
Accuvant LABS’ Senior Security Consultant Martin Bos and the Company’s Principal Security Assessor Eric Milam spotlight the issues related to spear phishing from the pentester’s perspective during their session at Hack3rCon event.
Martin Bos: Hi everybody! We’re here from Accuvant LABS; we’re talking about some advanced phishing tactics. The main basis of our talk is, basically, why user awareness is not working.

So, this is the obligatory table of contents (see left-hand image). Basically, we’re talking about what spear phishing is. Just a disclaimer: we actually wrote this talk for some more corporate type conferences, and we’re just recycling it. We like it, we hope you all do, too; but some of the stuff is a little bit elementary in the beginning, because there were some more corporate type people we were talking to, so bear that in mind.
We’re going to talk about how people are spear phishing us, what we can do about it, and why the current methods are not working. Who here has been phished? Who here is related to the Prince of Nigeria? Awesome, so we all know what a phishing email is.

So, my name is Martin, I’m Senior Security Consultant, also work on the Backtrack Linux project, and I’m a co-founder of a little conference like this one called Derbycon in Louisville, Kentucky.
Eric Milam: And I’m Eric Milam, I’m Principal Security Assessor at Accuvant, also participate in the Ettercap project as well as a number of other initiatives.

Martin Bos: Alright, just in case anybody doesn’t know – what is spear phishing? What’s the difference between phishing and spear phishing? Phishing is when you get an email like, you know, that you’re related to the Prince of Nigeria; everybody’s got one of those.
Spear phishing is, basically, when we as attackers – and when I say “We as attackers,” I mean pentesters, not attackers for real – are trying to target a specific organization, group of people, business unit, and sometimes an individual, although I’ve got really big qualms about how good spear phishing one person works. However, it’s happened. So, when we’re talking about spear phishing, we’re talking about targeting an organization.

Here are some victims of spear phishing attacks (see image). I don’t know if anybody reads the news, but, apparently, the White House was the victim of a phishing attack, and this is to let you know that this type of attack is alive and well. Obviously, we don’t really know what happened, but somebody in the White House clicked an email that they weren’t supposed to. And that just goes to show you that, I bet you, the people at the White House have been through extensive security training. I’m sure they’ve sat through all kinds of “Don’t click this” seminars by Boris, and it’s clearly not working, right?
Some other big victims of these attacks are RSA, Epsilon, another big one was these Nitro spear phishing attacks that targeted 50 chemical and defense companies; Mitsubishi Heavy Industries, who is a defense contractor, and there’re hundreds more pretty much all over the place. I would almost venture to say that this is one of the most popular externally facing attacks on the Internet today.

Alright, this is basically my validation for why we pentest (see left-hand image). I actually got into several arguments at the last conference that we were at about people that said that pentesting was pointless and that there was no reason to do it. If anybody knows me, I like to argue, but if I get up and leave, I’m really mad. Well, I got up and left this dude’s conversation.
We do these spear phishing attacks against ourselves so that we can test our clients’ security systems. We’re not just testing their users, we don’t just want to make the users look stupid. What we’re doing is we’re testing all of their controls that are in place to prevent this type of thing: you know, egress filtering, network segmentation, incident response – I mean, there’s a whole chain of things that need to be tested by a successful spear phishing attack.
Embarrassing users is not the goal, and showing users that they’ll click on anything is not the goal. Obviously, there is a little subsection for user awareness, I’m not against it, but I’m just saying that I don’t think we need to put all our eggs in the user awareness basket.
Eric Milam: And if you guys think about someone clicking a link – until the shell gets out there’re several layers of defense, and that’s what we’ll talk about as well.

