
 Distinguished security specialist Winn Schwartau delivers an engaging talk at DerbyCon, covering the issues of technology being exploited and weaponized.
Distinguished security specialist Winn Schwartau delivers an engaging talk at DerbyCon, covering the issues of technology being exploited and weaponized.
Hi! How many guys are actually hacking here? We’re going to talk about some issues that really got me crazy in the last couple of years – thanks to RenderMan back there, it’s his fault. We’re defending against hacks; that’s why we’re still stuck and so screwed. And why are we screwed? Does anybody think that we’ve got all the security shit done really working well?

Back then, a number of years ago I wrote a book. It’s called Information Warfare and was published in 1991 or something. A couple of days after it came out the FBI and CIA are at my door, going: “Where did you learn all of this stuff? It’s all classified.” I never had a clearance, don’t want a clearance, and I didn’t really understand the question. How could this be classified if I thought of it?
I got into a lot of trouble with the feds. The Brits decided to ban the book and realized after six weeks that it was not a successful strategy. And Information Warfare was about attack mindset methodology, in front of Congress and all that stuff. Back in the day they would say: “Why would the bad guys ever want to use the Internet?” That was the police system when I got involved in all that crap way back. I don’t believe that mindset has changed very much. Have we done a really awesome job with security in the last 20 years? Show your hands. Any vendors? Show your hands!
Way back when we were talking about the issues that hackers were vilified and all the crap back in the day, and people didn’t listen. People did not understand and did not want to believe anything that we were saying. The concept of cyber terrorism back in 1988 was: “What the fuck? What are you talking about? Are you nuts?” And I, seriously, for many years was wondering that where we are today was never going to come to pass.
Unfortunately, I was right about too many things. It was almost like a science fiction-ish thing in many people’s minds. And in my mind I had a great deal of doubt as well, because I was so disgusted with the state of the security industry, and vendors doing their bullshit. If there are any vendors in the room, I’m sorry, I’m a vendor too – and hopefully I don’t whine much. But some of the vendors out there are like: “Damn, come on, let’s get real!”

Some of these predictions (see right-hand image) have come true over the years. Some of the stuff I talked about: malware – I said it could be a form of war. “No, it’s not, Schwartau, you’re crazy.” Alright. Chipping – back in those days I made a hypothesis that we’re going to end up with third-party source silicone with built-in malware. “Schwartau, you’re out of your mind, Intel would never do that to us; you’re missing the point here.” And now finally there is some national awareness on the DOD level that chipping, or embedded hostile silicone, whatever term you want to use, is actually real.
We’re going to talk about HERF and EMP a little bit. Back in 1994-1995 I did for WarCon in DC; we set off a 1 terawatt EMP weapon, right next to the National airport. It was really cool. This was all off-the-shelf terrorist-level technology that I was interested in some 20 years ago, and how this technology was going to be adapted in the coming years.
Some of the global things back in those early days – in 1996 I was trying to say: “This stuff is a national security asset; information and economy and all these things,” and everybody said: “Bullshit, it’s not real, it’s not going to ever happen.” And we chose ignorance and arrogance and apathy road, routes, especially to Washington. And I guess some of you still go through bosses who don’t believe this stuff. There’s a few of you who have it like: “We’re not going to bother with this.” That is, obviously, from a paranoid hacker security mindset; absolutely not true.
We’re trying to move that forward somewhat, and even in the military it’s really the same. What about all the stuff that’s pre-kinetic? And I’ve always been interested in the pre-kinetic effects of things, because everything that’s going on beforehand has always been of big interest to me.

The argument has been “Using the will”, it’s been about capability; growing up is really what I was talking about. What are capabilities? At that point, in the early 90s, it was kind of us, pretty much alone, the US, but there were a lot of capabilities being developed. And it became a psychological mindset: “Are we willing, or the bad guys will be asymmetric?” And my argument was, and still is: “Yeah, they’re going to go asymmetric, because they don’t give a shit. They don’t care. Their beliefs, their culture, whatever their religion is, and all kinds of things that we see, are vastly different than us.” We cannot go by typical type of symmetric warfare mindset. It is going to be asymmetric and we’ve certainly seen this going on more and more over the years, and what just happened with that mall in Kenya – it’s like “Damn, it’s really getting insane out there!”

