
 Brian Krebs – renowned security journalist and the author of KrebsOnSecurity.com blog.
Brian Krebs – renowned security journalist and the author of KrebsOnSecurity.com blog.
I wanna try to set the tone of this discussion in a slightly provocative way. I’ve participated in enough of these round tables on security to know that they often devolve into discussions about how consumers really are the weakest link when it comes to internet security, and if we could just educate end users more, then things would be better. The idea that our security comes down to the end user seems to be something of a truism. It’s a crutch, I think, that allows us to sorta say, just shake our heads and throw up our hands and say if only people were to read our blogs more and pay more attention to the advice, we would beat this problem, we’d be in a much better place. And in many ways, you know, this thinking to me tends to minimize the seriousness of the threat that’s facing many consumers today, as well as the threat to businesses and to our respective national and economic security and prosperity.
I’d like to present a sort of preemptive point to that line of thinking by suggesting that we start looking at the notion of cybercrime in a less passive way, start looking at it for what it is, which is, in many cases organized cybercrime activity. The big differentiator between random virus attacks and organized crime attacks is that for the most part the latter has a magnitude, more resources to throw at their targets and quite a bit more success. So I think it’s fitting that I’m speaking at a conference sponsored by a company that has made such a big play for so-called Cloud-based services.
There is at the moment a kind of fascination with operating in the Cloud, i.e. having all of our data, our protection, our servers – what have you – apart from our normal operations. And the rationale here is that by doing so you can increase efficiency and resiliency, you can reduce the risk of data loss and destruction, and of course when it comes to antivirus products, Cloud Technology really can leverage the wisdom of crowds where, you know, the community of users shares information in real time about the latest threats out there. I think Cloud Computing is a phrase that is at the same time confusing because it means different things depending on who you ask. But also, it’s very useful because it helps us focus our attention on data security – what really matters. And we only have to look at the recent cyber attacks against Google and twenty other, many other top companies to see that in some way it’s pointless to spend all of our money and resources building higher and higher walls if we’re not protecting what is supposed to be protected by those walls, and that is, the data, intellectual property and so on.
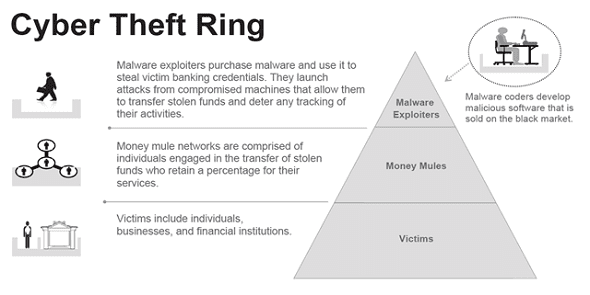 But what’s most fascinating to me about Cloud Technologies is of course the bad guys got there first. The individuals and criminal gangs that are driving most of the financial fraud and more than likely the bulk of the corporate espionage that we’re hearing and reading about so much recently, are really the ones who pioneered the Cloud, or what we refer to now as Cloud Computing. These criminal gangs do most of their work in the Cloud, including data storage, data stealing, spamming, Denial of Service attacks, the distribution and delivery of software exploits. And these cybercrime groups really are operating in top-down hierarchical groups, and many of them have set up their businesses in a sort of assembly line type of operations.
But what’s most fascinating to me about Cloud Technologies is of course the bad guys got there first. The individuals and criminal gangs that are driving most of the financial fraud and more than likely the bulk of the corporate espionage that we’re hearing and reading about so much recently, are really the ones who pioneered the Cloud, or what we refer to now as Cloud Computing. These criminal gangs do most of their work in the Cloud, including data storage, data stealing, spamming, Denial of Service attacks, the distribution and delivery of software exploits. And these cybercrime groups really are operating in top-down hierarchical groups, and many of them have set up their businesses in a sort of assembly line type of operations.
I spend a lot of my time tracking the operations of an organized cybercrime gang that appears to have more than 250 members throughout Eastern Europe, and these guys operate in very discrete divisions. One group is in charge of the research and development – you know, these are the guys that write the malware, they’re in charge of making sure that it stays one step ahead or two steps ahead of the best antivirus software technologies out there. Another group is responsible for harvesting banking credentials, checking account balances. There’s still another group that’s tasked with figuring out which banks to hit based on the methods they’ve developed to circumvent the different security mechanisms that the banks have in place. And then, there are groups that specialize in recruiting people to help them launder money. 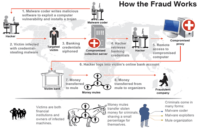 And when you see this kind of criminal operation pass the job or the task along, from one division of the gang to the other, it’s very impressive sight and it’s one that’s very, it’s actually very evocative of the drug cartels, in the way that they operate and share the profits actually. In fact, I’ve taken to calling some of the larger cybercriminal gangs ‘Cloud cartels’ because I think it concisely and accurately explains how they operate and gives sort of a real-world frame for what they are doing.
And when you see this kind of criminal operation pass the job or the task along, from one division of the gang to the other, it’s very impressive sight and it’s one that’s very, it’s actually very evocative of the drug cartels, in the way that they operate and share the profits actually. In fact, I’ve taken to calling some of the larger cybercriminal gangs ‘Cloud cartels’ because I think it concisely and accurately explains how they operate and gives sort of a real-world frame for what they are doing.