Martin Bos: Here are our obligatory statistics (see image); every presentation has to have some statistics. Like I said, these are more for the corporate type users we were talking to, but this was a survey done by Proofpoint at the last big Microsoft conference, and they interviewed about 350 organizations. 51% of them believed that they had fallen victim to a spear phishing attack, and more than 1/3 of those 51% believed that their spear phishing attack had resulted in some type of compromise, malware, login credentials, whatever. So, that’s quite a bit.
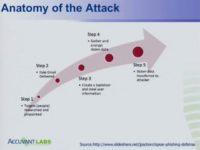
We do a lot of target research, so this is basically the anatomy of how an email attack works (see left-hand image). This is the difference between a spear phishing attack and a regular phishing attack. A phishing attack doesn’t require any research; we just send the email out to as many email addresses as we got off that Iranian web board that we could find.
So, we’re really invested in step 1: we spend a lot of time researching our targets, and we’ll show you one of the main tools that we use. We like to not only find email addresses for a specific company that we’re targeting, but we like to find out where they live, which people are working in the same office, and the most important thing that we like to find out is what position those people actually have, because we like to filter out people from the IT department and people that might otherwise find a phishing email fishy and report it.
The people that we like to target the best are HR departments, because, you know, their entire job is to sit at their desk and open up PDFs and macro-enabled Word documents all day long – that’s their job. See, so you can’t fault those users for opening suspicious documents all day long.
Eric Milam: That research also gives us an ability to find out what they are running in their environment so we can build our payloads accordingly. If it tells us on LinkedIn job board what AV they’re running, or they are looking for something specifically, like McAfee implementation or Symantec or whatever it is – it gives us a better idea, based on what we’ve done in the past, with our payloads and what we might need to incorporate and implement.
Martin Bos: Like Eric was saying, we use the email addresses to search message boards. We take ‘company’.com and do some Google search to find the Juniper forums, and we find some guy that’s like: “Hey, I’m trying to get my Juniper firewall working, and I’m having trouble with egress filtering these three ports, and here’s the config.” We love it when people do that, and we especially love it when you post for a job on LinkedIn that says: “We need a Symantec expert,” then, of course, they have Symantec AV. That type of stuff helps. So, doing your research, just like in every situation, really helps on executing a proper spear phishing attack.

Eric Milam: As Martin started talking about email harvesting, we gather email addresses for the target; there’s tools there at the bottom (see image), we’re going to go through one for you. The good thing about the tool that we’re going to show you is that it actually shows you the department the person works in, where they are physically located, what city/state, what their job title is. So, it’s really easy to say: “Alright, this guy is in network architecture, this guy has Security in his title, so we’re going to go and remove this person, because that’s someone that’s going to raise a red flag right away and maybe do some DNS blackholing to get our site, so that their internal sites can’t get to it.”
So, we use Goog-Mail, Goohost, The Harvester, custom scripts, again, LinkedIn, but the one that we like the best is Jigsaw. How many people have heard of Jigsaw, just the website Jigsaw? The cool thing about the website Jigsaw is that it’s basically from salesforce.com, it’s for people to hand out business cards. If you hand out your business card, then they take that business card and they upload it onto this website, so that’s how we know what names and titles of these people are.
If you pay for this service, you can also get the phone numbers and actual emails out. But most of us know that most email addresses are going to be first initial and last name, or first name dot last name, and even if they’re not I think you can make up your own: if you’re like oak@google.com, there are still probably aliases on the back side of the exchange server that are created with first initial and last name, they’ll still point to that email address. We’re going to go ahead and demo for you the jigsaw scripts real quick. This was written by a guy that actually works for us. Jigsaw recently implemented cookies, so we’re working on getting the code updated to get it working.
Martin Bos: Basically, what we’re doing here is we’re going to look for a company. The first thing you want to do is do an ‘-s’ and search for the company. We’re going to pick on Humana – sorry if anybody works there. Just a disclaimer: we didn’t send Humana any emails; we didn’t do anything to their organization, this is all passive.
And so, basically what it will do is it will search for Humana. Jigsaw operates by ID, so this is everything that it found for Humana (see image), but you can see at the top: it gives us the ID for Humana Inc., which is the real health care place, and it’s given us 1871 employees. And that’s quite a bit more than any of these other old school email harvesting scripts usually ever find.
So, you just give it an ID number, and then you just give it an ‘-r’, and you give it a report name, and it writes it out to a CSV file. The only other thing that it asks you is that if it finds multiple domains that are linked to Humana, you just have to choose the domain, so we’re just going to do ‘Humana’.
Eric Milam: When a company buys another company and still got the domain, what this will do is that when it builds the actual emails for you in a CSV, this is the domain that will be used for the email examples.
Martin Bos: And this takes a while, so we’ve actually got it already listed out here: so, basically, you just open it up.
 The company’s CSV stats for the test
The company’s CSV stats for the testEric Milam: So, as we were saying, you can see we’ve got here first name, last name, we’ve got the full name, we’ve got the department they work in, and you can easily set up a filter. Like we said, we filtered out the IT, there’s the position (see top left-hand image). It creates 2 email aliases for you automatically based on the domain that you provided in that first step, just first initial plus last name, and first name dot last name; city and state where they’re actually located, so if you want to target a specific region, a specific department – you have all those names in there.
Martin Bos: And what we like to do is go over here to department, for example, and we can grab all the IT and IS people, and we can go ahead and filter them out of there (bottom left-hand image). Of course, we would leave in the director though, because we know he can click our link and that will be the most embarrassing thing. So, that’s just one of the tools we use for email harvesting, but you can see that gave us 1800 targets just to begin with, by just a couple of commands.
Eric Milam: Here’s the cool thing about that list. So, you’ve got a list of 1800 emails; we know that probably not all of them are right. Here’s something that we like to do that not a lot of other people do – normally, they’ll just send out an email to those 1800 contacts. What I like to do is I like to use my fake Gmail account Jim Smith, and I just create a fake email that says: “Sylvia’s 60th Birthday Party,” Sylvia’s my Mom’s name, and I just basically say: “Howdy friends & family,” make something else up. I send it out to those 1800 (see screenshot).
I like to do this about a week ahead of time, because what happens is, first of all, most of the time it will filter out what email addresses are invalid. We’ve been told plenty of times by plenty of companies that if you send it to an invalid email address, it will just drop it. That’s 99.9% of the time not the case. It doesn’t matter if they’ve configured it or work with Microsoft, whatever – we’re still getting bounce back, so we’re able to filter that out.
Another cool thing that we get out of this is, especially during summer holidays, we get kickback saying: “Hey, I’m out of the office, but you can talk to so and so.” And then we can look up and say: “Oh, so and so is not on our list,” so we add them to our list. So, we start getting more people: we get the title of the people, we get phone numbers for the people, we get all kinds of information.
And one of the cool things we got recently is that there was a legal disclaimer in the footer for their emails. So, all these things help us build our email that we’re going to send out. It builds that trust level: if the language looks the same, if it’s laid out the same; we see how their emails are laid out, we see how their signatures are laid out; whether or not the email includes an image, etc. So, we can mimic that as closely as we can, because we want to exploit the trust that exists there.

