
 Andrew Horbury, Senior Product Marketing Manager at Symantec, provides a comprehensive overview of hacktivists’ and insiders’ activities and the related risks.
Andrew Horbury, Senior Product Marketing Manager at Symantec, provides a comprehensive overview of hacktivists’ and insiders’ activities and the related risks.
Hi and thank you, wherever you may be today. I’d like to welcome you all to this webinar which is part of BrightTALK’s Next Generation Network Security summit. The subject of today’s webinar is hacktivism and insiders, and I’m going to talk about some change in the motivation and different attack vectors between the two groups.
Much of what I’ll be talking about today is sourced from the Symantec Internet Security Threat Reports and their web-focused companion, the Website Security Threat Reports; also, a number of other reports from the Symantec Security Response team; and a variety of other internal results produced by Symantec. And I’ve got some links at the end of the presentation so that you can find out a little bit more, download the various reports and study some of the subjects that I’m going to cover.
Here’s the agenda for today (see right-hand image). I’m going to start off with a brief introduction, moving into hacktivism, then taking a look at some common targets, vectors and methods. I’ll then touch upon remediation and ways to protect your organization before tying up with various information sources, where you need to go next for more information.
So, starting off – what’s a hacktivist? Well, hacktivism involves groups of hackers who deface websites of political parties and the like in order to express their outrage. This outrage is often accommodated with demands and justice for those who have been perceived to be forgotten, mistreated or exploited. The motivation for hacktivism far outstrips cyber espionage and cyber warfare, and it’s a very-very close second to cybercrime.

I think one of the best examples of old-school hacktivism was shared with me by a college lecturer who described the blockade of a high street bank (see right-hand image) over their links to apartheid by students in the late 1970s and early 1980s. It was a great example of a denial-of-service attack, whereby the protesters barricaded bank branches and blocked the entrance to the bank. More recently, hacktivism has broken the protests in more ways than one. Hacktivism and its perpetrators, hacktivists, are notoriously difficult to pin down. Are they legitimate, hacktivists and protestors, or simple criminal groups or individuals? Are they after money, or are they ideologically motivated?
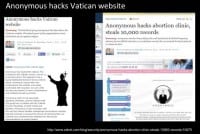
The simple answer is we don’t really know. More likely, they could be any of these things. Although there are fairly high-profile groups such as Anonymous, LulzSec and Antisec, they frequently claim responsibility for data breaches. These groups are entirely open, meaning that anyone can claim to act on their behalf, and proving the attribution is therefore relatively difficult. In fact, there was a situation around Anonymous back in 2012, when an individual claiming to be a member of the group stole the records of 10,000 women from an abortion provider shortly after Anonymous took credit for an attack on the Vatican (see left-hand image). This openness makes it almost impossible to assess how extensive such groups are and what threat they actually pose, and what hacktivist groups tend to be broadly united by a libertarian distrust of government, a belief in networks, the free systems and a mistrust of intellectual property laws. Their methods are wholly unpredictable.
Well, hacktivism appears first in the mid to late 90s. It began with the defacement of websites, and it has become, with the establishment of groups such as Anonymous, more politically engaged, more ambitious, and more sinister. 58% of all data theft in 2011 was tied to hacktivist groups, stealing more data than any other actor motivated by everything from greed to ideological aspects. In the latest version of data breach report, however, the percentage of confirmed data breaches deployed by hacktivists in 2012 is on par, but the amount of data they stole was substantially less, shifting from data theft to other forms of attacks such as distributed denial-of-service attacks.
So, while some hacktivists break into systems to steal data for their own game, others use brute-force and DDoS attacks to shut down target websites for ideological reasons. The motives and methods of hacktivists can be seen to be in constant flux. The mistake, however, is to think that this lack of consistency and unity makes hacktivism a lesser threat. This very ability makes it harder to detect, harder to predict, and a real challenge to defend against. If anything, hacktivism is a more dangerous threat because of its very unpredictability.
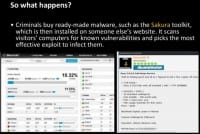
So, let’s take a look at what happens (see right-hand image). The feature of the Internet that makes it such an amazing tool for communicating across the globe with billions and billions of people can also provide a means for disgruntled people to voice their opinions, send messages of unity at great speed, and also coordinate electronic attacks; the development of widespread methods of DDoS toolkits, which we have actually seen being used as a diversionary tactic to distract from discovery of the real threats, potentially any attempts to stop it; and malware toolkits such as the BlackHole kit; and the re-emergence of the Redkit exploits – a bit more on Redkit in just a few moments.
In fact, an interesting point here is that cyber criminals are even using a business model known as ‘malware as a service’, where exploit kits offer extra services to customers in addition to the exploit kit itself. Combined with the ease of use and the ability to globally distribute them in minutes – this effectively means that an entire country can, in theory, mobilize a group of dedicated attackers, numbering in the millions, in a relatively short space of time.
So, let’s take a quick look at BlackHole which works in the following way: it is an exploit kit used to inject malware when a potential victim is on a website that has some form of unpatched vulnerability, or a redirect to such a site from another compromised website. Hackers typically use the exploit kits to drop malware such as botnets built with the Zeus toolkit, rootkits, or fake antivirus packages that are intended to be used for fraudulent malware protection.
And actually, Redkit works in a very similar way. As I’ve mentioned earlier, we’ve seen quite a re-emergence of Redkit after the author of BlackHole, a guy named “Paunch”, was arrested a few months ago. Those tools have been termed as a “cyber criminals’ Swiss Army knife”, and what makes them so prevalent is they remain effective over and over again. And because of this effectiveness, we see large botnets being created. The goal of attacks, generally, is to make or steal money, and for instance if a hacktivist hacks a large multi-national bank, they’re stealing your records to your bank. Every day even seemingly innocuous sites are targeted. In fact, even the most reputable sites get compromised and serve malicious software from time to time.

