
Kevin Poulsen, former hacker and currently Senior Editor at Wired.com, gives a captivating talk at RSA Conference on the intricate story of the cyber criminal named Max Ray Vision (Max Butler) who ended up going from white hat to black hat.
 Thanks for coming, everybody. So, as you’ve heard, I’m a journalist, I’ve been at Wired for about 6 years, and before that I was at the securityfocus.com and I’ve done freelancing for magazines and the like. And if you go back far enough, I’m also a former black hat hacker, though the word didn’t really exist back then – it was a long time ago. I was into the phone company extensively, which means both I liked the phone company and I was into them, so I was into the switching systems and the ordering systems, and all the testing systems. And it started off as a purely recreational thing, an extension of the phone freaking – it began before I was born, and by the end I found a way to monetize it: I started using my access to phone company switches to cheat at radio station phone-in contests. By today’s standards of cyber crime it was kind of slim pickings, but I got like a Porsche and a bunch of trips to Hawaii, and some cash, in total like 70,000 dollars.
Thanks for coming, everybody. So, as you’ve heard, I’m a journalist, I’ve been at Wired for about 6 years, and before that I was at the securityfocus.com and I’ve done freelancing for magazines and the like. And if you go back far enough, I’m also a former black hat hacker, though the word didn’t really exist back then – it was a long time ago. I was into the phone company extensively, which means both I liked the phone company and I was into them, so I was into the switching systems and the ordering systems, and all the testing systems. And it started off as a purely recreational thing, an extension of the phone freaking – it began before I was born, and by the end I found a way to monetize it: I started using my access to phone company switches to cheat at radio station phone-in contests. By today’s standards of cyber crime it was kind of slim pickings, but I got like a Porsche and a bunch of trips to Hawaii, and some cash, in total like 70,000 dollars.
I got caught, should have mentioned that part, and I ended up serving about 5 years in jail, it was all pre-trial custody, I was ultimately sentenced to time served and released. When I got out, I was not allowed to use computers connected to the Internet for a time; I worked as a canvasser for a political organization and I started doing freelance writing, and that eventually turned into a journalism career because once you’re convicted felon, how can you possibly sink any lower than to become a reporter?
So I’ve covered over the years a huge number of hackers and hacker gangs, and law enforcement people that have tracked them, and I found the subject fascinating, not just because of my own past, but because of the way the cybercrime scene has evolved. And when it came time for me to write a book, it was about this particular hacker who I found particularly interesting because he kind of epitomized himself the transition that we have all seen over the last decade of hacking as being primarily recreational thing, the kids doing it in their bedrooms like Matthew Broderick in “WarGames”, to being a professional criminal enterprise.
The White Hat Hacker