Defensive postures were initially set up by US military. And it was based upon the model developed in the 1970s, and effectively it said: “We’re going to build big walls around our computers to kick the bad guys out.” And that was the war network. We can dial in on our 300-baud modems, and some of us may remember: when we could download 4 pictures, it was a good night.
So they developed a concept of fortress mentality: “Keep the bad guys out!” The argument in the early days was: “How do you have anything working if you’re not connected?” Another argument was: “You have a chocolate shop on Main Street. Do you want the bad guys in your store? You don’t want the bad guys in your store, do you, right?” And we were: “What about a chocolate-loving bad guy? Your goal is to sell chocolate, so you want the bad guys in, if they buy chocolate. And how do you determine whether they’re a good guy or a bad guy before they rob you?”
That fortress mentality is not going to work, especially with what we’re all trying to achieve today. And this was the mindset, and it still largely is. According to my DOD friend, the problems that they had 25 years ago are exactly the same today. Things are not getting any better at all.

We’re starting to look at history. I’ve always been a history buff about when things got asymmetric. I guess, mustard gas – World War I, the A-bomb in World War II, when we actually got asymmetric for alleged good reason, whether you believe it or not, it was certainly an asymmetric move at the time.
As we moved to the unipolar world we thought it was going to be this peace everywhere. We scaled down everything, saying: “Peace on Earth now. We won,” which is clearly a massive, massive error, because the whole concept of waging war on the Internet was unknown to most people. They couldn’t grasp the concept of warfare being in that domain.
And again, we were right, they were wrong; and unfortunately, we’re all suffering. And it becomes an issue of capabilities, in my mind. I don’t care about motivations, because I can assume very easily the spectrum of motivations, from peaceful to the truly, totally, completely evil, dark, whatever you want on this side of the spectrum; then everything else is going to be in the middle. It’s about the capabilities in an open source world. And that’s where we are and why we’re sort of in the mess we’re in today.

I got interested very early in the concept of weaponization (see right-hand image). And we look at the history of technology, and we can go back thousands of years. Bronze was a great technology that meant for good, and we adapted it for bad. We continuously adapted new technologies and weaponized them one way or another.
So we keep weaponizing, and people keep introducing technologies in the hope that they’re not going to get weaponized. All of these things we are too familiar with, the kind of cool technology that came along, and how it’s continuously been adapted for bad stuff.
So, new technologies: was cryptography ever able to be used in a bad guy mechanism, originally out of the US? And it was the only technology, other than nuclear weapon that was completely classified by the DOD and the military establishments, because we owned that domain. And then open source came along, and it opened up this whole world of potential anonymity, disguising of data, where the private citizens could actually participate and do things that, prior to the data generated earlier, were completely owned and operated by government. So, that was a very fundamental change in the relationship between government, military and private sector around the world.

We kept developing more and more technology. GPS was originally developed as a military technology, and how many of us don’t have GPS on us right now? Probably not one person in this room. Can the bad guys use it? Yes. Do they use it? Yes. Do we have a defense against it? The only thing we can do currently is change the accuracy of the GPS signal. We can change it from 10 feet to 100 feet to 1000 feet, which means aircrafts then have a whole different system of takeoff and landing than the one that they currently do, because they’re relying on the same sort of stuff. Satellite reconnaissance – I don’t see too many people here with the aluminum hats on, but we all know that the NSA is listening in on our thoughts, because they have this technology that they got from aliens from Area 51.
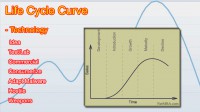
What we have to look at is life cycle (see right-hand image). One of the things that you get – there’s no magic here, there’s just standard life cycle curve – is the concept of “when an idea for a technology is developed.” Typically it’s done from profit-making or hopefully humanitarian aspects. And then there’s a proof of concept, and we finally end up with deployment. The issue has become, in my mind: at what point through life cycle does weaponization occur? At what point do we start looking at the hostile aspects of technology?
The argument is: “All new technologies will be weaponized.” I remember sitting with Al Gore in 1990 in Nashville, and he announced that “Oh, we now have the Information Superhighway!” And the cameras were rolling and I said: “Mr. Al, this is all really cool, with the Internet and all that. It’s going to be awesome, right? But what about…” and I laid out a few ideas on how the Internet would be weaponized. Gore leans over to somebody and says: “Who the hell is this guy? Get him out of here.” And that did actually make it on NBC, and that was kind of cool. But they were trying to only put the positive spin on stuff. Anybody here been to an Apple store and they ask how your MDM is? Seriously, Apple? This positive spin on everything is hurting us if we, as a community, have to readapt some of the thinking and look at the hostile way things are going to be occurring.