Martin Bos: The next thing we do is we have to create a scenario. How are we going to get these people to click on the link? So, the first thing that we like to do is register a real domain. You know, back in the day there were all these email phishing scripts that you could use from the command line, but email filters and fancy appliances have way surpassed that, they don’t accept emails from root anymore.
So, what we like to do is register a real domain with GoDaddy, because they’re so cool – they give you one free email address with every domain registration. So, what we found in analyzing most of those email appliances is that the one major thing that they drop emails on is reverse DNS. So, if there’s no reverse DNS set up, they will drop your email automatically. So, what we like to do is register a real domain and we get a real GoDaddy email address with reverse DNS, and it’s legit. We’ll show a little bit more how we do that in a second.
The next thing we do is create a scenario: what are we going to use the phishing for? The one that we always try to use on pentest is targeting open enrollment. 401k, health benefits – all that kind of stuff never gets approved, not one time have we ever had that scenario get approved, because, apparently, messing with people’s health benefits is not cool.
Years ago we used to do a work from home one, which was pretty good: we would send out an email that said: “We’re only selecting 50 people for a pilot program to work from home on Fridays. Just fill out this survey, do not forward this to any of your friends,” you know, all that kind of stuff. That would work really good for a while, but work from home started getting flagged by email servers, because, I guess, there was another phish like that on the Internet.
Another one that gets flagged all the time is the OWA upgrade. The only reason we use this is that we have some clients that are not security mature enough for some of the email attacks that we use, so they’ve asked for something a little bit dumb down to give their users a chance.
A few years ago there was a giant OWA upgrade phish across the Internet, so we’ve actually copied that, and we use that sometimes when companies are just starting out, because, like I said, our goal is not to embarrass their users; our goal is just to conduct a successful phish so that everyone can see what happens. So, we have an OWA one; it’s got misspellings on the website and everything in order to sort of give the users a chance.
But our absolute favorite one is the security report, and that’s what we’re going to show everybody today; cat’s going to be out of the bag, I guess, but it doesn’t matter. We use the security report because it works everywhere. Every single organization has security, and every single organization always has some kind of random people walking around that you’re not really sure what they’re doing, especially in IT: we’ve always got some consultants in there or some people doing risk assessment or something.
And so, what we like to say is: “Hey, this company just had a security audit,” and people would be like: “Oh, that was those weird-looking guys that were walking around last week.” And then we also like to throw in there: “We’ll show you the whole email,” but we also like to throw in there that some people got in trouble, some people weren’t following security policies. That peaks people’s interest; they’re like: “Oh my gosh, I got a ‘C’, who got in trouble?”
Eric Milam: A lot of the time they think it’s them: “I got to look and see if it was me, maybe I got tricked,” and they are basically getting tricked this way.

