to be a criminal case, and from time to time we do criminal defense work and we work either with public defenders or with private attorneys, and this is about this kind of situation.
So, our client Edgar has been charged with possession of contraband aka child porn on his computer, pretty unsavory stuff. He claims innocence, as usual, and I kind of roll my eyes because everybody always claims innocence, and 98 percent of these people did it.
We examined the computer, looked at the examiner’s report. We looked at the allegations, and let’s take a look at them (see left-hand image). They claim Edgar downloaded porn. They claimed that Edgar’s user account had passwords; this is all documented in the report. And they claimed that Edgar utilized newsgroups to download porn.
Michael: Who uses newsgroups to download porn? Anybody?
Eric: Ok, so they alleged that he downloaded illegal porn, and there is one thing to note, keep this in mind as we go through the talk: he left his house in April 2012 because his wife kicked him out because of all this stuff happening basically; so, April 2012, keep that in mind.
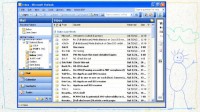
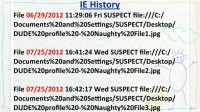
Let’s see what we came up with while examining the computer. First we looked at IE history (see left-hand image). As I mentioned before, IE history is able to show you when a file has been opened, so this is an actual example. I’ve changed the filename a little bit here. And what was the date that I just mentioned? April 2012. Ok, I see some dates here. Are these before or after April 2012? Put up your hand if it’s after. Alright, one fail here.
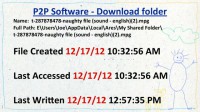
Let’s look at his peer-to-peer software download folder (see right-hand image). So, in the top there I’ve got the path where these naughty files were downloaded. And it’s a pretty typical path; these P2P programs change the filename to something long, so it’s like t-something-naughty file. I’m looking at the dates here again and… Michael, do you have a calendar? When is December?
Michael: It’s after April.
Eric: Ok…
Michael: Definitely after April.
Eric: Just wanted to check, we need to verify our forensic findings before we can publish them. So, you know, we’re verifying.
Michael: Fail!
Eric: They also claim that he used Outlook Express, really, to download porn. This is 2012, remember folks?
Michael: Makes me wonder, did they even analyze this guy’s machine? Where are they coming up with this stuff? We saw records of P2P, not Outlook Express.
Eric: In reality, yes, Outlook Express was on the machine, set up with an account called “PornoLuvr”. Ok, it was set up after Edgar moved out of the house, and only headers were downloaded, no content.
Michael: What do you mean by headers?
Eric: If you are using Outlook Express, a header is just the first part of the file. The email is going have the date, the sender, the receiver, maybe the subject line, maybe the first couple of words. But there was no content, there were no photos in there, just headers with, you know, admittedly porno names.
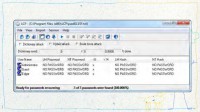
Let’s take a look at accusation number three (see left-hand image). They say his user account had a password, and the inference is that only Edgar was able to access it because there was a password. Let’s look at the password, shall we? Maybe we can zoom in a little bit on this.
This is actually a really cool utility, it’s free, it’s called LCP (see right-hand image). I will just go back to it for one second here. It’s a free utility. It’s really great for looking and seeing if there are passwords. You can also use it to perform an attack although it’s not very good.
Alright, more facts (undiscovered by the examiner). The P2P client was used to download porn – examiner didn’t find that – into a new user account called “PornoLuvr”, guess when – after he moved out of the house.
So we submitted our report to the prosecutor, a 5-10 page report, something like that, and the government drops the charges years after they charged this guy (see right-hand image). This does not ever happen, really. This is the first time. I have done hundreds of cases, thousands of exams, I don’t know how many. It had never happened before. And this is after the guy spent a huge amount of money on legal costs.
So, to do all this I just want to give a thank you to Rob Lee and SANS. We use Super Timeline Analysis to do a lot of this work. Super Timeline is a really amazing piece of software that will, basically, go through the computer and look at all the computer-generated artifacts and put everything into a nice chronological sequence for you. So, a really awesome piece of software.
Michael: Definitely one of the best pieces of software I have used.
Eric: So, the government interviews Edgar’s friend; the friend confesses, the friend did it. The friend was trying to get jiggy with Edgar’s wife and he put the porn on the computer. The court clears Edgar’s name (see left-hand image). They give him a finding of actual innocence; never happens.
Michael: I’ve had many people claim innocence, and this guy actually claimed innocence, and he really was.
Eric: Yeah, rarely happens. I have been to court a couple of times where they have been acquittals. And we didn’t go to court on this one fortunately, but we would have.
So, what have we learned? Base your conclusions upon actual evidence. Find multiple artifacts backing up your allegations – I don’t know where the password thing came from. Tie it to a person, not just a machine if possible. Try to look at user activity that would tie specific events to a person.
Remember, the maximum you can get is 20 in any category. However I have decided to break the rules a little bit for this one. So, examiner ineptness – he gets 5 bonus points built in right there. Oh yeah, the guy sued the city for millions of dollars; and, you know, there might be a job security issue for somebody in this case…
Michael: I don’t think that examiner is going to really have a job much longer.
Eric: And 100 bonus points because the court finds the suspect innocent, factually innocent. Thank you very much!
Michael: Thank you everybody!