IPv6 – we’re going to migrate (see right-hand image). What’s the migration number currently? Somebody gave you that number, and I don’t know, but no one is really arguing and I’ll stick with it. But was IPv6 really designed for functionality or security? It was designed largely for functionality, address space issues, and there’s an awful lot of null packets in there.
A bunch of IPv6 guys are saying: “Oh, we know how to weaponize this.” And so there is some cool stuff coming out of the weaponization of IPv6. There were some alternatives in the design of the protocol that were available at the time, using various types of defaults that could be modified later on for real application and utility. But, again, we did not think of this, because IPv6 was going to solve all of our IPv4 problems, and again, I don’t believe that for a minute.
When you’re online talking to your foreign people, is that a real woman that’s talking to you? Probably not. We’ve got all of that Siri and other droid voice stuff. Who are you talking to? Is it a computer or is it not a computer? And you’ve got an old phrase: “On the Internet you never know who is a dog,” or something like that. Now that we’re using this technology so much, how do you weaponize it? I’m not looking for answers this minute; I want your mind. You guys are the brilliant people in the community that figure this shit out before we get nailed by it.
We’re going to weaponize this stuff one way or another. I’d rather the community figured it out ahead of time, because only then can we start defending against the future instead of waiting for the bad guys to already implement it.

Some other technology: how do we weaponize telephones? We’ve already done it. Back in those days, I grew up on those dial things; I got busted by the FBI for hacking three slot machines when I was 10 or 12 years old. And then we’ve got mobile. It’s a computer, and how do we treat these things? Like old Nokias. These are computers, and MDM solves all of our problems, because Apple told it so. Was security ever considered in any of these devices? Of course not, because it was only a consumer device. Consumerization is one of the worst things that’s ever happened to networks. And how many CEOs or board-level people said No to consumer devices? Any people in this room have your board level people just say No.
Weaponization of these is going to happen. It already is happening. Three billion of these sons of bitches are out there, and the bad guys are going to completely ignore it, aren’t they? They’re never going to go after casual users? If anybody’s interested, I do have some papers out called “Cyberwar 4G”, which covers an awful lot of the issues that are going on with mobile, and where we’re going to end up in the coming years.

Oh, here’s the slide (see right-hand image), perfect. This gets into more and more, we’re going to get 20 billion of these things out by the end of the decade, some sort of mobile, IP-enabled stuff. Fundamental problem, really quickly: single-user, non-multitasking devices are wrong, because there’s only half a dozen, I think, 7 built-in native multitasking capabilities, and anything you need to make it multitask beyond that is called what? Jailbreaking. The numbers are already speaking for it. I remember three years ago I got one of the guys, and he made the statement that bad guys will never build malware for mobile. And my first comment, and I actually put this in the article: “Are you kidding me?”