And in Max’s case he kinda took the opposite course of what a lot of people did in the 90s, where he saw ex-hackers basically going legit, starting computer security companies, becoming penetration testers. He made his mark first in Silicon Valley as a white hat hacker. He kind of came out of nowhere in the late 1990s and burst out into full disclosure scene, started doing vulnerability analysis and looking at malware and the like. There he is (see photo).
If you’ve been around for a while, you might remember Max, he ran an open source database of intrusion detection signatures for Snort – it was called Arachnids; he contributed analysis and code to the Honeynet project; he wrote papers on viruses and worms, like the Ramen worm, if anyone remembers – that was really quaint. The problem is he also had kind of a mischievous streak, and in late 1998 he saw a CERT advisory about what was then a huge security vulnerability in the BIND name server software. So this software – it’s still pretty ubiquitous, back then it was everywhere, and it had a buffer overflow that you could use to basically take over the server with root capabilities remotely.
So the white hat part of Max was very concerned about this, because he believed nobody was going to patch it, which was not at the time an unreasonable thing to assume. He’d begun doing some consulting for the FBI, and he actually got on the phone and called the FBI agent he worked with at home to say: “Hey, this is a major vulnerability and I’ll tell you what: the militaries can be particularly vulnerable, because there is no way that they are going to be on top of this.” He felt like they didn’t take him seriously enough, so he decided to write a program that would scan IP ranges and look for this vulnerability, exploit the vulnerability, go in and patch it automatically. So he ran this and he targeted in particular government agencies and military IP ranges.
So this thing got everywhere, there was never a final count on how many systems were affected, but it was in the thousands, which, again, in the late 90s was a pretty big number, and he basically made a lot of air force bases and cabinet agencies, and these all sorts of government networks more secure in a way, because they’d had this vulnerability before, and now, after this code ran, they didn’t have this vulnerability. But here he had a little bit of black hat in him, and he couldn’t resist also installing a rootkit on all of these systems with a packet sniffer and a backdoor, and he could come in at any time. He actually had an email conversation with one of his victims who had discovered this activity; he sent him an email from the root account on this administrator’s own system and said:
– Hey, congratulations on spotting this, but I think you’re overreacting.
– Yes, I put backdoors on all these systems, but before – they could be hacked by anybody, now they can only be hacked by me, so I’ve made the Internet a safer place.
Max was naive. So he thought that because he had good motives and because he was a nice guy that nobody would be terribly alarmed by this. He was doing it anonymously, of course, but he didn’t really cover his tracks so much. He had his rootkit program to report back to him every time it infected a system. At one point, when he got into the Navy’s IP range, he got so many pings from these cracked systems that his own computer crashed.

And it was very easy for them to track him down from that feedback mechanism. So they wind up knocking at his door, it was the same FBI agent that he’d been working with plus a guy from the air force who’s done the detective work, and he immediately started apologizing and he confessed to everything. They tried to turn him at that point into an informer, they wanted him to go to Defcon and start gathering information on Defcon attendees. He was kind of well-respected as a white hat at the time, he also had one foot in the black hat community, so they thought that he could gather information. Then they asked him to wear a wire on one of his friends, he refused – and they charged him. So he wound up going here, to the Federal Correction Institute in Taft in Central California in the middle of nowhere as you can see, for an 18-month stretch.
The Robin Hood Hacker
Getting into Taft turned out to be a very important development, because before – he was kind of a misguided naive white hat, sometimes black hat, grey hat hacker who was just acting for hack value. Once he got into Taft, he started mixing with real criminals, white-collar criminals – it’s not a maximum security facility, but real career criminals with a lot of experience, a lot of criminal savvy. So if you’re ever been to prison, you know that it really is like a grand university of crime. Like, you get people mixing from all sorts of different disciplines, they hatch schemes and they learn from each other, it’s actually like the most fun part of prison – you meet interesting people. I experienced that myself. I know more about, like, how to rob a bank than I care to. When you knock over the grocery store and get them to open their safe, look for the mag mounted compartment at the roof of the safe where the cash is actually hidden – all sorts of tidbits like that.

He made a lot of contacts. When he got out, he genuinely wanted to go straight though. So this is where he moved on into his next phase. He was released to a halfway house, they told him: “You have to get a job or you’re going to go back to the joint.” You would think that would be easy for someone who used to make 100 dollars an hour doing penetration testing, somebody who had a really strong name in the computer security community. And when he was sentenced on these Pentagon hacking things, the biggest names in computer security research world wrote letters to his judge saying: “Don’t imprison this guy, it will be bad for the Internet. He’s helping us.” But when he got out, now a convicted felon, a convicted hacker in a very high-profile case, he found out that nobody would hire him, basically. He sent this now kind of legendary email from a halfway house in Oakland to a computer security employment mailing list saying: “I’ve got to get a job or they will send me back to the joint; I will work for a minimum wage until I get out of the halfway house.” He got virtually no responses, somebody eventually responded and paid him a little over the minimum wage to assemble PCs in their shop.