…Which is why it’s important to use a layered security approach and remain vigilant whilst online. A web service can also be attacked by malware just like a desktop PC. In 2012, Symantec Website Security Solution division, which is part of Symantec that I work for, scanned 1.5 million websites for malware. We scan over 135 URLs for malware each day, finding that 61% of sites serving malware are actually legitimate sites. 53% of legitimate websites have some forms of vulnerabilities, and 25% appear to have critical unpatched vulnerabilities (see right-hand image). The most common vulnerability we found was cross-site scripting (XSS) vulnerability, which is often just what the toolkits are looking for.

With 5291 new vulnerabilities reported in 2012, it’s critical to keep up to date with patches. Many of us say: “We’re absolutely up to date with software and application updates across every single device that we use today,” and all of a sudden I realize there’s an update pending on my phone which I should launch as soon as I’m done presenting today. It’s relatively easy to fall behind in this process. And with all of these unpatched vulnerabilities in legitimate websites, there’s often really no need for the malware authors to set up their own. As a reminder, with 61% of all malicious sites being legitimate sites, there’s often very low need at all.

Let’s take a brief look at web based attacks (see right-hand image). These are also successful because often small and medium-size businesses, as well as consumer systems, are not up to date with the latest patches for something like browser plugins such as Adobe Flash, Acrobat, perhaps it’s the Java platform. Well, while a lack of attentiveness can be blamed for consumers in terms of the updates, often in larger companies older versions of these plugins are required to run critical business systems, making it harder to upgrade to the latest versions. Such patch management predicaments with slow patch deployment rate make companies especially vulnerable to web based attacks.
So, why am I telling you this? I mean, you may think it’s unlikely that your company will be targeted, right? Well, over the next few slides we will be looking at levels of malware and global vulnerabilities that Zeus has been targeting. And yes, it might be in your companies – we’ll take a look at the types of companies that have been targeted.
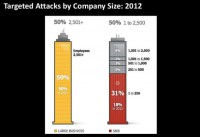
As we can see, it’s right across the board (see right-hand image). Most concerning is not just the big firms have been targeted – a sweet spot is the 1-250 employee group, such as a small business or a startup. Take a note: security really is important.