Martin Bos: Alright, these are the five steps that I like to follow when I’m creating the email (see image). The subject is the most important part, the subject line that comes up in your email client, because if that’s not good, then nobody’s going to open the email. It’s got to be easy to read; you can’t write these things with a PhD, because it won’t be realistic. You have to write in normal people corporate type language – obviously, depending on the organization that you’re going to be at.
If you’re targeting some farm machinery organization in Kentucky, you might want to throw in a couple of y’all-s in the email, and I’m from Kentucky, so I’m not making fun of us. But I’m just saying you want to make it easy to read and conducive to the people that you’re sending it to. And along those lines it should be legit, so there shouldn’t be any misspellings and there shouldn’t be any grammar issues. I mean, I don’t know about you, but when I send an email out to my entire company, I proofread it 5 or 6 times, because I don’t want to look like an idiot. And so I spend a lot of time making sure that my email is perfect.
Give the users a reason to click: obviously, you have to get them to execute some kind of action; the days of just opening an email and being infected with the black plague are over. People have to click on something, they have to accept something, they have to run something – they have to do something, so you have to give them a reason to click.
And, I already touched on that, but make it fit the organization. The example that I use is if we know the organization has 85% part-time employees, we would not send them a phishing email about open enrollment. Why? Part-time employees don’t have insurance, so it wouldn’t make sense.
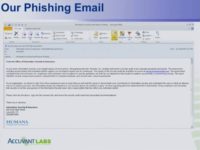
Eric Milam: So, here’s our standard phishing email (see image). Basically, what we do is we always end up sending that from information security, which is infosec@ – in this case it’s Humana-portal.com. So, what we do is when we set up the domain, it’s usually ‘(company name)-portal.com‘, and when we set up our server, we just add ‘secure.’, whatever, as a subdomain. I put everybody in the Bcc line.
So, here is our basic layout. What you’ve got here at the bottom – I spent about 5 seconds googling it – is the Humana logo, I put that in there. We’ve got the actual address and phone number. What we were talking about earlier, when I sent out the initial email, the Jim Smith email, sometimes I’ll actually get the phone number for their internal help desk – that’s good to put in there: if they start calling their help desk, everything looks legitimate. We’ve got the bold in the right place.
There’s a link in the email; one of the things that users always do is hover over to the link to see if it actually goes where it says it’s going to go. We always make sure it does; that’s a level of trust there. When they hover over there, it goes there, so it’s not any type of obfuscation.
But, basically, what it says is: “As you know, security is an integral part of our aspect; and recognizing that, we performed an audit; based on that, we were able to see that some employees and contractors didn’t adhere to our policies, so the auditors were successful in compromising systems and people, and all kinds of stuff.”
What we end up telling them is: “Hey, it’s your duty as a member of our company or organization to go out, sign in to this secure website, download it and read it. It’s up to you guys to help us protect ourselves from spear phishing attacks.” So, farther down in the original email it actually has that legal footer down there. All these little things help build trust when someone actually looks at it. The email looks professional, it’s spaced correctly, we’ve got the right signature line – everything looks good, everything looks legit.