So he grow frustrated, and he was at this point: he got out of the halfway house, he was staying with friends, he got one pen-testing gig from an old client that just kind of threw him a bone, but he wasn’t really going anywhere, and he wasn’t making any money, and his outlook was looking kind of grim when a friend that he’d made in the joint contacted him and said: “Hey, we should work together!” He met the friend in a hotel, they talked about what they might do together; that friend wound up introducing him to another contact, a career criminal and former bank robber named Christopher Aragon.
Aragon is an interesting guy, he had some juvenile convictions and then he got in trouble in the early 80s for a string of bank robberies, most of them botched, but the last one was successful – they actually got out with cash, him and his partner, but then there was a high speed chase through the streets of Aspen, and he was arrested and he went to jail. When he got out of jail, Chris dabbled in credit card fraud for a while, then migrated into drug trafficking, he got popped again in a big undercover operation involving huge amounts of marijuana.
So he went back to the joint again, he wound up when he got out in 1996, and then he went back in for violation, and then he got back out again, he decided it was time to go straight. So at the time that he met Max, he’d actually been a legitimate businessman for a while: he ran an equipment leasing company in Orange County that specialized in leasing computer equipment and office equipment to start-up companies. The problem was the dot-com bubble burst and his whole business collapsed.
So after really going the extra mile for someone with his background to be legitimate – he had a wife, he had kids, he was in Orange County – he was now looking to get back into crime. So he met up with Max and they started talking about what they might be able to do together. He agreed to fund Max, to give Max money to get a nice Alienware laptop and to get some other hacking gear.
And the idea at this point was kind of unfocused, but Max would basically hack fulltime and break into banks or build botnets, like whatever he could do that might ultimately become profitable in some way.

So it was very unfocused at first. Max had learned from his Pentagon hacking not to hack from home – a very basic lesson that he learned the hard way, plus he was still crashing with friends, so what they wound up doing is Chris would come up to San Francisco once or twice a month – this is where Max lived – and rent a hotel room for Max for anywhere from a few days to a week at a time. Max would check in to the hotel room and do all of his hacking from there.

For bandwidth and untraceability (this is where I have a visual aid) Max would use Wi-Fi, so he got an antenna and he would smuggle it up to fire stairs so that they wouldn’t have to bring it to the lobby, because they thought it might attract some attention. So this is the exact antenna that Max used. They would set it on a tripod by the window in a hotel room; most of the hotels were in downtown San Francisco, where the financial district is, so they could just set this up and sweep around; and if you ever played with NetStumbler, you know that an antenna like this would pick up a huge number of Wi-Fi access points, and the ones that even bother to have security, that were likely to be using the WEP were still likely to be crackable. He wasn’t actually trying to hack their networks using the Wi-Fi, he was just using it for bandwidth. He knew that if anybody traced his hacking, they would wind up nowhere and he was completely safe.
So Max had a lot of success by scanning for vulnerabilities, known vulnerabilities, occasionally zero-days that he got through his contacts, and cracking stuff. So he got into small savings and loans, and credit unions – he found them particularly vulnerable. He wrote a script that would go to the FTIC’s website and get a list of small institutions and then automatically get their IP range from the ARIN database and would start scanning their IP ranges. He was very quickly getting into stuff, but he had no idea what to do with it. He had no idea how to turn it into cash.