Next thing I’m really interested in is EMP and HERF (see right-hand image). Why do I care about EMP and HERF? It makes some other technology useless – perfectly good words. And we’ve known about it since some of the earlier tests in Bikini Island in 1946, and it was one of the accidental side effects, when some of the ship’s navigation systems that were monitoring the test went down.
We have HERF – High Energy Radio Frequency, EMP – Electromagnetic Pulse, HPM – High Power Microwave signals. And we’re starting to see programs that have been highly classified in the military. They began in the late 70s, called DEW, Directed Energy Weapon, sort of Star Trek-y, Star War-ish kind of stuff.
And I was curious: what can the bad guys do? The first one I saw, I don’t have a picture here, was in Holland. It was in 1990, and it was part of the old Star Wars project. Does anybody know what a Jacob’s Ladder is, any EE kind of people in the room? Alright, cool. It’s good that we have geeks in there, and not the RSA corporate assholes.
And so, Jacob’s Ladder is an electrical multiplier, and these guys wanted to make Christmas lights and use them for cool stuff in their condo. Turns out, their neighbors said: “How come you’re turning off our computers?” Oh, unintended effect, cool. And they ended up being able to spark gap discharge and take down stuff for a couple hundred feet. It was random, they couldn’t repeat it, but I really got intrigued by this.
So, when I went in for WarCon in 1994-1995 I got a buddy of mine who built this device down there (see middle part of the image above) – it used a wide dispersion pattern and was able to shoot down shit; he said a kilometer, he lived out in the desert and he did the testing. And I thought: if it’s inside of a building, there will be a much shorter range but he was in the desert. And I said: “How do we do something even cheaper?”
Some of you know who Heinrich Hertz is. Who does not know Heinrich Hertz? Perish yourself with your hands. No hands go up. Oh, wait; you don’t know who Heinrich Hertz is? 60 Hertz on the wall, right? Hertz, he was the guy, he invented electricity. If you believe this, get the hell out – no, I’m kidding.
So we found his original book on Hertzian Generator, I think it was from 1882, and we said: “Let’s build one with a car battery.” We plugged it in, shot it off, had a capacity so we could do the spark gap stuff, and thankfully the guy with a pacemaker didn’t die. The VCR died, the cameras died, and we thought: “Wow, this is really cool!” And then we upped it with a couple more car batteries, and probably shot off a Terawatt next to a National airport. Don’t be scared of a Terawatt – has anyone read my book Time Based Security? A few of you, maybe. It’s called the byte by time – a Terawatt over how much time, because then you’re looking at average power, spontaneous power, people forget that these are all parts of the fundamental Hertzian equation. Again, I’m going back 150 years here. It’s fundamental EE stuff that we have ignored.
Now, imagine you work for a bank. Imagine a branch office going down at 9:46 for no known reason. 10:13, goes down for no reason. 11:17, goes down for no reason. This stuff cannot be tracked, cannot be seen unless you’ve got specific EMP kind of monitoring capabilities, which puts you then into the nation state realm.
Are the bad guys going to use this? Take a look at the British tabloid and papers from 1996, headlined: “British gang taking down banking services for 400 million pounds.” One article was published, and the Secret Service and the MI6 pulled everything immediately thereafter. Is it going to be adapted? My belief is Yes, which comes down to a concept: “How do you defend against it?” How do you defend against something like this? Research, start somewhere.
My answer is: 1) you guys start thinking about it; 2) graceful degradation. How do you take your networks when they’re under attack of any sort, of any vector, how do you gracefully degrade services without having a binary function? Digital is not binary; it’s still on a spectrum. Our network, we designed this so that all data is equal, let’s protect absolutely everything – it’s not real. But some of the fundamental concepts that we’re using have this binary mindset. Degrade services gracefully under your control and design those into your network.

Some more technology: Un-Manned Vehicles – UMV (see right-hand image). A few years ago at WarCon we had a UMV helicopter. Now we have UMV. Has anybody seen the pizza delivery helicopters? That’s kind of cool! As these get more and more prolific outside of the military domain, and we’re starting to commercialize them – put on your evil hat, what can you do with this? Pizzas falling from the sky… Can we intentionally cause some sort of damage through our un-manned vehicles?
Right now we’re talking about cars that are all going to be autonomous driving; they’re going to be safer. Are we going to screw with them? Has anybody screwed with car hacking yet in the room? Alright, we need more of this. I was on the phone with OnStar three years ago, and they said: “We want to add some security” – “What do you need?” – “Oh, we want this to work…”, and they actually had these ideas. I said: “Yeah, but you need this and this, etc.” They said: “Yeah, but it’s going to up the cost like $4.” For your 37,000-dollar car that $4 is going to break your bank? And what are we seeing now? We’re seeing… what are they called? CAN – the Car Area Network, I think it’s awesome. The University of Ohio right now is doing a hacking; they’ve got 150 people now actually hacking all of these cars. I want you guys to think about the evil side of this before the evil guys start taking over and we start losing more and more.

There we go! In Germany they’re really paranoid about these things (see right-hand image), so what they do is they’ve got a cage with bumblebees in. They recently discovered on how to mechanically reproduce birds and flying bugs with new aerodynamic principles. Now that we understand how bumblebees fly, we can duplicate them with silicone parts, etc.
When you’re in a meeting, super sensitive board meeting, and there is a fly in the room, what do you do? Cancel the meeting? Yeah, ok. We’re going to have a very difficult time being able to distinguish quickly what are real units and what are silicone units. How do we adapt ourselves to this kind of espionage, whatever term you want to use, or this technology? Are we ready to start defending against this, or are we going to have to wait for the first half a dozen incidents, and then start having to catch up again? And I’m really tired after 30 years in security of still playing catch-up. I want to get thinking about these things earlier and earlier.