Just focusing on small businesses, in a recently published report, a survey of over 2000 small businesses conducted by the Federation of Small Businesses, which is a lobby group here in the UK, they collected some interesting statistics relating to cybercrime in the United Kingdom (see left-hand image). And although this is a UK study, I don’t think that it’s particularly specific to the UK. Many other studies show similar findings in other countries. So, just looking down the list here, 41% have been a victim of cybercrime in the past 12 months. 20% have had a virus infection in their business. 8% have suffered from a hacking incident. But what’s particularly interesting, the really worrying statistics is that 20% have not taken any steps to protect themselves at all. In a pool of 2000+ surveyed businesses – that’s at least 400 businesses that are probably at high risk – 36% say they regularly apply security patches, which leaves a huge pool of either those that do not do it at all or do it somewhat haphazardly. And bearing in mind the info in one of my previous slides that indicates that 53% of legitimate websites have vulnerabilities, you can start to see just how hacktivists and cybercriminals can get into companies.
However, on a post-it note, nearly 60% of those surveyed say that they keep their antivirus software up to date. I’m sure you’re all aware using an up-to-date antivirus solution is of course a great step forward, but it’s not necessarily enough against the attackers of today, where you need to take a layered approach of security, having firewalls, having antivirus, having demilitarized zone, having SSL encryption, etc. So it looks pretty clear from this particular survey that security is still not taken as a serious concern among small businesses, and for many it just appears to be an obstacle.

There’s a widespread availability of the toolkits we were speaking about earlier, and quite often these toolkits are, relatively speaking, quite simple to use – you don’t even necessarily have to be a computer mastermind or a security expert in order to use them. Even a group of relatively low-level expertise users can, with some management, pull off a devastating attack. And when you consider that that’s what an amateur can do, imagine what impact a more serious, more proficient user or sets of users can have. The methods of hacktivists include email bombs, spam, virtual blockades; and it’s detailed by the bank story that I provided a little bit earlier, which was a DDoS attack combined with physical effects.
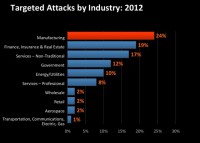
You can start to see how the hacktivists have taken their methods to the new world. Of course, these are in addition to general hacker activities such as web hacking, defacement, and malicious code attacks. As you can see on this slide here (see left-hand image), the breadth of the industries being attacked is incredibly wide-ranging; it’s not just focusing on any one particular industry; it’s many different types.
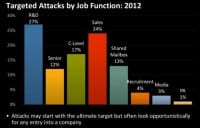
And you can also see that it’s not only the industries that are being targeted, but also many different types of people are being targeted and their job function is being targeted (see right-hand image). So, while some hacktivists break into systems to steal data for their own game, others use brute-force and DDoS attacks to shut down target websites for ideological reasons.

Did you know that insider theft makes up between 8-14% of confirmed data breaches, compared to the 88-92% attributed to external actors? Those figures come from the Symantec Security Threat Response data piece. But these relatively small numbers are somewhat misleading. So, whilst insiders might make only a small percentage of confirmed data breaches, they account for almost 70% of all corporate security issues, compared to the 31% that we can attribute to outsiders. This is reflected, in fact, by the UK Information Commissioner’s Office who fined and prosecuted more businesses because of insider slip-ups than they did because of outsider attacks in 2012.
In fact, the Symantec Internet Security Threat Reports state that most small to medium-size businesses should worry about someone in accounts just as much as they should worry about some anonymous hacker. The majority of confirmed data breaches committed by insiders without malicious reasons are done as some form of game, while there are of course a lot of cases of programmers, administrators engaging in insider data theft – most of such actions are attributed to employees with little or no technical ability or status. Employees involved in the payment chain, particularly in small to medium-size businesses, seem to be the main culprits, often solicited by external actors to skim payment cards or supply customer information in order to commit some fraud.
Only three cases of insider espionage were recorded in 2012, according to the Verizon Data Breach study. And all three involved appear to be ex-employees in managerial or executive positions, trying to take proprietary information to a new employer. So, who’s behind the crime, however? Those who commit such action often exhibit certain behavioral changes or warning signs, according to the research by the CERT’s Insider Threat Center, giving employees and colleagues the chance to prevent such breaches.

More than 30% of insiders engaging in IT sabotage have a prior arrest history. They perhaps may boast about the damage that they could do to an organization if they so desired. They might be bitter about being passed over for promotion, for example. They might also have serious conversations with co-workers about starting a competing business and start using the organization’s resources for side business or even for a new employer. The pattern or quantity of the information they retrieve also might change drastically, potentially indicating data theft. And particularly when you can see that people are leaving, you might see the pattern of data theft or data leakage go up. Many of the instances, however, were attributed to human error or insecurely stored information. But the fact that a lot of insider theft is accidental shouldn’t mean it’s overlooked. Data loss is serious and expensive, and if it goes public it can cause incredible damage to the reputation of the business for a long time.