Chris’ money was running out. So Max did the logical thing and he googled it: “How do you make money off of computer crime?” And that is how he discovered what is probably one of the biggest developments in cybercrime over the last 10 years, the signature development, really, which are the carder forums.
I can spend a huge time on this because it’s been a subject of a lot of discussion at the RSA over the last couple of years. Basically, in the early 2000s this grew out in Eastern Europe, but it spread to the U.S. The cyber crooks decided that doing business in IRC, in chat rooms the way they used to, was inefficient. It was hard to build a reputation and to do business with other people when you are nothing but a nick, a handle in an IRC chat room, which anybody can change at any time. And all the knowledge that they had about how to exploit different vulnerabilities or how to carry out different schemes was transient, it was ephemeral, it would vanish; you could explain something to somebody in an IRC chat room, and then it’s gone as soon as the chat session is over.
So they created these carders forums which were websites dedicated to crime. In a carder forum you give advice to other people about how to carry out credit card fraud and things like that. More importantly, you can buy and sell identity information in a very structured environment. So you get approved to be a vendor in a carder forum. That means that you’re selling maybe credit card numbers or hacked bank accounts, you give a sample to somebody who runs the forum; they will write a review of it. So they’ll try out your stolen credit card numbers and make sure that they have decent limits on them, that most of them, if not all of them, actually work, and they’ll write up a review, just like reviewing a business on Yelp. Then you start doing business. So you’ll have one person selling stolen credit card numbers, you’ll have somebody else who sells the blank plastic cards that you use to make fake credit cards out of the stolen credit card numbers; you’ll have somebody else selling safety paper to make counterfeit checks with; and then somebody else will sell the special magnetic print cartridges that you need to print on the counterfeit checks.

Max discovered the carders forums. He had no reputation in this community, so what he did instead was that he decided to hack everybody that was using them to get an inside look at what was going on. So he posed as a well-known vendor of credit card data and sent out a message to everybody saying that he had an excess amount of American Express credit card data, so he was just giving away his excess, so: “Click here and can get your free Amex”.
If you made the mistake of clicking there, as a lot of people did, you wound up being infected with a brand-new Internet Explorer vulnerability that would give Max root on your system, or administrative capabilities on your system.
So he got 30 or 40 hits instantly as soon as this message went out, and he continued to roll it afterwards. He instantly backdoored all of these carders, and one undercover FBI agent. He could see exactly how everything worked. He was wired right into the system at that point, and he immediately started stealing credit card data. In particular, he went for dumps – these are kind of the pork bellies of the underground. When you hear about people being arrested for stealing or selling credit card numbers, most of the time this is actually what they went after. This is the magstripe data on the back of the credit card.

The magstripe contains the same information on the face of the credit card – the account number, the name, the expiration date, but it also contains the secret code called a Card Verification Value on Visa cards and something else on MasterCard. It’s a cryptographically generated checksum that ensures that you can’t take a credit card number from the face of a card and make a working counterfeit card from it because you don’t know the secret code. You can’t phish the secret code, you can’t trick somebody into giving it to you, because the consumer doesn’t know it – it’s on the magstripe. There’s another secret code printed on the back of your credit card – that’s a completely different code. So it’s not credit card numbers that have value in the underground world; it’s these dumps, the magstripe data.

Max started getting these dumps, they typically sell for anywhere from 8 dollars for like Visa Classic – to 50 for a corporate card or gold card. He would steal it from criminals who’d already stolen it or bought it from somebody who had stolen it, and he would send it down to Orange County to Chris Aragon, the former bank robber, who in the meantime had set up a complete credit card counterfeiting factory.
Thanks to the carder forums it’s relatively easy to learn how to counterfeit a credit card: you have to start with the blank plastic which you can buy through the forums, there are people who specialize in it; you buy templates which will be the design on the face of a particular card done by a Photoshop expert; and then you emboss it and you have to tin it to get the metal on the raised numbers and letters; and then you have to put the magstripe data on it.

So Chris did all of this from a hotel room; actually, not a hotel room, he actually rented an apartment under an alias that he dedicated to nothing but turning out fake credit cards by the hundreds. And these were the results (see left-hand section of the image). He had a talent for this. He produced very, very nice cards. The holograms came from China.
The next step is monetizing this, so he would make fake IDs for himself and for his employees – here are some of his driver’s licenses (right-hand part of the image above). One of them was Chris Anderson who was editor-in-chief of the Wired magazine, but I think it’s no relation.