Martin Bos: The next thing you got to do is choose the attack vector (see image). And this goes back to our research: what type of AV they are using, whether we are targeting the HR department, particular favorite.
The couple of things that we use are, obviously, infected PDFs, Adobe’s got a 0day every week, so you’ve got a pretty good chance of one of those working. VB macros in Word and Excel documents – let me just go back by saying that none of this stuff is new and none of this stuff is revolutionary. Unfortunately, this stuff is still working, that’s the problem. So, Word and Excel documents with macros – that still works all the time. The main things we like to use are from SET, from Dave Kennedy’s toolset, so we like to use the credential harvesting, we like to throw a nice malicious .exe in there or two, you never know.
And, of course, we like to use the Java applet; we have a special Java applet from Dave that he gave us that we can’t give anyone, but we can show you. So, what we like to do is we like to get a combination of these things just in case one doesn’t work, we like to have backup. So, what we’re going to do for this demo is we’re going to do some credential harvesting, we’ve got a malicious .exe in there, and we’re going to do the Java applet, which, once again, I’m sure everybody’s seen, but we’re going to show you how you can make a legit one.
Eric Milam: One other thing we should understand is that spear phishing attacks are the most politically charged tests that you’ll ever do in your organization. So, if you are a pentester, you make sure that you get as far up the tree as you can; you talk to your customer and let them know: hey, human nature is fickle, you might not react the same way as the next person. I mean, we’ve been threatened to be sued, we’ve had our websites pulled down, we’ve had everything from people getting upset for being phished or falling for it.
So, if you’re wanting to do this within your organization, I’ll say it again, do your research, get recommendations as high up the tree as you can. Our goal is not to get anybody fired or anything like that, but I’m sure we’ve caused plenty of shitstorms by doing this, even though we’re doing legitimately everything they’ve asked us to do and not going outside the bounds.
QUESTION: How severe is your attack and infection, and do you put actual names of people who got tricked in your report?
Martin Bos: Usually we don’t want to harp on people just for visiting the website. Now, once they click on the link, obviously some kind of code is going to run, and then one of the first things we do is grab the system. But no, we don’t call out anybody specifically in the report at all.
Eric Milam: We specifically stay away from that, because we don’t want anybody to get in trouble. We can tell them we’ve gotten so many people that have logged in and we’ve got credentials and we know they’re valid. But we never give out their username, even in our reports we don’t give out their username.
So, basically, here’s the website (see left-hand image). We’ve got the logo that says: “Secure Portal” because it says it is; over there at the top it says “secure” as well. There’s no lock there, but that’s cool because we put the lock right there by the employee login, so we know it’s legit, we know it’s safe. We’ve just got a standard login with a Login button; we’ve got a nice little “Trouble Logging In?” – Martin will show you what that does.
We’ve got a Security Notice and it’s red, so it’s important; it basically just says: “Information contained within is confidential, and it is intellectual property of Humana Inc. System is actively monitored and access records are collected” – and they are, only by us, not them. And then it says: “Use of the information and applications contained in the system, introduction of malicious code, temporary interference and disruption of the service is prohibited.” So, we take care of all that for them.
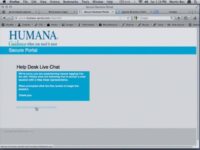
Martin Bos: So, we got this, and obviously this logs any user credentials that come in. The one kind of thing we like to do is we’ve got a little “Trouble Logging In?” button, because what we do is we actively monitor the GoDaddy account. So, after we send out the phishing emails we get a lot of people that actually email back and say: “Hey, I can’t log in to the site, what’s going on? There’s something wrong.” So, what we do is we have this help desk page (see image).
Eric Milam: It basically just says: “Hey, we’re sorry you’re experiencing some problems logging in. Why don’t you click this link, click the RUN button when it comes up, it’ll install our little help desk application, and I can chat with you live.”
Martin Bos: So, you see down there at the bottom we got our helpdesk.exe. I know none of you would ever do that, but it works. Think about all the other people in your office: it would be like “Oh, game on.” So, that’s our site. The other cool thing that you can do with GoDaddy is…
Eric Milam: So, here’s one of our other favorite things. We like to get as malicious as possible. So, you can change the WhoIs data, right? The reason you want to do that is that there are some smart people who will go out and check the WhoIs data from the Internet. So, all you’ve got to do is log in to your GoDaddy account, type in the organization name (“Humana” in this case), domain admins, it has the address – so basically I just looked up there WhoIs information and copied it directly to ours. And all I had to do is check this box that said: “Yeah, I certified that I’m with your organization, no problem.” Click OK – within 5 seconds ours matches theirs (see right-hand image).
The main thing that might be different is if they’re not registered with GoDaddy, that part will be different. So, what we do a lot of times, too, is we go and actually register the site where they registered their site, and then it looks almost 100% legit. So, we got ours that says: “Humana portal GoDaddy.”
Martin Bos: So, you can see up here I did a WhoIs on our Humana-portal.com site, and down there we’re legit.
Eric Milam: The only thing I ever changed in the email is that a lot of the time they say: “domain admin” or “admin”, or whatever; I just add an “s” on the end, so “domain admins”. GoDaddy rocks. Yes, we love GoDaddy.