What do you need to focus on with insiders? Well, you need to focus on your people; focus on deterrence rather than detection, because at the detection stage perhaps it’s already likely to be too late. You also want to identify information that is most likely to be valuable, and then also monitor ingress and egress, consider potentially restricting the flow of information outbound from one network to another. Also, use solutions like data loss prevention in order to limit the data flow loss. You also want to baseline normal activity, so start to consider looking at what employees do today and then see how those patterns change over time, subsequently looking at what could be perceived as abnormal activity.

So, what do they do and what are the threats? Hacktivists have different motives, and that makes the threat they pose hard to determine. To illustrate this, at the beginning of 2012 Anonymous claimed responsibility for a broad range of actions: publication of bank managers’ details, DDoS attacks on government websites, the hacking of two MIT websites, publication of VMware source code, etc. (see left-hand image). This is just one group. Other hacktivists have other motives and other methods. Protests against anti-Islamic Western messages have turned to website defacements and denial-of-service attacks.
A group calling itself the Cutting Sword of Justice used malware to wipe the computer hard drives of energy companies in the Middle East in August 2012 (see right-hand image). And a group called Izz ad-Din al-Qassam Cyber Fighters claimed responsibility for denial-of-service attacks against various financial institutions through 2012. The issue is further complicated by the fact that some denial-of-service attacks are used as smoke screen by actual organized criminal gangs before or after they attempt to engage in unauthorized transaction or a deep infiltration to disguise the theft and prevent attempts to stop it.

What does a hacktivist profile look like? Again, some of these things come from the Verizon’s Data Breach Report that I mentioned earlier. Well, hacktivists mainly target the information, public and service sectors. We know that they primarily operate in Western Europe and North America. Their most common attack methods are SQL injection attacks, using stolen credentials, brute-force and DoS attacks, remote file inclusion, and of course backdoors. The main assets they target are web applications, databases and mail servers. Their desired data is personal information, credentials and internal corporate data. Also worth noting, however, that this is a rough profile only. Hacktivist activities are erratic and can threaten businesses, both big and small in any sector, by exploiting website vulnerabilities, weak passwords, unpatched software and unencrypted sites.

Looking at insiders now, the most common insider cybercrimes were, according to the CERT’s Insider Threat Center, unauthorized access to or use of corporate information; viruses, worms or other malicious code; the theft of intellectual property. Additionally, the same research found that insiders often attempt to gain fellow employees’ passwords or obtain access through trickery or exploitation of a trusted relationship, which is, in essence, a type of social engineering, using charm or something like that in order to gain some information that they want to exploit and use.
In more than 70% of intellectual property theft cases, insiders steal the information within 30 days of announcing their resignation. So, again, it goes back to the point I made a little bit earlier, there are signs – as soon as people start announcing that they’re leaving an organization, they suddenly start to perhaps look for information that they need to take to a new employer or for their own new job. More than half of insiders committing IT sabotage were former employees who regained access via backdoors or corporate accounts that were never properly disabled. So, again, there’s a lesson to be learned there: to properly close down accounts and disable accounts as people move on to new organizations. The main threat from insiders, however, is that they generally know the business security systems and subsequently know exactly where to strike. The other common danger is that businesses often lack website security or lack strict access controls for data. Even temporary staff have access to privileged information.
This is exactly what happened in a recent insider data breach in South Korea, where a temporary consultant at the Korea Credit Bureau stole the details of up to 20 million South Koreans from the company’s servers before selling it on to various marketing firms (see left-hand image). Without the right access and managing capabilities, companies might be incredibly exposed. But of course not all insider actions are about money. Many incidents involve the unintentional exposure of private or sensitive data. These, however, can be just as damaging as intentional attacks. These can involve employees sending sensitive documents or information to their own recipient; saving or storing information in an insecure location; taking work home via personal email account, a personal mobile device; or taking sensitive data home on a removable drive or USB stick. Whilst these actions are not disastrous, they do expose data to unauthorized parties and put sensitive corporate information outside of the organization’s control, increasing the risk of data theft. But whether malicious or unintentional, the results of insider actions are often the same. The protection of data at rest and in transit is vital to businesses trying to combat these incidents and their actors.