And he would give the credit cards, and he would give the accompanying fake IDs to his employees. He learned that the best workers – they’re not all pictured here – are young college-age women, preferably attractive, who can walk into a store and just take everybody by surprise. It’s not the type of person that you normally expect to be a credit card swindler, and they can act like privileged Orange County youth.
So they would go in, he would pass out credit cards to them at the beginning of the day, they would hit the malls and they would buy designer purses and other hi-end material, which Chris’ wife would then sell on eBay. So this was the scam for a long time. Max would be stealing stolen dumps from other criminals, giving it to Chris Aragon who would have to scramble to make fake credit cards, give them to his crew, send them out to do shopping – all before the actual crooks that Max stole them from were able to use them. So there were some very frustrated crooks and some very happy hacker and former bank robber.

So things changed – I almost forgot this. At the same time that Max was doing this, one of the people that were infected with a “free AmEx” hack was involved in another major scam that was very-very big in the computer underground around 2004, which very few people are familiar with outside the computer underground. They called this the “Citibank cashouts”. Because Citibank was the most high-profile target, about half of the U.S. banks were apparently vulnerable to this.
The problem was that it turned out that whole CVV system – the secret code on the back of the magstripe that keeps you from being able to forge a credit card with just a credit card number – that wasn’t being checked on ATM transactions. The code was there, but about half the banks just weren’t checking it. I’ve never been clear on why, but I think it had to do with the migration from classic ATM cards that were only good for withdrawing cash, to debit cards that were also credit cards. But it was a huge vulnerability and, basically, the way this was exploited was there were phishing attacks targeting the major banks, particularly Citibank; very good phishing attacks – they would ask you for your ATM number.
And to the casual observer this was very puzzling, because the ATM card number – you shouldn’t be able to do anything with it. You can’t make a fake card with it because of the CVV. But they weren’t checking CVVs. So they would phish ATM numbers; they would program them; they would give them out to crews, cashiers who would then put them on the back of blank cards, put them in ATMs and withdraw cash. Max had hacked a cashier who was working for a big Eastern European cyber criminal that was a major player in all of this. He started stealing the ATM numbers, pulling the scam himself, going to ATMs. Ultimately he contacted this cashier’s upstream provider in Eastern Europe, told them what he’d done, said: “I hacked your cashier; he’s not taking security seriously, as you can see – I’ve been using your dumps for a long time.” So the Eastern European guy cut off the cashier and started giving his business to Max.
The Black Hat Hacker
So Max started hitting ATMs, basically doing straightforward business now just as a criminal mule for this guy in Easter Europe. In the course of a few months of doing this he wound up making a quarter of a million dollars.

So things changed, they got more intense after “Operation Firewall” in October 2004. By this time the first big carder forum in Eastern Europe had gone down; the biggest one now was called ShadowCrew, this was based in the U.S. The secret service compromised one of the administrators after he was busted doing a cashout in New York, turned him and they busted all the leaders of ShadowCrew. It was a huge move against the carding underground. And it left everybody kind of scattered and confused – the people hadn’t been charged, there were thousands of them still, but a lot of the leaders had been taken down and it showed that you can’t trust anybody. Basically, it left everybody very disoriented. It was about a year before they started to recover, and what happened then was a lot of competing forums came up, but they were smaller now. There was no supermarket like ShadowCrew was. So the whole underground was very disorganized: you’d have a couple thousand people on one site, a couple thousand people on another; they’d be using different names on one site, so it was kind of confused.