Martin Bos: Alright, next thing you’ve got to do is, obviously, choose the payload (see image). I know this is more of my corporate slot. Obviously, we like to use Metasploit, because everything’s built in, the listeners are there, it’s easy peasy, I’m not trying to reinvent the wheel. The main things that we worry about are reverse connections. So, when you’re reverse-connecting outside of an organization, TCP is just really difficult. Organizations have egress filtering, IBS, IPS, and all kinds of stuff. So, TCP barely ever works anymore.
We like to look at HTTP and HTTPS, because those are always allowed outside of an organization. However, nowadays they’re getting a little bit more crafty, they’re doing stuff like binary packing inspection and that kind of thing over SSL; not very often, but sometimes they are.
So, generally we stick with HTTP and HTTPS, but recently we did a pentest for an organization that we knew had outbound egress filtering. We knew that their Adium 443 were being monitored with binary packing inspection, so we didn’t know how we were going to get on to the network. There is a newer payload in Metasploit called Reverse All-Port TCP. You basically give it a beginning port, and it tries every single one to get out of the network until it finds one. The difficult part about this is that you have to set up your reverse listener with IPtable rules so it forwards every single port to the one port that your Meterpreter shell is listening on.
That was the trick that we had to figure out, but we did have this working and we got out on port, like, 47000, something really obscure and ridiculous that they just missed somehow or whatever. But it worked. We got shells, that’s all that mattered.
And the last thing is obviously defeating AV. Everybody knows Metasploit gets wiped off the board by almost every AV out there. It does come with some encoders, they do help, but they’re not for AV obfuscation. So, then we run into stuff like custom packers, doing some binary obfuscation, and digitally signed binaries and applets.
We like to digitally sign all our stuff, because it’s so easy, Dave taught us how to do that.
Eric Milam: For $199 at GoDaddy you can get a certificate to sign all your stuff.
Martin Bos: Another thing that we like to use, and this is super simple – we got a little bit, about 30 lines of bash right here, where we basically create an .exe with Metasploit, we do some set on some of the bad characters, we do some bite randomization in here, and then we come down and we just recompile it back into a C binary, and it comes out. We just call it a ‘backdoor .exe’ (see left-hand image). Just those little 30 lines of bash will make it around a whole bunch of AVs.
I’m not going to pick on Accuvant one, but you will see here in the demo, we got my Accuvant corporate Windows 7 VM here; we’re running the latest and the greatest: we got McAfee, and it’s ok, we’re good to go, we’re fully patched. Those 30 lines of bash – and the only AV that I’ve not been able to get around is that pesky Microsoft Security Essentials; we have some other ways to get around that, but other than that, that little bit of code works. It’s probably not going to work tomorrow after somebody sees this, but whatever.

And then, obviously, the end goal of the social engineering, not the basis of this talk, but I have to hit on that, is the post exploitation (see image). What are you going to do once you get the shell? It’s the most important part, you know. Getting the shell is not always that difficult, but what are you going to do with it? How are you going to keep it open? How are you going to get back in? And, most importantly, what data are you after?
Because we need to find data on our pentest, we need to find what the company uses to make money, because that’s what’s going to have impact on the CEO level people when you deliver your report. I don’t know a lot of CSOs that really understand: I compromised your domain controller and now I’m king of the kingdom. Well, that doesn’t really mean a whole lot, but if you get in there and you’re like: “Hey man, I broke into your Wendy’s and I accessed your secret sauce formula in the database and I’m selling it on the Chinese black market” – that creates an impact, right? What does the company use to make money?
Now we’ll try to demo this and put it all together. The first thing we’re going to do is we’re going to log in to our portal.
Eric Milam: One other thing that we like to do to create trust on the website is make it point out to a small piece, but it sometimes makes a difference. How many people know about favicons for websites? So, just going out and taking one of those logos and creating a favicon and making sure that it shows up – that’s always a good thing, just another layer of trust. Like we said, nothing revolutionary, but when you put all these little things together, it just keeps building on to the trust for you.
Martin Bos: And this is just a plain old Metasploit RC file, nothing revolutionary here, but I just want to show you all. One feature in Metasploit that we use on every single pentest is the spool feature which records every single thing that you do in the console; if you’re not using that and you’re on a pentest, you’re doing it wrong, because I can’t tell you how many times we had to go back and work through our spool file and prove to somebody that we didn’t tip over a domain – it wasn’t us, basically; or it was us. I always like to keep an accurate record of what we did.
Martin Bos: So, then what we do is we log in to our free GoDaddy email account, infosec@humana-portal.com. And what we do is we just save it in templates, so we’re good to go, and then we can blast it out to whoever we want. Here’s our email (see image). Like Eric was showing, you can see at the bottom we got the actual Humana footer down there, so it’s legit, right? We call it “Information Security Audit Report Findings,” the whole nine yards, the priority, of course, is high. And we send that off.
Eric Milam: Normally, it’s limited by 100 people in the Bcc, so you can see if we have 1800 people we’re going to send it out 18 times, it’s another reason why we create the template. It’ll pop up every once in a while and ask you to do the captcha to make sure you’re not a bot sending out these emails. But you can send out 10 within 10 minutes.
Martin Bos: Alright, as I said, I’m using my corporate VM, so I’m picking on my own company, nobody else’s. Dave’s Java applet, I’ll show you, does this really cool thing, but it sucks for demos. So, let’s make sure our listener’s up, and once again, this isn’t revolutionary, everybody’s seen Dave do this Java applet in the SET. I just installed the newest version of Java this morning.
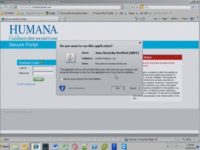
Eric Milam: The note says it is safe. Right there they see in bold: it’s safe, I’m at the Humana site, it’s secure, I see the lock, I see the security notice (see left-hand image). And one thing you can’t see is this: “Always trust content from this publisher”.
Martin Bos: Yeah, it doesn’t show right up in IE9, this is IE9, by the way; so it doesn’t show up, but Dave has it, so it autochecks this “Always trust content from publisher” box, so I’ve got to go there and delete this certificate all the time, because I forget. Once again, this is not new, this is not revolutionary, it’s been said forever, but what we want to show here is that Dave was able to go out and register a company and, basically, get a code signing certificate for this applet, all for under $1000, really cheap, and anybody can do this.
And you can basically call the company whenever you want, it’s safe, and this is the kind of thing that we like to do at Accuvant: we like to code sign our binaries, we like to do this type of thing, and the reason is that it is so cheap to do, and as soon as people see that it’s verified by a publisher, they’re good to go. And so, once again, this is pretty normal, but we always try to uncheck this. I don’t know why it doesn’t show up in IE9, it’s kind of annoying.
Eric Milam: You can change that name to whatever you want: if you’re targeting Humana, you can make it Humana Inc. or whatever. Basically, what we did is we set up reverse DNS so that it says Humana.com. So, you notice here we’ve got our standard shell, nothing new here.
Martin Bos: We actually customized our website a little bit, because in the beginning it didn’t do quite what we wanted, but now Dave’s does, so we’ll probably be switching this up a little bit. But the other two things that it does here is, obviously, this logs to a file just like the credential harvester, and then, once again, if you have trouble logging in, you can go down here and you can run the helpdesk.exe.
Eric Milam: Also, when you can’t login, all it does is go to an Excessive Requests page (see image below), and that’s why we get a lot of emails back from the users that basically just say: “Hey, there’s excessive requests, the server’s down, I will try again later.” And that’s another reason why they have trouble logging in: I’m using web credentials I’m not supposed to use, that type of stuff. So, that’s normally something they go after as well.
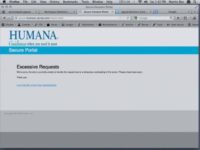
Martin Bos: Yes, we like this better than the 404 page. Excessive Requests, it still looks the same, it’s not an error message, really, it’s like a custom page. And it makes sense, because everybody in the entire company just got this email and they’re all trying to download the PDF at the same time, so this looks legit, right?
Real quick, if anybody’s interested in that Jigsaw script, it is in Backtrack, but it’s also up here at https://github.com/pentestgeek/jigsaw, if you want to download that and utilize it. If you’re interested in the real Jigsaw website, it’s right here. You can actually just sign up for free and browse the site. The script takes advantage of a flaw in their API, but you can just create an account, log in and get that information that way.