We’re all familiar with the international drug cartels, right? In a lot of ways, I think the ‘Cloud cartels’ (the criminal gangs that I think are mostly responsible for much of the cybercrime that we see today) operate in very much the same way as the drug cartels, particularly when you think about one of the biggest problems on the Internet today – spam. The desire to spread spam which in most cases advertises counterfeit commercial drugs – the parallels are pretty stark. In fact, the similarities in the business operations between the drug cartels and the ‘Cloud cartels’ extend all the way down to the street level. Their operations are so similar that these two types of cartels actually share a lot of the same terminology. For example, the illegal drug market would come to a hole, really, if it were not for the activities of the ‘drug mules’, and these are tens of thousands of individuals who physically carry the narcotics on their person, and in some cases actually ingest these drugs as they’re transmitting them across the borders into the United States and Europe.
And as I mentioned earlier, I’ve spent the better part of the last year investigating the operations of a pretty massive organized cyber gang operating in the Eastern Europe. And these guys would not earn nearly as much money if it weren’t for so-called ‘money mules’ – these are willing or unwilling people who were recruited through work-at-home job scams over the Internet. And they’re basically recruited to help move money from victim corporations (companies that these organized groups have hacked into), to help them move that money out of the United States.
I wouldn’t wanna stress this comparison too much but even the way these cyber gangs splice up, what they steal is very evocative of the drug gangs, considering that a major component of these ‘Cloud cartels’ really is large-scale information harvesting and theft. And whatever these guys cannot use, they will sell in bulk. So for example, they often sell the identities that they’ve stolen in mass, they’ll sell it for a very low price per identity. That information, once it’s sold, is sold to another buyer; it usually gets separated out even further, by bank, by region before it’s resold yet again in one form or another, like the refining process of cocaine actually, when it’s choked into bricks and further parceled out into a kilo, broken up into packages. And then it’s resold on a regional, geographic level to dealers who then adulterate it and do all kinds of other stuff, and sell it in even smaller quantities.
I say all this because it seems to me there is a huge need for people to take the threat from Internet security and organized crime gangs a lot more seriously, rather than the tendency today, which is to view a virus infection (if it happens to be caught) as an isolated event. And it seems to me there is a great need among organizations, and individuals alike, to change their mindset when it comes to thinking about cyberthreats. On an organizational level, the focus really needs to be on protecting the data that’s a value, and companies need to change their mindset from the sort of fortress mentality, you know, and just accept the fact that the bad guys are going to get in; and basically putting in place systemic protections that limit any damage that they can do when they get in.
The banks, the financial industry – they’ve been leaders on this particular approach to cybercrime for many years. And if you ask the guys that do damage control for them, they will tell you their main focus is on identifying where the crown jewels live, making sure they have good visibility on who has access to that, and very clear visibility on what’s leaving the company.
So as far as concrete steps that Internet users can take, I would suggest a few things. I think we are long past the stage where people can rely on a single technology, whether it be antivirus or firewalls or whatever, to save them. The biggest question I get from users is “Well, Ok. So my antivirus says that it detected so and so threat, but I don’t know whether that means I’m safe, if it fixed the problem, if that’s been resolved, what do I need to do next?”. And, you know, the unfortunate truth is that it’s not that simple to answer anymore. And that applies whether you’re a regular Internet user or you’re part of a corporate network.
You know, there are basic security precautions that regular Internet users can take to prevent these kinds of problems, and the truth is that using (this is gonna sound kinda basic) but using something other than Internet Explorer to browse the web is a giant step forward for most people. And that’s not to bash Microsoft at all, it’s just a recognition of the fact that Internet Explorer is really tied to so many other things in the Operating System; that exploits that are designed to attack IE have a much greater chance of success. Adding protections like NoScript Add-on for alternative browsers like Firefox and being extremely paranoid about any Emails that entice you to click on a link or download an attachment – these can block a majority of the attacks out there today.
In the enterprise, however, the situation is a lot more complex unfortunately. The user doesn’t always have control over the software that’s on the machine, and at the end of the day people have to get work done, right? And as we all know the enterprise doesn’t really stop at the borders of the company’s network. People take work home, they access files remotely, and so there really is a real blurring of the lines between where company’s network resides and where the home user’s network resides, because the two often overlap. I would say organizations have a tendency to focus on unsophisticated attacks from hackers because they are, generally speaking, the noisiest and the easiest to detect. But that focus can really overlook some of the infiltrations and attacks that tend to be more systemic and have higher economic impacts on the compromised entity.
From where I sit, business would be wise to spend more of their scarce resources on first identifying the data that they have that’s a value to the attackers, and making sure that there’s a strong awareness about what’s going out of the network. So particular attention needs to be paid to those employees who have access to the company’s crown jewels (the data that really makes up value of those companies), whether it be the company’s internal data or the keys to that company’s online banking credentials. There need to be more layers beyond username and password that grants access to this information.




