Max entered into this a year after the “Operation Firewall”, and with Chris he started his own forum, which he called Carders Market. Him being Max, he wanted to call it Sherwood Forest. He still thought of himself as kind of a Robin Hood guy, but Chris Aragon was more of an experienced marketer, and he thought Carders Market would appeal more to the other criminals.
So Max started Carders Market with Chris. He took on two identities at this point: he called himself Iceman for running Carders Market. So Iceman was the king of Carders Market. Another identity, Digits, was a vendor who was selling dumps. His theory was that nobody could come after him for running this site if he wasn’t also known to be selling stolen data. He figured he had, like, a First Amendment argument: we can talk about crime as long as we’re not committing it.
By this point he was no longer stealing from other criminals, but he had his own source of dumps. This was a result of a very cool vulnerability in RealVNC, where basically you could turn any VNC client with a very small tweak into a skeleton key that would get you into any real VNC server.
When Max saw this vulnerability pop up, he basically swept the entire IPv4 address base looking for vulnerable systems. He got into a lot of cool stuff, but what interested him most were these point of sale systems which were then used at restaurants around the country. The point of sale systems were responsible for checking you out when you’re done eating your meal: they swipe your credit card and it charges you, and it gets stored on a server in the back office. But he was getting into those servers where he found that a lot of them were actually storing the dumps even after they’ve gotten an authorization for the transaction.

So he would go in and he would pop them. He wound up being in hundreds of restaurants around the country. His first one was the Pizza Schmizza in Vancouver, Washington. He was in everything from hi-end restaurants to Burger King in Texas. So you order food, you swipe your credit card and Max has it and Chris Aragon has it, and now as Max is vending as Digits, other people in the underground are buying it as well.
So he wound up getting about 1,1 million credit card numbers from restaurant point of sale terminals, and he’d got another million by stealing from other hackers before that. That wound up not being enough.
What happened next was there was another vulnerability. In fact, his whole career is kind of vulnerability driven, he discovers a vulnerability and then he starts playing with it and gets in trouble. This was a big one; it emerged first in the Eastern European underground and then was discovered by the computer security community. Max got on it before there was a patch available; he got with another partner that he’d met online and said: “This is huge. Nobody is going to be patching this anytime soon. I have an exploit, I’m going to customize this so that nobody can detect it. Tell me what systems you want to get into, tell what companies you want to target that you think will get us money. We have a free pass to own data in any company we want.”

So his friend came up with a list of targets: Bank of America, GMAC, CitiMortgage, Capital One. Max staged a spear phishing attack, and this was the first reported spear phishing attack aimed against the financial industry. And he got into, he says, all of these targets. We know for a fact he got into Capital One. 500 people got this phish. It was Max posing as a reporter, asking about a breach at Capital One and providing a link to what the reporter said was a story that was already up about it in another publication.
So if you clicked on that link, you got hit with this vulnerability and Max was on your system. So at Capital One 500 people clicked on the link, and Max got on their network.
It turns out that, too, was not a path to instant money for Max, because these networks that he was cracking were huge, so he kind of got lost in the networks and distracted by things that were going on back in the carding scene where he found that people were being disrespectful to Iceman.
He couldn’t really stay focused on the business end of this. He decided that the carding scene as it then existed was fundamentally broken and inefficient. There were too many forums. There were, in addition to his forum, 4 others that had about the same number of users – like 2000 users each, and that the whole market was broken. He wanted to restore things to where they were in the ShadowCrew days, when there was one forum everybody did business on, and naturally he thought that that should be his forum. So he used a variety of hacks in order to penetrate all of his competitors’ systems. This is what he did instead of making money.
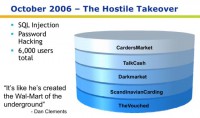
So he broke into TalkCash, Darkmarket, ScandinavianCarding and TheVouched which was supposed to be a high security invite-only forum. He used SQL injection and other hacks to do this. He stole all of their user databases and all of their content. He incorporated them into his own, into Carders Market, and then he dropped the tables on all of these sites.
So he destroyed all the sites behind him. He sent out a big message, an email to his entire new user base, which was now 6000 users instead of 2000, saying: “Welcome to Carders Market. You’re a member of my site now, you’ll find that the old sites don’t work anymore.”
This turned out to be his wrongdoing. He got a lot of attention over this hack: USA Today learned about it and they wrote it up; they quoted Dan Clements saying: “It’s like he’s created the Wal-Mart of the underground.” The secret service took an interest in him and the FBI took an interest in him. The FBI was interested because one of the sites he hacked, Darkmarket – one of the administrators on this site was an undercover FBI agent. It’s Keith Mularski, who you’ve probably seen at the conference. Keith Mularski had been in the forums for a while under the handle “Master Splyntr” and he’d taken a very passive role: he was just intelligence gathering.