What can you do about it? Well, you can never entirely eliminate the risks from hacktivists and insiders, but you can certainly mitigate them by enhancing your security. This doesn’t mean stocking up on every piece of security software on those firms – it requires a considered approach to the risks, where cost-effective security software only plays a part. So, let’s look at these in order. Taking security, the first step is to assume that you are a target. Small size and relative anonymity, as we’ve seen, are really not defenses. Hacktivists can use a website to disguise their actions and attack larger, more valuable targets. And insider attacks occur at businesses of all sizes and sectors.
Clearly then, antivirus on its own is not enough – you need to deploy a range of security software to protect your employees and your information. You need best-fit cost-efficient software that both protects and enables business rather than constricting it. Your employees should be able to work securely without fear that they might be endangering the business, and this means regularly updated endpoint protection to stay protected from the latest malware; SSL encryption to protect data at rest and in transit; a secure regular backup and recovery system to prevent data loss and exfiltration; proper access and permission controls; and mail and web security, including regular malware and vulnerability scans to protect your website and keep your employees safe online.
But security means more than just software. You need to anticipate potential issues and be proactive about managing disruptive and disgruntled employees. It’s worth considering having documented working place policies that clearly state the company’s position on things like salary increments and promotions, working hours, workplace behavior and so on and so forth. And when you consider an increasingly mobile workforce, it’s particularly important, with more and more employees working remotely, that they know that the culture and the policies that make up the company still apply when they’re working far away from the home base. You also need to ensure that the cases of retiring and departing employees are completely closed, that they hand back any computer equipment, laptops, mobile phones, any other devices are collected, making sure that over the course of the exit from the company there hasn’t been any kind of data leakage and that they all are given the opportunity to have an exit interview to talk for any issues that they may have before they leave the organization.
Considering that the majority of insider attacks are instigated and started by disgruntled employees and those about to leave, it helps to have a supportive and open company culture. Within reason, allow your employees to work where and when it suits them. Give your employees the opportunity to talk or to suggest improvements to business processes, to become engaged to the workplace. And invite them to talk for any issues they’re having. Any possible resentment or issues that might start thriving inside the company should be ceased as soon as they are discovered.
Educating your staff about data protection and the threats posed by hacktivists and insiders is also an essential part when we’re looking at defense. Make sure your employees know what data is okay to share and take home, and perhaps also consider employing mobile device management software to secure mobile devices, detect applications that can share data between one another, and also have home and work applications, not allowing them to transfer data between the two, and also have the ability to remotely wipe the information should it fall into the wrong hands.
You also should consider having periodic security training sessions for your employees to make sure that they’re up to speed for all of the business and security software that you use, that they know how to stay safe online and how to protect and securely store the data, particularly in cloud applications. This means the very obvious: using strong passwords with special characters and capital letters and numbers; not visiting suspicious websites; not opening unusual emails, particularly ones that look too good to be true and which may contain a malicious PDF or links to what appears to be a normal invoice, but is actually to a malicious website; and not downloading or installing applications if you don’t recognize the source or perhaps it’s not signed by a reputable code signing body. You may also need to make employees aware of the danger of insider and hacktivist attacks, and the associated risks of social engineering so that they can spot and report suspicious activity and avoid inadvertently creating vulnerabilities. Cyber attacks and their perpetrators are unpredictable and constantly evolving, but being aware of the risks and taking these first steps can help to give you the edge.

That almost brings me to the end of this webinar. I hope I’ve given you a good introduction into understanding of hacktivists and insiders. On the slide you can see a number of links where you can go and find out some more information. You can follow us on Twitter; the Threat Intelligence team, particularly, tweets a lot about vulnerabilities, malware and virus attacks, attack vectors, and a lot of the information that I’ve covered has been sourced from this particular team. You can follow me on Twitter – @andyhorbury. You can also download the Internet Security Threat Report, which I referred to a little bit earlier, at www.symantec.com/threatreport. We’ve also got a white paper resource site where you can download any kind of documents including the Website Security Threat Report, various technical white papers on things like forward secrecy. If you go to www.symantec-wss.com you can download all of that information there. We also frequently blog about lots of different issues, and you can read that at www.symantec.com/connect/blogs/website-security-solutions.
So, I’d like to say thank you – it’s been my absolute pleasure to present today, and if you want to contact me with any questions, here’s my email address: andy_horbury@symantec.com. Thanks a have a great day!




