Martin Bos: Like in every good presentation, what we really wanted to talk about here is why user awareness isn’t working. Once again, this was more on the corporate side, but things to look for in an email: do you know the sender? Is there some malicious attachment to it? Can the information in the email be used to attack you or your company? This sounds elementary, but you’ve got to really read an email if you don’t know who it’s from, especially if it asks you to take some kind of action.
I’ll just give a quick example: at our work they contracted some third-party company just to do like a compensation survey kind of thing. I mean, it’s pretty standard in the industry: “Do you think you’re being compensated correctly?” But the company that was doing this didn’t consider that they were sending it to a security company, so everybody in our group got this email the other morning that was like: “Log on and fill out this survey,” and all of a sudden the emails start flying back and forth, we’re submitting it to our IT: “Why didn’t your firewall catch this? We’ve never fallen for this,” you know, on and on and on. And it was legit, it was a totally legit email, but the thing was they didn’t validate it. And so everybody in our group was like: “There’s no way we’re filling it out,” and so even after they said it was legit, nobody still filled it out, because it didn’t come from our company.
Eric Milam: I filled it out because I told them I wanted extra 100K a year.
Martin Bos: Anyway, you know, is the link suspicious or raising any flags? We showed you we like to use the actual links, we don’t like to obfuscate our links, so a lot of times people have been taught to hover their mouse over a link, and if it tells you to go somewhere else, then it’s not legit. But even if the entire URL is not legit, as long as the link is going to where it says it’s going to go, you see that match in your mind, and you almost always go there. I know nobody here would, but anybody else might do it.
And, obviously, IT or Security would never ask for your password. Once again, a lot of this stuff sounds kind of elementary, but people are falling for this stuff every day.
Eric Milam: We wouldn’t be up here talking about it if it weren’t happening all the time.
Martin Bos: I hate to admit this, but one of the main ways that you can limit exposure to this stuff is patch your motherf**king systems. These are some of the most attacked things, everybody’s looking for an Adobe 0day, Flash, Java, Microsoft – I mean, all these things; these are the most widely attacked systems. So, one of the first things you can do is not buy some fancy piece of email equipment – work on your patching process. Is a 30-day cycle enough? Can we afford 30 days to patch Microsoft? I mean, there are things that we can do internally in our organizations that are already in place to prevent some of this stuff.