But after Max hacked Darkmarket, he went to Darkmarket’s capo – a UK carder called JilSi, and he said: “Hey, I can see you’re in trouble here; you can’t keep out this Iceman guy, you’re getting DDoS attacks now, your reputation is going down to hell. I’m an experienced Eastern European cyber crook, I know how to set up servers that can withstand attacks and won’t be hacked and can’t be DDoSed. Why don’t you let me take over Darkmarket?” So JilSi said “Yes”, and with approval from Washington, D.C., Master Splyntr (Keith Mularski) took over Darkmarket and began running it as a very ambitious undercover operation.
A lot of my book which you should all read is devoted to what happened over the following year. Basically there were only 2 big crime sites now, at least in the English-speaking world. One of them was run by an undercover FBI agent and the other one was run by Max Vision, an undercover computer security guy who turned black hat hacker, who used to work with the FBI. And they were each trying to destroy the other one. As Master Splyntr – Keith Mularski – was constantly baiting his foe Iceman, calling him a snitch ironically, and mocking him and enraging him further; Max in the meantime kept hacking into Darkmarket, where he eventually discovered through IP logs that Master Splyntr was logging in from an FBI office in Pittsburgh. So Max tried to expose Darkmarket as an undercover operation.
Mularski crafted a very finely honed strategy to try and debug that. Part of that was he covered up a lot of evidence that Max had discovered: he got some WhoIs records changed at the last minute and stuff like that. So when Max’s lieutenants held kind of a trial of Master Splyntr designed to prove that Master Splintr was a fed, a lot of the evidence was gone now and the other carders that Max was making this case to began to think: “Maybe Iceman was the fed and was trying to disparage poor Master Splyntr.”

This cat and mouse game continued for about a year, and in the end, well… I should have given a spoiler warning. Anyway, so Max got caught. He’s now in prison for 13 years. This is a lot less time than he could have done just for the stolen credit card numbers. It’s still, obviously, a very harsh sentence. He’s going to be out in January of 2019.
In the end, the final tally was he’d stolen 1,1 million cards from restaurant point of sale terminals and about 700,000 from other criminals. The feds calculated 86 million dollars in charges on the cards that he’d stolen. Max, in the end, not being terribly concerned about money, made a tiny fraction of that: he made probably around a million dollars and he spent a lot of that on things like a Sony robotic dog and giving money to homeless people, and so on and so forth. He was an impulse spender, like a lot of hackers.

So the final lesson here is: Shop online – it’s safer than shopping in real life. This is counterintuitive, but what we learned from Max, and to a much greater degree from the Albert Gonzalez hacks of major retailers like T.J. Maxx, is that all credit card numbers are going online, even if you think they’re not. And because the dumps are what’s needed to actually produce cards that you could use in real life, and the dumps can only be stolen from real-life point of sale systems and the infrastructure behind them, the dumps are what the hackers have been going after. If you ever read a story that says: “Credit card numbers are so plentiful in the underground that they’re selling for 2 dollars, or 50 cents, or something like that,” they’re just talking about the credit card numbers on the front of your credit card, which, in fact, are nearly worthless to carders because they don’t contain that CVV code, because they’re not dumps.
The magstripe data – that’s still worth upwards of at least 5 dollars and up to 40 or 50 dollars depending on the type of card and what kind of limit it has. And then the rest are obvious.





























save all of u
Very interesting read indeed. Thanks for the share David!