Some stuff is amazing these days, some of the new technologies. We are going to have bio-engineered prosthetics. And can we fuck with that technology? We have a lot of security problems with computers and networks and devices, or whatever – now we’re going to merge it with the humans. Are we ready for that, when the bad guys start screwing with it? Or should we start designing in higher levels of defensive posture before massive deployment of this technology? I argue we need to do better defensive engineering at the life cycle development curve. And every development team should have hostile people as part of it, build in the hostile mindset at the very beginning of every development cycle.

Brain stuff: they did it on a TV show, it was one of the news channels, and they had a quadriplegic lady, and they gave her some implants on her brain and whole mobility with silicone devices and hardware. It was absolutely amazing. She was able to actually eat ice cream using her brain waves. Are we going to be able to screw with this? The answer is Yes. This technology is in alpha stage, it’s proof of concept. I want evil minds addressing it now, before some committee says: “I truthfully state that this is going to work great in an ideal non-hostile environment.” And that’s, unfortunately, how many standards are created, in a simple benign environment, and I don’t believe that we live in a benign environment.
We’re going to be treating mental illness with more and more electronic type of impulses. We’re seeing much more with audio waves and cancellation frequencies. It’s an interference pattern that exists electromagnetically. They are having a very profound effect upon various forms of mental illness. How do we screw with that?
Military is taking sound waves and using them for crowd control. Is that ever going to end up in the hands of the bad guys? Hell yeah, because whatever the good guys can build for a million dollars, you, when you’re not looking at porn, can do for $10. That’s what this community does: takes that million-dollar thing that I can do for $5. It could be the other way around. The point is: this community knows how to reverse engineer and duplicate stuff on the cheap. I want it done more and more for these new technologies.

Distributed technology, distributed power; the largest computer in the world, what is it? The largest computer in the world is hostile botnets. Think about it. Now it’s available to the bad guys, for how much money? That costs them free, doesn’t it? They rely upon ignorance and apathy on the part of users in order to become part of them. So the same technology that was relegated only to nation states 20-30 years ago is now currently part of the bad guys’ arsenal. How do we defend against this? I can’t get anybody in Washington to even acknowledge it’s a problem, because they don’t understand the fundamental nature of multithreading, multitasking, and all this MPU kind of things that are going on. Some low level guys get it, but getting anything up in the hierarchy is not happening.

EC2 – I’m a huge fan of EC2, I think Amazon is doing an amazing job, cloud stuff notwithstanding; I love total flexibility of the way that network works. Will Amazon sell massive amounts of EC2 space to Al Qaeda? Of course they will, because Al Qaeda is going to use anonymity, they’re going to use bad guy stuff, and nobody is going to know there’s Al Qaeda inside of it. The same technology that is available to us is still available to the bad guys, and we’re not considering this in the way that they’re attacking.
Four years ago I was looking for a present for my 7- or 8-year-old nephew. They had this intelligent nano-tech thing that was on a macro scale, kind of like big Legos, and they had automatic architecture built into it. It was absolutely awesome: unpredictable behavior. It was tremendous. As we move forward in this world of nano-tech, are the bad guys going to have access to nano? “Toys R Us”, yes, the bad guys are only good at “Toys R Us”.
This technology is going to be awesome. We can do some tremendously great things with it. Turn on your evil hat, please. What is so great in this technology that we might be able to have defensive posture built into it? Or is it kept so far from us that we’re completely screwed? I don’t know the answer, but I do know that it’s going to be weaponized. One way or another it’s going to be weaponized, and we need to start thinking of what the defenses are going to be. And the only way to do that is to figure out how to turn them into weapons first. And it has to be done in an open source environment, not the classified DOD or MI6 or GCHQ. It’s got to be done open source so we can have real discussion. And maybe there’s a way to build some defenses? I don’t know the answer. But I do have a question and I know the frustration I’ve had for 30 years, getting to where we are.