Eric Milam: Like Martin was talking about limiting exposure: what do we want to do? One of the main things that we see when we’re at an organization is that their network segmentation is horrible. If I get on a laptop or desktop in California, I can usually see the entire organization in China, India, whatever. So, you want to think about network segmentation. And these are all the steps you want to think about: from the time that the user clicks the link until that shell gets out, like Martin’s did, to an attacking server. There’s all kinds of steps in between.
Did AV pick it up? If it didn’t, is there a host-based IPS to pick it up? The next step should be: is there IPS/IDS in place? Did that pick it up? If it gets past that, is there any type of egress filtering out there? Did that pick it up: yes or no? What exactly is out there? Is there advanced malware detection, did that pick it up? So, there’s all these steps that happen, even if the user falls for it, why don’t we say that user awareness is definitely important? We’re not saying: “Don’t educate the users,” what we’re saying is: “You guys as defenders of the network, or other individuals as defenders of the network – it’s not about testing the users. You want to test that entire path from the point that the user clicks it.”
Because if we’ve got 2000 individuals, you know at least one person is going to click it. The good thing about that is you can test that all the way through: what’s working, what’s not working, what caught it, what didn’t catch it, am I spending the money in the right places?
If you don’t have these types of items, things like, we’ll say, credential harvesting – there’s two factor authentication on OWA. Who actually has OWA exposed externally without two factor authentication? Does anybody want to raise their hand and admit it? So, basically, if you get that, and once you’ve got that, you log in to your OWA, then you do a search for the logins, and now you can just widen your spear phishing attack to everybody in the company. And you can send it internally now, from a legit email.
What you can do is you can take the email that they’ve got, we’ve done it before. Just forward it on and say: “Hey, Betty Joe, did you get this email? Can you click this link and try it and let me know?”, or send it out to a group and say: “Hey, I got this. I can’t get to it, can you guys click on this and check it out?” So, yes, user awareness is extremely important in educating them, but don’t put all your chips in that basket, because there’s lots of stuff that we defend or can use to defend within the network that we should be looking at.
Martin Bos: And network segmentation is the main thing that we don’t see. This is the stuff that is already in place in your organization: you do not have to buy a fancy appliance, you just have to get somebody who knows how to write Cisco rules or Juniper rules. And what I mean by network segmentation is, like, you know I was bashing on the HR department before, they’re blindly opening Word documents and PDFs all day long, but that’s their job. So, what can I do as an IT defender to segment the HR department, because that’s what they’re going to do, because that’s their job?
So, what I do is I take them as business units when I make combinations, and I say: “This is the HR department, and all they need to do is get to the Internet, Facebook, and there’s two or three internal applications where they enter in their customer data or their applicant data or whatever, and they need to be able to get to active directory, and that’s it.” So, I make up a list of what they need to be able to get to, and I block them from everything else in the network. And you can do every single unit in your organization that way. Is it difficult? Sure. Does it suck? Yeah, but you’re going to be protected when somebody clicks the link.
Eric Milam: And please, for the love of God, segment your dev environment. Because we destroy that; that’s the first place we’d look for, because we know shit’s going to be on the network that’s not patched.

So, basically, summing it all up. User awareness should not be the end goal of social engineering. Yes, it is important, but there’re many layers that exist from the time that a malicious attacker sends that payload or does those different things before the shell gets out.
Testing should encompass all defenses of an organization: again, we’ve got lots of blinky lights. You’ve spent all this money and budget making the organization solid or solidified or fortified, whatever you want to call it – make sure you’re spending that money in the right place. If you just spend too many dollars on a blinky light device and you test it and it doesn’t work – how are you going to feel about that?
Martin Bos: And do not hire the pentest team of the people that sold you the device. Hire a different team. And I’m saying that our company sells blinky lights stuff over here, and we’re on the pentest, we don’t have anything to do with that. But if our company sells you a device, we’re not going to have our company come in and pentest it. I mean, get a different company to do it.
Eric Milam: Plus, Martin and I, and I’m sure others in our group, have no problem blowing up our TS department. If they implemented something and we’re there to test it, we’re going to completely destroy it if we can. Not a lot of organizations are like that, but we pride ourselves on that. That’s it.
Martin Bos: Alright, thanks everybody!




