Swarming and self-organization. Is everybody familiar with John von Neumann’s Automaton theory? Quick brief comments, simple rule set: if I am here, in one second move here, next second, move here – that’s the entire rule set. Now you take 20,000 things pulled together with the same rule set, what happens? Is it predictable? No, unpredictable chaos.
Now, has anybody read Michael Crichton’s book Prey? If you haven’t read it, read it, because it takes this concept very well. It’s a little science fiction-ish, it looks into the future. What happens when we introduce chaos into the systems? Can we actually do it? And using exceedingly simple rule sets, which means one or two lines of code, I can introduce chaos. This is an emerging theory. What happens if I introduce that instead of trying to steal your data? The spam message is hostile and it has an Automaton chaos trigger. What happens? I don’t know the answer because it’s unpredictable – I know it’s not good. How many people are really studying this? Unfortunately, not enough, because it is in the realm of mathematics, it’s in the realm of unpredictability, chaos theory – they all get into this mysterious area that you don’t understand. But we really need to start understanding that there is going to be a problem.
As we approach the singularity more and more, as the technology gets more and more powerful, introducing chaos will be done by accident. How do we know this? Windows 2000 never crashed. Windows 2000 was a fundamental achievement. It was 64 million lines of code, and we, the world, were the beta testers. I remember Microsoft tested it for 10,000 hours. Let me do the math: 50 million users, 1 week, 2 billion hours, and suddenly we’re the beta testers. The same concept is here. Can we pre-beta-test with modeling ahead of time?
Does anybody remember when we actually had real, honest to God, computer security? Is anybody old enough to remember? The only security system in the world that was ever rated A1 was in the early 80s and was called something like “secure operating mainframe protocol”, I don’t remember exactly. The way that security used to be done before it got fizzled down to the world that we’re in of self-organization and chaos in complex systems – was mathematical formalization. There were really massive formulas you could work out proofs, mathematical proofs that all of this stuff was actually going to be secure and was actually going to work. We don’t do that anymore because things had gotten so complex. As complexity increases, security goes down, and chaos is automatically triggered into these systems. We’ve got to really start investigating this stuff.

Bio-chem, same concept; my first experiment with my chemistry set when I was 5 was the first thing I built – hydrogen sulfide! It was a bomb – of course. And then my mom was really mad at me. And we’ve all done it. Now, what are we able to do today? Labs have gotten really sophisticated. We have distributed technology. I’m nowhere near this stuff at all, but I do know that we need to be addressing defensive postures against some of the capabilities that are built in the open source arena.
Same thing with the DNA. Chupacabra down in Puerto Rico was obviously made by the NSA as an experiment with alien breeding. When this technology hits open source and becomes a 50-dollar item, what’s going to happen? I don’t know the answer, but I hopefully will see. I don’t want to die by that. It’s probably not going to be pleasant, as we’re seeing more and more of this kind of magic occurring.
Batteries: finally batteries are getting really cool. We can have distributed non-grid, off-the-grid-style power. That’s awesome for us. What about bad guys? When the bad guys get off the grid, looks like they’re going to make our job one hell of a lot harder, because they’re going to have access to the same off-the-grid technologies that we do. It makes building stuff in caves a hell of a lot easier. It’s a fundamental change in how we’re going to have to look at defensive postures by using technologies that the bad guys are going to have access to as well.

All sorts of possible answers, and I’m happy to make this slide (see right-hand image) available to anybody. Don’t forget: we, the US, are only 4% of the population. Our laws are like a town sheriff in the South who wants to harass speeders from the North. We are a local board when it comes to legality globally. It’s never going to work at all.
Classifying – that’s always worked in the past too, right? Maybe, some of you guys have actually had technologies picked up by DOD or those guys. I think we need to be completely open source with this entire arena.
Do we turn ourselves into a police state? Again, we’re only 4% of the planet. Are the bad guys going to have access to this stuff? This is the fundamental issue that we have totally ignored until China really came along.
And then coming down scared shitless… Carrington Effect. If you don’t know the Carrington Effect, please google it. What happens if coronal mass ejection actually hits the Earth? All studies on this are absolutely correct: low probability, high impact, the entire planet shuts down for 18 months. For 18 months the planet is off. How do we defend against it? Yes, we can. The defense against it is to have a graceful degradation model, because we have a 7-hour warning. If the CME and the angle of the dangle is correct, turn the planet off. Unload every transformer in the world is the only protection against this. Can it be done? Yes. Will it be done? No, because we’re going to get politicians involved to “help” us.
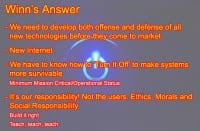
So, my answers: develop offense and defense at the same time, get rid of the existing internet IPv4 and IPv6, build something else. Learn how to turn shit off and still have capability, some level of capability as you turn your shit off. And keep in mind: we’re the ones who fucked this up. We gave the users a hell of a lot more. Would we ever give a user a 777 cockpit to drive down the highway? We’re giving them complex stuff to screw up. We keep blaming the users, but it’s our fault. We’re giving it to them, and it’s our fault for never looking into the bad side of technology before we deploy it, otherwise DoS would never have taken off.
Thank you very much!




























